Security Now Episode 886 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for security. Now, Steve Gibson is here. He's got his take on the LastPass breach. I know you wanted to hear all about that. Then it's an interview with a hacker, some really interesting revelations from a ransomware hacker in Russia. Finally, he's gonna talk about wacky ways to exfiltrate data from air gap computers. Some really interesting ideas here. It's all coming up next on security now podcasts you love from people you trust. This is TWI. This is security. Now with Steve Gibson episode 886 recorded Tuesday, August 30th, 2022. Wacky data exfiltration. Security now is brought to you by Secureworks. Are you ready for inevitable cyber threats, Secureworks, detects, evolving adversaries and defends against them. The combination of security analytics and threat intelligence direct from their own counter threat unit. Visit secureworks.com/twit to get a free trial of contagious, extended detection and response also referred to as XDR and by Grammarly.
Leo Laporte / Steve Gibson (00:01:17):
Get more time in your day with confidence in your work with Grammarly. Go to grammarly.com/security now to sign up for a free account. And when you're ready to upgrade to Grammarly premium, get 20% off for being a listener. It's time for security. Now to show we cover the latest security news with the man, the myth, the legends, Steve Gibson. Hi Steve. Yo Leo. Great to be with you again for this last podcast of August. Where has the year gone? Where has it gone? Yeah. Yeah, actually Lori and I were were, this is, we have an anniversary of our first date coming up here. It's five years. What? It's like five years. That's great. Where did that time go? Do you do you give are there gifts for the first date that one give, thank God. No, she's so sane. She's like, oh, <laugh> you don't have to worry about that.
Leo Laporte / Steve Gibson (00:02:16):
No, the reason we're married is that she's completely like, not that way. Yeah. Low maintenance. We call it like I have to tell her that it's Valentine's day. She says what? Oh, okay. Do you care? No. Okay, good. Let's okay. What's on TV. <Laugh> so what are you guys watching these days? Oh, well we're really liking the old man. Isn't that good? But yeah. Well, I won't say anything I'm after you finish it, let me talk to me because it starts so well. I totally agree. And I think I just hurt, hit the rough spot you're talking about. Yeah. And it's like, wait a minute. This is not what I wanted to have happen. Bingo. I just, yes. I loved the way it was progressing. And then, you know, then does her, yes. Zoe does exactly when that happens. And it's like, this is like went off the rails.
Leo Laporte / Steve Gibson (00:03:11):
Unfortunately, roundabout episode four. It's too bad because that's exactly right. And it was Roman numeral four and episode IV. Yeah. In in the apartment and it's like, oh God, I feel bad. Cuz I've recommended this to so many people. But I recommended after the first three episodes. <Laugh> yes. And I, and, and the reveal that we got that, that surprise. Oh goodness. Yeah. You know? Yeah. About his daughter and, oh, that's a good twist. Yeah. And Lithgow is still in fine form. I love after all these. Oh my goodness. So yeah. Anyway, great cast all around actually watching that. I think the next one is the, I can't think of what the name is. It's not the timeline, it's the something not, not the time Traveler's wife. I'm sure not, no, no, no. Watch that. Although Lori might like it cuz the, the star is naked a lot and he's very hunky <laugh> it's you know, it's so funny cuz you can see the TV watching that you can see the TV executives going.
Leo Laporte / Steve Gibson (00:04:20):
Can you be anchor? Yeah, he can. Yeah. you know what? I, you know what I've been wa watching and it's an old show that I discovered lately on Amazon prime it's called Patriot and I think you guys would love it. Oh. So make a note of that. Yeah. However you were saying just briefly and we should put it into the recording now. Yes. Since we have, are you hit the record button already? Yes. yes. You started reading. Thank you. <Laugh> you started reading the singularity trap. I did. You were right. This is the book that last week, Steve almost didn't do the show <laugh> because he like four pages left and he just couldn't put it down. So I thought, well that's pretty good. And it's by Dennis E. Hamilton, who did the incredible Bob averse, Dennis Taylor, Taylor, I'm sorry. Incredible Bob averse saga.
Leo Laporte / Steve Gibson (00:05:09):
And it is definitely that style, same reader, Ray Porter. Yep. And I'm quite enjoying it. Yeah. You it's pick got wit and, and it's written smart, you know, it's smartly written and yeah. Yep. I agree. I agree. Okay. So we're gonna talk about wacky data ex filtration <laugh> brought to us by those amazing engineering students at the Ben Guion university of the NACA which never fails to entertain. But first we're gonna, we have to discuss because boyed by Twitter, Twitter, DM feed, go over board with the implications of last week's LastPass breach disclosure. We then look at some, some recent saber rattling by the USS federal trade commission and federal communications commission over the disclosure of presumably private location data, which turns out not to be such. I wanna share some pieces of a fascinating conversation with a Russian ransomware operator which gains us some insight into the way he conducts attacks and the way he views the world, which is just a little jarring for me.
Leo Laporte / Steve Gibson (00:06:28):
I also wanna tell everyone about a new tracking, stripping and privacy enfor, email forwarding service. That's just come out of its year long beta from our friends at the <laugh>. I wish you'd come up with a different name, duck, duck go. We also have another big and widespread T update mess to share that I've got a welcome progress report about my work on spin, right? Some listener feedback. And then we're gonna look, as I said, at two new wacky ways of exfiltrating data from air gapped computer systems. So, wow. I think in other great podcast, wow. In our listeners, exfiltrating data, wacky ways, there've been quite a few come to think of it over the, over the years we've been doing this show. Well, and I, I, I remind us at the beginning of talking about this, about aiming the laser right at the bag of potato chips.
Leo Laporte / Steve Gibson (00:07:28):
Right. <laugh> good. Well, get into that in a second, but first a word from our sponsor. Oh good. It still works. <Laugh> just checking my checking. My buttons. This episode of security now is brought to you by Secureworks. Secure works is a leader in cyber security building solutions for security experts by security expert Secureworks offer superior threat detection and rapid incident response all while making sure that customers are never locked into a single vendor. Secureworks offers an open extended detection and response platform. It's called contagious. XDR why do you really have to ask if you're a listener in 2022, cyber crime will cost the world, get this $7 trillion. That's this year by 2025, the figure grow to 10 and a half trillion with a T in 2021 last year, ransomware totaled 20 billion in damages attacks occurred every 11 seconds by 2031, ransomware has projected a cost 265 billion a year in strike every two seconds.
Leo Laporte / Steve Gibson (00:08:41):
And I think that's actually low. I think that's an optimistic estimate. How do you make sure your organization does not add to those numbers? You don't wanna be the next victim. The answer is Secureworks. Contagious XDR Secureworks. Contagious provides superior detection identifying over 470 billion security events per day. Prioritizing the true positive alerts, eliminating alert noise and allowing organizations to focus on the real threat. In addition, contagious offers unmatched response with automated response actions to eliminate threats before damage is ever done. Whether your organization has a limited it staff and budget, or whether you run a well funded, fully staffed security operations center, you're gonna get customized support with SecureWorks contagious managed XDR. You can easily leverage secure work's experts to investigate and respond to threats on your behalf so that you can cut dwell times, decrease operational burden and reduce cost. And with 24 7 by 365 coverage, whether you experience a Christmas day security event or half your team is out sick, you can trust Secureworks is behind you.
Leo Laporte / Steve Gibson (00:09:51):
Many companies are facing a shortage of security, talent, hiring retention harder than ever, right? Secureworks customizes the approach and the coverage level you get in order to give you exactly what you need. Bottom line SecureWorks acts as an extension of your security team on day one, alleviating cybersecurity talent gaps. What happens if you've already found a intruder in your system? There's no need to worry. Write down this number, put it on a post-it note by your screen. 1-800-BREACHED one 800 B R E a C H E D. That number will connect you with the Secureworks emergency incident response team, and they can provide you with a media assistance 24 7 in responding to and remediating a possible cyber incident or data breach. Just having that phone number is reassuring at Secureworks. You can learn more about the ways today's threat environment is involving the risks it can present to your organization, including case studies reports from their counter threat unit and more visit secureworks.com/twitt.
Leo Laporte / Steve Gibson (00:10:58):
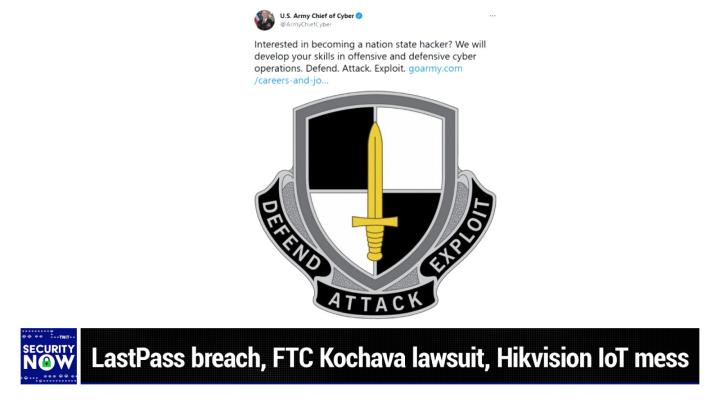
I'm gonna get a free trial OFTs XDR that's secureworks.com/twitt. Please use that address. So they know you saw it here, SecureWorks defending every corner of cyberspace. This is the partner you want secureworks.com/twit. Now back to Mr. Ji. Okay. So this picture of the week mm-hmm <affirmative> was tweeted to me. Yes. And it was so cool that, and I apologize for like wondering if it was authentic or not. So I, I went back to the source to the original tweet from the us army chief of cyber who tweets from at army chief cyber C Y B E R. And the, apparently the slogan is defend attack exploit <laugh> okay. And yeah. And so the, the, the tweet reads interested in becoming a nation state hacker, we will develop your skills in offensive and defensive cyber operations. Wow. Attack, I'm sorry. Defend attack exploit. And then there's a link and I've got the link of the show notes and a link to the original tweet. Now, Leo, I have to say that, you know, I've often wondered if I were a youngster. Like, what would I do? Well, even if the pay wasn't that great, the idea that you could actually like, like, it would be legal for you to be like, make portable dog killers. What is that?
Leo Laporte / Steve Gibson (00:12:53):
Wow. No, I mean, this is so cool. And, you know, props to them for just saying this is, look at him standing next to this big emblem there. Yeah. Defend attack exploit. It's defensive and offensive is what it is. Sign me up, baby. Yeah. Oh goodness. Yeah. You know, I'm not crazy about the uniform though, but well, and the problem is if you're really good, you probably get moved into the bureaucracy at that point, I would say, ah, okay, I'm gonna take all my skills that I've just sharpened and go somewhere else. This is very Jason born though. You really do wanna do this, right. It, oh, I do. Yeah. I mean, it's legal. You can attack people. Holy crap. You put for the good guys. That's right. Yeah. That's right. You know, you're dealing, you know, we're taking, getting, given the rusts something back, the only thing I don't like, and I guess you can't expect more from the army is the word cyber just by itself.
Leo Laporte / Steve Gibson (00:13:50):
I don't like cyber. Right. But I guess that's, you know. Yeah. I think that's that's with us, you know, thank we can thank William Gibson for that one. Well, I, but I don't mind cyber in conjunction with another word, but this guy is the us army chief of cyber. Oh, I agree. That's a little awkward. Yes. Yeah. Yes. <laugh> if you said, you know why? Cause they say cyber warfare, they don't wanna say cyber warfare, but that's what it is. Right. They just don't wanna say exactly. Yeah, exactly. You could say cyber defense, but then it's, it's exploited as well. So, so we've been talking about careers in it and in hacking and you know, it's if, if you you're particular like bent would, was, you know, suggest that I just wanted to make sure that everybody knew that that this was actually happening.
Leo Laporte / Steve Gibson (00:14:41):
So very, very, very cool. Very nice. Yeah. Okay. So not so cool was the news of last week's LastPass breach announcement, which as I mentioned before, overwhelmed my Twitter DMS. So I wanted to lead with this because so many of our listeners myself included are using LastPass. So I had as a consequence, also received an email from LastPass, the current LastPass CEO. And I, I say current because it's been just been jumping around somewhat recently, a guy named Kareem tuba had the following to say in their online blog posting, which echoed the email that he sent to everyone. He said, I wanna inform you of a development that we feel is important for us to share with our last past business and consumer community. Two weeks ago, we detected some unusual activity within portions of the last past development environment.
Leo Laporte / Steve Gibson (00:15:46):
After initiating an immediate investigation, we've seen no evidence that this incident involved any access to customer data or encrypted password vaults. We've determined that an unauthorized party gained access to portions of the last past development environment through a single compromised developer account and took portions of source code and some proprietary last past technical information in response to the incident we've deployed containment and mitigation measures and engaged a leading cybersecurity and forensics firm. While our investigation is ongoing, we've achieved a state of containment implemented additional enhanced security measures and see no further evidence of unauthorized activity based on what we've learned and implemented. We are evaluating further mitigation techniques to strengthen our environment. We've included a brief FAQ below of what we anticipate will be the most pressing initial questions and concerns from you. We will continue to update you with the transparency you deserve. Thank you for your patience, understanding and support.
Leo Laporte / Steve Gibson (00:16:57):
So note that there's not a categorical denial that anything like password vaults, it's just no evidence of. Right. So I feel like there's, we, we're not completely out of the woods that I'd like to know that there is in fact not merely no evidence of, but it didn't happen. Okay. I'm, I'm curious what you think about that. The other thing is, I think this is part of the TWI, the Twilio breach that this is a follow on, on the Twilio hack, which turned out to really be problematic. It was pretty deep because so many people use Twilio for authentication and other you know, texting. So, so of course we have the, the problem of proving a negative. So you know, lack of evidence, isn't true. Evidence of lack and so forth. Right. Okay. So, so the, the short version of the FAQ, I, I don't, I'm not bothering to share at all, but it was basically that there that they believe there is to be zero impact upon LastPass users, you know, no need to change passwords, do anything, or take any action of any kind.
Leo Laporte / Steve Gibson (00:18:05):
And I'm sure they're unhappy that this occurred since, you know, I'm sure that they hold their proprietary information in high regard and don't want attackers snooping around in it. But we've always known since I first checked out the technology that Joe Siegrist originally designed is that so long as the LastPass code that runs our local browser vault is not it's self compromised. No, and that's the, that's the key. I mean, that's the, that's the golden goose. There is the, is the, the, the script in our browser that knows how to decrypt the local copy of the vault. As long as that's not compromised, the only thing we're providing to LastPass, the only thing they have of ours to lose is a very well protected encrypted blob of entropy one from each of their users. You know, that's what they hold for us in the cloud, which allows them to link all of our devices together.
Leo Laporte / Steve Gibson (00:19:14):
And I'm sure this is no longer unique technology. I don't know that it was back then, but, you know, though, I haven't looked, I would imagine and hope that's what every other password manager also does because it's the only way to do what we all want safely. We know that LastPass uses a strong many iteration. PBK DF you know, a password based key derivation function, which runs in our local browser to encrypt all of our password data before it ever leaves our local machine. So you need to have a good, strong password to protect your vault. If you have that you're as safe as you could be. And presumably, you know, adding any of their other security measures, such as multifactor authentication hardware, Don goals, et cetera, only strengthens things from there. But this leaves us with the question with LastPass, having admitted to having one of their developer accounts breached, should we change password managers?
Leo Laporte / Steve Gibson (00:20:20):
You know, that's, I was asked that directly by many of our listeners, and it's a worthwhile question lacking any additional information and no additional information is available at this point. I think that's an emotional decision rather than irrational decision, which is not the discounted. I mean, I, you could argue that the human race is here because of the result of emotional decisions. Yeah. You could argue trust. No one is an emotional decision too, I guess, right? Yes. Yes. So the reason I think that that is that this is that we, that we need a rational decision is that, you know, because there's no, there's no factual basis currently for knowing about what matters to make an informed decision, it would be necessary to deeply understand the company's policies and procedures, like as an insider and to know exactly how this particular breach occurred. They're not saying their policies and procedures would tell us how they have set up the barriers, which hopefully exist between their developer resources and their production services.
Leo Laporte / Steve Gibson (00:21:37):
Yeah. You hate to think that you, that it's so easy that all we have to do is social engineer, one person, and then it's all gone. Right. And Leo, just look at what we just learned about the way Twitter operates. Yeah. You know, it's like crap. Okay. But, but then you would also need to know that same thing about the password manager you were considering switching to again, an emotional decision needs, no justification. Whereas a rational decision is only about justification. Now. I've always been careful to draw a clear distinction between policies and mistakes policies are deliberate mistakes. Well, they're mistakes when you're an employer, for example, and this is the example you and often used Leo, you know, and an employee screws up, do you fire them because they screwed up or do you consider that they made a mistake and have learned a valuable lesson from it?
Leo Laporte / Steve Gibson (00:22:39):
You know, if, as a consequence of having made a mistake, they're now a better and more valuable employee, why give them to your competition? So, you know, unfortunately we don't know enough about the inner working as a LastPass to make an informed decision about switching, you know, should we now be more or less afraid? How does their actual policy and behavioral security after this incident compare to the actual security available elsewhere? Well, and there's an interesting comparison because it's believed that the same nation, state hacker who did the Twilio attack we know door dash was attacked by the same guy they say, yes. But Okta signal and LastPass all at all breached roughly the same time using similar social engineering attacks. So, but who, the one who wasn't but was attacked, was CloudFlare. Remember this, you had this story last week.
Leo Laporte / Steve Gibson (00:23:37):
I think they use UBI keys. And because they use strong security, even the, even the, the social engineering attack worked, it didn't compromise them. Yeah. So that's, that's the that's the kind of thing I'd like to see from LastPass. Yes. Right. And, and, and in his note he was non-committal, I mean, it wa he wasn't specific, he talked about, you know, increasing their security and tightening their boundaries and things. It's like, okay. Again, it, so, so, so we have, we have an example, but again, to, to make a change, you need to know about where you're changing to just as much as you need to know about where you're changing from. So, you know, if LastPass learned a valuable lesson, that's great, but I have no idea. And neither does anyone else. Their track record is all we really have to go on.
Leo Laporte / Steve Gibson (00:24:35):
And it's been good so far because the security architecture is good. And it's the security architecture that I'm relying upon at the same time. As I said, presumably everybody else's security architecture is equally sound because none of this should be rocket science anymore. Would you re if I was changing your LastPass password at this point, would that be a reasonable response rather than changing your password manager? No. No, no. I don't see how that has any effect. Okay. Because, okay, good. Because it's the password, which is used only locally, right. To encrypt the blob, which we send there, they don't have access to that or nor they need that. They, they, they never have, they don't want it. And that was, you know, Joe's original con you know, his original concept. So if I were starting out today, all other things being equal, I would probably choose bit warden you know, being sponsor open source.
Leo Laporte / Steve Gibson (00:25:30):
We gotta say yes. That's not why you're choosing them. I'm sure <laugh> no. And in fact, you know, being open source, I'd be able to do the same sort of security architecture vetting, right. That I once did with LastPasses designer, Joe Siegrist right. As we all know, as, and as you just said and reminded us bit warden is currently a sponsor of the TWI network. And I think that's great though. It's worth noting that LastPass had never been a sponsor here at the time I chose them. Yes. I chose chose fact. It was because you chose them. I think many years later, I figured it was, came to us. Yeah. Yeah. You know, I chose them because Joe was more open than everyone else, which allowed me to understand exactly how their system worked and why it was the proper design. It's kind of ironic because if in fact, what the bad guys got from LastPass is the source code bit.
Leo Laporte / Steve Gibson (00:26:21):
Warden's open source. They, they got that already, is it right? And, and in a properly designed system, it it's should matter. It shouldn't matter. Yes, exactly. Yeah. Yeah. So anyway, many of the flood of DMS I received last Thursday asked whether I was still using LastPass. And if so, whether I was now planning to change security now podcast number 256, I love that it was two to the power of eight was dated July 9th, 2010. And it was titled LastPass security, the little summary description for it on TWI says, Steve, thoroughly evaluates LastPass explains why high security passwords are necessary and tells us how LastPass makes storing those passwords secure. So it looks like I've been using LastPass for the past 12 years. And I still am. If they ever give me a rational reason to change, I will in a heartbeat and whether or not bit warden is still a sponsor of the TWI network at the time, I would probably go there because openness matters.
Leo Laporte / Steve Gibson (00:27:29):
But, you know, so does inertia and the devil, you know, so anyway, I still using them. I, I don't see any reason to change subject to additional information coming to light. You know, there's never been a, a breach that, that, that affected our, our storaged security because of the way it's designed. Yeah. And that's what counts, you know, and that's really what counts. Yeah. And then it's a matter of looking at the pricing and the features and, you know, does it, what, what suits your, your model best? I just never have a problem with it. So it's no reason it's not, it's not irritating me. And I have a very soft spot in my heart for LastPass. Not only cuz of your support. And I used them for many, many years. But when they became the studio sponsor a few years ago, they kept us on the air through COVID.
Leo Laporte / Steve Gibson (00:28:21):
If it weren't for LastPass, I don't know if we'd still be on the air. So I have a very soft spot for LastPass. I do use bit warden. I like the idea of open source, but I think there's pretty much feature parody between most password managers at this point. Yeah. And it really it's just inertia. It's like, I there's no good reason for me to leave cuz it works. And if there, when there is, yeah, I'll be out of there, like in a hot second, but so far so good. Okay. <laugh> what's not so far so good. Is that just yesterday? The us federal trade commission? Well maybe this is good. Actually filed a lawsuit against the large data broker known as coach Chava, K O C H a V a probably most of you can go to their website.
Leo Laporte / Steve Gibson (00:29:12):
I can't, but I'll tell you why in a minute the lawsuit's complaint that is the federal trade commission, us federal trade commission's lawsuit complaint alleges that the company coach Chava offered for sale, the precise geolocation data of hundreds, of millions of mobile devices, and one wonders where they got it. We'll get to that in a second revealing, potentially sensitive information. And what the agency says amounted to an unfair or deceptive consumer practice, according to the FTCs complaint as part of its operations. This, these guys are in Idaho. Coach Chava collects a wealth of information about people and their mobile devices, including by purchasing it from other data brokers and cells customized feeds. The FTC explained that among the information it sells is precise geolocation information associated with a unique marketing ID that could be used to reveal visits to sensitive locations, such as places of worship and healthcare providers, such data can also be relatively easily tied back to an individual by observing patterns, such as regular sleep and work locations.
Leo Laporte / Steve Gibson (00:30:32):
Samuel Levine, the director of the FTCs bureau of consumer protection set in a press release, announcing the suit where consumers seek out healthcare, receive counseling or celebrate their faith is private information and should not be sold to the highest bidder. The FTC is taking coach Chava to court to protect people's privacy and halt the sale of their sensitive geolocation information. When asked about the suit coach Chavas legal representatives did not immediately respond to a request for comment, coach Chava charges clients $25,000. And I don't know if that's monthly or what, but I all, I saw that number for access to its location feed. Like what, like where is so and so right now, I don't know. And until recently offered free samples, coach, Chave attempted to preempt the action by suing the FTC early, earlier this month, alleging overreach in proposed complaints. The agency shared in July and August, like, okay, we're this is the way we're getting ready to complain about you got any comment.
Leo Laporte / Steve Gibson (00:31:47):
And so they got, they got sued shortly before suing the FTC. The company also announced a new capability called privacy block, which it said should assuage the agency's concerns by removing health services, location data from the Kochava collective marketplace. So, okay. We know what's behind this, right? This is all being allowed to occur. Well, first of all, the tracking is only being allowed to occur only because it's invisible to the consumer. If tracking was apparent, it would never have grown. So out of control, as we know, apple started requiring their apps on the iOS platform to obtain consumers explicit permission to track them outside of the app. And the result was a resounding no. So, you know, I'm glad that slimy companies like this coach Chava are finally being put under the spotlight. It's annoying that it took the Supreme court's overturning of their previous decision in row to bring this to the forefront, but better, late than never.
Leo Laporte / Steve Gibson (00:32:54):
And as I noted before, when I attempted to go to HTTPS colon slash slash www.coach, Chava, K C H ava.com to see what they were bragging about. Chrome told me that the domain was unknown. I got back DNS probe, finished NX domain. What of course NX domain is the error for there's no DNS listing for this. What then I smiled when I realized that was because I took your suggestion Leo last week and decided to experiment with next DNS. Oh, Bravo. As an advertising and tracking blocker. Obviously those guys already know about coach Chava and they're saying no. So if I know, I I'm very impressed with what I've seen so far. I, if I was curious, I could have, I quickly whitelisted coach chava.com and then gone to their site and, and poked around or, you know, changed my DNS and then change back, whatever you, you ain't missing anything.
Leo Laporte / Steve Gibson (00:34:01):
<Laugh> like, I'm just gonna tell you, incidentally, they offer a product to help you improve your apple search a performance as well. So Uhhuh, they know a lot, they know a lot. Yeah. Yeah. Wow. Yeah. So, so this is the world we're in. This is the data broker. And the question is where are they buy this information? Which brings us to the federal communications commission not to be left out though not that it appears to matter much. The us' federal communications commission has launched an investigation into mobile carriers, geolocation data practices. Sure. Mm-hmm <affirmative> Uhhuh mm-hmm <affirmative> Uhhuh last Thursday, the FCC shared responses from mobile carriers to a probe into how they handle geolocation data and announced a new investigation into carrier compliance with the commission's rules about disclosing how much data is stored and shared. Okay. So the FCCS chairwoman, Jessica Rosen Wark said in a press release quote, our mobile phones know a lot about us.
Leo Laporte / Steve Gibson (00:35:10):
That means carriers know who we are, who we call and where we are at any and where we are at and where we are moment at any given. Oh, thank goodness. Yes. I was gonna say, oh, come on. Where are we at? Where we at? We at where we are. Thank you at any given moment. Okay. I couldn't believe that was actually gonna be at the official press release. That's why the, you must use Grammarly. I'm sure that fixed it up. Yeah. <Laugh>, that's why the FCC is taking steps to ensure she says this data is protected except they're not Uhhuh. Anyway. Good luck with that. Though, I suppose this might answer the question of where slim ball coach Chava obtained the information that they're now aggravating ag. Yeah. Aggravating aggregating. I like aggravating. Yeah. Aggravating and reselling. Okay. So the commission, the FCC sent inquiries to 15 carriers, including at and T T-Mobile, Verizon GoogleFi and others last month, asking them to spell out their policies around geolocation data, including how long information was retained as well as how and why it might, oh, no.
Leo Laporte / Steve Gibson (00:36:27):
What circumstances? Like how much do they pay you? It might be shared with third parties. The FCC requires mobile companies to get this, to get consumer consent for sharing information, unless such sharing is necessary to complete a service or required by law, which is the big, the biggest loophole ever written, right? Oh, oh no. We have to retain that information in order to make our cell towers work. So we're, we can, we're allowed to anyway, unfortunately, you know, aside from that, has anyone ever actually succeeded in reading the fine print of the agreement that you click on with any of these companies and what is one to do? If the terms turn out to be onerous, you know, all the other carriers used the same fine print two years ago, as evidence of their lack of ability to actually do anything in 2020, the FCC proposed more than $200 million in what they had described as still pending fines for major carriers, for selling user location data without consent or appropriate safeguards, Jessica Rosen, war whose grammar is correct tasked the FD FCCS enforcement bureau with the new investigation, into the company's compliance with rules, requiring them to fully disclose to consumers how they are using and sharing geolocation data.
Leo Laporte / Steve Gibson (00:38:06):
Again, a lot of good that'll do since they seem unable to collect 200 million in still pending fines from two years ago, you know, I would just say, pull the plug and get their attention, but that'll never happen. Justin. Brookman the head of tech policy at consumer reports said that nevertheless, quote, the quality and specificity of answers that the FCC received as a result of their inquiry definitely ranges among the respondents. But there's some interesting concrete information in there, especially on data retention periods. However, not surprisingly, in some cases, the responses simply referred to their dense, publicly available privacy policies. You know, it's like, yeah, go see the fine print. That's what everybody already checked. But some others did answer questions directly at point by point that you know that Justin, this consumer reports guy agrees with me that transparency isn't enough. He said, people have no choice, but to share very sensitive data like geolocation with mobile carriers, for those products to work, there should be substantive constraints on what they do with that information and for how long they keep it.
Leo Laporte / Steve Gibson (00:39:25):
You know, so what I wonder is in a world where that information can be sold to third parties in real time, that is, you know, it's not like it's being typed up or printed out and emailed in boxes somewhere. It that they, that information can flow out the moment it's captured and where it's timeliness makes it a, it valuable. It's unclear to me whether retention time anymore matters at all. That sounds like, you know, pre every communications is free sort of time scale, Harold Feld. Who's the vice president with a company called public knowledge, also called for regulatory actions saying the FCC should set new rules of the road for mobile carriers, privacy. He said, quote, these letters show that despite the constant invocation of industry standards and best practices, carrier geolocation, data practices are all over the map. For example, the length of time carriers retained location data as determined by proximity to cell towers ranged widely and as long as five years in the case of at and T.
Leo Laporte / Steve Gibson (00:40:46):
So my feeling is unless we make them delete it, they're not going to, but again, if they're allowed to sell it immediately to third parties, retention time, no longer matters at all. They claim that they must keep it for business purposes and to maintain the health of their networks. Fine. Simply outlaw its sales to any other entity period, but that's not gonna happen. The FCC appears to be toothless to me. They completely seated control over broadband privacy during Trump's administration. And while the FCC still theoretically has substantial regulatory authority over mobile phone carriers, the carriers appear to simply be ignoring the FCC. So I don't know it would be nice to have something happen at the federal level. Maybe it's gonna be at the state level, which brings me to California in very late breaking news. Only a couple hours ago, tech dirts, Mike Masick reported that.
Leo Laporte / Steve Gibson (00:41:53):
Who was he? Mad, bad. Ooh, babies. He mad <laugh> and I don't blame him. <Laugh> yes, he is the California state Senate just passed what he described as three horrific new internet regulation laws, apparently written by bureaucrats who have no idea how the internet works since this just happened. I haven't had any chance to look into it, but if it's interesting, we'll talk about it next week. And we'll talking about, do you more Leo? Yeah, I know all about it. We'll be talking about it tomorrow and on twig. It, it is one of those, you know, things where it sounds on the surface to be very good, New York times published an article about it, you know, essentially saying, yeah, it's good to have privacy. It doesn't understand how the internet work. It's not gonna solve the problems that's intended to solve. And in fact, it's probably gonna make a worse and it's certainly gonna be an onerous burden for us because any well, one of the laws is to protect child people under 18.
Leo Laporte / Steve Gibson (00:42:58):
But in the COPPA, the child online privacy and protect prevention act protects kids under 13 only, but against sites that are aimed at kids, this affects all sites. So if you think an 18 year old might visit your site, well guess what they do, they do. Then you have to do a number of things to protect them, including <laugh> age verification of what you have to make sure that nobody is under 18, who's visiting your site, or if they are that you mitigate any hazards to them. Well, Mike's point is, well, you're asking us to figure out how old people are when they visit the site. Every single visitor, every single and collect that information. That's not exactly privacy forward. No, nor does it protect anybody. So this is, I think your summation is exactly right. Written by bureaucrats who have no idea how the internet works.
Leo Laporte / Steve Gibson (00:43:52):
It's politically probably very popular, cuz it looks good. Looks like it protects children and protects. Privacy does not. Anyway, we'll talk about it. And 100% of the Senate voted for 33 to nothing. Yeah. Nobody voted against it in California. Now the last butchers against this will be the governor. And what Mike's hoping, I think a lot of people are hoping is that governor Newsome will, will hear from people like Mike Masick and say, oh yeah. And maybe that he's he's tech savvy enough to understand, you know right. What this means, what, what people like the New York times say will the tech giants don't like it because of course they want to collect more information about us. But imagine the thing is it's, you know, Facebook already knows how old you are. Google can easily figure that out, but security now grc.com TWI TV.
Leo Laporte / Steve Gibson (00:44:44):
Do we wanna start collecting age information about everybody who visits? No. And in fact, when I set up GRCs forums, I ex I explicitly removed that from the signup sheet and from any criteria. Cause I didn't wanna ask for it. I don't, I don't wanna know. I don't care the legislature's response to Mike as well. You know, <laugh> we don't ha the ag, the California attorney general gets to decide who's prosecuted. He's not gonna look at twit and say, oh yeah, this is a hazard of 18 year olds, but Mike's point is well great. So now you give the ag a tool that if he doesn't like somebody, he can, he can attack him. That seems like on the basis that they're not collecting a, a visitor age information. Right. Right. Yeah. Well, we'll just add that to the cookie banner. Leo, we'll just add another field just like that.
Leo Laporte / Steve Gibson (00:45:32):
No. When, by the way, when year were you born, all of a sudden, if you start collecting age information, now a whole range of GDPR regulations apply to you because you are collecting personally identifiable information, right. So it opens you up this whole can of worms. Anyway, don't get me started. I agree with that. Lori's been talking about New Zealand lately. Yeah. Sounds better and better <laugh> and by the way, no internet presence. <Laugh> <laugh> just stay off the internet. It's a bad idea. Okay. let's take a break. Then we're gonna talk about I'm gonna share some pieces of a conversation with a ransomware hacker or attacker that I think everyone's gonna find very interesting. Very interesting. Well, this is actually something that Jessica Rosen, morsel and all the folks at FCC might want to use, come to think of it.
Leo Laporte / Steve Gibson (00:46:23):
<Laugh> maybe they do use it. And that's why she says <laugh> she doesn't say we know where you're at, wherever they at. <Laugh> I'm talking about Grammarly. We love Grammarly. We all use it here at twit. As your fall schedule starts to fill up with obligations, more emails in the inbox. You, you start to think anything to save some time would be a big help. Grammarly is a very important tool for anybody who writes. And I don't mean writes novels. I mean, even if you send emails, cuz it's all about making your communications clear and concise and accurate. So yeah. It'll keep you from saying, I wonder where they're at. <Laugh> sure. It'll it'll say, you know, you might wanna rephrase that, but it'll also say that might have been a little bit Bruss. I th this is one of the things Lisa loves about it in her email.
Leo Laporte / Steve Gibson (00:47:17):
She's the boss. She writes one line, one sentence emails, you know, all bosses do that, but, but Grammarly will from time to time say, oh, you know, that sounds a little bit harsh. Maybe you wanna add a little softener to that. And Lisa appreciates that because she's, you know, she's trying to get things done, but Grammarly just keep, it's kind of like, there's somebody on your, over your shoulder going, you know, you probably don't know how that sounds to other people, but it doesn't sound good. Whether you're doing emails, reports, presentations, writing articles, you'll finish your work quickly and confidently with Grammarly. I was always, I'm the kind of guy said, oh, I, my spelling and grammar. Perfect. I don't need those things until I start using Grammarly. And I realized, it tells you a lot of stuff about your writing doesn't have to do with correcting necessarily.
Leo Laporte / Steve Gibson (00:48:07):
But for instance, you could say that more concisely or, you know, you're writing that at a very high grade level. Maybe you wanna make it easier to understand for people. You can try it for free. It's free to download. It works where you do. In fact, you can even go to grammarly.com/security now, and paste a paragraph in. If you're just curious, what will it say about this paragraph? We should actually paste the FCCS statement <laugh> into there and see what it says. So you can just use it that way. The free version of Grammarly covers comprehensive spelling, grammar, and punctuation. Now, as, as good as I am at spelling and grammar, punctuation is always a challenge for me. Did I need a comma there? Should I put another one? Should I take one out? And partly that's cuz in the back of my head, I think in my eighth grade English teacher, he said you've committed blunder and I oh no.
Leo Laporte / Steve Gibson (00:48:58):
So <laugh>, Grammarly's nicer than that, but it will help you instantly proofread provide suggestions. Your writing always comes across as professional and mistake free. It's it? You know, there used to be in the old days of magazines and newspapers, you'd have a copy editor, somebody who would go through your stuff and just make sure you don't make any, you know, obvious blunders. This is like having a friendly copy editor at your Beck and call that's the free version. If you go to PR Grammarly premium, the, and which is what I use their clarity focused sentence, rewrites help keep your writing clear into the point. And that's what I really find valuable saying that was a little awkward that sentence. Or you could do that in a more concise way. So you get through work emails quicker. You, you make your point more clearly, cuz that's really it's about cation, right?
Leo Laporte / Steve Gibson (00:49:47):
And it helps you be a better communicator and you can get back to the stuff you need to do. Get an instant take on how your message comes across with grammar. Lee's free tone detector. So you always make the right impression. That's a very useful thing. And I I'm gonna tell you every once in a while, I'll see an email from Lisa and I go, whoa, ow. But I'm not gonna go to her. Say that. I ain't gonna say that I'm no fool Grammarly does it for me. I like that. Get more time in your day with confidence in your work and do it with Grammarly. G R a M M a R L Y grammarly.com/security. Now you can sign up for the free account there, but when you're ready to upgrade to Grammarly premium, we'll get you 20% off just cuz you listen to security now 20% off Grammarly premium or try it for free grammarly.com/security.
Leo Laporte / Steve Gibson (00:50:37):
Now I, you know, I understand people go, oh I don't need that. I don't need that. Try it. Just try it. I thought the same thing. And then I went, oh I do need that. That's great. Grammarly.Com/Security. Now back when I was writing the tech talk column for info world I as all columnists had a copy editor. Yes. mine was a great guy named Michael Miller. Oh I know Michael. Yeah. Yep. And he once said to me something that is, it was like what? 30 some years ago. And it's just stuck with me ever since he said, well, Steve, you know, mostly I just go through your columns, searching for the word witch <laugh> and I change, I change them to that because you're you, you do that. I go, oh. And so of course I've been self-conscious about it ever since I, I like the word witch and sometimes it seems better than you either use, which I, I don't know if it's the same Michael Miller, but I think it is.
Leo Laporte / Steve Gibson (00:51:39):
He became editor in chief of PC magazine. We were talking about him this morning as a Miller that's Michael Miller, great guy, Michael Miller, really like him. And he's done very well since I don't think it says in here former copy editor for Steve Gibson. Oh he'll know, <laugh> <laugh> for eight years. He had to go through with which his, which thank God he had copy and replace. Yeah. find and replace. He was, he was a great guy or he is a great guy. I really like Michael. Yeah. Yep. Yeah. So the guys over at the publication, the record had a lengthy conversation with a Russian ransomware attacker by the name of Michaelle, Matt Bev. Interesting. And all, although I didn't think that much of the, oh, I didn't think that much of the conversation, which revolved around a lot of the squabbling among adversarial ransomware groups would be that much interesting to our listeners.
Leo Laporte / Steve Gibson (00:52:36):
Maha's answers to a couple of the questions were interesting. So I've selected a few bits out of that longer conversation to share. And I should mention that this is a translation from Russian cuz the conversation was held in Russian. So the semantics will be a bit non-English and I've also edited a bit since this young man's choice of descriptive language was a little bit blue. So it's you know, it was not, not safe for work. Well, he is a hacker. I mean, come on. He is, he is. And yeah, I didn't have a problem with it, but you know, we got a large listing audience. Yes, no, I appreciate that. We don't want to have to scan your face to find out how old you are. No Dimitri from the record asks how often do people from different affiliate programs compete in the same network to extort victims?
Leo Laporte / Steve Gibson (00:53:27):
Mm have you had such situations? And in other words, Dimitri was asking, are there ever collisions among different attackers and Michale says, this happens often <laugh> especially when, what, especially when several people own the exploit or pour logs from the same traffic market. If we are talking about extracting initial access credentials with a Steeler, he says, I took some source codes. So called proof of concept from GitHub and modified them. If you remember, there was a well known CVE for the Fort net VPN. We found it with one programmer from the forum based on the list of IP addresses, we got approximately 48,000 entry points. I was very surprised then really shocked, but we did not even work through 3% of this list, not enough time. And when others, well let's say our competitors began to use this vulnerability. There were intersections across networks. I often went into a network already locked.
Leo Laporte / Steve Gibson (00:54:39):
And by then, by the way, when he says locked, that's his term for encrypted? So, you know, so he, he went in and everything was all of the servers were already encrypted. So he says, I often went into a network already locked by someone and didn't touch them because it's not my job to encrypt for the second time. But some guys overlock networks, they come in and see that it is encrypted. And so that nobody gets it, they encrypted again, there were cases where the guys and I just crossed paths on the network during development exchange that is development of their, of their presence in the network, exchanged contacts and somehow discussed what to do next. We basically always agreed. And it even happened that we then jointly did some other projects in the summer of 2022. That is this summer. He says, this happens all the time because everyone is hungry for the material.
Leo Laporte / Steve Gibson (00:55:44):
How could we get to the initial access? Actually, there aren't many options. There are vulnerabilities such as RCE, you know, remote code execution in various products of VPN devices. Everything that can give access to the network or a network access login from Steelers. But basically everyone is now flooded from traffic exchanges and there is little unique traffic and those who have it, they pour just for themselves or are already working in some teams. So it's absolutely normal that there is a conflict of interest on the networks and now it will be even more. Okay. So I thought Maha's comments that they were only able to exploit 3% of the list of 48,040 net VPNs because there's not enough time. In other words, he's saying there really is an active race when a new patch drops and a proof of concept is made available for something like a critical remote access vulnerability.
Leo Laporte / Steve Gibson (00:56:58):
So, you know, these credence are actively watching everything waiting for the first glimmer of a newly discovered problem. And they realize that there is gonna be a lot of the systems patched quickly. So they're not wasting any time and significantly. They are not finding any of these problems themselves. These are not high end security researchers gone bad. They're living off of the interval in the delay to patch. They're not good enough to find the trouble themselves, but they are good enough to quickly weaponize a working proof of concept. When it's posted to GitHub, then immediately turn around and employ it to gain entry wherever they can. And the, the, basically what he's saying is there's now a lot of them all basically competing for access to re to, to opportunities that appear whenever they do. And so it's who can get in there first. So Dimitri asks, tell me about some attacks that stood out to you, which was the fastest, how long did it take from the first penetration into the network to receiving the payment?
Leo Laporte / Steve Gibson (00:58:27):
So Michale says there were many interesting ones, but I would like to sum it up before talking about the attacks. There are small networks, there are medium networks and there are very large networks. And I'll tell you it's much easier to work with a network of an organization with $1 billion of revenue than in a network of an organization that has income of 9 million. I'll tell you why. There are many more computers that are easier to hide on and easier to navigate than in a small network where you are limited. You have to move very fast. And when I started my career, <laugh> I love the word career. It's like, this is a career. Okay. When I started my career, I started with blue, keep a vulnerability and Microsoft remote desktop. I hacked five small networks per day because I had to go in and do it right away.
Leo Laporte / Steve Gibson (00:59:31):
But as I progressed, the time I spent on the hacks increased, he says my longest development, probably everyone has heard about the Capcom company. I got there through a Fort net vulnerability. As a matter of fact, when I went there, I was a little surprised that everything was in Japanese. There is no hierarchy, there's no division into departments and they have everything in a big heap. I found a dead domain admin. That is how the name Bauch, which is one of his monikers appeared. He said, Capcom had an admin BA back or bamboo. And when I found this administrator, I realized that no one uses him, but he was an enterprise type. Okay. So Michaela is explaining that he found an abandoned, active administrative account, which he was able to use. And he took Bauch as one of his, several aliases from then on, he said the fastest attack in my life happened.
Leo Laporte / Steve Gibson (01:00:38):
As soon as I got the proxy log on vulnerability. At that time, I had a programmer on a grant who was finalizing the exploit. One of the interesting networks was a logistics company in the Netherlands, large warehouse, very large warehouse. I got in and immediately obtained the domain admin tokens. These guys weren't very secure, conscious, and didn't worry about anything. I remember I went there at 8:00 PM Moscow time and at about 4:00 AM Moscow time. So that was eight hours later. He says it was already all locked up. Meaning he'd encrypted the works. He said from 6:00 AM. The administrator wrote to us in a panic to which I told him, bro, wait for the supervisor. So anyway, he's saying that someone who realized some, something was wrong and Michale didn't want to talk to an underling. So he said looking around the network, everything seems to be simple and clear.
Leo Laporte / Steve Gibson (01:01:49):
They have an administrator's domain for us. The password was the same for everything. Oh boy. On Uhhuh, on hypervisors, on a backup server in the work group, everything. After analyzing the network, I found a w I M you know windows backup system. I could get all the passwords from it, right? Because, because it's an offline backup, he says, and thereby got all the backups. Although their backups were so bad. <Laugh> he said, he said they just, they just backed up to the NAS. He says, I went to the NAS and formatted. It went to ESXi encrypted. And then after about an hour, he wrote to us. So he says the admin wrote right at midnight, he said, I would like to resolve the issue. I said that the issue could not be resolved because he was not a boss in the morning.
Leo Laporte / Steve Gibson (01:02:53):
He, this is Michaela in the morning. I had to fly to another city. I remember sitting at the airport, the company writes to me $2 million transferring 2 million. He said, I have never had such an amount in my wallet. Wow. I get on the plane realizing that I have a laptop with $2 million. He says, well, I gave them decors. And when I arrived, I opened the chat. He says, dammit, something is not right there. They just yell. You destroyed VMD. K. He says, of course that's the, the, the file format, right? For, for ESX, I virtual machines. He says, so there screaming at him, you destroyed VMD. K. He said, I tried to figure it out and asked for VMD K samples. But the VMD K files are zero K bites. Ooh. That's not good. So he writes, everything is screwed. I am writing to this developer who created the exploit for me?
Leo Laporte / Steve Gibson (01:04:02):
How could this happen? He says, well, I don't know. He said something broke. Nice. <laugh> these are quality people we're talking. Yeah, I, you and they a, he says, and they asked to return the money. Well, he said we had no choice, but to block them. <Laugh> great. So he said, we scammed them for this money. I still blame myself for this. It was the fastest and most solvent attack I've ever done. Besides the fact, this guy is an absolute SC bucket. The thing that really strikes me is how he invulnerable. He feels he's, he's confessing to at least two major crimes Capcom in this Dutch warehouse. Yep. With absolute impunity, the Russians don't care. Yeah. And, and he says something in a minute that I just, I, okay. So Dimitri says, how do you see the ransomware industry in three years, will ransomware remain the best monetization model for cyber criminals?
Leo Laporte / Steve Gibson (01:05:08):
Or will they move onto something else? Michale says, it's like how carding used to be popular. And there was a lot of money in it, but now it's dead and ransomware will soon die. Not in three years, he says, but sooner he says, and I disagree with that, but we'll see, he says literally everything. Now, this is interesting. Literally, everything has changed over the last six months. And remember where he is. He's in Russia. He says since the beginning of the special operation in Ukraine, almost everyone has refused to pay. Oh, good, good. He says, I often encountered people who wrote to me in the chat. You are a Russian occupier, be content with $10,000. And we won't give you more. At least take that. Zoe. He says, return on investment has completely fallen in the last six Boohoo, what investment? Geez. I know return on investment has completely fallen in the last six months.
Leo Laporte / Steve Gibson (01:06:24):
He says it became difficult to work in general, poor baby. He says, if it dies, meaning ransomware, it dies. You need to come up with something new, but ransomware is worse than heroin. Mm-Hmm <affirmative> I haven't tried heroin, but I've seen people who are on it. And I'll tell you, this ransomware is worse than drug addiction. There is so much money anywhere. Oh, there, there is no such money anywhere as there is in ransomware. I know I even compared it to drug dealers from Hydra, the world's largest dark net marketplace, which was shut down this year, they earn less than we do. Okay. So he's calling this earning money. He says, and he, he, he finishes, but at the moment, ransomware remains the leader in monetization. There are no other schemes on the internet that would carry more monetization or I don't know about them yet.
Leo Laporte / Steve Gibson (01:07:30):
Mm-Hmm <affirmative> so, you know, as I read that, I'm struck by how casual yeah. Michaelle is. Yeah. About being a criminal, you know, there's an utter lack of morality. You know, he, he did fear. He did appear to feel badly that his DEC, his DEC descriptor didn't reverse the encryption of the large warehouses VMD K files. So he got 2 million without returning their data. Oh yeah. He feels bad. Yeah. Well, and he had to block them cuz they were screaming at 'em. Yeah. So, but, but what seems to be utterly absent is the idea that extortion itself is wrong. Right. You know, he, he talks about it as a career. Like it's a legitimate profession that he's in like, like his parents would be proud <laugh> you know, as though if you have leverage over someone using that leverage for your own personal gain at their loss is acceptable.
Leo Laporte / Steve Gibson (01:08:30):
Horrible. So anyway, I thought that everyone would find this interesting. These guys are not geniuses, they're computer savvy. They use other people's tools to force those abroad. Meaning as not in Russia to give them money. Yeah. They're like criminals anywhere. They have no zero moral compass and I'm sure justify it in their mind and oh, it's horrible. Yeah. So, and you know, and I just don't cover the continuing ransomware problems, but I mean, it is because I know our listeners are like, yeah, yeah, yeah. But I mean, I, I, I skip over story after story. Oh yeah. After story, same with breaches. I don't even bother about talking about breaches anymore. Yeah. It's not stop. Yeah. Hmm. So a bit of good news. The privacy centric duck, duck go has had what it calls an email protection service in beta since July of last year.
Leo Laporte / Steve Gibson (01:09:31):
So more than a year, but they've just opened it to the public. It looks like a very useful and completely free service. So our listeners might wanna jump over and grab their name or their favorite handle quickly before it's taken. So I'll explain how to do that first. And I'll tell you why this seems like such a nifty service to register, go in a web browser to duck, duck go.com/email. If you don't and you probably won't currently have their browser extension installed, you'll need to do that first. You can remove it later since it's not required to use the service once it's set up, although you do need it to manage the service. And there's some cool management stuff. I'll explain in a second. So you'll be asked to provide a username which has not yet been taken and it will become sort of your base or default@duck.com email address.
Leo Laporte / Steve Gibson (01:10:30):
So what, whatever name or handle you choose@duck.com will be your default email address. You also provide an email address which will receive cleaned and formatted and forwarded email. Okay. Oh, and so after you install the, the, the browser extension, go back to duck dot, go.com/email. Now it'll say, ah, and then you'll be able to set up your account. So what does all that get you? Their email protection is duck. Duck goes dedicated email forwarding system, which strips advertising and profiling trackers from email links, scripts, images, media, all that crap before forwarding them to your registered forwarding email. When you receive the forwarded email, you'll also see a short report which has been added to it, of how many trackers were removed, which companies were responsible for their injection into your email and more duck. Duck go says that after a year of running the beta program, 85% of all emails on the tester, on their testers, their beta testers communications contain trackers of one form or another.
Leo Laporte / Steve Gibson (01:11:52):
So at that point, anything sent to your username@duck.com will be forwarded after being cleaned and reformatted. And in a very cool feature. Email protection also provides users with unlimited disposable and dynamically manageable private addresses to use on sites. You want to supply with a per site or not your primary email address. These can later be deactivated if spamming to that address becomes a problem. And you can ask for as many of these throwaway email addresses as you need. And of course using unique email addresses, confers some of the benefits of using unique passwords on sites, you know, in the event of a website's data breach, the link ability of your identity to any other of your identities online will be dramatically reduced. So messages passing through duck dot go are never stored by duck dot go. They make that very clear while what small amount of accounting and forwarding information is kept for operational regions is deleted within 30 days after the account's closure.
Leo Laporte / Steve Gibson (01:13:14):
So if you close the account within a month, it's gone no long term footprint. And even though email is forwarded to your real email address, it's still possible to reply to those emails, which will then come from a duck.com address. So this could be useful where anonymity is U is, is would, would be important. So it's a hundred percent free. It has a user friendly dashboard for quickly configuring forwarding addresses and making on the fly changes. You can manage account settings and all that. In addition to a browser extension, there are apps for Android and iOS, which allow for the same sort of dashboard management in those apps. So, okay. I still don't like the name, but the service seems pretty cool. Since I run my own server, you know, at grc.com, I'm able to, and I do create tons of email addresses, I mean, email aliases.
Leo Laporte / Steve Gibson (01:14:17):
So that exactly for this purpose. So I'm giving somebody, I'm not sure about an alias and if I ever start getting spam there, well, first of all, I know where it came from and I'm able to terminate the alias. So this is that sort of a service which in addition to that is filtering email to remove tracking crap from it. So anyway, seems like a neat deal. We know duck dot go and that they really are privacy centric. So I wanted to make sure everybody knew that this new service had just come out of beta.
Leo Laporte / Steve Gibson (01:14:51):
Okay. Another big IOT mess. And each one is of these that we talk about is a lesson. I'm not gonna get preachy because I know that can get tiresome, but the state of the T industry brings my blood close to a boil every time here's, what's going on this time, the cybersecurity firm, CMA C Y F I R M a recently published a report describing a long and still outstanding security threat created by insecure inter. And these are like commercial grade internet surveillance cameras produced by a us based firm, hick vision. H I K V I S I O N. They're located down here near me in Southern California, I think city of industry anyway, one year ago, a year ago in September, 2021 in response to a discovery by security researchers, which was given CVE 20 21, 36, 2 60 hick vision did the responsible thing.
Leo Laporte / Steve Gibson (01:15:57):
They published a firmware update to correct a serious vulnerability. Unfortunately, it's for a camera. Okay. The researchers discovered that the hick vision cameras were vulnerable to a critical command injection flaw. That's easily exploitable via, especially crafted messages sent to the cameras, vulnerable web server, which is what it exposes to the internet. Okay. So that was then today, SIFI analyzed a sample of 285,285,000 internet facing hick vision camera, web servers. They found that today a year later, roughly 80,000 are still vulnerable to exploitation. And this of course is the problem. Some contractor you've hired purchases, a camera or 50, and installs them. They set them up, send you an invoice and move on to their next job. Meanwhile, you have some number of web servers on your network, which can be taken over remotely. And the takeover is not theoretical. There have been two known public exploits for this CVE 20 21 36, 2 61 was published in October of 2021 and the second in February of 2022.
Leo Laporte / Steve Gibson (01:17:32):
So that's known public exploits published, meaning this is exactly what Michaela is sitting around in Russia, waiting to see pop up on the internet. And he jumps on it in competition with all of the others of his ilk in December, 2021, a MIRI based botnet called moat used one of those two publicly published exploits to spread aggressively and enlist those cameras into DDoS swarms, which generating those record break DDoS attacks, which now force everyone who needs to remain online to move behind and pay for DDoS protection. Exactly these kinds of O T devices. It may include thousands of compromised H vision cameras. There are 80,000 available today in January of this year. Siss a alerted that that CVE 20 21 36, 2 60 was among the actively exploited bugs in its list. Siss a warned organizations that attackers could take control of devices and that they should be patched immediately.
Leo Laporte / Steve Gibson (01:18:46):
Yeah, they should have been patched last September. How that work out as I noted those 80,000 still vulnerable surveillance cameras were just recently enumerated. The cameras are very popular and they appear to be industrial grade. As I said, hick vision has an impressive looking website in CFIs report. They tracked those 80,000 vulnerable IPS back to 2300 organizations across 100 countries. None have applied the security update, which is now nearly a year old CFI report notes that Russian speaking hacking forums often sell network entrance points, relying on exploitable, hick vision cameras that can be used either for bot netting or lateral movement to gain entrance into the organizations where they're deployed. Like I said, just what Michaela is looking for. I have a chart in the show notes showing that geo geographic breakdown of the camera's locations, most of them are located in China because it's a Chinese company.
Leo Laporte / Steve Gibson (01:19:57):
So not surprising. Yeah. 12,690 of them. And the United States has the second, most 10,611 while Vietnam, the UK Ukraine, Thailand, south, South Africa, France, the Netherlands and Romania all count between 7,000 and 2000 vulnerable endpoints each. So wow. Lots of vulnerabilities in those companies. You might be interesting to know that it is controlled by the Chinese government. It is not, I mean, it's a private company, but the majority of shares are controlled by the CCP and Uhhuh. It is used in many police surveillance systems all over the world. <Laugh> I was wondering about that too, because you know, we don't even talk about if you compromise that you obviously, you can see whatever those cameras are seeing. That's the least of it though, right? <Laugh> yeah, yeah, yeah. Leading the future of I O T they say they proclaim. I know God. Yeah. So the CR credential lists for those cameras pop up in hacking forums often.
Leo Laporte / Steve Gibson (01:21:05):
And, you know, I still doubt that the public at large understands the danger. That's represented by the casual attachment of high tech devices to their network. As long as that remains true purchasers, you know, won't know that they need to consider the operational life cycle of such devices. You know, we've all been trained now about OS and smartphone updates, but there's no, there's just no awareness that your thermostat needs to be updated. If, if some third party is not taking care of that for you. So we really are in the wild west of, of internet IOT.
Leo Laporte / Steve Gibson (01:21:50):
Okay. Over the past weekend, I posted two status updates to the GRC dot spin, right.dev news group. The first posting had the subject Friday night update. And I wrote gang. I just finished the complete read through of spin rights. Dynas stat system. That's, it's like the core of its data, recoveries stuff. I wrote. I've been slogging my way through it for the past week or so. It's extremely involved. And it was working once I wanted to be certain that I hadn't done anything to break it with all of the changes I've made, the IO driver abstraction and the relocation of several working buffers into high memory, since they did affect the SSTA code deeply, I've had to work my way through every code path. It's still going to need extensive testing. But that will be joyful since it will mean that spin right is essentially working and just needs to have the final bits of debris eliminated with this done.
Leo Laporte / Steve Gibson (01:23:02):
I now need to finish the comparatively trivial task of updating the rest of spin right's main processing loop, the data inversion media testing, et cetera. And then it will be ready for the thorough testing of all of its main debt of its main data recovery loop. But we're definitely getting tantalizingly close. So that was Friday night, then Saturday night update. I wrote, okay, I'm done. This is not to say that I have any mail <laugh> I have E I have mail. Thank you very much. This is not to say, I wrote that I have any illusions that it could possibly run yet. There's no possibility, but I have finished working through all of the code and now it'll be up to spin, right? To show me where it's not yet ready for prime time. What I plan to do next is to get it actually running so that it would appear to the casual observer to be working.
Leo Laporte / Steve Gibson (01:24:04):
That'll still be a chunk of work since I've deliberately not allowed it to begin execution. It's certain to explode fabulously, but before long, it won't be exploding anymore. When it runs at that point, when there's no longer anything obviously wrong, I'll verify that it's actually doing something useful and that all of the various data recovery paths, several of them knew are working as they're designed to, and then it'll be done. So I just wanted to share it with everyone here who is not following along with the blow by blow in the spin ride development group, where things stand tonight after the podcast, I will begin running, spin, right? And fixing everything that doesn't run since as far as I know it all should, once everything appears to be running I'll then begin the work of carefully inducing, various sorts of media read and write failures and carefully watch spin right deal with each type of problem to make sure it's doing the right thing.
Leo Laporte / Steve Gibson (01:25:13):
And by amazing coincidence, a listener of ours, a Emil Khan sent me a Twitter DM, which I saw this morning. He said, hi, Steve, love the show. Been a regular listener for 16 years. Now, check out this video of John Carmack, talking about the importance of using a debugger while you code. So the YouTube video that am Emil linked to is an interesting 50 minute conversation with the, of course, legendary coder John Carmack. I have the link in the show notes and it's our GRC shortcut of the week. So grc.sc/ 8 86, that'll bounce you over to the YouTube video. What I learned by watching the video to my surprise is that John and I code in exactly the same way that is with exactly the same philosophy at our listeners will remember that at the beginning of my return to working on spin, right? Everyone heard me talking about setting up a comfortable and smooth debugging environment before I did anything else.
Leo Laporte / Steve Gibson (01:26:28):
And you've heard me mention it over and over. Since then, my wife, Lori lived with me grumbling about that for several months, while I struggled to get everything working exactly the way I wanted. In my case, I was, it was challenging because my target environment for the debugging was Ms. Dos. And to do the sort of debugging I wanted to do, I needed a real time link between a state of the art 64 bit windows machine and a 16 bit real mode dos machine. And that has become much more tricky to do as the years have separated those two worlds. Anyway, I thought it was interesting that John's code writing philosophy and mine are the same, rather than trying to guess what's going on rather than attempting to debug in our heads. We both immediately go to the debugger to watch the code execute step by step.
Leo Laporte / Steve Gibson (01:27:28):
As I often noted here, something about the programmer's ego prevents us from seeing what the code actually does. We see what we want it and expect it to do right up until the debugger slams our face into the reality. At one point John notes, that tools that are easy to use get used, whereas tools that are difficult or cumbersome tend to only be used as a last resort. He and I have apparently both learned the lesson that having a comfortable and easy to use debugging environment is the way to get the best possible code written. So thank you, Emil, for sharing the link to that conversation. And for any of our listeners who are interested, grc.sc/ 8 86.
Leo Laporte / Steve Gibson (01:28:22):
Okay. Oh, and a couple more little bits of closing the loop Vlad. Veek he tweeted, hi, Steve. I have an update on this. I pressed, oh, actually I was on, on, on an update from last week. He said I pressed cyber reason to clarify whether the escalation of privileges would've been successful. If the users were not part of a local administrator group and they confirmed it. And then he sent me out a, a LinkedIn link to their dialogue and he said, might be good to mention on next security. Now, even Microsoft is saying that removing admin privileges makes over 90% of attacks ineffective. So anyway, so what, what this guy sent to cyber reason who we were talking about last week, he said, very nice report. Thank you. However, may I ask why you did not mention recommendation for computer users not to be assigned administrator privileges as one of the key controls, protecting them against the escalation of the attack.
Leo Laporte / Steve Gibson (01:29:32):
If an attacker is not member of local administrator group, then running FOD helper dot XE, which we talked about when we did this whole walkthrough of, of, of the, you know, the analysis of the attack will not give attackers the administrator privileges by bypassing UAC. Am I correct? He asked cyber reason to their credit replied. They said thank you. We should have previously addressed that. The point of the article is not to be exhaustive in terms of recommendations. In the case involving Bumble B users were already in administrator group and UAC bypass worked, but you are correct. Users need to be an administrator group. The article is focusing on postex exploitation. The recommendations list is not exhaustive. So I thought that was interesting. Remember that we we've talked about the way, the way Microsoft has basically compromised the, the whole problem of being of running as a non-privileged user, but not making it burdensome to get root or admin privileges, you know, in a, in a traditional Unix or Linux environment, you are typically running, not as the root U user.
Leo Laporte / Steve Gibson (01:31:03):
You can do lots of things, but there are certainly low level admin things where you need to log off as the user or upgrade your rights using Linux and Unix commands to the root privilege in order to get something done. And you're able to run a single program under those privileges, the way windows does it is they, they developed this notion of a split token where you, you actually have two different security tokens. You're running with one with lesser privileges usually, but that's what the UAC does. The, the user access control is to switch you dynamically to the, the, to the admin privileged token. So his point is, and it's is really worth remembering and highlighting. It's not, it would be interesting to try running windows without the ability to elevate. I know you can, but the typical end user would probably find it more annoying than it was worth that than, than, you know, was worth the trouble or worth the added security.
Leo Laporte / Steve Gibson (01:32:15):
Maybe not. So the enterprise user where, you know, they're not supposed to be making deep change to their system. So, so removing the ability to elevate by, by taking them out of the admin group that's worth remembering as a possible way of, of mitigating as Microsoft has said nine out of 10 of the attacks, which do require admin elevation and finally ed MKR who is his Twitter handle is, oh, well damn, 2010. I dunno why he's at high Steve FYI. I canceled my last past premium subscription today. He said, Peren due to the recent close call security breach. He said, I've had LastPass since they were a sponsor on TWI. You gave your thumbs up to their software slash encryption and before log purchased the company, I'm trying to limit my exposure with my password managers, plural. And we'll see why in a minute now to just one I've used passwords plus from data vis SIDS version 1.0, oh my God.
Leo Laporte / Steve Gibson (01:33:33):
When it was sold on a five inch floppy disk, I'd used rod 13 for password protection, I believe. Did we have passwords? There was only five Leo that's when you went well, we know that yours was, we know that yours was monkey. Yeah. When, when, when data VI was version one. Oh, wow. I, I didn't know we had passwords, but I guess we did anyway. He said they recently stopped all support for their product. Okay. Yeah. And their CEO decided not to move over to a subscription option to keep it to in order to keep it profitable. Good. Good. So people stopped using data vis I guess and really, where are you gonna stick a five inch floppy these days? <Laugh>, that's, that's gonna be a, a problem. I can give you some ideas, but okay. Yeah. You gotta roll it up first.
Leo Laporte / Steve Gibson (01:34:27):
Yeah. Anyway, he said, I tried M secure premium as the recommended password manager to replace passwords plus, but decided to cancel that password manager today, too. I guess he was in the mood to cancel these managers. He says, as I found their tech support, severely lacking. Oh yeah. You don't wanna ever talk to anyone's tech support. He said, it seemed to me that M secure was a one or two man operation. Okay. I'm kind of, well, we got Greg and we got Sue, so I guess that's three people anyway, two and a half. He says, yeah, he says, I'm sticking with bit warden as they have the best options prices. And they also support the UBI key. Thank you as always for your great work on security. Now I'm looking forward to spin right. Six one since I've been a subscriber since version 1.0 and yes, it also had a five inch floppy disk in the beginning.
Leo Laporte / Steve Gibson (01:35:26):
<Laugh> and thank you, ed. And congratulations on no longer using 20 different password managers twiddling it down to just one. Wow. Yeah, yeah, yeah, yeah. So, okay. If you want a break, why don't you take a little break cuz you gotta, before we launch into this yeah. You've been talking for a long time and I, and I will take over for a minute. <Laugh> I could feel, I could feel the tension building in your throat. I just wanted do a plug for club TWI. This is a how we're kind of smoothing out the ups and downs in advertising. This was an idea that came to Lisa during the pandemic and it's really been a boon to us. What do you get in club twit? You get for $7 a month, that's all ad free versions of all our shows, this show plus everything else.
Leo Laporte / Steve Gibson (01:36:17):
We do. You get access to a really fun social media site. I think, I mean, a discord discord discord is where you could chat about the shows, but also about anything else on your mind, every geek subject under the sun, we even have our own Mindcraft servers. We have we have a trivia contest going on in there. Plus we have some discord only shows which you will also get access to either live or with a twit plus feed, which is a separate feed just for TWI club members. We do a lot of stuff in the discord, a number of shows for instance, hands on Mac mic sergeants show is for club members only right now as it grows and we get advertisers, it, it will certainly become public eventually, but same with hands on windows. No, never.
Leo Laporte / Steve Gibson (01:37:06):
Okay. Never Lisa says we also <laugh> so subscribe. Right? That's the idea we wanna make it desirable. We also have the untitled Linux show, the gizz fizz. We do a lot of events. We just did Stacy's book club. We're gonna do that again. Our community manager at Pruitt is planning more events in the future. So there's a lot of reasons to join. And for seven bucks a month, there's hardly any reason not to join. Now I should mention if you just want security now, and I know some of you do, you can buy that from the iTunes pod apple podcast for 2 99 a month. That'll give you the ad free version. I think for a few bucks more getting the whole thing is a great thing and it really helps us out. So go twit.tv, twi.tv/club TWI. There's a yearly plan as well.
Leo Laporte / Steve Gibson (01:37:57):
There's enterprise plans. Check it out. And that's where we also have information about buying individual shows, including you can buy the hands on Mac or hands on window show again, club twit is at twit.tv/club TWI, and now return to Steve Gibson. I just looked Michael Miller on LinkedIn and not surprisingly that we have a couple mutual connections, Scott Mac and oh yeah. And Evan Kaz, there you go. And, and, and by the way, Michael Miller still works for Ziff Davis of all things he works for their investment arm is their CISO. So he's, he's still in the biz, but great guy. Cool. All right. Now time to tell us what wacky data exfiltration is. Oh, and thank you for that pause to refresh. I thought, you know, you've been going a lot the time I thought I should need it. Yeah. Okay. So through the years we've had fun considering all the various ways that Dr.
Leo Laporte / Steve Gibson (01:38:56):
Mordecai Guri and his student researchers at Israel's cyber security research center of the Ben Guion university of the negative, which I also love saying every time I can have come up with, for secreting information from air gapped, computer equipment, that's like a hobby of theirs. So we'll all recall picking up the vibrations from the surface of a bag of potato chips, sitting unnoticed in a conference room. There was also a in a, a party setting. The balloons were known to be vibrating to the, the conversations being held around them. And remember there was a plant that the whose leaf was vibrating. And so, yeah all that, anyway, there have been many of these such inventions, all of which they've developed and, and actually pulled off in order to determine the feasibility and the achievable information transmission rate. So in the past week, we have their reports of two additional covert information leakage channels.
Leo Laporte / Steve Gibson (01:40:08):
The first is actually one that we've discussed in the past. That's the blinking LEDs on network interface cards. Now I was quick to discount that since the LEDs, as anyone knows, who's actually looked at them, don't actually blink in time with the data. You know, although there's no hard and fast standard for the way they do blink. I, you know, I notice on my equipment, they're blinking for the same data in different ways you know, rates and like just the different styles. In general, they just show a flash when there's data on the act on know data activity on the line in either direction. And the light is on enough for you to be able to see it. But knowing that did not deter these Intrepid Israeli researchers in their paper entitled ether led E T H E R L E D. It's titled ether led sending covert Morris signals from air gap devices, via network card, Nick LEDs.
Leo Laporte / Steve Gibson (01:41:24):
And they explain highly secure devices or often isolated from the internet or other public networks due to the confidential information they process this level of isolation is referred to as an air gap. In this paper, we present a new technique named ether led allowing attackers to leak data from air gaped, networked devices, such as PCs, printers, network cameras, embedded controllers and servers network devices have an net have an integrated network interface controller. Nick, that includes status and activity indicator LEDs. We show that malware installed on the device can control the status LEDs by blinking and alternating colors, using documented methods or undocumented firmware commands. Information can be encoded via simple encoding, such as Morris code and modulated over these optical signals. I wouldn't use Morris code. I use the code and coding used on hard dis drives cuz that's serial also. But anyway, an attacker can intercept and decode these signals from tens to hundreds of meters away.
Leo Laporte / Steve Gibson (01:42:44):
We show an evaluation and discuss defensive and preventative counter measures for this exfiltration attack. Okay. So in a sense they're cheating or at least they're modifying the rules in a Kobiashi Maru like way they're allowing for malware to rewrite the Nicks firmware to take control over the L LEDs. In that case, it would indeed be possible to hugely increase the rate at which data could be exfiltrated from an air gap network, which has no other means of communicating, but those Nick cards can be seen. What I appreciate, I think most about these guys is that in every case they really do wrestle to the ground, whatever wacky topic and method they are researching, they really do the work. For example, in this case, their eight page paper described the three methods which can be employed to control the LEDs of Nick interfaces. They said, okay, first driver slash firmware control.
Leo Laporte / Steve Gibson (01:43:57):
They said in this method, the E D controlling code runs as a kernel driver or within the Nick firmware changing the led state slash color requires direct access to low level registers or special non-volatile memory addresses. This method enables the highest degree of control over the LEDs, but is very hardware specific and mostly undocumented. For example, documentation discusses, how to control the ethernet LEDs in an, in an Intel Nu Nu PC. It can be done from a kernel driver or by writing to specific addresses in flash memory at word 18 hex, which holds the LED's configuration for embedded controllers. The control of the Nick is typically performed via internal bus or USB interfaces. For example, sample code for land nine 15 X ethernet controllers programs, the corresponding L E D register via USB commands. So that's the first way then, you know the best, if you can get it, what way?
Leo Laporte / Steve Gibson (01:45:12):
Number two, link status control. They say in this method only the status L E D can be controlled. The malicious code can intentionally change the link speed, which in turn causes the network adapter to change the status. L E D for example, setting the link speed to 10 megabits, 100 megabits, and one gigabit will set the status L E D to off green and Amber respectively selecting the link speed can be done by interacting with the Nick driver. For example, the E T H tool command line tool and Linux enables to change the link speed of the ethernet controller, the same as possible in the windows OS via the net sh command note that setting the link speed requires root admin privileges in both Linux and windows. Technically the link speed is determined through the auto negotiation procedure in this procedure, which occurs in the physical layer, the connected devices share their capabilities regarding support of parameters, such as transmission rate, half full duplex, et cetera.
Leo Laporte / Steve Gibson (01:46:24):
The link speed of a network. Nick can be determined from the computers OS and third user L E D control. They say in this method, the user directly turns the status LEDs on and off by enabling and disabling the ethernet interface using APA using API or tools such as the E tool or E th command. The user directly turns the status LEDs on and off by enabling and disabling the ethernet interface. Another technique to be, to blink the status, L E D is using the test or identify functionality, enabling the operator to identify the adapter by visual indication. These operations can be triggered programmatically or via low level tool such as E tool. Okay. So as they always do, some of them, some group of them, whomever, you know, really looked at this and run out every detail and actually implemented these strategies.
Leo Laporte / Steve Gibson (01:47:32):
They consider the cameras needed to receive the information and the camera frame rates and interactions thereof. The, the, the maximum distances at which cameras can be focused upon LEDs on Nick adapters and you know, basically what could be done to make the entire thing work. Then they finally get down to the effective bit rates, which are achievable through each of these three methods. They have the, the driver firmware control that first and best one. They, they, they have in, in their table. Oh, K, which is their short for on, off keying. And they say blink, blink, frequency and colors allows them to achieve 100 bits per second. So they talk about using being, being able to use that to exchange text files, username, passwords, encryption keys, and, and pin codes. The second approach is link status control. They can get one bit per second there.
Leo Laporte / Steve Gibson (01:48:38):
So you're not gonna exchange anything really long or at least not quickly. And then the final, the user L E D control, they're claiming two bits per second. So you could do key logging, usernames and passwords credentials, encryption, keys, and so forth. So, so that's the first, this, this blinking of, of Nick LEDs. You know, again, I discounted it because again, it's not the actual data that's moving through the lines, but yeah, if you had control over the link, if you got software into the system in the first place, in a system that was unable to communicate with the outside world, but you were able to briefly infiltrate it, then you could clearly give it enough time, exfiltrate data. And, and really, you know, if you could cheat the firmware and get a hundred bits per second, then you could clearly do some damage, but it's also worth remembering that for many important secrets, you do not need a lot of bandwidth.
Leo Laporte / Steve Gibson (01:49:47):
Some of the very best kept secrets are also very short. A server's elliptic curve. Private key might only be 256 bits long, and even a larger RSA key is still only two or four KBIs. So even at a measly one bit per second, sluggishly bringing a land link up and down a two K bit key can be transmitted in only a little over half an hour, about 34 minutes. So it's possible if you wanted to do it. Okay. So that's the first wacky idea, wacky idea, number two, and arguably somewhat less wacky they're recently published 11 page paper is titled gyroscope and they spelled it weird. But understandably they spelled it G a I R O scope. You know, as in, you know, air gapped, gyro, G a I R O scope, they said injecting data from air gapped computers to nearby gyroscopes.
Leo Laporte / Steve Gibson (01:51:02):
And you might think gyroscopes what, but they're in every one of our smartphones, the papers abstract explains. They said, it's known that malware can leak data from isolated air gapped computers to nearby smartphones using ultrasonic waves. However, that was like from speaker to microphone, right? We talked about that little deal, and that was theirs years ago. So it's known that malware can leak data from isolated air gapped computers to nearby smartphones using ultrasonic waves. However, this covert channel requires access to the smartphones microphone, which is highly protected in Android OS and iOS. It might be non-accessible disabled or blocked in this paper. We present gyroscope an ultrasonic covert channel that does not require a microphone on the receiving side. Our malware generates ultrasonic tones in the resonance frequencies of the MEMS gyroscope MES is the acronym or abbreviation for micro electro mechanical system, which is what these little, you know, itty bitty well <laugh> electro mechanical systems are.
Leo Laporte / Steve Gibson (01:52:31):
So they said these inaudible frequencies produce tiny mechanical oscillations within the smartphone's gyroscope, which can be demodulate into binary information. Notably the gyroscope in smartphones is considered to be a safe sensor that can be used legitimately for mobile apps and JavaScript. We introduce the adversarial attack model and present related work. We provide the relevant technical background and showed the design and implementation of gyroscope. We present the evaluation results and discuss a set of counter measures to this threat. Our experiments show that attackers can exfiltrate sensitive information from air gapped computers to smart phones, located a few actually up to eight meters away, more than 24 feet away via a speaker's to gyroscope covert channel. So this one is more serious and interesting. We were just talking about residences last week with the Janet Jackson rhythm nation video and the Tacoma narrows bridge. What's special about resonance.
Leo Laporte / Steve Gibson (01:53:46):
Is it a relatively small signal like gust of wind up the, the Tacoma narrows, which would be entirely harmless in isolation, can some into the power of successive, properly timed bits of energy to result in a significant signal. That's the effect these guys have taken advantage of here. They explained what's going on in the me's gyroscopes. They said it is known that acoustic tones, degrade MES sensors in a frequency range known as the resident's frequencies. This ultrasonic input produces erroneously, low frequency, angular, velocity readings in the X, Y or Z directions. The vulnerability of MES sensors to ultrasonic corruption is due to the mechanical structure of a me's gyroscope. The misalignment between the driving and sensing axes axes is one of the main causes of the fault output generated by the gyroscope, the phenomenon and its physical and mechanical roots are discussed in relevant literature.
Leo Laporte / Steve Gibson (01:55:06):
It was observed in the previous works that the typical residents frequencies of MEMS are within a fragmented band in the ultrasonic frequencies, mainly above 18 kilohertz. The frequency of the resulting vibrations within the sensor is determined by the structure of the me's gyroscope, it's positioning and the distance from the sound source as always, they do all the footwork actually develop and implement a full attack from, from the, the software in the PC to run the speaker as an ultrasonic sound source and determine how far away they're able to position the smartphone and what data rates they're able to get. They determine the natural residence frequencies for a number of, of the MES gyroscopes in a number of different smartphones. And they demonstrate the ability to send eight bits per second of binary data, completely covertly, and obviously silently cuz it's above our ability to hear from a standard PC speaker to a smartphone located up to eight meters away.
Leo Laporte / Steve Gibson (01:56:18):
Actually I said 24, it's actually 26 feet. So that's pretty slick as always. When I talk about the work that these guys are doing, I'm left thinking that it would be, you know, it would be a blast to be in this professor's class. You know, being asked to actually make these out of the box attacks work. You know, that would be an awful lot of fun if you're not working for the us government doing attack and defend and infiltrate or whatever that was, we call it cyber cyber. Yes. If you're not in the us cyber <laugh> I just think of Donald Trump saying his son Barrett Barron was excellent in the cyber <laugh>. That's what I think of when I think of that, it would be a good class to be in coming with this stuff. Lot of fun. You could do it yourself.
Leo Laporte / Steve Gibson (01:57:11):
Maybe you should let let's think of a new way to do it. We've done, you know, glass windows, you said potato chip bags. That's for listening to audio exfiltrating from computers. Oh, there's gotta be lots of ways. What about the oh, of the hard drives? Remember we even had the sounds of the power supply yeah. At one point. Yeah. And, and like, and, and getting fans to spin at different speeds. So like it speeds up and slows down and you, and you could hear that at a dis I mean there's lots of ways, you know, mm-hmm <affirmative> I mean, and, and remember the original what was the military where they were able to from a distance, they were able to look at the, the electric magnetic noise coming off of a CT screen. Right? That's Tempest. Yeah. Tempest that's yeah.
Leo Laporte / Steve Gibson (01:58:02):
Yep. Tempest. They could do it through walls. <Laugh> unbelievable. Unbelievable. Well, a fascinating story. Thank you for bringing that up. I appreciate it. This is why you listen to security now, right? Mm-Hmm <affirmative> get all the security news and, and some, and some mind, you know, mind meet mind, candy mind is candy better than meat <laugh> we do. Steve does security. Now every Tuesday, one 30 Pacific, four 30 Eastern, 2030 UTC. Watch us do it live@live.twi.tv. There's audio and video streams there. Chat with us live@irc.twi.tv or in the discord chat room, but you don't have to watch live. I mean, that's the whole point of, you know, we record these and we, and we carefully craft a podcast out of them. We take this play and we shape it. And then we put the podcast up on the websites. Now Steve's site is grc.com.
Leo Laporte / Steve Gibson (01:59:00):
He has 16 kilobit versions of the show. That's a unique version for the bandwidth impaired. We do 64 kilobit audio as well. He does it and we do it. He also has transcripts, which really are handy for searching or for reading along as you listen, thanks to Elaine Ferris. Who does those for you every week? Steve, all of that@grc.com while you're there, you might wanna take a look at spin, right? The world's best mass storage, maintenance and recovery utility. Getting there, getting there is the word spin, right? Six is the current version, but if you buy that, you'll automatically get upgraded to 6.1 and you can participate in the rapidly winding down process of a developing six point. Actually there actually will be a long beta period. Oh, okay. Cause I'll have the dos side code nailed. Well, before I have everything packaged up as the windows app, that's able to, to produce the butable USB sticks and everything else, so, okay.
Leo Laporte / Steve Gibson (01:59:55):
So there will be something to to owning six oh. And being able to get the, the beta of six one. Excellent. so it really is worth joining. Then go or buying, go to grc.com. You can leave feedback form there, grc.com/feedback. You can also Twitter him. He is the tweeter guy at G SG GRC at SG GRC. We have copies of the show at our website which is twit.tv/sn 64. Kilobit audio and video. That's our unique format. Since we record video of this after the fact it'll be up there usually a couple hours, maybe three hours after the show ends. You can also get it on YouTube. There's a dedicated YouTube channel to this show and all of our shows and probably the easiest thing is subscribe. And your favorite podcast player. That way you'll get it automatically.
Leo Laporte / Steve Gibson (02:00:51):
As soon as it's available discussions continue. Obviously you chat is a little late, you know, if you're listening to it download, but we have a great forum. Steve has his forums@grc.com. We have the twit community forums@twit.community. There's also a twit Mata on. So if you're, if you want Twitter without the tweets, all the tweets, none of the tweets, it's at twit.social. That's our Mata on instance that concludes this thrilling gripping edition of security. Now thank you, Steve. Have a great week. I have my friend. I will see you in September.