Security Now Episode 910 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for security. Now. Steve Gibson is here lots to talk about. H T T P S finally comes to the Brave Browser. Are you worried about Chinese cameras? Spyware Hmm. And a new encryption technology for lightweight platforms that might be good enough to replace it all. It's only coming up next on Security Now. Podcasts you love
... (00:00:26):
From people you trust. This is TWIT.
Leo Laporte / Steve Gibson (00:00:34):
This is Security Now with Steve Gibson. Episode 910, recorded Tuesday, February 14th, 2023 Ascon.
(00:00:45):
This episode of Security Now is brought to you by BitWarden. Get the password manager that offers a robust and cost effective solution that can drastically increase your chances of staying safe online. Get started with a free trial of a teams or enterprise plan, or get started for free across all devices as an individual user at bitwarden.com/twit. And by PlexTrac. The premier cybersecurity reporting and collaboration platform. With PlexTrac, you'll streamline the full workflow from testing to reporting to remediation. Visit plextrack.com/twit to claim your free month of the PlexTrac platform today. And by Fortra, the cybersecurity landscape is full of single solution providers, making it easy for unexpected cyber threats to sneak through the cracks. That's why Fork created a stronger, simpler strategy for protection. They're your cybersecurity ally, working to provide peace of mind for every step of your journey. Learn more@forr.com.
(00:01:53):
It's time for security. Now with a jovial, the happy the ever tru ent, the ever insent ever effervescent Steven Gibson <laugh>, our host of the show. And then he's in a good mood today, despite the bad news that he will inevitably be bringing us as he always does on this show. I see. That's exactly, that is exactly the case, Leo. Yeah. actually the, the good news is a function of the picture of the week, which is just a real hysterical knee slapper. Yeah. but we're gonna answer some questions as we are want to do of late. What more has happened with the ES X I ransomware story is malicious use of chat. G P t going to continue to be a problem. What exactly is Google giving away? Why is the brave browser changing the way it handles URLs? What bad idea has Russia just had about their own hackers?
(00:02:51):
Why would Amazon change its S3 bucket defaults Now, who's worried about Chinese security camera spine <laugh> and who has just breathed new life into Adobe's p d viewer? What's on our listener's minds and what the heck is ACON and why should you care? Those questions and more will be answered on today's 910th episode of security Now. Wow. It's one after 9 0 9. That is exactly where I got that. Nu that's how I came up with a number. Leo <laugh>. You I just had one. Yeah. Hey, it's called Increment. You do that enough and you run out of Digits <laugh>. Pretty soon you overflow. That's the register and then you're done. Let us talk before we get into the meat and the picture of the week, which is hysterical. <Laugh>, let us talk about Bit Warden. Everybody's new favorite password manager. I've moved to Bit Warden. Steve was talking about it earlier a couple shows ago.
(00:03:55):
It is the only open source check cross platform that's a must plat, a password manager that can be used at home. Okay. At work, yep. On your mobile, on the go. Yep. And is trusted by millions. We are all doing it. The Bit Warden Switch. And you know what's great? It's very easy no matter what your old password manager to switch over to Bit Warden and then get all the benefits of Bit Warden with Bit Warden. You can securely store credentials across personal and business worlds. I think anybody who listens to this show knows you need to use a password manager and probably gets asked a lot, especially these days. Which Password Manager do you recommend? Well, I recommend Bit Warden. I've been using it for a few years now. For a number of reasons. For individual users, it's free, free Forever cuz it's an open source product so you don't have to pay for Bit Warden and I asked them specifically cuz some other password managers remember, change their free tier.
(00:04:55):
I said, are you ever gonna, you know, take back this offer? They said, no, we can't. It's open source. It's, it's part of the we're we're not made to make a profit on the free tier. That's good news. Now, I still pay $10 a year for a premium account. I think that's a very fair fee. And I would pay it not for the features. I would just pay it because I wanna support these guys. They made such a great product and because it's open source, you're gonna see improvements all the time. In fact, we were talking about a memory hard password derivation you know, hashing. We talked about pbk DF two and why it's not memory hard. Steve's talked about S Crypt and Argon Two. In fact, a couple episodes we talked about, somebody had submitted a pull request to Bit Warden for s Crypt and Argon Two, they've dec they decided, you know, let's, we'll, we'll put Sry on the back burner and focus on Argon two.
(00:05:49):
And Bit Warden has said Yes in the next version of Bit Warden, we will offer that as a password hardening option. That's really good news. Probably meaningless to the general public. But you, if you listen to our shows, you know, that's a big deal and that's what Open Source can do for you. It really makes a difference. Of course, as with any password manager, your vault is end-to-end encrypted. You know, they do everything right. They do, do they go one step better than that other guy? <Laugh>, who shall remain nameless. They encrypt all the data, including the URLs for your websites that you've visited there. There is no plain text, meta text that comes along with your vault. No, it's all encrypted. They don't track your data in the mobile apps. They do crash reporting. And if you don't like that, even that's removed. If you're on an Android with Thero version, see, this is where Open source is great.
(00:06:41):
People don't want something or they do want something, they can make those changes. The great thing is the Bit Warden community is vibrant, is active, and is always making bit warden better. You can review their library implementations if you want on GitHub. You can review the bit Warden privacy policies@bitwarden.com slash privacy. Of course, you should always do that before adopting any program. But it's even more important really for a password manager, right? Protect your personal data, protect your privacy with Bit Warden, adding security or passwords with strong, random, true randomly generated passwords. Unique to every account. But you can go one step further because they have a username generator that let you create unique usernames for every account. You can use any of the five integrated email alias services with Bit Warden our sponsor. Fastmail works with it. Simple login, a anonymity Firefox Relay, and now Duck dot Go all allow you to create unique login names as well as unique passwords and still get the email sent to those names through those services.
(00:07:46):
A masked email address. So now you, it's kind of doubling the security. It has another benefit if a, if a company sells your email to somebody, you'll know exactly who it is cuz you have a unique email address for every single company, every single site, every single program you sign up for. I love this. It also keeps your main email address out of, you know, the lists. Bit Warden is a must for businesses as well. We're moving now right now to bit Warden at twit. It's fully customizable, adapts to your business needs. They have a variety of tiers. There's a teams organization option for smaller businesses. $3 a month per user. We're going for the enterprise organization plan. $5 a month per user. You can share private data securely with coworkers across departments. That's a nice feature. Or the entire company as we get closer to tax time.
(00:08:34):
You'll love the ability to send, you know, stuff that should really be private and cr in an encrypted fashion to your clients, to your other company. Employees. Individuals. Again, basic free account, free forever, unlimited number of passwords, cross platform. One thing you might wanna upgrade to the dollar, less than a dollar a month. The $10 a year plan for two factor. And I, I really love it that bit Warden lets me use hardware security key with my bit warden. I feel like that's even, you know, even more secure. I really like that feature. To me that's worth 10 bucks a month. There's also family plan. If up to six users, you don't actually have to be in a family that's just what they call it, up to six users as a group. $3 33 cents a month and you get a lot of additional features.
(00:09:21):
Bit Warden supports importing and migrating from many other programs. It's very easy to move. We've, we've all done it. Steve did it. I've done it. Look, if, if nothing else, please use a password manager. Some password manager. If you want to use the best use Bit Warden, the only open source cross platform password manager you can use at home on the go at work, trusted by millions of individuals, teams, and organizations worldwide. Get started right now with a free trial of the teams or enterprise plan or free Forever across all devices as an individual user. But do me a favor. So they know you saw this here, bit warden.com/twit. Please use that slash twit cuz then they're gonna know, oh yeah, we saw this on twit. That's really important to us. Bit warden.com/twit. I think we all agree this is the way to go, the way forward.
(00:10:15):
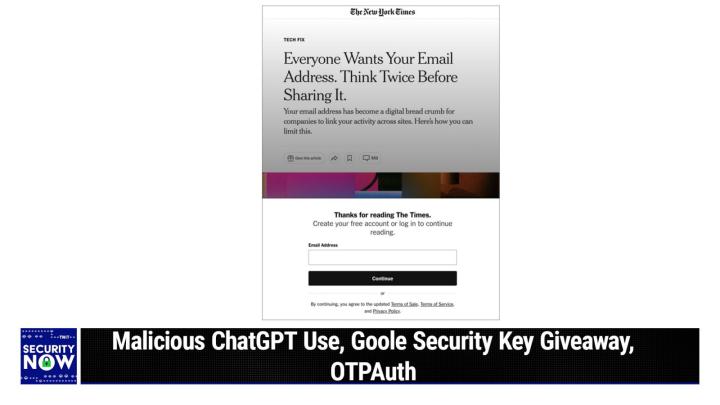
Bid warden.com/twit. All right, I got your picture all queued up, Mr. G <laugh>. So big thanks to one of our listeners who actually encountered this when he was surfing on the web. The the upper portion of the photo is at is shows that they, they, they was visiting the New York Times and the Tech, the tech Fix column has the headline in this case, everyone wants your email address. Think twice before sharing it. And it has the subhead. Your email address has become a digital breadcrumb for companies to link your activity across sites. Here's how you can limit this <laugh>. Now, unfortunately the lower portion of the page says, thanks for reading the Times. Create your free account or log in to continue reading. What's your email address <laugh>?
(00:11:19):
Very nice juxtaposition there. That's awesome. Oh, it's just, it's just perfect. Hysterical. So, you know, I've often followed a link there and sure enough, the bottom part of the screen is saying, okay, you know, we're not, we're not gonna get in your face too much, but we'd like to know who you are. And unfortunately in this case, it was, you know, it came up over the, over the story about, you know, don't give anybody your email address except, you know, we're asking for it. Well, but see if you're using Bit Warden, you could just give 'em that obfuscated address. Could. That's right. Yep. That's right. Okay, so E es X I ARGs follow up. We know that a story this big, you know, isn't going to immediately disappear. And, you know, so we have some follow ups to last week's reporting on this.
(00:12:09):
First, and this was sort of cut me by surprise. I didn't realize that cisa, you know, our, whatever the hell that stands for. Cyber Cybersecurity Information Security Agency or something cisa, C I S A that there is involved in various cybersecurity projects in an open source fashion. They've got a GitHub account, github.com/csa dot, I'm sorry, CSA, G O v github.com/csa, G O v. Anyway, CISA formally released an open source E S X I ARGs, you know, that's the ransomware that was messed up at least 3,200 individual E ES X I VMware servers. Anyway, a ransomware recovery script is what they've relu what what they've released. And so, you know, as I said, I've never really paid much attention to SSA's extensive presence on GitHub. But examples of some of their projects, there's something called GET gov, which says, building a new.gov registrar for a bright.gov future, something, a project called Red Eye, a visual analytic tool supporting red and blue team operations cset, a cybersecurity evaluation tool and cross feeded external monitoring for organization assets, external monitoring for organization assets.
(00:13:53):
So it's like, wow, there's a bunch of stuff there, which I really wasn't aware of. So anyway as far as SSA's ES X I, ARGs ransomware Recovery Script, they wrote, CISA has released a recovery script for organizations that have fallen victim to E ES X I ARGs ransomware, the ES X I ARGs ransomware encrypts configuration files on vulnerable ES X I servers, potentially rendering virtual machines unusable ES X I ARGs hyphen RECOVER is a tool to allow organizations to attempt recovery of virtual machines affected by ES X I ARGs ransomware attacks. CSA is aware that some organizations have reported success in recovering files without paying Ransoms. CSA compiled this tool based on publicly available resources, including a tutorial by EN Sam SANEs and Amit ak. This tool works by reconstructing virtual machine metadata from virtual disks that were not encrypted by the malware. Remember I talked about this last week that there was that, well, well, I'll get into it more in a second.
(00:15:10):
They said, for more information, see SISs esx, I ARGs Ransom, we're virtual machine recovery guidance. And then they've got a disclaimer with boilerplate about, you know, use this at your own risk and we're not making any representations and blah, blah, blah. And, you know, look at the script yourself, make sure it's safe for your environment and so forth. So, you know, not accept assuming any liability for damage causing by using the script and so forth. Anyway, so this is quite cool. We have the cybersecurity arm of the US government being active you know, proactive and posting scripts on GitHub to help mitigate what has become a massive problem. Okay? So that's the good news, <laugh>. The bad news is that the very next day this, this was posted last Tuesday, on Wednesday, a new version of the E S X I ARGs ransomware appeared, which rendered any such scripts as this useless though it would still be potentially useful to anyone who was hit with the earlier version, which did not also encrypt the master VM DK file.
(00:16:21):
Remember I noted last week that it wasn't clear why the bad guys were not also encrypting the large system image dot vm DK file. I, you know, maybe they were just in a hurry to blast as many systems as possible in the shortest amount of time. And they figured that no one would know any better if they were just to encrypt the tiny pointer files, but they fixed that oversight. Now they're encrypting the main dot VM DK virtual machine image file. So there's no shortcut to getting one of these systems back. And also, as I was expecting last week, those running open s l p honeypots did see the number of scanning ips jump from three to more than 40 A. And, you know, while 40 is a large number and maybe some more bad guys got in on the act, it's also certain that with a, a, you know, a story that's generating this much news, many of those scanners would've been security firms who were all interested in making their own assessment of the size and scope and, you know, scale of this problem.
(00:17:32):
So I don't think that's 40 bad guys. It's probably half and half. You know, who knows? And as a result of some of those scans, we also know that that at least in some cases, reports have pegged the total number of exposed ES x I instances as high as 83,000. But those are not necessarily all vulnerable instances. Rapid sevens use of their telemetry data, which was gathered through their project sonar counted nearly 19,000 confirmed currently vulnerable. And so there's an example of somebody who was scanning the internet, probably, you know, one of those 40 or more that were seeing touching honeypots. So they found 19,000 near nearly 19,000 currently vulnerable VMware E ES X I servers now connected to the internet not having the patch for C V E 20 21, 21, 974. So I also read one comment from a cloud provider who indicated that as far as they were concerned, their responsibility is hardware and connectivity and no more.
(00:18:55):
And actually, I, you know, as, as a user of a rack at level three, you know, that's, they're actually one step back. My rack was empty and I had to provide my own hardware. But all they're saying is, you know, here's a here, here's a plug where you get bandwidth, and here's some power strips where you can plug your stuff in, and we're gonna keep it cool and keep the lights on for you. Otherwise, you know nothing. But in the ca e even in the case of a cloud provider where they are allowing you to use their hardware, they're providing that, at least in this one case, you know, their position was, we give you the hardware, we, it's gonna be connected to the internet, and it's, it'll have power. That's it. You know, the maintenance of whatever software the customer is running is the customer's sole responsibility.
(00:19:48):
And they feel that this is true. Even when they, the cloud provider were the ones who initially established the running software, including E S X I on that machine. So that being the case, I, you know, I wonder again, whether in like, wondering how this happened, whether this might be a classic case of something falling through the cracks where each party believed that the other was responsible for its maintenance. So, you know, everybody was pointing fingers at the other party saying, well, we thought they were gonna do that, and as a consequence it didn't happen. So anyway, the consequences of all this were disastrous. And it'll be interesting to see whether any behavior change occurs from anyone as a result of this. Well, there are a few, I think actually we had one really neat piece of listener feedback from somebody who works at VMware that we'll be getting to and a little bit later.
(00:20:49):
Okay. checkpoint Securities blog posting a new one is titled Cyber Criminals Bypass Chat, G P T Restrictions to Generate Malicious Content. And so paraphrasing a bit what they wrote, they said there have been many discussions and research on how cyber criminals are leveraging open AI's Chat G P T platform to generate malicious content such as phishing emails and malware checkpoint researchers previous blog described how chat G P T successfully conducted a full infection flow from creating a convincing spearfishing email to running a reverse shell, which can accept commands in English. Checkpoint researchers recently found an instance of cyber criminals using chat G P T to quote, improve the code of a basic info Steeler malware dating back from 2019. Although the code is not complicated or difficult, difficult to create chat, G p t successfully improved the Info Steeler's code. So anyway, chat checkpoint, you know, in and throughout the rest of the article, they noted that there are currently two ways to access and work with open AI's models.
(00:22:14):
The first is through the web interface, which is what, you know, 99.99% of everyone does, right? You just, you get the chat G p T Web UI, and you ask it a question. And, and that's how you work with chat G p t Dolly two or the open AI playground apps through the web interface. But the second is sort of the back door, which is the api, which is used for building applications, processes and so on. And what that allows people to do is to present their own user interface that looks like whatever it is they're wanting to, you know, whatever surface it surface it is that they're, they're making available. And then on the backend, they're talking to open AI's API in order to perform the actual work as part of its content policy. From the start, and we talked about this a little bit last week, OpenAI had created barriers and restrictions to minimize the creation of malicious content using its platform.
(00:23:20):
Several restrictions have been set within chat GT's web user interface to prevent the abuse of the models. For example, if a user requests chat g p t to write a phishing email impersonating a bank or asks it to write Malware chat, G p t will very politely refuse. And in fact, in in their in, in their blog posting, they, they actually show <laugh>, they showed the, the web UI where they'll, they wrote I would like you to write a phishing email impersonating, you know, blank bank. And actually they had blacked out the bank's name and chat. G p t was very polite in saying no. And it explained what phishing emails were <laugh>, in case the person asking for one didn't know and explained also why it wasn't gonna do that. So, you know, that's cool. And I have no idea how you impose those sorts of restrictions on something.
(00:24:22):
Of course, I have no idea how any of this stuff works anyway. It's also, and I, I surprise Checkpoint doesn't know this easy to trick chat G p t into telling you all sorts of things. It's not supposed to. So, yes, exactly. And, and so that's a again, and, and, and Leo that, that, that's exactly my, my point when I say, you know, how do you, how do you design restrictions on something, which is chat, just chat gtp. I just, I just, well, they, you know what, when Open AI released it, they said, we're, we wanna see what you do with it, because this is how we test it. That's how you test it. You put it, you let people bang on it, yeah. Hack it, and then you can wow, figure out better controls and then put it out again, and then they'll hack it again.
(00:25:07):
And you, this is the same process. All of this stuff goes through, right? Yep, yep. You never know you release it, right? And they, they are reporting that cyber criminals are working their way around Ja GT's restrictions, and that there is active chatter in the underground forums discussing how to use open a AI's api, where apparently there were no attempts to restrict this. I, I got the sense that the, the web facing restrictions were just sort of there like, like, you know, like a, like keyword hits or something, you know, it's like, it, it seemed like a half baked approach, but they figured that they ha they had to do something for what most of the people would be using, which was the, the, the web facing user interface. So anyway, it turns out that the underground is figured out that the API doesn't have these barriers and limitations.
(00:26:08):
So what's now been done is they're, they're creating telegram bots that use the api. The bots are being advertised in hacking forums to increase their exposure. The current version of Open AI's api, which is used by external applications like this, apparently it, it's called G P T Hyphen three Model, which is connected to Telegram. It has no apparent anti-abuse measures in place. And as a result, it allows malicious content creation, you know, whatever you want. Phishing emails, malware code, the stuff that the web interface will exa, you know, at least somewhat push back against in an underground forum. Checkpoint found a cyber criminal advertising, a newly created service, a telegram bot using Open AI's API without any limitations or restrictions as part of its business model that is this, you know, this cyber criminals business model. The criminals are able to access the unrestricted chat, G p t backend, a p i, for an additional 20 free queries.
(00:27:24):
You get, you know, 20 to get, get you hooked on it, and then after that you're charged $5 and 50 cents for every 100 queries, which seems like a pretty good price. Okay. So, you know, my sense is this will probably be, hopefully this will be short-lived, you know, and c can you just imagine what things must be like right now over at Open ai? You know, they probably knew this was gonna be popular. They, they, but they must have been surprised by this, this stunning, like, like overnight sensation that this thing created wh when it came out. So, you know, I'm sure they're aware that chat G p t is being abused for the backend, and I would not like to have the job of figuring out how to prevent that abuse, because that seems like a difficult thing to do.
(00:28:20):
Last Tuesday was safer Internet day. What a cute concept. Anyway, on that day, Google announced that they would be giving away 100,000 of their Titan hardware security keys to individuals at high risk of online attack. They posted last Tuesday there's no shortage of security challenges for high risk individuals. In fact, a 2022 study by Google and yu gov found that over half of journalists and professionals in politics have had their online accounts compromised. Not us. Nope, nope, nope. The threats are intensifying the stakes for individuals and organizations are increasing. And we're d we're, and it says Google, we're dedicated to keeping online users safe, including helping people at higher risk of cyber attacks. They said that's why on Safer Internet Day, we are announcing our new online safety and security partnership with the International Foundation of Electoral Systems, I F E S to provide free security training and tools to high-risk users.
(00:29:39):
And this will be, you know, global. They said this work is designed to help shore up the defenses of democracies that work for all. We're also building on our partnership with defending digital campaigns at D D C to protect US political campaigns ahead of the US 2024 elections, and will be distributing 100,000 security keys globally to high risk individuals throughout 2023 at no cost. And they finished. In addition to our partnership with I F E S, we're expanding our long-standing collaboration with defending digital commands. That's that D D C to equip campaigns with the security tools they need ahead of the US 2024 elections through the campaign security project. D D C will help secure campaigns in all 50 states, providing security training and products at no cost since 2020. Over the course of our partnership, D D C has secured over 380 campaigns and distributed over 20,000 security keys.
(00:30:47):
And we look forward to continuing to support D D C as we near a critical election cycle. So 20,000 and, and those, those security keys were also provided by Google at no cost. So they're gonna go five times that in during 2023 in order to, you know, really push out security. And of course, this is good advertising for the Titan security key. And Leo, it is quite sobering to imagine that more than half of journalists yeah. And political professionals have had their accounts hacked. I mean, I guess they're highly exposed. They're probably not super security conscious. They probably, you know, they may not like, you know, have an easy password because they need to let, you know, in some cases, allow their, their collaborators to, you know, sh you know, log in as them to, to do something or, you know, who knows.
(00:31:43):
But wow, certainly moving to stronger identity authentication is a win-win. Yeah. Yeah. Okay, this is an interesting story. Last week we were talking about that default inclusion of those 40 top level domains in the global browser, H S T S list, the https s strict transport security list and about the broader H S T S list in general were domains whose T L D was not among those chosen 40 would need to explicitly add themselves to that global hsts list. As I mentioned, you know, I did with grc.com years ago and I recall further talking about which browsers had finally started, assuming that a URL entered without either an H T T P or H T D P S scheme specification would be assuming H T D P S was what the user meant unless that failed to function. And I recall at the time noticing that the brave browser was not among those that had decided that it was time to switch.
(00:33:06):
Well, last Thursday, the Brave Browser Project explained their intentions in that regard, and their explanation contains some interesting new information. Although, well, it, it's, we we'll talk about it seems a little odd. So here's what they posted under the headline https s by default they said starting in version 1.50, and you know, <laugh>, I sort of had to give them some props for not being allowed. Version 150, like, you know, everybody else now, you know, version 1.5. That's cool. Anyway, they said, brave will include a new feature called https s by default, that improves web security and privacy. By increasing https, use Brave will upgrade all sites to HT dps s falling back to HT d p only if the site does not support https s or in the rare case, a site is known to not function correctly when loaded over H G D P S.
(00:34:10):
They said this feature is the most protective, aggressive default H C D P S policy of any popular browser. And I had to do double check the date <laugh> on this posting cuz it's like, what wh when did you write this? Yeah, but it was last Thursday. And they said like, okay, maybe they haven't checked the other browsers, which have all been doing this for like two years. Anyway, they said, and speaking of Brave will be available on Android and desktop versions of the Brave Browser to begin with, with iOS coming later because HT D P s is critical to privacy and security browsers like Brave are eager to load sites over HT D P s wherever possible. And yes, all the other ones have been doing that for a while. They said, and since many sites today support h only HTD p s, it's simple to load these sites in a private and secure way.
(00:35:08):
And encouragingly more and more sites are being built or, or updated to support https s only or to use other TLS protected protocols like Secure Web Sockets. Unfortunately, this is where what they're writing is interesting. Unfortunately, they said there are many sites on the web that still support H T T P and some laggards that only support insecure H T T connections. Brave's goal is to automatically upgrade these sites to https s whenever possible. And then said i e in all cases where a site loads and functions correctly when loaded over HTT p s they said, but deciding when to upgrade a site to https s is tricky. In cases where a website does not support HT dps attempting to upgrade from HTT P to https s will produce an obvious error, right? Other sites support both https s and HT d p, but do so from different domains.
(00:36:17):
And they said, you know, as an example, HTTP colon slash slash example site versus https slash slash secure example.site. Again, this feels like the 1990s, but okay anyway. And they say that makes automatic upgrades tricky and still other sites appear to load correctly when fetched over https s but actually have broken functionality. Okay, well now that's an edge case that is certain could be a problem. They said in short, ideally browsers would never load sites over H T P and browsers could automatically upgrade all insecure requests to HT D P s. In practice, though, it is difficult to know how, when, and if a site will function correctly when upgraded from HTTP to HT P S ST starting in version 1.5, the Brave Browser will use a new system for upgrading insecure H T T P connections to secure and private https s connections. The new feature called https s by default works as follows.
(00:37:31):
If you are about Division A page loaded over H T T P brave checks to see at the destination is on a list of sites that are known to break when loaded over https s Brave maintains this list of breaks over HTT P sites, which is open for anyone to view and use, and we'll be getting back to that in a second since it's interesting. If the requested site is on the list, brave will then allow the site to load over HT d p. In other words, you know, no automatic upgrade provided they said that it's not on the list. Brave will attempt to load the site over HTT p s by upgrading the navigation request from HTTP to HTPs s If the server responds to the replacement HTD DPS s request with an error, then Brave assumes the site does not support hdps S and will load the site over H C D P.
(00:38:27):
Otherwise, Braves loading of the site over H DPS s will ensure a more private and secure connection. Again, interesting that they think this is like groundbreaking, but okay. Brave's new https s by default feature replaces the previous list-based approach Brave has used since our first beta versions In that approach, brave used the H T D PS everywhere list, which they say is a terrific public resource maintained by the e f to decide when to upgrade HTD P connections to https s But while the Htd p s everywhere list is useful, it has two important drawbacks. First, the HT d p s everywhere list is no longer maintained. Actually, I went over to the e f wondering why that was and they said, yeah, it's, you don't need it anymore, <laugh>, everybody's using HTT p s so just go ahead. And then they said, meaning that the list is increasingly out of date.
(00:39:28):
Well, that's true because you don't need it anymore. Then they said, second, despite the best efforts of the EF f, any approach that uses a list of what sites should be upgraded is going to be limited. As the number of sites on the web is enormous, and it's difficult for the list maintainers to keep up. Braves approach by contrast maintains a smaller and more manageable list of sites to not upgrade. Say so they've, they're ex excited because they're flipping it upside down. Finally, more broadly, the main benefit of Brave's new HT dps s by default feature is that it has a better default, right? It defaults to htd p s in is default configuration. Https s everywhere would allow unknown in, for example, not on the list sites to load over H C D P Braves new https s by default approach loads the site over HT p s even in cases where a site is new or unknown.
(00:40:27):
Okay? So, you know, it's not that this is not a good thing, this is a very useful improvement for Brave and welcome to the club. You know, the, their use of an excluded upgrade domain list, however is interesting. Nearly two years ago I checked it was on March 23rd, 2021 was when Google announced that from Chrome version 90 on the assumed default for Address bar URLs that don't specify a scheme, you know, and really who's entering https colon slash slash every time anymore would be switched from http, which was the historical default to https. So with Brave saying that some websites do not handle automatic connection security upgrading, I was curious about what would happen if I went to one of those will not upgrade sites. The list is at GitHub under Brave Ad Block hyphen lists Master Brave Lists, H gtps s upgrade exceptions.
(00:41:39):
And for anyone, should I have the link in the show notes? And the second and third domains on the list jumped out at me since they were, they were columbia.edu and www.columbia.edu, you know, but that was nuts. You know their presence on this list would mean that Columbia University could not be accessed by https. And again, what year is this? So I tried going to http slash slash columbia.edu and also http colon slash slash www.columbia.edu under both Chrome and Firefox. And in every case on either browser, I was promptly redirected to https slash slash www.columbia.edu. In other words, they pre pres the redirection appeared to come from columbia.edu because they saw me making an H T T P connection and said, oh, no, no, no, no, you want to go over here. So, you know, it handled the redirect properly. So, you know, it doesn't hurt to have them on the list, but it suggests that perhaps that list of 112 domains needs a bit of maintenance and it actually, it would be an easy thing to do, right?
(00:43:15):
All you have to do is have a bot go and try to connect to each of those domains over HTTP and see what happens. And if it bounces you over to https, you're good. Take it off the list. So, you know, for what it's worth, again, that list was a total of 112 domains. We already know two need to be removed. So now we're down to one 10. There was another one that jumped out at me. It was shakespeare.mit.edu and I thought, okay, herd of m mit what are they doing? Turns out I think someone tripped over the cord on that one. Yeah. nothing happens. H TT P or H TT P s Shakespeare has left the building. So you know, that's just that, that one's just dead. And the other ones are really obscure. I mean, like, you can kind of find among the remaining 110, some maybe interesting domains, but not really.
(00:44:16):
So, you know, okay. In any event, for what it's worth, I wanted to let any brave browser users who may be listening know that from 1.5 onward brave would be assuming https by default for any domains that matter to you, assuming that none of those 110 other weirdos don't. So in that regard, you know, brave is declaring, you know, for what it's worth, they're declaring this to be a huge innovation. But it appears to me that they're now reaching parody with the rest of the industry. And of course that's good too. And Leo, weren't you using Brave for a while and then Yeah. Came back. I'm pretty much sticking with Firefox cuz I don't want Yeah. A monoculture with Chromium and so, right. And I'm, I'm now a hundred percent Firefox. Yeah, that's Firefox. Firefox works great. It's, it's fantastic as plenty of extensions.
(00:45:07):
I, I can't think of any reason not to use Firefox to be honest. No. In fact, the thing that moved me away from Chrome, cuz I was using Chrome a lot, is I've got a little Intel Knuck you know small little integrated PC that I use in the evening. And when I would just, just opening Chrome the fan on that little thing, which would spin up and it was like, what the heck? And, and doesn't, you know, it's quiet when I'm using Firefox, obviously, you know, Chrome is just whatever it's doing, it's it might be, it's like Chrome does an assessment of all of the apps that you have installed on your machine. Whenever you run it. There's like, there's something going on. I know on my Mac if I have Chrome on the machine the way Mac is set up Mac os these days is you'll get a notification when something puts a background application running in the background.
(00:46:02):
Ah, which is nice. That's a nice security feature. And Chrome pops that up all the time. They're always, or it's Google, but I think it's from Chrome. Google's always putting something in the background and I don't like the idea that Google's running stuff in the background. No, on my, on my Mac. So the, my mistake putting Chrome on there and only did it because there was a website that said, well, you gotta use Chrome, which is kind of inexcusable in this day in age, frankly. Yeah, really. I think it's time for our second break. Well, I think you're right. And then, then we're gonna talk about some announcements from one password and about what Russia has done. All right. Wow. Yeah, I wanna talk about PlexTrac, the Purple Demon platform. Lots of people have you know, security teams.
(00:46:50):
They might have a, you might, you or your somebody you work for might have a red team to discover, to pen test, to discover flaws. You might have a blue team to remediate those flaws. You might even have a purple team that's in the, between the two to communicate one to the other. And I betcha if you have a purple team, they know about PlexTrac, in fact, they're probably using it. Plextrac is the premier cybersecurity reporting and collaboration platform, which completely transforms the way cybersecurity work gets done. Even if you didn't have a purple team, maybe you only have one team that does everything tests and remediates, that's probably the most common situation. You need PlexTrac. You've gotta report your findings, you've gotta display them in a visual way. You might be spending a lot of time getting data from a tool, importing it into a, you know, a Word document or, and then, and then into another d and an e Plex track.
(00:47:47):
Does it all, are you ready to gain control of your tools, build more actionable reports, focus on the right remediation? Are you working to mature your security posture? And, and frankly, you ought to be. Do what mature security teams do. Use PlexTrac, optimize efficiency, facilitate collaboration within your team. Plextrac is a solution for you. It's a powerful and yet easy to use, very simple cybersecurity platform that centralizes all your security assessments, your pen test reports, your audit findings, your vulnerability tracking into one place. So it's easy to remediate. Plextrac transforms the risk management life cycle, allowing security teams to generate better reports, faster to aggregate and visualize. Visualize is important word when you're talking to the C-Suite, right? Analytics and collaborate on remediation, collaborate, that's another important word in real time. The PlexTrac platform addresses pain points across the spectrum of security team workflows and roles.
(00:48:52):
There's no better tool for managing offensive testing. In fact, once, once the, once these red teams start using PlexTrac, they go, whoa, we're never going back. It makes it easy to manage the testing and then report the findings. You can put code samples in screenshots videos. They can be added to any finding. You could import finding from all the tools you use, Nesta, burp, whatever, import 'em right in. So it streamlines that workflow. Plus you can create custom templates because you're probably doing the same thing again and again and again. Create templates so that with a, with a click of the button, it pulls the data in and creates the report. You spend less time typing. Analytics and service level agreement functions will help you visualize your security posture so you can quickly assess and prioritize to ensure you're tracking remediation efforts to show progress over time.
(00:49:44):
It's got built-in compatibility with all the leading tools and frameworks, including vulnerability scanners, pen testing as a service platforms bug bounty tools, adversary emulation plans. It means you can improve the effectiveness and efficiency of your current workflow. Robust integrations with Jira and ServiceNow ensure you're always closing the loop on the highest priority findings. It just, it just makes everything work easier and better. Enterprise security teams will use PlexTrac to streamline their pen tests and their security assessments and incident response reports. And, and a lot more PlexTrac clients say they're getting up to a 60% reduction in the time spent reporting. A 30% increase in efficiency and five x R o I in year one. In year one. All in all, PlexTrac provides a single source of truth for all stakeholders transforming the cybersecurity management life cycle. You really need this tool. I'll tell you what, book a demo today, see how much time PlexTrac could save your team.
(00:50:50):
You could even try it free for a month. P L E X T r a c.com/t w i t see how it can improve the effectiveness and efficiency of your security team. Just go to plex track.com/twi claim that free month. Really, when I talk to people again and again who've, who've tried PlexTrac, who've switched to it, they, they just, they swear by it. Wouldn't you like to swear by your tools instead of swearing adam plex track.com/t W I t. Please use that address so they know you saw it here. That's really important to us. Plex track.com/twi and thank you PlexTrac for believing in Steve and security now and supporting the show. We really, really appreciate that. Plex track.com/twi. On we go, Steve. Yay. So after we recently noted bit warden's acquisition of an open source passkey developer with, you know, the outlook for PAs key's support from bit warden looking good, I wanted to also note that one password has also just announced their support for Paske and interestingly, not as a holder of their user's private keys, which they had talked about doing before, but as a way for users to unlock their password vaults without needing to enter a master password.
(00:52:19):
In other words, whereas biometrics, for example, are often used for convenience as it means of unlocking a previously supplied master password. What one password will be doing is actually using PA keys itself to fully replace all use of a master password just as passkey should be used. They, as I said, they previously said that sometime in early 2023, meaning this year they planned to become a pass keys aware password manager, meaning that they would be maintaining their user's list of private pass keys. This is what we're, you know, we're hoping for from all of the major password managers. And it's a feature that they're all gonna need to support as PAs keys begins to happen, hoping that it does, you know, as we know, the unfortunate adoption of PAs keys, which is based upon 5 0 2, means that users will still need to manage their private passkey keys.
(00:53:25):
You know, right now we're managing our passwords that changes to pass keys. And this means that just as we have it now, centralized cloud storage synchronization remains a practical requirement. And as we talked about this when it was announced, apple, Google and Microsoft will be doing this for their users within their own closed ecosystems. But really practical use requires a platform agnostic solution, which is what the third party pla pa password managers will provide. So anyway, just a bit of news from one password. I know that we have a lot of listeners who are using it.
(00:54:04):
We have a new term entering our lexicon, Russian patriotic hackers. Ugh. Huh. The Russian government get this has stated that it is exploring the possibility of absolving Russian patriotic hackers from all criminal liability for attacks carried out in the interests of the Russian Federation. Wow. Russia is choosing to become a true fully western hostile outlaw nation. The head of the state Duma Committee on Information Policy, Alexander Stein told reporters at a press conference on Friday that an exemption would be granted to individuals located both abroad and within Russia's borders alike. Stein said, as quoted by RIA and TAs, he said, quote, we will talk in more detail when it receives more of a clear wording, unquote. So it's, you know, it's always been the, the case that the creation use and distribution of malicious computer software was punishable in Russia with up to seven years in prison.
(00:55:34):
And since there have never been any exemptions to this law, many of the current pro Kremlin activist groups are technically breaking Russian law and could face prosecution, especially in the aftermath of a possible regime change. And, you know, on the idea of a regime change, nothing would make many of us happier. But this forthcoming exemption would allow pro Kremlin hacktivists to carry out a tax with a legal cart blanche, presumably applying to groups who attack Russia's enemies, thus defining their alliance as being pro Kremlin. So wow. Basically Russia's saying, yeah as long as hackers, Russian hackers, wherever you are, are attacking our enemies, that's fine. Go ahead and do it. Where, you know, we have our, I mean, not only, you know, tacit approval, but now explicit exemption Yeah. From prosecution under Russian law. Yeah. I mean, we always suspected this, but now it's obvious.
(00:56:44):
It's yes, it's out. Yes. Now, now it's policy as opposed to, wow. Oh, what <laugh>? Wow. So in wonderfully welcome news, that immediately begs the question, what the hell took them so long <laugh> though, in fairness, that is a question that we ask on this podcast almost as often as we ask what could possibly go wrong. A w s has announced that, believe it or not, newly created instances of S3 online storage will be secured by default. What a concept you, you create a new S3 bucket and it's gonna be secure by default rather than insecure. I haven't seen this mentioned anywhere in the press yet, but I received a notice directly from Amazon because I'm an A W S three subscriber. I use AWS as my sort of my master cloud cold storage archive. By that I mean that I rarely transact with it. For example, I have a huge amount of static data sitting there.
(00:58:01):
Many years ago I ripped and stored my lifelong collection of prized audio CDs for safety. The uncompressed wave files are stored in multiple locations, and one of those locations is s3. Every month I receive Amazon's storage bill and I just shake my head since it's like $2 and 53 cents because most of what Amazon charges for is bandwidth usage and mine is zero. So S3 is, you know, for like that kind of offsite glacial storage is, it's a bargain. Anyway. As a consequence of being an s an A W S S3 subscriber, I received some very welcome news via email last Tuesday. Amazon wrote, hello. We are reaching out to inform you that starting in April, 2023, Amazon S3 will change the default security configuration for all new S3 buckets. For new buckets created after this date, S3 S block public access will be enabled. <Laugh>. How could somebody even write this email with a straight face?
(00:59:18):
It's just <laugh>. Just astonishing. As a, you know, we're FairWarning starting at April 23. We're going, you know, turn on security. Wow. block public access will be enabled. And they said, ed S3 access control lists will be disabled. Meaning that, you know, rather than having granular control over what's what, we're just gonna block all public access. So you don't need an acl. They said the majority of S3 use cases do not need public access or acls. Yeah, like I said, what the hell took them so long? They said, for most customers, no action is required. If you have use cases for public bucket access or the use of acls, you can disable block public access or enable ACLS after you create an S3 bucket. In these cases, you may need to update automation scripts, cloud formation templates, or other infrastructure configuration tools to configure these settings for you to learn more.
(01:00:26):
Read the a w s News blog link one and what's new announcement link two on this change or visit our user guide for S3 block Public Access link three, the S3 object ownership to disable ACLS link four. Also see our user guide for AW WS cloud formation. On these settings links five and six. If you have any questions or concerns, please reach out to AWS Sport Link seven. And for anyone who is an A Ws user did not perhaps receive this email, I have all the links there, all seven of them in the show notes. You know, and Wow, when you think back over the, the hundreds, it must be okay, we're episode nine. Okay. Maybe not hundreds. We're 910. We don't talk about a w s insecurity one out of every nine episodes, but okay. Many <laugh>, the many times we've talked about a w s being exposed and compromised on the internet, presumably without its owner's knowledge, the fact that block public access had never been active by default for a cloud storage provider just boggles the mind.
(01:01:46):
We kind of do that though, right? I mean, <laugh> oh my God, every so often that it's, it's, it is obvious that's the default. Yes. Right? It's the tyranny of the default. Yep. It's like we're, you know, users just assume that Amazon would not do this, and until now they happen. So, you know, again, props to them, but wow, what took you so long? Okay, so more anti-Chinese camera removals. The article appearing in the Australian last Thursday was titled Chinese Surveillance Cameras in Our Halls of Power. And it's apparently intended to induce concern because the article begins almost 1000 <laugh>. Oh my God. That's almost 1000 Chinese Communist Party linked surveillance cameras and other recording devices. Some banned in the US and Britain have been installed across Australian government buildings leading to calls for their urgent removal. Amid fears data could be fed back to Beijing government departments and agencies have revealed at least 913 cameras, intercoms electronic entry systems and video recorders developed and manufactured by controversial Chinese companies. Hick Vision and Dawa are operating across 250 sites, including in buildings occupied by sensitive agencies such as Defense, foreign Affairs, and the Attorney General's Department, Australia's five Eyes and a U K U S partners in Washington and London moved together in November to ban or restrict the installation of devices supplied by the two companies, which are both part owned by the Chinese Communist Party.
(01:03:46):
Okay. <laugh>, as we've previously covered, the US and the UK did take similar steps to remove the cameras produced by those two companies from their respective government networks. And yes, as we all know, in a closed design closed source world, it is possible for such devices to get up to some mischief. And I suppose that in some settings, you know, a stream of encrypted communications flowing across a government network might go unnoticed. I probably wouldn't surprise anyone, but more worrisome is that such a device might be a launching and jumping off point for malware that's waiting to spring as global political tensions rise. And as more and more of the physical world is subsumed by the cyber world, cyber protectionism seems inevitable. And we're certainly seeing its rise now since anything can be buried and hidden in the most innocent looking chip. There isn't any real defense against the But what if question because what if could be a true potential threat if a, if a competent technologist was to testify in front of a congressional committee on international cyber threats and was asked if they could absolutely positively assure that some device has no ability to do something malicious, they would have to answer no Senator, because <laugh>, you know, it's, it's possible.
(01:05:35):
You know, and so, you know, I I mean we're sort of stuck in this conundrum. I mean, I, I do think that there's no alternative than for vetted local technology companies to produce the technology that is being used by that local government. If, if the government wants as much assurance as possible, that there's no hanky pany in any of the technology that, that they're using. I mean, there just isn't any way around it. I mean, and you know, there's that, there's that paranoia factor. Leo, how many years have we, was that there, there, there was that n s a key that people thought was in Windows? Mm-Hmm. <affirmative>, it was like mm-hmm. <Affirmative>, no, it's just, it used the three letters, N sn a. Mm-Hmm. <affirmative>. Mm-Hmm. <affirmative>, you know, adjacently. And so that upset everybody besides, if the n SSA had a key, they wouldn't put their name on it.
(01:06:35):
They wouldn't, they wouldn't name it something else. So, wow. You know, a, a again there you can't prove a negative, right? So there's no reason to believe that any Chinese camera has ever misbehaved, but suddenly everyone's looking up at them, you know, oh gee, you know, is the com is the Chinese Communist Party spying on me through this camera? Probably not, but, you know, it could be. So, can't have that anymore. You'd need a lot of people monitoring those feeds. Yeah. I mean, that's a lot of work. That's a lot. You could have an AI monitor it, maybe, and looking for some kinds of things and I don't know. Yeah. Well, and again, you know, if, if anyone ever spotted the traffic flow from one of those, it would be game over. Yeah. You'd know. Yes. Yeah, it would be. Yeah. That's the end of it.
(01:07:31):
Right? So right now, it's never happened. Microsoft, believe it or not, is going to embed Adobe's Acrobat p d f reader into Edge. They announced that it would embed a acrobats PDF engine into future versions of their Edge browser. It'll be taking Place, place next month in March of 2023 for Edge versions on both Windows 10 and Windows 11. The F FAQ that Microsoft created for this announcement to accompany the announcement was unsure about when Edge for Mac Os would receive the same PDF reader. They just said, quote, availability for Mac OS is coming in the future. We will have more to share at a later date. So, since the current Edge P D F engine will be removed on March 31st, 2024, meaning a year from now, I guess both P D F engines will be cohabitating during this changeover period. And presumably users will have a choice.
(01:08:34):
And, you know, they were saying, you know, Adobe Acrobat P Reader is the original. Nothing does as good a job. Nothing renders fonts as accurately, so we're just gonna use theirs rather than, you know, who knows? Probably the, the, what, what's in there now is probably some descendant from Ghost Script or some, you know I guess it's open source, right? Because the, the, the chromium engine is able to render PDFs. So anyway, they, they decided to go proprietary and use the real Acrobat. So, okay. Okay. Now I've got some feedback from our listeners. And to everyone's credit, I think without exception, everybody was self-conscious about still wanting to talk about passwords <laugh>, because Wow, because last, last week I said, okay, we're done with this topic. Well, except we're not, because actually there were some interesting other twists that people have. It's probably the single most widely used security tool, right?
(01:09:40):
Yes. And that was my thinking, is it makes sense that people, this is of great interest to our listeners who are techy and are willing to, you know, really think about these things. And yes, you're right, Leo. It is, it is the one thing that everybody, it, it's everybody's collision with security is their password. So, a, whose handle is at Dutch physicist, he said, hi, Steve. Hope that's all. Hope that all is going well for you. I presume that you may not wanna get back to the passwords topic again. And as I said, everybody sort of opened with that. He said, however, I'm curious of an aspect with the one time passwords. They're based on a pre shared key. You've discussed plenty about the mobile app options and et cetera for storing those keys on the client side. However, I've not seen much discussions about the protection of those pre shared keys on the server side.
(01:10:42):
Are they protected in HSMs, you know, hardware security modules or some other mechanisms? I also have not heard of any breaches of those pre shared keys. Maybe I'm being too paranoid, but I would appreciate your view on this best. A so that's a great point. What one time pass codes were designed to prevent was the capture and reuse of a static password in, in the recent so-called credential stuffing attacks that we were talking about, where that large database was at billions of previously stolen pass u usernames and password combinations has been shown to be surprisingly effective due to people still reusing, you know, their password. I go, this is my password, and I use it everywhere at multiple web websites. So the success of this attempted reuse is blocked when despite reusing a password. The site also requires the use of a time varying six digit secret passcode.
(01:11:55):
The problem with these passcodes is as a noted that this still requires that every website keeps the shared secret secret. And this has historically been shown to be surprisingly difficult for websites to do. The inherent weakness of the one time passcode system is that it uses symmetric cryptography where each end shares the same secret. Another way of saying this is that the same secret is used to both create the passcode and to verify the passcode, and that's the weakness. What makes, for example, squirrel and web authen different is that by using asymmetric cryptography, each party in the system uses a different key. And the roles of the keys are different. The public key that's held by the website can only be used to verify an identity assertion created by using the user's private key. As I often said, squirrel gives websites no secrets to keep.
(01:13:09):
And web often is the same by the use of asymmetric public key crypto. These systems, squirrel and web often only provide websites with a user's public key, which does not need to be kept secret since the only thing it can be used for is to verify a user's identity claim by comparison. A stolen symmetric key can also be used to assert a user's identity. If a website were to lose their one-time passcode symmetric keys, the bad guys can use those stolen keys to recreate the user's one-time passcode to spoof their identity and log in as them because the system is symmetric. But if bad guys were to steal a user's public authentication key from a website, you know, using web authen, it would be of zero use to them since only thing those keys can be used for is to verify a user's identity claim.
(01:14:18):
That's a huge difference. Once this improved system, the asymmetric system is universally deployed, hopefully it will be someday online identity authentication will be significantly improved. Until then, we will continue to see escalations in attack cleverness with the increased use of one-time passcodes. We've seen the bad guy circumvent its protections with the increased use of proxying attacks where the user is visiting a spoofed intermediate page, which prompts four receives and forwards the user's one-time passcode on the fly, thus successfully accomplishing a real-time bypass of one-time passcode security. Anyway, great question. James Howley, he said, when I first switched from last pass to bid warden, I also decided to keep using OTP off for my one-time codes. While listening to SN 9 0 9, I wondered if bid warden might be a better choice for some, because it would only have a one-time code for the domain. It is registered to the same way a password manager prevents putting a password into a spoofed website.
(01:15:39):
Oh, ah-huh <affirmative>, that's interesting. That is a really good point, which had not occurred to me before. So thank you for that, James. So, okay, now we have a dilemma. Giving your one-time passcode secrets to a password manager to use risks exposure of those secrets since they're no longer in a disconnected offline device, you get the benefit of cross-device synchronization that's useful, but again, the secrets need to be kept secret. But as James points out, the advantage of using a strict U R L matching deployment of those one-time passcodes is that unlike an unwitting user, the password manager would not be spoofed by a lookalike domain name. Okay? But since we assume that the password manager's anti spoofing protection would first apply to, its not gratuitously filling out the username and password on a spoofed site, we don't really also need it not to fill out our one-time passcode.
(01:16:56):
It already protects us from divulging the first phase of our credentials. So on balance, while I think that's a, that's a, that's a certainly worth observing that I think that keeping time passcodes separate still provides optimal security. But you know, definitely a interesting thought experiment. Okay, our VMware listener asking for anonymity sent to me. Hi Steve. I'm a longtime listener of security now and now work at VMware on E S X I. Naturally, I just wanted to add a couple of comments on the most recent ES X I ARGs discussion. Overall, I thought the discussion was good, but I was a bit taken aback by the suggestion that VMware scanned the internet for exposed ES XI servers. You've never suggested such a thing for any other vendor, even Microsoft or qap earlier in the episode. It definitely seems like it could work on a voluntary opt-in basis, but otherwise it seems untenable to me.
(01:18:06):
It's been talked about quite a bit in the past in various contexts, but it's rather difficult at times to figure out who to contact if a vulnerable host is found. While I agree in theory that it would be nice if there was a quick and easy way to contact system admins of a particular system that's directly exposed to the internet, it's quite difficult in practice, especially in a way that doesn't have far reaching privacy implications. Fortunately, there is, oh, I'm sorry. Furthermore, there is a free version of E S X I, which is popular with hobbyists and who, and those just wanting to run VMs on a single server ES x I is not just used by enterprises and IT professionals. On a brighter note, he said, I'm happy to report that starting in E S X I 8.0, all demons and long-running processes are sandboxed by default.
(01:19:07):
And we've also added additional hardening to make it harder to run E L F binaries that don't come from the installed base system packages. So this is very cool to hear from someone at VMware. And as we note he's right that I haven't previously been suggesting that all vendors proactively scan the internet looking for vulnerable versions of their own software. But I truly think that this is something that we need to think about in the future. I have mentioned on several occasions that there is little doubt that malicious actors and likely state level agencies are already scanning the internet to create quick reaction databases of what is where, so that when a high profile vulnerability is found, targeted attacks can be rapidly deployed. Why should only the bad guys have such databases? Once upon a time, internet scanning itself wAsconsidered a hostile act when I first created the Shields Up system, which was 24 years ago in September of 1999.
(01:20:19):
And Leo, you were doing screensavers at Tech TV at the right time. That's right, yep. I was periodically contacted by various network admins who were wondering why my ips were probing their networks <laugh>. I explained that it was their own users inside their networks who were requesting that I check on the state of their network security in most cases back then, they politely asked that I not honor such requests. So Shields up has always had a do not scan list of, of blocked ips, which it refuses to probe. And if someone tries to do that from, in that such a network, it just pops up a notice and says your administrators, the administrators of your network have requested that shields up not probe their networks. So, you know, go talk to them. Okay? But if such a system like Shields up were to be launched today, 24 years later, not a single peep would be heard from anyone.
(01:21:33):
The network admins of the world have all collectively given up on the entire idea of identifying all of the random crap or really any of the random crap that's now flying across the internet. I mean, you know, there are still instances of code RED and NMDA infected Windows NT servers sending out packets. Mm-Hmm. <affirmative>, you know, looking for a vulnerable system, you know, and it was in, it was in acknowledgement of this that I eventually coined the term internet background radiation, you know, og a neutrino just whizz through my body. Where did it come from? Well, who knows? And who cares? <Laugh> A Nim Neutrino. <Laugh>. That's right. A nmda Nu Neutrino <laugh>. So my point is, scanning the internet was once unusual. An attention getting it is no longer. And we've recently been talking about the moves we're seeing of multiple governments beginning to take the security of their own nation's networks into their own hands.
(01:22:40):
So our VMware listener is correct, but I have not been suggesting that other private vendors should be doing this. But something needs to change. You know, it would be amazing and wonderful if qap were to maintain a list of publicly exposed instances of their always buggy systems. At the same time, our listener brings up actually the most important point, which is, okay, what then? How do they contact the owners of the system that's publicly exposed? Bad guys don't need to contact anyone since they wanna attack the systems. But good guys do need to contact someone since they wanna remediate the trouble.
(01:23:29):
The good news is our VMware listener said quote, it's been talked about quite a bit in the past in various contexts, but it's rather difficult at times to figure out who to contact if a vulnerable host is found. So I guess the good news is the idea is sort of in the air, you know, but he's also correct about the privacy implications, which follow from any attempt to somehow make endpoints identifiable to everyone on the public internet, right? Cuz they've, they've got, they would have to be ev everybody or no one. So we're left with the conundrum, which is created by the asymmetry of the fact that bad guys want to attack exposed systems while good guys only want to inform them. You know, and I am, you know, thankful that our vm VMware listeners spoke up. Thank you. And I don't think there's a good answer right now, but the way things are going, it seems like we need one.
(01:24:30):
Brad Jones, he said, Steve, I know we're all tired of talking about the security of our passwords, but I'm interested in your thoughts on the following. Selecting a known bit warden master password that is already considered somewhat secure, then running it through something like a Base 64 calculator to generate an actual password used to unlock the vault. As you would likely never remember the password, anytime you need to unlock, you would run the known password through the calculator to generate the vault password, for example. Although clearly you would never use password 1, 2, 3, 4, 5, 6, 7, 8, that would generate the password you would use as your master password, which is, and then he has the, the base 64 conversion, capital U, capital G, capital F, lowercase Z, C three, DVC M, capital Q, lowercase X, and blah, blah, blah. You know, gibberish. He says there are many desktop and mobile applications that can complete this calculation without running the known password through an online encoder or decoder.
(01:25:44):
Okay, so algorithmic password generators are an interesting idea. The concept was to use an H Mac function, which is essentially a keyed hash function. So the user would generate a single secret permanent key, which would key the hash function. They would then enter, for example, the domain they're visiting into the hash function, and it would output an absolutely maximum entropy password. Since every domain would produce a different unique password, there would be no password reuse. And there would also be nothing to remember per domain. Since any domain's password, any domain's password could be recreated on demand from the domain name itself. And actually, this is, this was part of the, the, the, this was the germ of the idea of how squirrel converts domain names into into private keys, which are then turned into public keys. And, but even before that, this idea intrigued me so much that I wondered whether it might be possible to create a truly secure paper-based encryption system.
(01:27:08):
Our longtime listeners may recall that the idea I hit upon and then developed was to traverse a per user customized Latin square. I called the system off the grid since the passwords came from a grid and the system was offline and used no electricity. So anyway, Brad's idea was, is right that, you know, you know, to suggest yet another means of generating unique per site passwords that would that that could be deployed using an algorithmic, an algorithmic system based on something that could be input. And if you used a secret key and a hash function you could just use the domain as, as a place to start. Okay, Leo, our final break, and then I am going to introduce our listeners to something very new and very cool acon, which has just received N I S T standards. Ooh, endorsement. It is a new NIST standard for cryptography. All right. Careful what you're asking for ask. You might get it right off what you can do for your <laugh> <laugh>.
(01:28:28):
First the word from, for F O R T R A, you don't maybe know the name for, but for 40 years, help Systems is known, has been known for helping organizations become more secure and autonomous. Over the years, customers have shared that Help Systems has been so helpful, but it's still getting harder and harder to protect their data. Oh, that's true, isn't it? If you listen to this show, you know, cyber threats evolve. They're more powerful than ever before in an industry where the only constant is change, it turns out adaptability is the best way to grow in the right direction. Help system listen to their customer's concerns, problem solved and delivered with impressive results. And consequently, they are adapting a different company today, help Systems. Very important now is now Fortra your cybersecurity Ally, F O R T R A for continues the same people first support and best in class portfolio that you've come to expect from Help.
(01:29:36):
Systems Fork transformed the industry by creating a stronger line of defense from a single provider. They work with the top 10 Fortune 500 banks, the top 10 of the Fortune 500 banks in the world to keep them secure. That's a pretty good endorsement, don't you think? For, for forres. Infrastructure also helps support kind of mission critical installations like nuclear power grids and other important utility services. I think that's a pretty good endorsement for, for fortress's. Key area, I should say, really areas of e of emphasis where technology meets humanity include securing infrastructure, securing that's important on the grid, isn't it? Sec. And, and nuclear power plants. Securing infrastructure, securing data that's important for everybody. Security awareness and operational support. So let me talk about the different things for can do for you. They've got professional security services. You know, everybody these days has, has somebody on their team that's looking out for security.
(01:30:42):
But you, you probably can use some help from forrey. You can get help with pen testing services. They have security consulting services. Always good to get a second opinion, right? Social engineering services help train you and your team how to avoid getting fished, for instance. They also can do red teaming exercises. You know, it's one thing to have a red team on your team, but you bring in the pros from Dover, the guys from outside to come in and, and attack your system. <Laugh>, that, that gets everybody on their toes, doesn't it? You bet. For also has managed security services, including managed detection and response, managed data loss prevention, and IBM I security services. So you can use for for, you know, consultancy. You can use them as an additional part of your security team, but you'll know one thing throughout every step of your journey.
(01:31:41):
Fortress experts are there determined to help increase security maturity while decreasing this is important, the operational burden that comes with it. See, sometimes you say, oh, I can't afford to be more secure. You need for, you can for understands we're all more powerful together. So they prioritize collaboration with customers throughout every step of their cybersecurity journey. And every customer is unique. Fortune knows that for organizations, fortune knows the road to creating a stronger, simpler future for cybersecurity begins with that daily commitment to listening to each individual concern and providing integrated scalable services. They are there for you with you. Check out all the critical solutions and experts that for family has to offer, including through the combined intel of Fortress, Zari and Fish Labs solution. I'm sure you've heard of them. Fortress Quarterly Threat Trends and Intelligence Report. Oh man, that is a super valuable resource that gives you an analysis of, you know, what's going on right now.
(01:32:45):
The latest findings, insights into key trends shaping the threat landscape. You can't sit back and say, oh, I know everything that's happening. You gotta, you gotta keep up, right? Fortress approach is different in pursuit of a better future for cybersecurity. They're driven by the belief that nothing is unsolvable Fortra positive changemakers and your relentless ally in providing peace of mind through every step of your cybersecurity journey. Does that sound good to you? It should. Positive changemakers your relentless ally, providing peace of mind through every step of your cybersecurity journey. Set yourself up for success. Go to for.com. Check out one of their free trials or demos today. You owe it to yourself to learn more about for, for 40 years as help systems. They've been doing this job. They are on top of the modern latest technologies. They're here to be your ally for here's to a stronger, simpler future for cyber security.
(01:33:44):
Who's in, are you in? Visit for.com to learn more. F O R T R A for.com. F O R T R A for.com. We thank of so much for supporting security now. All right, I'm ready to, I'm, I'm asking for a friend what is asking <laugh>? What is asking? Okay, so last Wednesday, the US National Institute of Standards and Technology, you know, our NIST announced that a family of authenticated encryption and hashing algorithms known collectively as, Ascon A S C O N will be standardized for applications in lightweight cryptography. A and lightweight cryptography does not mean less secure as, as we'll see. So I'll have a little bit more to say about that in a second. This final selection was a result of a four year competition, which ran from 2019 through just now 2023 among competing proposals. This was the same process that led us to the selection of the rhind cipher to become the official a e s standard.
(01:34:55):
So that's, you know, you know, rein dohl is, you know, military strength, if you'll pardon the expression Ashan has now become the standard for providing high 128 bit security for low end lower end devices. So, you know, and for example, there's an entire suite of symmetric cryptographic ason functions for the Arduino already exist. So NIST summarized the, the competitive selection process by writing. NIST has initiated a process to solicit, evaluate and standardize lightweight cryptographic algorithms that are suitable for use in constrained environments where the performance of current NIST cryptographic standards is not acceptable. In August, 2018, NIST published a call for algorithms to be considered for lightweight cryptographic standards with akin authenticated encryption with associated data. That's, you know, authenticated encryption associated data. A E A D we'll we'll get to more of that in a second. An optional hashing functionalities. The deadline for submitting algorithms has passed.
(01:36:15):
NIST received 57 submissions to be considered for standardization. After the initial review of the submissions, 56 were selected as first round candidates of the 56 first round candidates, 32 were selected to advance to round two. So they were, you know, whittling them down. Okay, so what exactly does lightweight crypto mean? Rather than aiming for the highest conceivably needed security, which will be adequate to protect data for, you know, the next several decades, at least, NIST's lightweight cryptography competition, was it up to select the contemporary crypto system that would be best suited for deployment on today's much more limited i o T systems. This means that, for example, while sharing the same 128 bit block length as the rhind dohl, a e s cipher, you know, because a cypher's block length really cannot be reduced much below 1 28 bits without compromising security, the key lengths can safely be reduced by half to 128 bits.
(01:37:30):
This allowed the use of a family of faster, more efficient and easier to implement algorithms, which can run efficiently on much lighter weight hardware. Okay? Now, some have wondered whether dropping the key length in half to 1 28 bits is sufficient for contemporary security. The fact is, it's still insanely, plenty of security. We only went to 256 bit keys because why not? If we have desktop and server machines, and there's virtually, you know, on those platforms, virtually no cost for doubling the key length. You know, on the other hand, those are, those are expensive algorithms, which is why Intel has now specific a e es instructions because some of the things that a E ES requires the processor to do are extremely time consuming. So Intel said, okay, let's put some instructions to, to speed up a E es into our micro code. And they've been there now for a while.
(01:38:43):
Well, if a e s weren't hard to do, Intel would've never done, you know, cipher specific instructions Ascon doesn't need any of that as, as an example. So the point is, we did 2 56 bits because we could, so let's examine the implications first of 1 28 bits, two to the 1 28, right? The number of combinations, the number of possible keys, that's 3.4 times 10 to the 38th. So that's, you know, 34, followed by 37 37 zeros. Okay? Now say that we wanna brute force the keys value, and for the sake of argument, let's say that it would be possible it's not, but say that it would be possible to completely test a candidate key at the full clock rate, say 3.4 gigahertz of A G P U. You know, it's not, possibly, it's not possible to actually do that since A G P U fast, as they are still require many clock cycles to get any work done.
(01:39:55):
But for the sake of this thought experiment, say that it was possible to fully test 1 2 56 bit key every clock cycle at 3.4 giga tests per second. Okay? So that's 3.4 times 10 to the nine, right? 3.4 gigahertz giga test per second brute force tests per second each, each clock cycle. We're, we're doing a brute force test. We can't, but for the argument, let's say we could, to test all possible 128 bit keys where there are 3.4 times 10 to the 38 possible keys, we divide 3.4 times 10 to the 38th by 3.4 giga tests per second. That's 3.4 times 10 at the ninth. So we just subtract nine from 38 yielding 29. This tells us that testing candidate keys 128 bit candidate keys at the rate of 3.4 billion tests per second, which no actual system is even capable of coming close to doing, we would need 10 to the 29 seconds to brute force all combinations.
(01:41:13):
Okay? Now there are only 31.5 million seconds per year. If we triple that, it brings us to 94.5 million, which is close to a hundred million. So we'll round that up to 10 to the eighth, which is a hundred million. So eight from 29 leaves, 21. Thus brute forcing a 1 28 bit secret key at 3.4 billion guesses per second, which is not possible, would require roughly three times 10 to the 21 years. Given that we all generally live less than 10 to the two years we're left with plenty of security margin. In other words, 1 28 bit security. Although, you know, we're so used to talking about, you know, thousands of bits for asymmetric key strength and 2 56 bits or more for a ES and rhind 1 28 bit security is an insanely ample amount of security. And now thanks to this device constrained cryptographic competition, we have this super strong security available to lightweight embedded processors, ns, which don't need any special instructions cuz it's all simple.
(01:42:43):
NIST's original call for submissions, explained their target, you know, their need as follows. They said, the deployment of small computing devices such as R F I D tags, industrial controllers, sensor nodes, and smart cards is becoming much more common. The shift from desktop computers to small devices brings a wide range of new security and privacy concerns in many conventional cryptographic standards. The trade off between security performance and resource requirements was optimized for desktop and server environments. And this makes them difficult or impossible to implement in resource constrained devices when they could be implemented, their performance may not be acceptable. Lightweight cryptography is a subfield of cryptography that aims to provide solutions tailored for resource constrained devices. There's been a significant amount of work done by the academic community related to lightweight cryptography. This includes efficient implementations of conventional cryptography standards and the design and analysis of new lightweight primitives and protocols.
(01:44:04):
Okay, so the winner was acon, a family of authenticated encryption and hashing algorithms, which are not only designed to be lightweight and easy to implement, but also with added countermeasures against side channel attacks. And ason was not only selected to be NIST's new lightweight crypto standard, but it was also pre, it also previously won the same spot in the Caesar competition, which ran for five years, from 2014 through 2019. Caesar, C A E S A R is the acronym for com for competition for authenticated encryption, security applicability and robustness. And yes, that's clearly one of those reverse engineered acronyms that's always a bit awkward. So ACON is also Caesar's primary choice for lightweight authenticated encryption. And of course, during the N I S T competition, it was already obvious that ACON had won the Caesar competition since that closed in 2019. So really the question was, is there anything more that we know now subsequent to the Caesar competition that is better than ashcon?
(01:45:28):
And the answer? No, you know, there were more than 50 submissions of other things, and Ascon was it, you know, and I've, I've mentioned authenticated encryption here. We've talked about the need in the past for both encrypting the data for privacy and also authenticating the data to prevent its manipulation at any time. And assuming that the two steps of encryption and authentication are separate as they were originally, we've examined the question of in which order the two operations should be accomplished. The universal agreement is that you first encrypt and then you apply authentication to the encrypted result. The reason is on the receiving decrypting end, the message is first authenticated to assure it has not been tampered with, not modified in any way, and only if it authenticates should the message then be decrypted. This prevents the use of some very subtle attacks that we discussed years ago, but the use of so-called authenticated encryption offers a better solution.
(01:46:44):
As his name implies, authentic encrypt authenticated encryption algorithms are able to perform both operations at the same time. And there's one very valuable extension to this known as authenticated encryption and associated data or a E A D for short. A E A D algorithms allow the so-called associated data to remain unencrypted and in the clear, while still being encapsulated within the authentication envelope. So you can see it, but you can't change it. I have some experience using these algorithms since squirrels local on disk identity storage format needed to have some local storage, which would always be left un well, some that would be kept encrypted on the disk, but also some other that, for example, the users settings, which would need to be available all the time, even without the user's key and the whole thing, you know, the, the, the entire the entire package needed to be tamper-proof.
(01:47:58):
So I chose to use the A E S G C M cipher, which is an A E A D cipher. This perfectly resolved the need for having both secret and non-SEC data that could not be altered without breaking the authentication of the whole. So in any event, what we're getting is in this lightweight competition is an A E A D cipher, which is gonna be extremely useful. It's what NIST wanted, and it's the contest winning technology that ason provides to IOT devices. It also brings and provides similar features to hashing because Ason did also offer a hashing technology and actually a lot more. It was designed by team of cryptographers from the GRA University of Technologies in Phon Technologies, Lamar Security Research and Rabu University. So it's bullet points that is of its benefits are authenticated, encryption and hashing with fixed or variable output length with a single lightweight permutation.
(01:49:07):
And I'll be talking about this permutation in a second. Provably secure mode with keyed finalization for additional robustness. Easy to implement in a hardware and software lightweight for constrained devices. It's got small state meaning not much a storage needed, a simple permutation box and robust mode, fast and hardware fast and software pipe liable, bit sliced. It has a bit sliced five bit s box for 64 bit architectures scalable for more conservative security or higher throughput timing resistance. No table lookups or additions side channel resistance. The S box is optimized for countermeasures. The key size equals the tag size equals the security level. That is their all 1 28 bits, minimal overhead. The cipher ti, the cipher text length equals the plain text length. So there's the, there's no padding needed, single pass online encryption and decryption. And it uses anot. So the NIST requirements were for a key size, no shorter than 1 28 bits, and there could be a family of variance having different parameter lengths.
(01:50:29):
The design targets were interesting. NIST wrote, submitted A E A D. Algorithms and optional hash function algorithms should perform significantly better in constrained environments, meaning hardware and embedded software platforms. Compared to current NIST standards. They should be optimized to be efficient for short messages as short as eight bites. Compact hardware implementations and embedded software implementations with low RAM and ROM usage should be possible. The performance on asic, you know, application specific integrated circuits on ASIC and F P G A should consider a wide range of standard cell libraries. The algorithms should be flexible to support various implementation strategies. Low energy, low power, low latency. The performance on micro controllers should consider a wide range of eight bit, 16 bit and 32 bit microcontroller architectures for algorithms that have a key, the pre-processing of a key in terms of computation time and memory footprint should be efficient.
(01:51:43):
The implementations of the A E A D algorithms and the optional hash function algorithms should lend themselves to countermeasures against various side channel attacks, including timing attacks, simple and differential power analysis and simple and different differential electromagnetic analysis designs may make trade-offs between various performance requirements. A submission is allowed to prioritize certain performance requirements over others to satisfy the stringent limitations of some constrained environments. It may not be possible to meet all performance requirements stated in the previous paragraph. The submission document should, however, explain the bottlenecks that were identified and the trade-offs that were made. And basically no trade-offs were necessary. Ashan does it all. So we now have a new family of power, memory and general resource efficient algorithms that have been studied and pounded on now for years by many academics. And cryptographers GitHub offers implementations in c c with some assembly, Python, j, Java, and rust.
(01:52:56):
And there's also risk five implementations as well. I have links to everything here in the show notes. Github also has an ason suite of cryptographic functions all based on what's known as, and I mentioned this before, the ason permutation. The permutation is the core cryptographic function at the heart of Ason. Highly efficient, super secure. Now proven that GitHub page provides the open source code for the following functions. We've got, of course, authenticated encryption with associated data. We've got hashing, we've got a pseudo random function, a message authentication code, an H Mac based key derivation function, hashed message, authentication code, you know, H Mac. We have a e A D most with side channel protections. We've got a keyed message, authentication code, a kmac, password based key derivation functions, P B K D F A, pseudorandom number generator, synthetic initialization, vector, extensible output functions, and direct access to the ACON permutation.
(01:54:09):
All of those are available through the a p i of, of the code here at, at the it's gi github.com/rwe, R w e a t h e r slash acon hyphen suite. And a related page with all of the same functions for the Arduino. So the industry, as I said, has a robust and seriously secure set of lightweight functions which have already been poured to many languages, platforms and hardware, which are tuned for and suited for the needs of embedded resource constrained iot style devices. And I obviously already made the case that 128 bit key length, that is just fine. It'll last us our lifetime and well, what, 10 to the 18 times more. So why not just replace a Es? Why not replace rein dohl with this? You really could. The, I mean the, the, I think they, they, they went high.
(01:55:12):
Rein DOHL is available in 2 56 bit, 3 84 bit and five 12 bit key lengths. So you could just go insane <laugh> with rein Dohl <laugh>. You know, I, I agree. I I, you know do you need to, I guess is the question and, and even if you went to five 12, would it survive a quantum computer? Well, this is all symmetric and quantum computers. Oh, it doesn't matter. Do not attack symmetric ciphers at all. Right? Right. Okay. Yeah. So if I have any need in the future, I'll be using these because, you know, ason, it's had, its you know, it, it's, it's, it's been really picked over now for many years. And you can imagine that the, the 50 other submissions, they were tr they were trying to find a problem with Ashan in order to have theirs chosen, but they couldn't. I think, you know, this would be good for pgp to replace. I think they're using triple desk for the symmetric key. It would be a nice, yeah, nice improvement. <Laugh>, yeah. Not that speed is a big issue, but still just something that's easier to implement maybe. And it's interesting Ascon Yeah. Huh? We have it now. We got it.
(01:56:31):
Thanks to our weather, whoever that is, is our weather a person or is it I didn't look. Yeah. to, to, to see, but, but basically you're taking the, the, the core innovation, which is this permutation box, which is well defined, and then you're building all these other functions around it. Yeah. And we sort of know how to do that now. Get the feeling our weather's a person who's just really good, be might at this stuff. Yeah. He may have just done an an implementation of these functions. Yeah. Interesting. Wow. You know what, this is great. You learn so much. Listen to this show and you stay up to date. And I know that's why so many people in cybersecurity and it listen to security now, and we're glad you do. I hope you'll keep listening. Get a copy of this show from Steve.
(01:57:21):
Probably the best way to get the Bandwidth Impaired 16 kilobit version <laugh> or the transcripts. He's got he's got human written transcripts, which is very nice to read along or use for searching all 910 episodes. That's all@grc.com. While you're there, pick up Spin, right World's best mass Storage, recovery and maintenance utility, six point ohs, the current version. But 6.1 is imminent. If you buy now, you'll get a co upgrade to 6.1 for free. So do that. You can also participate in the development of 6.1 and there's lots of other great free stuff, including a chance to leave your feedback for Steve grc.com/feedback. He also is on Twitter and his dms are open at sg grc at SG G R C. We have copies of the show on our website, TWI tv slash sn. There's 64 Kilobit audio in our unique form video. So you can see Steve's giant mug, <laugh> in, in the flesh, as it were, <laugh> go to twit tv slash sn.
(01:58:28):
There's a Security now YouTube channel dedicated. You could also subscribe in your favorite podcast player. It doesn't matter. Steve's site or our site subscribe. It'll get the same high quality version of the show. And it all counts towards downloads. So we appreciate that. Let's see, what else should I tell you about? Oh, if you wanna watch us do it live, that's the freshest version that doesn't, we don't really count the, the number of people watching live. So if you're gonna do that, please download a copy anyway, that way you got it for your library and all that. But if you wanna watch live, we do it every Tuesday right after Mac Break Weekly. That's usually between one 30 and 2:00 PM Pacific, 5:00 PM Eastern. Be 2200 UTC if you wanna watch live at Live TWI tv. If you're watching Live chat, live in our irc, our Internet Relay Chat.
(01:59:18):
Yes, traditional old school baby IRC twit tv. If you wanna be a little more modern, we have a Discord chat for our club members. That's a great hang too, by the way, all day long and all night long. A great hang, it's a great hang man. Go <laugh>. But you gotta be a member. Seven bucks a month. What do you get? Ad free versions of everything, including this show. You get the discord, you get the Twi plus feed with shows we don't put out anywhere else. Like hands on Mac with Micah, Sergeant Hands on Windows with Paul Thro, the Untitled Linnux show, the Gizz Fizz Stacy's book club, a whole lot more. All the interviews and specials we do as well. TWIT TV slash club twit, if you don't yet a subscriber, do us a solid it, it makes a big difference to our bottom line. Right now we have about 6,000 members. There are 700,000 people who listen every month to our shows. If we could just get 10%, we wouldn't even need ads. We could just say it's done, we're happy. And the other 90% could continue to enjoy <laugh> the the show ad free as well See, it's Easy. Twit.Tv/Club twi Steve, have a wonderful week. We will see you next week with another great edition of security. Now I'll be back.
Ant Pruitt (02:00:35):
Hey, what's going on everybody? I am ANn Pruitt and I am the host of Hands On Photography here on twit tv. I know you got yourself a fancy smartphone. You got yourself a fancy camera, but your pictures are still lacking. Can't quite figure out what the heck shutter speed means. Watch my show. I got you covered. Wanna know more about just the i i o and exposure triangle in general. Yeah, I got you covered. Or if you got all of that down, you want to get into lighting, you know, making things look better by changing the lights around you. I got you covered on that too. So check us out each and every Thursday here on the network. Go to twit tv slash hop and subscribe today.