Security Now Episode 901 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for security. Now Steve Gibson is here, and it's again, questions and answers. What browser Just added support for past keys. How can you recognize a totally fake cryptocurrency trading site? And has Apple finally given us the keys to encrypted data in the cloud? Steve analyzes it. All the security news. Next on Security Now podcasts you love
... (00:00:25):
From people you trust. This is TWiT.
Leo Laporte (00:00:33):
This is Security Now with Steve Gibson. Episode 901. Recorded Tuesday, December 13th, 2022. Apple encrypts the cloud. Security now is brought to you by Barracuda. Barracuda has identified 13 types of email threats and how cyber criminals use 'em every day. Fishing, conversation hijacking, ransomware plus 10 more tricks cyber criminals use to steal money from your company or personal information from your employees and customers. Get your free ebook at barracuda.com/securitynow. And by BitWarden. Get the password manager that offers a robust and cost effective solution that can drastically increase your chances of staying safe online. Get started with a free trial of a teams or enterprise plan, or get started for free across all devices as an individual user at bitwarden.com/twit. And by ExpressVPN, secure your family's online activity and unlock tons of new shows by visiting expressvpn.com/securitynow, take back your online privacy today.
(00:01:47):
Use our link to get three extra months free with a one year package. It's time for security now. Yay. You've been waiting all week, haven't you? Well, it's your good news. It's finally here. So is Steve Gibson from grc.com. Our host The Man of the Hour. Hi Steve. Yo Leo, great to be with you. Episode 9 0 1. And I was originally gonna talk about something else but this news hit and it was like, okay, you know, and a actually it was with by far the most tweeted question that I've had in a long time about any news. And that of course is Apple's announcement that they're going to begin encrypting iCloud. So Apple encrypts the cloud is today's topic, but we're, they don't, that's just what we're gonna wrap with. We're gonna answer a bunch of questions as we are now. <Laugh> po poised you over the last few weeks. What browser just added native support for pass keys and where are they stored? What service have I recommended that suffered a major multi-day service outage? I love, by the way, I love this question, question format. This is great,
Steve Gibson (00:03:00):
<Laugh>. It works. Yeah. Yeah. How can you recognize a totally fake cryptocurrency trading site? Which messaging platform has become cyber crimes favorite? And how would you go about monetizing desirable usernames? Hmm. What's the latest TikTok Legislative insanity. And is it insane? Which two major companies have been hit with class action lawsuits following security breaches? Was MetaBank leaked data truly useless? And Apple has finally given us the keys to our encrypted data in the cloud holding none for themselves or have they?
Leo Laporte (00:03:43):
Oh boy, that's a good one. That's a great question. Can't wait to hear that. I knew, you know, you, you, you texted me earlier that you were gonna cover this and I told everybody on Mac Break Weekly. Yeah, this Apple just rolled this out. I just turned it on on my phone. Well, actually I didn't cuz it said, before you turn it on, you have to get updates on all of your Apple devices, of which there are more than a dozen. So, which makes
Steve Gibson (00:04:06):
Sense. I'll, I'll talk about, I'll talk about that. You have, you cannot have any older versions. No, they all have to know about Yeah. This technology. So
Leo Laporte (00:04:13):
It's gonna take me out to go around a lot of stuff <laugh> and update it before I can do it, including my watch. But first let's talk about our sponsor of the hour and then we'll get to the picture of the week and the meet of our conversation with Steve Gibson. Our show today brought to you by, you know this name, well Barracuda the kings of email and just in general protection for you in your office. In a recent email trends survey Barracuda found that 43% of respondents said 43% said they'd been victims of a spearfishing attack. I think it's a hundred percent. And just the other, the other 57 didn't know. That's all I have. Have you, I guess maybe it depends on what you mean by victims. I didn't click, but I bet, you know, if those spearfishing account attacks went out against some of our employees, we might be subject only 23% of the respondents said they had actual dedicated spearfishing protection.
(00:05:16):
That means the rest of 'em are just counting on employees. Not to be fooled, that seems like a recipe to for a disaster. But Steve says, what could possibly go wrong? <Laugh>, how are you keeping your email secure? Barracuda has identified 13 different types of email threats and how cyber criminals use 'em every single day. There's phishing. Yeah, but there's also conversation hijacking. There's ransomware plus 10 more tricks cyber criminals use to steal money from your company or personal information from your employees and customers. Are you protected against all 13 types? Do you even know what they are? Could you name them? Email. Cyber crime is becoming more sophisticated. Attacks more difficult to prevent. We've seen that attacks use social engineering. They'll add urgency and fear to the message to get their victims to act without thinking it's, this is tough. I mean, who hasn't fallen almost at least fallen for some of these?
(00:06:12):
And then I know I've like, had my finger on the button and go, wait a minute, I'm not gonna click that link. Social engineering attacks not, not limited to spear phishing, but including spearfishing business email compromise cost businesses an average of $130,000 an incident. It's not cheap to remediate. And they could be worse than just money can be reputational damage. Right? And, and of course, they're gonna use what's in the news. When the demand for Covid 19 tests ramped up at the beginning of this year Barracuda researchers saw an increase in covid 19 test related phishing attacks, and they went up 521% between October of last year and January of this year. It makes sense, right? They're gonna, they're very topical. They're not, they're, they're not dumb. They're very talented. These guys crafting these spearfishing emails as public interest rise rose in crypto, for instance, last year crypto attacks went up 192% in the same period.
(00:07:14):
October, 2023, April, 2021. And, and all, I can go on and on and on. In fact, you just look at the headlines, you'll know what your next spearfishing attack is gonna be about. In 2020, the Internet Crime Complaint Center, IC three received 19,369 business email compromise or account email Compromise complaints, almost 20,000 in one year, adjusted losses, 1.8 billion billion. The point is, it's not enough to, you can't build a perimeter defense against email attacks. You gotta let email in, right? You can't secure it at the gateway. So, I mean, you, of course, I'm not saying don't have gateway security, we do, but you, that's to protect against viruses and ransomware and, you know, spam and all that stuff. But your gateway's useless against spearfishing because it's targeted. It has the name of your employee in it, has the name of the boss in it, that kind of thing.
(00:08:09):
You gotta have protection at the inbox level. And this protection has to be, as one might imagine, pretty sophisticated because the, the attacks are changing by the minute. So you need AI and machine learning that's constantly updated to detect and stop the most sophisticated, and they're therefore the most dangerous threats. Here's where you start, cuz I know I don't wanna overwhelm you with how bad it is. It's bad, but you can start in an easy way. Get the Barracuda Report 13 email threats you need to know about right now. You'll see how cyber criminals are getting more and more sophisticated all the time. How you can build the best protection for your business, your data, and your people with Barracuda. Find out about the 13 email threats that you need to know about how Barracuda can provide complete email protection for your teams, your customers, and your reputation.
(00:08:57):
The ebook is free. It's waiting for you. Just go to barracuda.com/security. Now. You, you could find out once just by going to that site. It's a really good company with some great stuff. Barracuda.Com/Security. Now, B A r R A C U D A, Barracuda your journey secured. Thank you Barracuda for supporting us for doing the great work you do. We use them, recommend them. You should probably do us a favor as a listener, go to that address, that way they know you saw it here. Barracuda.Com/Security. Now, thank you for doing that Picture of the week time, Mr. G.
Steve Gibson (00:09:35):
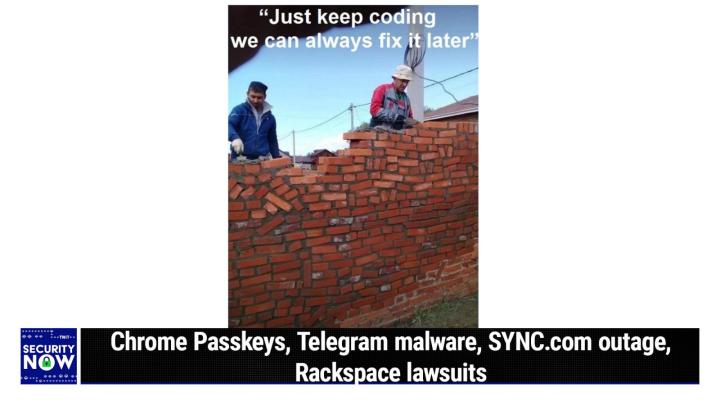
So rarely does a picture, I think really work as an analogy as well as this thing does. As a coder and you're a coder we know the danger of, of as you're writing code, just like not making sure that what you're writing is correct. You, there, there is this sense of building a foundation and you know, you, you sort of, you, you, you create part of it and then you add to it and you, you, it grows. Well, you know, you want the beginning of that process and all the various stages between the beginning and the end to be correct. Anyway, the, so the caption on this picture is just keep coding. We can always fix it later. And <laugh>, this is, this is so perfect <laugh>, because so what, what, what you and I are laughing at is a, there's two brick layers. I guess they started, this is not, they started, okay, well, except look, looked at that vertical one.
(00:10:43):
I love that vertical one. It's like, so you have to, you have to ask what is the story here? I mean, this is, they kind of know that bricks are supposed to be horizontal kind of, and kind of, but first of all, they seem to have a problem with their brick sizing. They're, you know, these are not all the same size as bricks. And so, and there's like some wedgies in there and there's, I mean, it's just, it's a disaster. But, but the, the beauty of the picture is like way down to the bottom is a brick that's, you know, it's never going to get fixed because it was four days ago in the process of building this wall that this brick, someone stuck it in vertical because, well, they had a gap to fill or something, Eric. And they just, Eric
Leo Laporte (00:11:26):
In our chat room says, that's a go-to statement. <Laugh> <laugh>,
Steve Gibson (00:11:32):
Once
Leo Laporte (00:11:33):
You see it, you can never unseen it.
Steve Gibson (00:11:35):
<Laugh>. That's hysterical. Yeah. So anyway, I just, it's a great analogy because, you know, you know, these guys just said, oh, well, you know, what the heck just keep going and there, this is never gonna get fixed. That brick down there. It's will be vertical, vertical as long as that wall is standing, just like some bug that got written in the beginning and you know, they just said, ah, just, you know, we'll fix it later. No bad idea. Okay. a good idea was covered by ours, Technica Friday headline, which read past key support rolls out to Chrome's Stable. They said with a huge <laugh>, this is ours, Technica with a huge list of caveats. Initial Google Passkey support is here. They wrote Google's latest blog says quote, with the latest version of Chrome, that's 1 0 8. I have it. I probably everybody does version of Chrome.
(00:12:36):
We are enabling past keys on Windows 11, Mac Os and Android. And they, and, and ours wrote the Google password manager on Android is ready to sync all your past keys to the cloud. And if you can meet all the hardware requirements and find a supporting service, you can now sign in to something with a PAs key. So they then in their coverage, take some time explaining stuff that we all know about PAs keys that we've talked about, you know, and they get most of it right in kind of a watery down sort of way. Then they talk about compatibility <laugh> by writing. Today. Pass keys essentially require a portable device. Even if you're logging into a stationary pc, the expectation is that you'll use a smartphone for this, but you can also use a MacBook or iPad the first time you set up an account on a new device.
(00:13:34):
You'll need to verify that your authenticating device, your phone is in close proximity to whatever you're signing into this proximity check happens over Bluetooth. All the passkey people are really aggressive about pointing out that sensitive data is not transferred over Bluetooth. It's just used for a proximity check. But you'll still need to deal with Bluetooth connectivity issues to get started. They say when you're signing into an existing account on a new device, you'll also need to pick which device you want to authenticate with. Probably also your phone. If both of these devices are in the same big tech ecosystem, you'll hopefully see a nice device menu, but if not, you'll have to use a QR code. Second big issue, they said, did everybody catch that os listing at the top? Google supports Windows 11 with past keys, not Windows 10. What, which they write is going to make this a tough sell.
(00:14:40):
Stat counter has Windows 11 at 16% of the total Windows install base with Windows 10 at 70%. So if you happen to make a Paske account, you, you could only log in on newer Windows computers. Okay? So they continue, paske get stored in each platform's built-in key store. So that's key chain on iOS and Mac Os and Google password manager or third party app on Android and Windows. Hello, on Windows 11. Some of these platforms have key syncing across devices and some do not. So signing in on one Apple device should sync your pass keys across to other Apple devices via iCloud. And the same goes for Android via a Google account, but not Windows or Linux or Chrome OS syncing they write, by the way, is your escape hatch. If you lose your phone, everything is still backed up to your Google or Apple account.
(00:15:44):
Google's documentation mostly doesn't mention Chrome OS at all, but Google says we're working on enabling PAs keys on Chrome for iOS and Chrome os There's also no support for Android apps yet, but Google is also working on it, which makes me wonder like, okay, these, these, a lot of these limitations seem significant and weird. Anyway, they wrap up this news of crow's of Chrome's emerging support by writing. Now that this is actually up and running on Chrome 1 0 8 and a supported os, you should be able to see the passkey screen under the autofill section of a Chrome of, of Chrome settings, so you know, of, of a Chrome browser settings. So you can go to Chrome colon slash slash settings slash pass keys, put that into the address bar, and they said, next, <laugh> we'll need websites and services to actually support using a passkey instead of a password to sign in Google account would be a good first step.
(00:16:54):
Google, they, they said Google account support would be a good first step. Right now you can use a pasky for two-factor authentication with Google, but you can't replace your password. And they, and they finished everyone's go-to example of paske is the PAs keys.io demo site, which we have a walkthrough hub of, and then they, they do that. So, you know, I've got Chrome 1 0 8, so I put Chrome colon slash slash setting slash pa keys into Chrome's address bar, and I was greeted with a little, you know, thing that said, okay, this was on Windows 10, and it just said to manage pass keys, use a newer version of Windows. Oh God. And it's like, wow, really? I mean, that's what you're gonna get on Windows 10. So, so it's, it presumably it's the, the windows. Hello. Which I mean, it's very cool that, that the browser is not storing your PAs keys, that the browser manages this process, but w but it's in the substrate.
(00:18:04):
It's, it's in Windows itself where the PAs keys are stored. That seems like a way, a much better idea than having them in the browser. But wow, <laugh>, you're not letting people with Windows 10 have it. Good luck with that. So, you know, 70% of the world won't be able to use it. You know, these feel like arbitrary limitations, you know, lack of syncing among competing platforms and devices feels like the attempt to, to create walled gardens. It feels to me as though passkey the way this is going pass keys, like passwords may also become the domain of our existing password managers. We know that any password manager that has a pulse has got to be racing as fast as possible to getting support of PAKEs up and going. And of course, they will provide cross client synchronization and, you know, none of this, sorry, you, you can't use it on Windows 10 nonsense.
(00:19:15):
So, you know, we can hope that that's coming. We still have the chicken and egg problem, of course, of getting it to actually work and then having places where you can use it to sign in. But you know, you and I Leo, are old enough to remember when people thought that the web would never happen <laugh>, because it was like, well, you know, there's, why is anyone gonna put a webpage up when there's only five people who are using the internet? I've got Gopher. I don't need a web. Yeah, I Exactly. <Laugh>, exactly. Okay. So while we're talking about synchronization I thought I should mention that my favorite cloud synchronization platform sync.com had something happen to it. The problem first surfaced last Wednesday, apparently after a scheduled maintenance somehow went wrong and things didn't appear to be fully restored until just yesterday. I utterly depend upon sync.com and the outage had me revisiting the wisdom of that dependency.
(00:20:14):
You know, I'm not a typical user since I also run a pair of NAS boxes, you know, network attached storage boxes at each of my two locations. And as we know, there are many other syncing alternatives. Reading between the lines of syncs frequent online status updates, you know, through these slowly passing days, you, you sort of got the sense that this was causing a major problem for their customers. You know, there was a lot of, like, we really understand how much you need this back and believe us, we're working on this as hard as we can, yet they never really told us what was going on. Anyway I came away, first of all, I thought it was my problem. I didn't immediately, I didn't even know that there was like a status log page until I dug in. So one of the things that I discovered, I I know that a, a lot of our listeners are now sync.com users as as probably as a consequence of me having said, you know, yeah, it's, it's been years and I love it.
(00:21:12):
I'm still using it. Anyway, what I discovered was that the client, the, the desktop clients do not update themselves, or if they do mine weren't, like they got stuck or something. Anyway, the world, they're, the sync.com world has gone to 2.1 0.7. What am I saying? 2.1 0.4. Sorry, don't go crazy. 2.1 0.4. I had to manually get that and run the, that, that, you know, the latest version in order to bring my client's current. They were, you know, I've had sync for years and, and like, they were really old. So everything seems to be like working really well now that I actually have clients that were written in this century. The good news is when you run it, it just, it seamlessly installs itself and like removes the old one, puts in the new one, gets us all set up and, and going. So I just wanted to say yep, if you, if you were affected by the sync.com update, I feel for you, I was too. They, you know, if they were saying, oh, some of our users are experiencing problem really, okay, I would love to hear, for example, if there are sync.com listeners of this podcast who had no problems at all for the last week, that would be interesting to me because maybe it was just some people, I dunno. Okay.
Leo Laporte (00:22:36):
I by the way, you use, you mentioned Sync thing. Yes. And of late, since Sync Thing is open source and completely local, I feel like I don't know if I need a cloud because I have everything on every computer. And then I was thinking, well, one advantages of the cloud is it's always on. So you use an s as I do a Sonology Nest, you could put Sync thing on your Sonology Nest. So I'm basically treating my Sonology Nest as the canonical copy of all that stuff. Yep. And it's pretty fast. I, I use sync thing, update source code. I know that's one of the things you do is so that you can work at Laurie's in, at the office. So it's pretty fast. I will, I will finish a project close or, you know, close a window, go over my other computer and it's almost always there by then.
Steve Gibson (00:23:19):
So I'm glad you mentioned it because I should have I have sync thing on both of my NASAs Bo both the Drobo Yeah. And the, and the Sonology Sonology. I use SyncThink to synchronize some directories between them. And Sync Thing is what we use with Lori's fleet of laptops, which she has out to her clients to keep them all synchronized, synchronized,
Leo Laporte (00:23:42):
Smart. So they all have the same stuff on 'em. That's smart.
Steve Gibson (00:23:44):
Yeah. Yeah, yeah. It's it, it is absolutely a win. It's free,
Leo Laporte (00:23:48):
It's open source. It works. It has it does not traversal. You know, I just, I just, I love it. It's really, really good. In fact, it's really made me rethink how I back stuff up since I have a copy of everything everywhere. Yep. You know, without being in the cloud at all.
Steve Gibson (00:24:03):
Yep. Okay. So I titled this piece MetaBank Reboot, because that might literally be what happened this past weekend. We've been, you know, recently following the drama with Australia's latest private medical insurer, MetaBank that's the one that exposed a huge number of a huge, well, a huge number of its current and past customer data. 9.7 million clients got exfiltrated on the dark web then it got released in, in, into the public when they refused to pay. Well on Friday, the Sydney Australian, you know, morning Herald had an interesting bit of news <laugh>. Their coverage began. Private insurer, MetaBank app stores, contact center, and IT systems will all go dark this weekend. As it overhauls its cybersecurity following the nation's worst data breach in corporate history. They said from 8:30 AM Australian Eastern daylight time on Friday oh, I'm sorry, PM 8:30 PM end of the day in Australia on Friday pm E Eastern Australia they said Australia's largest health insurer will shut down.
(00:25:30):
Its IT systems followed by retail store and customer contact center closures on Saturday. To quote further strengthen systems and enhance security protections was the official line from Medibank. They said the company expects normal activity to resume by Sunday at the latest. They also said Microsoft IT security experts from the Asia Pacific region will travel to MetaBank Melbourne headquarters to assist with the operation. And then I kind of equipped to myself, I guess Microsoft is gonna show them where the update button is located on their server. And they said this was said to have been planned over several weeks and will be Meta Bank's first shutdown of such scale. Well, yeah, you could imagine this is a, like for a massive private insurer to shut down everything. So in other words, you know, shut down, update software and firmware and everything else, then turn everything back on again.
(00:26:36):
So the, the Herald finished by saying the overhaul is part of a series of maintenance strategies termed operations safeguard. So Right. They gave this a big banner as part of this established after the personal information they said of up to 11, I'm sorry, 10 of up to 10 million current and former MetaBank customers was breached in a cyber attack. The data was released on the dark web when MetaBank refused to pay a 15 million. We never had numbers before. A 15 million ransom demand by the hackers who police have said were based in Russia. The company said the damaging cyber attack will cost the firm at least 35 million in initial recovery costs, though that is likely to grow as law firms and regulators circle a MetaBank spokesperson said, although there had been no further suspicious activity detected inside its system since October, the insurer was carrying out further maintenance to strengthen its online security now.
(00:27:48):
Okay. If we could read between those lines, what might be happening is a complete wide scale coordinated reinstallation of system software. I mean, not just an update, as we've noted before, and Leo, you and I have talked about the, the, the problem after something has been compromised is in a complex system, you can never really be certain that something isn't still hiding somewhere. So, you know, imagine you're in their shoes and the, the, there was, we don't know right what the forensics examination actually found. It might have left them horrified or terrified, you know, and feeling that they had no choice other than to just wash everything clean and reinstall. And boy, you know, if so what a nightmare. Oh. And, and they did say <laugh> since the, since the hack MetaBank has bolstered monitoring, added detection and forensics capability across its system and scaled up analytical support via specialist third parties.
(00:29:04):
Right? So they've brought, you know, a bunch of people in and they said it also recently introduced two-factor authentication. Ah, imagine that where, where accesses granted only after providing a code sent to one's email or s m s Oh, okay. So not very good two-factor authentication, but you know, better than none anyway. So being completely down and offline for as many as two days sure does sound like a major sweep cleaning of all mission critical systems. And, you know, they probably had no choice. It was PT Barham who is credited with saying there's a sucker born every minute. I was reminded of that when I came across this bit of news about a cybercrime group that's been named Crypto Labs, the cybercrime research group known as group ib, who we talk about from time to the time, identified a new cybercrime operation, which they named Cryptos Labs.
(00:30:13):
Okay, get this since 2018, so four years. This Cryptos Labs group has operated a network of more than 300 scam websites posing as FinTech, you know, financial technology and cryptocurrency trading platforms. Group IB says the group used search engine ads and social media posts to trick French speaking users across Europe into investing more than 480 million euros. Okay? So nearly half a billion euros in these scam websites by leading them to believe that they would get to trade in stocks and crypto assets. But researchers say that once users put money into their accounts, they're, you know, bogus accounts, the crooks either asked for more, you know, get as much as you can, right? Or ignored their customers before shutting down platforms and moving to a new domain group. IB said it named this group, cryptos Labs after the kit, they used to automate the deployment of fake trading portals, right?
(00:31:33):
Since we're gonna be doing this a lot, <laugh>, let's create a kit that makes it real quick to set up a new fake trading portal, because, you know, we're not gonna be there long. We're gonna have to do it again soon, okay? It typically, the, these, these portals typically mimicked 40 different popular banking, FinTech and crypto brands. So, you know, these guys were pretending to be Coinbase and set up one fake cloned Coinbase site after another people, you know, had heard of Coinbase, their friends were talking about it then they encountered an advertisement in a search engine or in social media, and they thought, Hey, I just got paid. Now's the time. They didn't really know what Coin Base's domain name was. So they just clicked on the advertisement and went to, you know, coin bases.org. And since everything looked quite official, they never thought that it might be an illegitimate ad and site people would transfer money in.
(00:32:41):
And at some point, once enough had or someone wanted their money back, the fake domain would be shut down and another would be set up in its place using this cryptos lab tool that just, you know, <laugh> just spits out these fake platforms. So this is not the internet that term that, that, that Tim Burners Lee envisioned back in 1989 when he originated the concept of an internet full of interlinked H T M L documents that anyone could create and publish on their own. It's not as if crime hadn't existed before. It's just flowed into this new medium. So that's gonna happen. Two interesting pieces of news about Telegram. First, malware on Telegram, the Russian security firm, positive Technologies published a report on telegrams budding cybercrime ecosystem. According to the company's scans, telegram has slowly replaced hacking forums and is currently being used for advertising a wide spectrum of hacking services and malware.
(00:33:57):
The sale of remote Access Trojans corporate network account credentials and cash out services are among some of the most popular topics on <laugh> Telegram now, okay, so there's one tidbit, but get a load of this one Telegram, which now we know is generally becoming the favorite hangout of the crime. Underworld has decided to further expand their subscriber base by allowing users to sign up without needing one of those pesky sim cards to anchor their identities. Telegram wrote today starts a new era of privacy. You can have a Telegram account without a sim card and log in using blockchain powered anonymous numbers available on the Fragment platform. Okay, so what I thought, what's fragment? So I followed a link, https slash slash fragment.com, and I was told, oops, this service is not available in the United States. Hmm, okay, that's interesting, <laugh>, I wonder why not. Mm-Hmm. So I thought that Wikipedia might know about fragment, and perhaps it does, but the word fragment is so common that I wasn't able to find it there.
(00:35:29):
Among all of the other fragments, Googling turned up an abbreviated reference that was more tease than anything else. Google said, buy and sell usernames. Hmm, sec, secure your name with blockchain mm-hmm. In an ecosystem of 700 plus million users, and assign it as a link for your personal account, dot, dot dot. And that's where the little summary cut off on Google search. I thought, buy and sell usernames. Mm-Hmm. <affirmative>, what? Now? I know that Kevin Rose might be willing to sell you an icon of a zombie, but what's, what's fragment? So I dug in some more and I found some news about fragment over@crypto.news where their coverage had the headline. Telegram now allows users to buy and sell usernames via auction. And then it goes on to explain Telegram releases. New feature transforms usernames into digital assets, and it says, popular cloud-based instant messaging app. Telegram has just launched a new feature to allow users to buy and sell short, recognizable, you know, outside usernames for personal accounts, public groups and channels.
(00:37:04):
Telegram has commenced an auction for the best usernames on fragment, a free collectible trading platform with this new feature, telegram usernames have become digital assets that can be secured and sold between parties according to the innovative platform's. Unveiling note, ownership of the collectible usernames is secured in the immutable ledger of to <laugh>, t o n to, and it's, and it goes on a fast and scalable blockchain network, which no one's ever heard of before. Interestingly, the new feature allows owners to add multiple username aliases to their personal accounts group or channel. Also, each collectible name can be accessed with its at username on Telegram or outside Telegram, using links such as username dot tme and tme slash username to acquire usernames on Telegram Buyers visits, fragment search for their desired U, but not un unless you're in the US I guess for whatever reason, you can't have a fragment in the us.
(00:38:28):
But here, you know, a VPN might be your friend search for their desired username and click on auction if that username is still available. So, okay, telegram is like tied in with fragment somehow. And now you, you have to buy your user, your Telegram username on the blockchain. So then it says, buyers will then be redirected to a page, which shows the highest bid along with the bid set up and minimum bid. Okay, so earlier this said that Ton was an immutable ledger, apparently it's also a currency. I went over to coin market cap.com/currencies/toco and I learned that a ton has a current value of $2 and 10 cents us. And it was fluctuating as I was there at that page could make up its mind between two 10 and two $11. It's also, it's got a 24 hour trading volume of $44 million. 44 million.
(00:39:46):
Whoa. Yeah. $628,950. That was yesterday, 24 hour cycle. And I saw that there was a ton.org. So I went over there and I discovered that to stands for the Open Network, t o n. And from the Tan homepage, we learned that quote ton is a decentralized layer one blockchain designed by Telegram to on Uhhuh. Interesting. So the, the loop closes designed by Telegram to onboard billions of users. They hope it boasts ultra fast transactions, tiny fees, easy to use apps, and is environmentally friendly. Okay, so let's get this straight. Telegram noticed that they had a lot of users and a popular platform. So they decided that they wanted to monetize the ownership of Telegram usernames. They wanted to create a marketplace which would allow Telegram usernames to be bought and sold. So they created Ton their own cryptocurrency, anchored it with their own blockchain. They then established an auctioning system, which uses the ton as its exchange currency to allow their users to bid for purchase and sell Telegram usernames.
(00:41:25):
The rest of the coverage of this, the first part of which I already shared, tells us how this is going. Under the heading, massive instant adoption of new feature, millions of tans earned in username sales. We have less than si. This is the, this is the, the reporting of this less than six hours after the launch. Thousands of usernames featuring international brands and celebrity accounts have been put up for sale. Still on auction are at Nike, at King, at eSport, while others such as at auto, at Aviva, at fifa, et cetera, had been sold for as much as 900,000 ton. Oh, now we don't know what the ton was worth when it sold, but the ton is now $2 and 10 cents. So that's what, 1.8 million thereabouts. Judging by data on the fragment platform, millions of tos, you might say a ton of tos have been earned by Telegram users from the sales of their short usernames.
(00:42:46):
So user users who were on Telegram early, got in, got a short name, those are desirable. They're now able to cash in on their short username by selling them for tans and then liquidating tans for cash. There's still more to be made as there are still lots of usernames currently on auction. The, the report says, an example is the popular shoe brand, Nike, which has over 300,000 ton bid for it at the moment. Telegram is affording its users full ownership of their usernames, and they are embracing the idea. So think about that. There's no trademark protection, I guess. So anybody could buy Nike on Telegram who is willing to pay enough. And that's gotta make Nike a little nervous, right? Because Telegram, you know, it is a, a happening place right now.
Leo Laporte (00:43:50):
So the, actually it's more complicated cuz I don't think they actually own ton telegram. I love Telegram by the way. And, and you know, you can, you can look at what you just described in, in as you did kind of a
Steve Gibson (00:44:04):
Scans, a
Leo Laporte (00:44:05):
Scan scans. But also if you're trying to solve this issue of, and this is an issue, it's an issue with Signal having to tie your account to an actual phone number. Yeah. You'd need to do some sort of, I think blockchain is actually, this might be one good application blockchain, some sort of decentralized authentication system. My shirt name is Leo LaPorte. So, you know, I own that, but I didn't buy it with to, I just always have had it, right. So I re I when you started talking about this, I said, well wait a minute, doesn't Telegram have its own crypto? And they did. They started something called the Graham, which the, in 2018, which the s e
Steve Gibson (00:44:41):
C, that's kind of a good name.
Leo Laporte (00:44:42):
Graham was a great name. Graham, s e c halted it because they were doing an ico, remember when that was the big thing, the initial coin offerings and they hadn't registered the ico. O c SCC halted it. So telegram abandoned to which stands for the open network and it's open source. So, so developers have kept it going according to the Verge. Pav Valora of the owner of Telegrams said he supported the project a year ago saying, I'm proud of the technology we created is alive and evolving. So it is cool a third party effort. And I, I agree. Anytime I hear crypto, I go, okay, what's, and especially if you're selling usernames, you know what's, you know, this is a, you know, but if you think about it, if you wanted to replace phone numbers, you need some sort of unique fingerprint, right? Yeah. you could do what Thema does and, you know, meet in person and do it. But there's some sort of Thema generates a a a a a, basically a private and public key chain, correct. Key print, correct. Correct. But how do you get your key out there is the problem. So this is an interesting solution. I wish Signal would do something that didn't require a phone number because I think that's a Yeah. You know, that's a
Steve Gibson (00:46:00):
Problem. And, and it, it definitely is a privacy concern, right? Yeah. Because you've got to have something that is, you know anchored to assist Plus,
Leo Laporte (00:46:06):
Plus Signal might, any Signal app I run is attached to a one phone. I can't put it on another phone without,
Steve Gibson (00:46:11):
Right. You're, you're only able to have a light. You, you're able to sync a desktop but not another phone. Exactly.
Leo Laporte (00:46:17):
Right. And, and with Telegram, I can, I have Telegram everywhere, so, you know, different strokes. I agree. There's, you know, potential for misuse, obviously with water
Steve Gibson (00:46:28):
Time for me,
Leo Laporte (00:46:30):
<Laugh>, oh, have some water. Okay. I'm having coffee in my sand mug. So you have some Oh, oh, very nice. Isn't that cute? Now you have some water while I talk about our fine sponsor for this segment. It's actually a good timing cuz you know who it is. Bed warden love the BitWarden. I've been talking about them a lot lately. Somebody called me on the radio show on Sunday and said I'm all, I'm, I'm your age Leo <laugh> and I'm trying to figure out how to protect everything I have and yet still make it available if I should pass away suddenly to my, to my heir as an executor. And I said, bin Warden. And he said, well how did explain that? I said, well, bid Warden has an emergency contact emergency access contact that you can set up. You're put, first of all, put everything in bid warden.
(00:47:21):
That's just, it's just sensible. It uses that strong public key crypto. Steve is always talking about and I use it for my, I have passport images in there, driver's license social cuz it's a hundred percent secure trust. No one only you have the key a crypto vault and it's not just for passwords, although it's the best password miniature out there cuz it's open source. So you know exact everything by the way is open source. Even the, the plugins for the browsers, everything is open source. So I really, I really like that about them. They have rolled out pass keys Passwordless login for the web vault, which is really cool. You can authenticate to the Bit Warden Web Vault using your Bit Warden app, single sign on instead of your master password. That should reassure. People are worried about remembering their master password and it is as secure, right?
(00:48:13):
You have organization Vault and login flow updates. Lemme give you a couple of these. Let me, I should just say right up front. Bit Warden is the only open source completely Cross-platform works everywhere. Password Manager you can use at home, at work, you can use on the Go. And it's trusted by millions. The basic personal Bit Warden is free forever. I asked him, I said, well we had another password manager they started charging. He said, no, no, it's open source. W we can't charge, it's free forever. We've never designed the the business side of this based on ever charging you for the personal vault. Now I pay for some premium features, 10 bucks a year cuz I wanna support 'em. But they do have organizational features. They have Enterprise and Teams and Family Vaults. Some organization functions now have been moved to improve the web, web vault ui to accommodate new login options.
(00:49:08):
The login process has been separated to two screens. So you'll have skim updates. S C I M triggered events will now log in from Skim instead of unknown. This, you know what, it's so great that they put this in the ad. They know they're talking to the Steve Gibson crowd, so they know that. I mean, I wouldn't put this in an ad anywhere else, but for you, you need to know skim triggered events will now log in from Skim instead of unknown. That's good. And the Skim a API key will now be obfuscated by default. Just little features like this I think this must be from their updates page generate usernames and passwords from iOS app extension. Oh, I love this. I was just talking to the Fast Mail people and I said, I love it that I can use Bit Warden to create usernames with a fast mail account.
(00:49:58):
And they said, yeah, we love it too. <Laugh>. so you can get an iOS app extension, it's in the share menu while using apps like browsers. That's cool cuz that's a problem on mobile. You don't have the browser extensions capability, but it's in the Share app. So you can on-the-fly generate usernames and passwords from the iOS app extension. They've got a nice new theme which you will love. The Solarized dark theme has been brought to mobile. They've optimized performance BitWarden's, improved web vault load times and experience for the accounts with access to thousands of vault items. I don't use the web vault that much. I use the apps. I have an app on Mac, I have an app on Linux, an app on Windows. I have browser extensions. But if you use the web vault, which is actually a good thing cuz that can, you can use that anywhere. You'll notice it's loading a lot faster. Bit Warden has also added query parameters in group filters for Google Workspace.
(00:50:56):
Okay, <laugh> if you need it, you know, I guess what that means, BitWarden is also a must for your business. If you are not yet using a password manager in business, you know, your employees are writing passwords down and putting them in a little crumpled note in their drawer under their, you know, their desk blotter. Maybe you've gotta post it on the side of the screen. This is not password safe, this is not security. Get a, a great password manager, they won't mind using. It's fully customizable. You can adapt it to your business needs and it's very affordable. The team's organization option is $3 a month per user. And by the way, they use their personal vault. It starts with you set up their personal vault and then they join the organization. So the users, they're gonna get security in their whole life.
(00:51:42):
Now all of a sudden that's just really great. Enterprise organization plan is $5 a month per user. They let you share data privately between coworkers, across departments, the entire company. It's a much better way to share passwords than writing it down and handing it or sending it via email or a text. So you start with your basic free account, free forever, unlimited number of passwords, upgrade anytime to the premium account. Like I said, less than a buck a month. There's a family plan, six users premium features, 3 33 a month for once the whole family gets that. I am, look you, you by now, if you listen to this show, you know, you should be using password managers. I'm just saying you should use the only open source cross-platform password manager that can be used at home on the go at work and is trusted by millions of individuals, teams, and organizations worldwide.
(00:52:35):
It's BitWarden. You can get a free trial of teams or enterprise right now, or of course start for free across all devices forever as an individual User. Bit warden.com/twi. This is the one. Just, that's all I can say. It's works, it's beautiful. The extensions work beautifully. I just use it for everything now. Bit warden.com/twit. We thank him so much for supporting security. Now I know Steve doesn't use Bit Warden, we'll get him someday. Yep. But I think he would agree better to use password manager than not. Absolutely no question. Yep.
Steve Gibson (00:53:15):
So I just, I wanted to mention cuz this is in the news in the, in the technology that the TikTok banning has continued Texas has now joined the ranks, and I was gonna say that Texas was the latest, but that was yesterday <laugh>. So who knows what's happened since then. Texas governor Greg Abbott has banned the use of TikTok on the devices of state employees. And in doing so, becomes the fourth, happens to be Republican led state to ban TikTok on employee devices that follows Maryland, South Carolina and South Dakota. Remember that last week it was South Dakota that I noted was first with their governor Christie Nom saying that she hoped other states would be following suit. I guess her wish is coming true. Greg Abbott also ordered state agencies. I I this was interesting to come up with plans to govern the use of TikTok on state employees, personal devices not owned by the state.
(00:54:18):
Yeah, good luck. Can't do that. So that's just yikes. That's just performative. He can't do that. Yeah. he wrote in a letter to state agency leaders that there are growing threats posed by TikTok to the state's sensitive information. Quote, TikTok harvests vast amounts of data from its users' devices, including when, where, and how they conduct internet activity and offers this trove of personally sensitive information to the Chinese government. Okay, but wait, there's more. Indiana's Attorney General brought a pair of lawsuits against TikTok accusing the company of deceiving users by claiming that their data was protected from the Chinese government. And for exposing Indiana children to adult content, the lawsuits claim that the Chinese based social media giant has deceived and harmed Indiana residents. Indiana's first lawsuit alleges TikTok has marketed its video sharing platform as safe for teens, even though it's algorithm serves up abundant content unquote depicting drugs, sexual content, and other inappropriate themes.
(00:55:33):
The second lawsuit asserts that TikTok has deceived consumers by suggesting their personal information is protected from the Chinese government and the Communist Party. Okay, so the Attorney General said in a statement, the TikTok app is a malicious and menacing threat unleashed on unsuspecting Indiana consumers by a Chinese company that knows full well the harms it inflicts on users. With this pair of lawsuits, we hope to force TikTok to stop its false deceptive and misleading practices, which violate Indiana law. So the Attorney General is asking for emergency injunctive relief against the company and is seeking monetary penalties for every time TikTok violated Indiana's deceptive consumer sales act. Wow. for what, how you violated Sales act if it's free. Yeah. I w I was wondering if maybe there was something I had missed. So I have it in the show notes. I'm not gonna drag our listeners through it, but Caspers Ski has a very, a very useful factual piece by piece walkthrough.
(00:56:57):
And the upshot is there is no smoking gun here. There is, there's nothing that TikTok is doing that any of the other social media platforms, you know, most notably Facebook being the largest and here in the us is it also doing to, to get, I, I thought okay, what's on the other side of this? You know, how about a balanced look? So I found some coverage that N P R offered from less than a month ago about the FBI's raising of concerns, which apparently is what started all of this over what TikTok might be capable of doing. And what's interesting is the quotes from FBI director Christopher Ray during a Homeland Security Committee meeting. So NPR r story says the F B I alleges TikTok poses national security concerns. Right? Okay. So, okay, it's a concern. The, so NPR R says, the head of the FBI says the bureau has national security concerns and that they even quoted that about the US operations of TikTok warning that the Chinese government could potentially use the popular video sharing app to influence American users or control their devices.
(00:58:30):
Gee, like what? Facebook, like Twitter, like everything, right? Anyway, sorry. F B I director Christopher Ray told a House Homeland Security Committee hearing about worldwide threats on Tuesday. This was the middle of last year. It was like the 17th I think of November. That the F B I has quote a number of concerns just days after Republican lawmakers introduced a bill that would ban the app nationwide. How do you do that? Okay. Anyway, Ray said, I mean this is sounding like right, some other country we talk about somewhere else. Ray said quote, they include the, the concerns that is include the possibility, possibility that the Chinese government could use it to control data collection on millions of users or control the recommendation algorithm, which could be used for influence operations if they so chose or to control software on millions of devices, which gives it an opportunity to potentially technically compromise personal devices.
(00:59:51):
And then NPR reminds us TikTok, which hit 1 billion monthly active users in September, 2021, is owned by the Chinese company. Bite dance. Chinese national security laws can compel foreign and domestic firms operating within the country to share their data with the government upon request. And there are concerns about China's ruling communist party using this broad authority to gather sensitive intellectual property, proprietary commercial secrets and personal data, blah, blah, blah. So you know concerns and based on concerns and China and communism, what we see to my reading is a bunch of grandstanding by governors and attorneys general who wanna make a dig a big deal about this because it's owned by a Chinese company. We've seen misbehavior on the part of our domestic firms who are looking at things that they shouldn't. There there was some Buzzfeed News had some audio cuz I spent some time digging into this wondering what the heck there was some audio, the buzz fees news found of some TikTok employees clearly looking at the data of some TikTok users, much like Facebook has been caught looking at their own users. And, and Twitter has been, has been, was caught doing the same. So anyway, to me this looks like a bunch of nonsense. We'll see where it goes. I it is, I would be surprised if we end up with legislation banning TikTok.
Leo Laporte (01:01:39):
Did cuz persky go into what information TikTok knows about you? I mean, cuz that's I guess the fundamental question. There's, there's two, there's two parts to this. A a is TikTok giving informa, let's assume the Chinese government has a pipeline into by dance. I mean, that's a big assumption, but let's assume they do. Is TikTok gathering. What kind of information is it gathering from my phone that it's sending to the Chinese government? That's problem number one of then. Problem number two is people say, well, you know, they could use the algorithm to propagandize us, you know, to convince us of something which is legit. Although the Chinese government is not unhappy to use Twitter and Facebook and <laugh> YouTube, they don't need, they don't really have to have some other way to do it. But what did Kaspersky say about it's, it's, is it any differences from any other app on the, on the, on the phone?
Steve Gibson (01:02:27):
No. Kaspersky directly addresses the question of privacy concerns. They wrote, one of the most vi viral aspects of TikTok has been privacy concerns with questions like, what data does TikTok collect? And does TikTok steal your information regularly circulating online? They wrote, like many other social networking platforms such as Facebook, TikTok collects a lot of information about its users. This includes every TikTok video watched and for how long the entire contents of every message sent through the app, since messages are not encrypted, the user's country location, internet address and type of device being used. And with the user's permission, TikTok also captures its users' exact location rather than just their, you know, their IP address, the their phones contacts and other social network connections. But
Leo Laporte (01:03:29):
You have to give them that because
Steve Gibson (01:03:31):
I, to build a graph, it's
Leo Laporte (01:03:32):
Always asking for my contacts and I always say no. And I, okay. I think I, as I'm assuming that Apple blocks it, if I don't say yes, I mean they, that they're not sneakily underhanded. Oh,
Steve Gibson (01:03:42):
I bet Apple
Leo Laporte (01:03:43):
Would.
Steve Gibson (01:03:43):
Yeah. And, and finally their age phone number and payment information. Again, if, if you say like, yes, you,
Leo Laporte (01:03:50):
You allow it, you provide, unless you say you're 98 and you live in Muni, Indiana, which you could. Yeah. Yeah.
Steve Gibson (01:03:56):
So Casper says, this information can be used to assemble a detailed profile for advertisement targeting by understanding who its users are, who their friends and family are, what they like, and find entertaining and what they have to say up to their friends to use the app. Users grant access to their microphone and camera. If they create videos, the app captures closeups of their face. And
Leo Laporte (01:04:22):
By the way, potentially, again, you have to do that only if you're gonna use it to create videos. I don't, I use it and most people don't. They use it to look at videos to watch. Yes. And every time it says you want the camera access, I say, no, you can't. No, I don't want you to have that. So that again, that's the turn on, right?
Steve Gibson (01:04:38):
So they said potentially this provides biometric data, which could be used in conjunction with other images which exist online. Tiktok also uses technical measures to encode its activity. This means that some of what it does is hidden from external researchers, which all the apps do. Tiktok says this is to disrupt hackers and other malicious actors. There's been extensive media coverage of TikTok privacy concerns. However,
Leo Laporte (01:05:07):
Yeah, I think how mad we'd be if TikTok was sending all that information in the clear <laugh>, you know that's not good either <laugh>
Steve Gibson (01:05:15):
The way, the way all of our, our webpages used to be once, right? Yeah. And Casper, Casper Casper Ski said however, most social media platforms worldwide collect, use, analyze, and ultimately profit from users personal data. Tiktok argues that it collects less data than platforms such as Facebook or Google, since it does not track user activity across devices. So again to me This is all just, you know, the FBI say, well, we have concerns cuz maybe, you know, quote, an opportunity to potentially technically compromise personal devices, right? Because you loaded an app. All apps have that opportunity to potentially technically pot talk compromise personal devices. Anyway, to me this is protectionism, right? It's xenophobia and protectionism and an opportunity for so far it's all been Republican political people. It's performance to say, it's performance to say, yeah, the, the coms are going to get our kids.
(01:06:27):
Yeah. Okay. And while we're on the subject of nonsense filed two days after last passes, November 30th disclosure Password Management Company Last pass has been hit with a class action lawsuit after experiencing two data breaches in the past three months, which we've talked about. In fact, it was a, it was a title of our podcast a couple weeks ago. The plaintiff, in this case, debt Cleanse Group, legal Services L L c, filed a class action complaint against LastPass US L P on December 2nd in a Massachusetts federal court alleging Lynn negligence and breach of contract. The Chicago based Debt Relief firm said it used last pass to manage its passwords. However, it says last pass was negligent in its duties, evidenced by the fact that it has experienced two data breaches in the past three months. The class action lawsuit alleges that last pass was negligent with data security stating that last pass used ineffective data security measures to protect its customer's information. The lawsuit states there is a strong probability that entire batches of stolen information have been dumped on the black market, or are yet to be dumped on the black market, meaning plaintiff and class members may be at an increased risk of fraud and identity theft for many years into the future.
(01:08:15):
So debt cleanse responded to news of the breach by changing all of its employees passwords for accounts that used LastPass, which took considerable resources. It said it seeks to represent all LastPass users whose information was ACC access was accessed in the breach. Well, that's a, that's a very small number. It seeks certification of the class action, damages, fees, costs, and a jury trial. So, okay. The geniuses over at Debt Cleanse freaked out and totally unnecessarily changed all of their passwords for everything they noticed that last pass made an announcement of a secondary breach following on from the first one, but they somehow failed to heed the statement, which was also right there both times that no user information or passwords were at any time at risk or exposed to either of those as a consequence of either of those two breaches. Now, Leo, I know you and I feel quite similarly about class action lawsuits. You know, from time to time I'm awarded, you know, something like 92, 90 2 cents from, from something I purchased once that faded too quickly if it was left out in the sun or whatever, you know, somewhere some lawyers made some money. Yeah, that's still it is the indivi, the, yeah. The individuals in the class on whose behalf the action was taken netted 52 cents, you know, the
Leo Laporte (01:10:07):
Only, or whatever the other, there is one secondary value to class action lawsuits. Companies still have to pay that money and it's, it's certainly has sometimes a salubrious effect on the accompany you know, maybe stopping them from doing that again, if you know what I mean. Yeah. So there is that. Well,
Steve Gibson (01:10:23):
And unfortunately I mean, I don't, I can't even imagine what a trial would look like, like, because this is technical stuff. I mean, did know. I mean, it's, I mean, you would like it just to be dismissed when the, when under deposition, last pass techie says nothing that happened could have possibly compromised anyone's passwords.
Leo Laporte (01:10:52):
You know, how do you prove that to a judge and jury who are not technically sophisticated? Oh, they bring in you, somebody like you to say, well, I'm an expert and in my judgment it's safe. Yeah. I mean, what else are they gonna do? And just, you know, you've he used to do that. Didn't you testify?
Steve Gibson (01:11:11):
I did. I did. And when I, I tried to explain to a judge who literally had, I will never forget this, to his right was a green oxygen tank. Oh, geez. And he had the nasal cannula Yeah. Up his nose and a mask in case he needed a little extra hit. Holy cow. You know, cow af I mean, this is who was, you know, judging this and it went the wrong way. And I thought, okay, I'm done here. Yeah, <laugh>, this is a, this is dumb. Okay, but we're not done a, a tiny piece of Rackspace overall cloud hosting, business hosting Microsoft Exchange email services was hit 11 days ago by ransomware. Things have not been going well for them ever since. An article published yesterday in IT World Canada summed things up and offered some interesting perspective on the cloud industry overall. Here's what IT World Canada wrote, they said on December 2nd, Rackspace experienced an outage for its hosted exchange environment.
(01:12:19):
The company blamed, quote, a security incident. Unfortunately, first mistake was they didn't say what it was a status update issued by the company. Noted. We proactively shut down the environment to avoid any further issues while we continue work to restore service. Okay, now that really stretches the phrase putting a good face on the problem. You know what? They were too embarrassed. You know, I guess they should have just said, we got hit with ransomware right from the start, because like that happens now, unfortunately. Anyway, back to what I it, world Canada said, they said one week later, the outage continues and wow, the company has Yes, this is like that medi medi story. Wow. And the co the company has confirmed that it is due to a ransomware attack. Rackspace has not indicated how much data might be lost, whether it will pay the ransom or when the managed exchange service will resume.
(01:13:25):
This is the only information from the section of the website dealing with the press. However, in an announcement on its investor's page, the company notes that the hosted exchange business accounts for less than 1% of the company's revenue, which by the way is a hefty 3 billion per year. And on the page, they reinsure investors that the company has cyber insurance and <laugh>, I guess they're gonna be needing it. We'll get to that in a minute. But the but, but world, it said, but the attempt to reassure investors may not be working in an article on December 10th. So that would be last Sunday investment blog market watch criticized the company for being frustratingly closed mouthed about the incident and noted that the company's stock had declined. The article notes quote, since the incident came to light, Rackspace shares have tumbled by a third. This is a relatively small part of the company's business.
(01:14:35):
Only about 30 million a year in revenue, right against 3 billion in total. So yeah, that's 1%. But the bad blood that Rackspace is generating will leave a lasting stain. The stinging critique of the company's communication is significant. But another quote from the article raises an issue that could extend beyond Rackspace to the entire cloud industry. The writer notes quote, while I remain a big believer in cloud computing, the Rackspace attack is an urgent reminder of the risks in relying on cloud for mission critical applications if your provider isn't keeping up with software patches and paying attention to security risks. So the use of cloud computing, even for mission critical applications, has grown rapidly for years. But that growth has accelerated in the past year and has predicted to further accelerate in the next 24 months. And, you know, when, when we had Paul and Mary Jo on Windows Weekly, they were often talking about how Microsoft is like, that's like Microsoft doesn't really care about desktop anymore, right?
(01:15:51):
They just, it's all Azure. And, and we know that a w s is a massive thing for Amazon. So sure enough, and it's funny because I so clearly recall the looks I received from the IT guys who attended Digit search customer advisory board meeting six years ago that I was also invited to. I made some offhand comment about the rack of gear I had over at level three, which brought all discussion to a halt. I said, what <laugh>? And one of them replied, apparently for the entire group, nobody does hardware anymore. Oh, well I do, you know, I like hardware with lots of little blinky lights. But anyway the, the, this piece ends. Senior management has bought into the cloud in a big way. But could investor nervousness from the Rackspace outage have an impact on attitudes in the boardroom when a service that gives you 1% of your revenue leads to a 30% drop in your market share?
(01:17:07):
Cloud proponents made to quote Ricky, Ricardo says the article have some splaining to do. And that was just the first shoe to drop. The second shoe was yes, Rackspace is now facing not one, not two, but at least three class action lawsuits reports are that Rackspace will need to defend themselves. In so far, at least three different class action lawsuits related to this recent ransomware attack from which they're still recovering and may never be able to fully recover from the attack left countless companies of, unfortunately it was tons of small and medium sized businesses that had all outsourced their email to exchange server hosted by Rackspace and they just got wiped. So it's not clear that it's coming back. In an interview last week, rake's, Rackspace suggested they may not be able to recover all their customer's data, which they referred to as legacy data.
(01:18:16):
The company also appears to have given up on hosting exchange email servers in its cloud. Yeah. And said it was migrating all its existing customers to Microsoft 365. Right. Give it to Microsoft, which according your documents that Rackspace file with the s e C will cost the company 30 million. Right? Cuz that's that 1% of its revenue. But who cares? It's certainly not worth the headache. I imagine that hosting exchange server was more of a means to an end for Rackspace, you know, a way of establishing a relationship with an enterprise, and then over time, probably moving more of their non email business into the cloud. You know, that didn't work out so well. Okay. The trend appears to be what we're seeing broadly is everyone is getting very tired of the consequences of these apparently never ending attacks. Governments are going on the offensive saying that they're no longer going to be waiting to be attacked.
(01:19:27):
The you know, they're gonna go proactive. Other governments, yes. Other governments are calling their own employees criminally negligent and bringing them up on criminal charges. I don't know if that's fair, but Right. And the class action ambulance chasers now only take a day or two to file their lawsuits. Why is all this happening all of a sudden? Well, we know because criminal organizations, apparently some with state level sponsorship and protection have realized that the cryptocurrency boom, coupled with the presence of exchanges to local fiat currencies, provides them with a means of being anonymously paid. That provided the motivation. Clever hackers provided the means, and the final piece, endless opportunity was readily supplied by the industry's historically lacks cybersecurity. So today everyone is furious, besides themselves pointing fingers and suing, but who's still never being held to account by a perversion inherent in the system.
(01:20:40):
We've built the suppliers of the buggy, brittle, and breakable systems are never to blame. I would say stay tuned. That's gonna be next. Juries are made up after all of end users, and they're not gonna be sympathetic after everything this industry has been putting them through lately. Oh, and one last piece, speaking of losing patience, another country goes on the offensive. On December 11th, it was reported that Japan kind of, you know, quiet, peaceful Japan intends to establish a legal framework that will allow strengthening of defense measures in cyberspace, including the ability to attack preemptively <laugh>. The Japanese government intends to change the rules so that it can start tracking potential attackers and breaking into systems, the attacker systems as soon as there's a potential threat. Hmm. Cur current regulations make it extremely difficult to apply such measures unless there's an emergency situation that requires the mobilization of defense forces after a military attack.
(01:21:55):
The plan is reflected in a proposal to amend the national security strategy that has just been submitted to the governing coalition. The draft amendment is expected to be approved by the cabinet before the end of this month. So we're clearly seeing a changing of attitudes across the board. Wow. Indeed, my friend. Okay, get this Leo. The following was sent to me via Twitter dm, and I'm not sure that this individual would want his name published, so I'm not sharing it. But he's the Australian cybersecurity person who was tasked with finding and downloading the MetaBank data from the dark web for analysis. He sent the following, he said, hi, Steve. I just wanted to drop you a line about the MetaBank data. You mentioned insecurity now 900 that you didn't know what use the data would be if it wasn't formatted properly. I'd like to offer one way it could, could be useful in the wrong hands.
(01:23:07):
I work in cybersecurity for a law enforcement government department in Australia, and I was tasked with finding and downloading the MetaBank and Optus data. I absolutely agree. The data held within the extracted data was not formatted and was of limited use in its raw format. He says, parz all CSV files with different structures, presumably depending upon the database. It was extracted from closed parz. He said, it's true that the data is of limited use as the medical information about the patients was all in code format, which meant nothing, excuse me, without the application to match the code to the treatment the patient received. However, my job was to search through the data to see what law enforcement officers details were leaked. Can you imagine how bad it would be if an individual used their government-issued email address, which has their law enforcement division within the domain of the email address to sign up with MetaBank?
(01:24:21):
Suddenly you would be able to match a name and home address of a person and verify it was a person working for the law enforcement division. Thanks to their email address In the wrong hands, I'm sorry, it says in the hands of the wrong people such as criminal gangs. This information could put these law enforcement officers in serious danger. Sadly, data of this nature was leaked and our organization now has to help protect these individuals. I'm sure you've already considered this scenario with leak data. Really, any leak data could be used this way. But considering the high profile nature of this leak, we are having to take it very seriously. Thank you for such a wonderful podcast, and thank you for the very interesting note from the field. I'm, you know, it, it's abundantly clear that this podcast has aggregated quite an amazing group of listeners.
(01:25:21):
I am continually humbled and flattered by the people who take the time to listen to these ramblings every week. So thank you all. Paul Jolly wrote, I know you've spoken of UTF eight in past episodes, but was left, but was left asking myself what could possibly be the legitimate purpose of some characters after I encountered. And then he, he has a u plus 2 0 0 B. So that's a Unicode character. He said recently, he said, I appreciate English isn't the only language used in the world, so I understand why this extended character set is useful. But as previously described on the podcast, can also see how it can be abused type of squatting and domain names, for example, by using characters that look like their asky equivalence. Getting back to my recent experience, he said, I received an email where the sender name would not sort alphabetically in my email client.
(01:26:26):
I didn't think much of it at first, but then decided to investigate. It turns out that they had inserted a zero width space character. Wow. Wow. Before the first letter of their name, making it appear at the top of my sorted list. That's very sophisticated. Holy cow. Yeah. The three bites could be seen in a hex editor as E two hex 80 and then hex eight B, but would not visibly appear in notepad. He said, I've never encountered this kind of white space before and thought it would be worth mentioning because I expect something like this will only be used for mischief. Try it yourself by renaming a folder in windows and putting this special character at the beginning to make your folder a appear at the top of assorted list without any visible white space or pasted in notepad a few times and see the file size increase when you save the file.
(01:27:30):
But there's nothing to select or highlight on the screen. The world doesn't need this. Hmm. So anyway, another lesson here is that for every useful thing we create, there are clever people who will subvert that use into abuse. Yep. oh a spin write note. Spin writer's currently at Alpha Release five with many further improvements already implemented for its next alpha release. Everything is going quite well, thanks to a truly gratifying level of engagement. We now have exactly 500. When I looked this morning, registered users in GitLab, we've been uncovering mysteries around the edges that I've been working to solve. And also things that I didn't anticipate. And I should also mention that the, the people testing are also solving these mysteries as well. For example, in six one, it's possible to select a drive from the command line by its model number.
(01:28:38):
But Western digital's model numbers contain spaces and spaces are used as a delimiter to separate command line entities. So the answer's simple, right? Allow tokens to be quoted to have their contents parsed. Literally, when I wrote the command line parser, I forgot to add support for quoting literals. So that's an example of something that needs to get fixed. Someone booted spin right from a cd, and it didn't notify them that their request for logging to the CD could not be honored. So it's, you know, those sorts of things. They're things I want to take the time to get correct now so that I don't have to correct them later. And we do have a couple of mysteries. One guy who has two HP all in one PCs if he warm boots from Windows 10 into spin, right? Spin right locks up as soon as it starts running, you know, trying to actually run on the drive.
(01:29:39):
But if he cold boots the machine, everything works fine. Okay. Now we might say, okay, so don't warm boot. And that might be the fi you know, <laugh>, you know, there you go, doctor. It hurts every time I raise my arm like this <laugh>. Well, don't make your arm like that. You're a silly boy. <Laugh>. Exactly. So, you know, that might be all that, you know, I'm, we, we may end up saying, okay, you're gonna have to call boot, but it could be a symptom of something more important. So I found one of those machines on eBay for $47 course. God, I can't believe you. And it's in my, it's in my car's trunk right now. Wow. I'll figure out what's going on. Dedication, and I'll answer, I'll answer the question. That's best expressed using one of my favorite spin right development abbreviations, which now comes up frequently.
(01:30:32):
The abbreviation is W T F <laugh>. There's a lot of that. I've been doing a radio show for 19 years. It's basically filled with that. Yeah. Wow. Yeah. I have one piece of miscellaneous to share, and then we'll take our last break. The Zima board fan list, single board computer that I stumbled upon and told everyone here about has apparently been a big hit. I keep seeing kind of casual, offhand mentions of it in the postings among those who are testing spin, right? And also in Twitter messages. Okay. So given how long it takes to obtain one after ordering it from Hong Kong, and the fact that shipping is not free, I was surprised and delighted to learn a few hours ago that Amazon has all of them in stock and available for astonishing same day arrival, not even next day today at least in my location. So as a prime subscriber, the cost is $10 more than ordering the ZMA board directly from its source, but there's no shipping cost. So it's $129 versus one 19 and you can have it today. So anyway, I know that not having everyone, not that not everyone bothers being a Prime subscriber but for what it's worth, it's on Amazon. So I just wanted to share that bit of happy news. Let's take our last break. I'm gonna sip some water, and then we're gonna talk about Apple's big announcements of, of encryption improvements.
Leo Laporte (01:32:06):
Our show today is brought to you by Express vpn. We talk all the time about VPNs. I think by now you certainly know what a VPN could do for you. So really the only question is which VPN n to use. And I am very clear in my mind why I use Express V P N Let me go through this for you, just to kind of give you some sense of why I've chosen V P N from Express V P N. So first of all, Steve's always said this, you should never use a p n that does any logging of any kind. You know, they shouldn't have a record of your visit. They shouldn't have any records of what you've been doing on the vpn. N that's true privacy protection. See, the problem is with the V P n, the, the reasons you use A V P N to protect yourself from spying by your internet service provider are from being attacked in a coffee shop or eliminate geographic restrictions, those kinds of things.
(01:33:02):
All that privacy and security stuff, you just really just kicking the can down the road. The VPN provider, the place you emerge under the public internet potentially could be as bad as the, as the hacker in the coffee shop or, or the ISPs listening to. So a free vpn n for instance, is not worth the money you're paying for <laugh>. It's really a bad idea because those people are incented to spy on you to make money on you some other way. What you really want is a VPN where they charge a reasonable amount, express VPNs, about seven bucks a month. They use that money to provide many servers all over the world. So you've got great geographic access. They rotate their IP addresses, keep 'em fresh so that people aren't blocking you because well, that IP address, we know where that comes from. And most importantly, they put their efforts to giving you lots of bandwidth so you don't feel slowed down and keeping your privacy secure.
(01:33:55):
Ex There was a great article on bleeping computer, actually, it was thrilled to read it. And we, and we, and of course we trust Lawrence Abrams, the creator of Bleeping computer. He talked a little bit about how Express VPN works, and it was very impressive. They use a custom Debian distro, which wipes itself daily. So every reboot every morning they reboot and it wipes everything off the drive completely. But that's, and for many that would be, well, that's good, that's enough, but no. But what about that during that day? Is there anything logged? Well, they also created this truster server technology, which runs in RAM and it's sandbox. So when you press that big button on your, on your phone or your router or your computer to turn on express V P N, and it makes the connection to a server, you can make it near you or anywhere in the world.
(01:34:40):
When it makes that connection, it spins up At that time, your u your version of the trusted server, you and only you are using that. So there's no cross population, it's sandboxed. And when you're done and you close the vpn, it's gone. And it doesn't leave a trace. And by the, the way they have regular third party audits to verify that their privacy policy is exactly what they do. The, the auditor verified, the trusted server does what it says it does, all of that. So it's absolutely true. But there's another way. I know it's true because from time to time, there are countries unlike ours, where authorities will come and seize the servers without a warrant, without a knock. They'll just come and take 'em. No chance to wipe 'em. They just take 'em. This happened in Turkey. You can read the news reports, express V P N, they barged in take the servers.
(01:35:31):
They're trying to track somebody down. What did they find? Nothing. There was nothing, nothing on the servers. And this has happened many times. So we know Express V P N does that a unique IP address, fresh IP address that is never attached to you or your identity. It is, it is secure. It is done right. I just, I honestly think that they're, you know, if you do the research, you'll love Express vpn. You'll understand why it's the one I recommend. So secure your online activity secure. Maybe even more importantly, your family's on online activity. They now sell like Express VPN sells routers you with Express p n builtin, or you can add it to it. They, they have a list of routers. You can add it to the software too, so that it's running on your router. So your whole family is protected ExpressVPN.com/security.
(01:36:27):
Now, when you sign up for a year, you'll get three months free. That's our little offer to you to get you to use that address expressvpn.com/securitynow that brings you down below seven bucks a month. Don't use a free <laugh> a free VPN provider use ExpressVPN. It's the only one I use. Express vpn.com/security. Now they spell it out. That's the other reason I like 'em. They use vowels. E X P R E S S Express vpn vpn, spell VPN n by the way, dot com slash security. Now, I won't, I won't, I won't insult you by telling you how to spell security now. Use it, enjoy it, feel secure and your family will like it cuz they can unlock shows in all over the world, which is <laugh>. Very wanna watch a little, a little extra anime just to go to Netflix Japan.
(01:37:15):
It's all there for you. And you can go to fragments.com in the us. There you go. And that's right, you can't use it in the US unless you're not in the us. Ah, that's right. Wink, wink, nudge, nudge being a little sneaky <laugh> sneaky Pete, you all right? I love, I love what you're talking about. X ExpressVPN and you disconnect the VPN n you do. It's gone there. That, that Santa Ram <laugh> complete with sad effects. Alright, I really, so this was huge news last Wednesday after the show when Apple announced, yes, we're gonna turn on end-to-end encryption in the cloud. I just got it. Ios 16 two, everybody did Mac OS had an update. You could turn on advanced data protection and it includes cloud backups. But I knew I should not, I should not assume unless I listened to Steve and find out what he has to say about
Steve Gibson (01:38:08):
This. Okay, so last Wednesday, apple posted the news was generated the most feedback, as I said at the top of the show of anything that's happened recently. So I knew we needed to address that today. Before that, I was planning to talk about the technology behind a clever new generic bypass of web application firewalls. Okay, nerdy, but cool. Don't worry. We're gonna get to that next week. Today it's Apple time. So Apple's headline reads, apple advances user security with powerful new data protections. The subhead, which introduces three new terms reads iMessage, contact key verification security keys for Apple id, and advanced data protection for iCloud, provide users with important new tools to protect their most sensitive data and communications. Okay, so we have three new things. Apple explains that iMessage contact key verification allows users to verify their communicating only with whom they intend.
(01:39:17):
We'll see what that means in a minute. Then there's security keys for Apple ID where users have the choice to require a physical security key to sign into their Apple ID account. Okay? So that's gonna be very cool. And advanced data protection for iCloud which Apple explains users will, will be able to obtain what Apple says is end-to-end encryption, to provide apple's highest level of cloud data security, where users will have the choice to enhance the protection of important iCloud data, including iCloud backup photos, notes, and more. Okay? Now before we go any further, I should note that that this just became available. Leo, what was said in Apple's announcement was that it was available for beta now and would be available for non beta by the end of the year. Yeah.
Leo Laporte (01:40:14):
One week later.
Steve Gibson (01:40:16):
Plus you're not. Okay. You're right. Okay. So, but, but that's only the, it's only the iCloud backup. The other two are early 2023 rollout globally and iCloud encryption also the, the, the, the so-called advanced data protection for iCloud that's globally in 2023. As far as I know, it's only in the US for now. I'm
Leo Laporte (01:40:42):
Sure there are all sorts of issues of rolling it out globally, so I understand. Yeah. Yeah.
Steve Gibson (01:40:46):
Okay. So, okay. Let's look at each of those three security improvements. The good news is that most of the information is available about the thing that people are most excited about which is, you know, that not even Apple will be able to get in type of true user encryption of user data stored in the cloud. But because that's where the most information is, I'm gonna say that for the last, the bad news is that neither of the other two security improvements is explained anywhere that I've been able to find in much detail. But at this point, maybe there's not much detail to be had of their iMessage contact key verification. Apple only said, they said conversations between users who have enabled iMessage contact key verification receive automatic alerts. If an exceptionally advanced adversary, such as a state-sponsored attacker were ever to succeed in breaching cloud servers and inserting their own device to eavesdrop on these encrypted communications.
(01:41:59):
And for even a higher security iMessage contact key verification, which I think is where it gets its name, users can compare a contact verification code in person on FaceTime or through another secure call. Okay? And that's all we know, presumably until it's rolled out early next year. They do provide a photo showing a little emergency triangle icon underneath, which is written, an unrecognized device may have been added to, and then whatever the account's name is, you know, Steve, Jenny, whatever account, and then they have a, a clearly clickable in blue on their, in their screenshot options, dot, dot, dot. But we don't know what one's options might be. Okay, so this idea of a foreign device being added to an account covers one of the two theoretical ways that we know iMessage can be subverted. Since iMessage conversations are broadcast to all of an account's registered and logged on devices, if an adversary were to somehow get their own additional device added to a user's account, that additional device will automatically be privy to all of the attacked accounts messaging.
(01:43:25):
So this seems like a useful feature somehow Apple has has arranged to be able to assure that even the, that in the event of that happening, this aspect of some sort of integrity checking won't be fooled and that message would appear informing you that an unknown device was, was now sharing your account. But since Apple handles all key management for its users, the iMessage attack we've always wondered and worried about is law enforcement serving Apple with a wiretap subpoena, which would compel Apple to surreptitiously add an additional key into an iMessage conversation. Since iMessage can already handle multi-party messaging, adding a hidden key seems eminently plausible and it's unclear under what grounds Apple could refuse an a legal order for something they could probably do. But that's all speculation for which there's no evidence. The issue arises. However, anytime any third party manages keying on behalf of its users, you know, that's the convenient way to do it, but it's less secure.
(01:44:44):
The other piece of this announcement, which will apparently need to wait and see is this means for somehow comparing and confirming what Apple calls this contact verification code. You know, like in person on FaceTime or through another secure call. So like, you know, you're, you're like reading it off of the screen to the other person. This, I'll call it the CVC, is presumably and hopefully a hash of the user's public key, which matches their private key, which is then converted into an Ask E code. So it's, you know, not just binary, gibberish or hex. And note that this is exactly what my favorite messaging agent Thema, which you mentioned earlier, Leo has understood, was important and has always done from the start. So that's all we know for now about iMessage contact key verification. I'm sure we'll talk about it again, you know, next year once it's rolled out.
(01:45:48):
Next up is the so-called security keys for Apple id. Apple explains it by writing. Apple introduced two factor authentication for Apple ID in 2015. Today they say with more than 95% of active iCloud accounts using this protection. That's nice to know. And that's a big number. It is most widely, it is the most widely used two factor account security system in the world that we're aware of and they broke their arm patting themselves on the back. I should clarify that. What we're talking about here is just the use of some other device to receive a six digit code to authenticate a user. So yeah, everybody has that. Okay, then they say,
Leo Laporte (01:46:36):
Although Apple, I don't know if you've experienced it does it nicely by showing you the location of the person asking for the code right? On the map, and then you say allow, and then it shows you the code. I mean, they've done a nice job of that I think, right? Yeah. Right. They're not texting you with a six digit code on your SMS number.
Steve Gibson (01:46:54):
Right? So they said now with security keys, users will have the choice to make use of third party hardware security keys to enhance this protection. Ooh.
Leo Laporte (01:47:06):
Yeah.
Steve Gibson (01:47:07):
This feature is designed for users who often due to their public profile, face concerted threats to their online accounts such as celebrities, journalists, and members of government for users who opt in security keys strengthens apple's two factor authentication by requiring a hardware security key as one of the two factors. This makes our two factor authentication even further, I'm sorry, takes our two factor authentication even further. Preventing even an advanced attacker from obtaining a user's second factor in a phishing scam.
Leo Laporte (01:47:43):
Woohoo. So that's the key, right? Because you can fish that six digit number Yes. But you can't fish a Yuki cuz Nope, it's mine <laugh>. Nope.
Steve Gibson (01:47:53):
Yeah. So we're getting hardware authentication Dons, that's good. And I imagine that Stina and the team over at Yubico is happy to see third party hardware dongle becoming far more mainstream. They've
Leo Laporte (01:48:06):
Offered Yuba keys with lightning for a long time. I have them one that has lightning on one and it's type C on the other. They also have R NFC UIC keys that work, so, yeah, yeah, yeah.
Steve Gibson (01:48:18):
So what I'm, what I'm wondering, Leo, is what stage of authentication is this unlocking your device? Or is this like when you turn, when you need to like put in your passcode at like after the first time you, you turn it back on? I
Leo Laporte (01:48:33):
Would imagine, I would guess it's that second. You know, you're not gonna do it every time you unlock your device. I mean, I maybe you could set that but it's whenever the two factor pops up anyway. Right? Right. Right, but I, I do wonder, and you always, you taught me this, what's the fallback method? Because cuz the weakest link is always the fallback method, you know, so they might be great. They say, well you could use a Yuki or we'll text you a message and that wouldn't be quite as useful. Very good point. Yeah. Yeah. Okay. Now we'll have to learn about that
Steve Gibson (01:49:03):
Encrypting the cloud. Most of the content of that first announcement page is glitz and self-congratulatory hype. The good news is that there's a second page available containing much more detail, but since it leaves out some of the broad strokes, we'll cover them here first. Okay. Ivan Christie, is that who you pronounce his name? K R S T I c? He's, he's, he needs it some more vowels just like Express ES ExpressVPN. Ivan Christ who's Apple's head of Security engineering and Architecture is quoted in this first broad overview saying, advanced data protection is apple's highest level of cloud data security, giving users the choice to protect the vast majority of their most sensitive iCloud data with end end encryption so that it can only be decrypted on their trusted devices For users who opt in advanced data protection, which you'll hear me just abbreviating to a d p cuz they keep saying it over and over and over, keeps most iCloud data protection even in the case of a data breach in the cloud.
(01:50:11):
Now this is what's interesting for users who opt in advanced data protection keeps most iCloud data protected, even in the case of a data breach in the cloud, they're big on this data breach in the cloud here, I have some comments about that later. So, you know, they're, they're naturally not saying that this keeps their hands off of any of their user's data, which is of course the main reason everyone wants this. But rather they're saying it's to protect their users in the event of an iCloud security breach. Okay, fine. Whatever, you know, as long as we can have it. They explain, and here's the interesting bit. They said, iCloud already protects 14 sensitive data categories using end-to-end encryption by default including passwords in iCloud, keychain and health data. Okay? Meaning that, that Apple does not have access to that stuff. Unlike most famously the iCloud backup
(01:51:24):
For users who enable advanced data protection, the total number of data categories protected using this end-to-end encryption rises from that 14 to 23, which then includes iCloud backup notes and photos and more. The only major iCloud data categories that are not covered our iCloud mail contacts and calendar because of the need to interate with the global email contacts and calendar systems, but no iCloud backup. That's the biggie, right? Remember the back in 2016 after the San Bernardino shootings, it was Saed Farouk's phone whose iCloud backups had they been available and had the F FBI not changed the password on the account could have been decrypted by Apple to provide the F B i with the vital evidence that they say they needed at the time. So, you know, this was the big deal about iCloud backup. You know, it, we, we learned that under some situations it could be made available. Yeah. Apple even said
Leo Laporte (01:52:35):
Yes. See, we cooperated. All they had to do was go back to his house.
Steve Gibson (01:52:39):
Right. Okay. So just to, to wrap up the overview, apple is expending some significant effort, in my opinion, to spin this additional encryption as user protection in the event of a breach, presumably to deflect some of the government's and law enforcement's annoyance over more stuff being encrypted. Apple went out of their way to write, they said enhanced security for user's data in the cloud is more urgently needed than ever before. As demonstrated in a new summary of data breach research. Quote, the rising threat to consumer data in the cloud published today. Experts say the total number of data breaches more than tripled between 2013 and 2021, exposing 1.1 billion personal records across the globe in 2021 alone. Increasingly, companies across the technology industry are addressing this growing threat by implementing end-to-end encryption in their offerings. So again, this is Apple saying, you know, we're doing this to protect our users from data breaches because that's a big problem.
(01:53:56):
And of course the users want it because Apple has the keys. Mm-Hmm. <affirmative>. Okay. So that's the broad strokes. There is more good stuff in a se in a secondary document. Advanced data protection for iCloud they write is an optional setting that offers apple's highest level of iCloud data security. When a user turns on advanced data protection, I'm gonna now call it a d p, their trusted devices retain sole access to the encryption keys for the majority of their iCloud data, thereby protecting it with end-to-end encryption For users who to who turn on a d p, the total number of data categories protected using end-to-end encryption rises from 14 to 23. It includes iCloud backup photos and notes. Okay. And more. But that stuff all seriously encrypted. Conceptually, they said ADP is simple. All cloud kit service keys that were generated on device and later uploaded to the, what's called the available after authentication.
(01:55:10):
You'll hear that phrase a couple times more to the available after authentication iCloud hardware security modules. So they have HSMs in Apple data centers get this. Okay, I I'm gonna back up again cuz this is important. All cloud kit security keys that were generated on device and later uploaded to the available after authentication iCloud hardware security modules in Apple data centers are deleted from those HSMs and instead kept entirely within the accounts iCloud key chain protection domain, which again, apple has no access to. Apple does have access to that available after authentication. Icloud hardware security modules where the keys have up until now or up until the user turns that on, that's where they've resided. So they were, they were in hardware, they were projected as well as Apple could, but available after authentication. Now not they are deleted when the user turns that on, those keys are deleted from the HSMs that Apple had, they're handled.
(01:56:29):
They, they, and they're moved into the iCloud keychain protection domain, meaning Apple can't get there. That stuff is sent down to the user for them to decrypt locally. They are not decrypted at apple's end. They're handled like the existing end-to-end encrypted service keys, which means Apple can no longer read or access them. Okay. They wrote, ADP also automatically protects cloud kit fields that third party developers choose to mark as encrypted and all cloud kit assets. When the user turns on advanced data protection, their trusted device performs two actions. First, it communicates the user's intent to turn on a d p to their other devices that participate in end-to-end encryption. It does so by writing a new value signed by device local keys into its iCloud keychain device metadata. Apple servers cannot remove or modify this attestation while it gets synchronized with the user's other devices.
(01:57:42):
Second, the, the device initiates the removal of the available after authentication service keys from Apple data centers. So that's what I was just talking about before. Now we're getting more into the detail. The device initiates the removal of the available after authentication service keys from Apple data centers. As these keys are protected by iCloud HSMs, this deletion is immediate, permanent and irrevocable. After the keys are deleted, apple can no longer access any of the data protected by the user's service keys. At this time, the device begins an asynchronous key rotation operation, which creates a new service key for each service whose key was previously available to Apple servers. If the key rotation fails due to network interruption or any other error, the device retry the key rotation until it succeeds. Okay. This is very cool and very serious. Apple is saying, since we once had those keys, we want all of those keys not only to be deleted but then rotated out of service so that even though we've already deleted the keys, you are now using new keys that we have never seen and never had anywhere in our possession in an unencrypted form.
(01:59:16):
Excellent. Yes. Yes. It is really serious. So they said after the service key rotation is successful, new data written to the service cannot be decrypted with the old service key. Right? Because, you know, key rotation means replacement. It's protected with the new key, which is controlled solely by the user's trusted devices and was never available to Apple. They wrote. So notice what's been quietly acknowledged here. This has nothing to do with breach protection anymore. This is all about Apple strongly selling the truth that they no longer have access to their users'. Icloud device backups, photos and notes. Wow. Okay. Then they say, when a user first turns on ADP Web Act. Now here's some interesting caveats cuz you know, they've got some things that they needed that they, that they've got that they, they offer some things that they have to have the keys for at their end if you want those things. Yeah,
Leo Laporte (02:00:18):
We've talked about that. That there is a limitation of what you can do if you don't have access to the data.
Steve Gibson (02:00:25):
Right. They said when a user first to turns on ADP web access to their data@icloud.com is automatically turned off.
Leo Laporte (02:00:36):
Oh, that's a big one.
Steve Gibson (02:00:38):
This is because iCloud web servers no longer have access to the keys required to decrypt and display the user's data. Wow. The user can choose to turn on web access again and use the participation of their trusted device to access their encrypted iCloud data on the web. Oh. After turning on web access, the user must authorize the web sign in on one of their trusted devices each time they visit icloud.com. Good. The authorization arms the device for web access for the next hour. This device accepts requests from specific Apple servers to upload individual service keys, but only those corresponding to an allow list of services normally accessible on icloud.com. In other words, even after the user authorizes a sign in a server request is unable to induce the user's device to upload AER upload service keys for data that isn't intended to be viewed on icloud.com.
(02:01:51):
You know, such as health data or passwords in iCloud key chain Apple servers request only the service keys needed to decrypt the specific data that the user is requesting to access on the web. Every time a service key is uploaded, it is encrypted using an ephemeral key bound to the web session that the user authorized and a notification is displayed on the user's device showing the iCloud service, whose data is temporarily being made available to Apple servers. Now what this really means is if you really don't want Apple ever to have access, you have to stop using icloud.com. Icloud.Com is a backdoor in, I mean, they've, they've, they've done everything they can, all the due diligence possible. They've, they've, they've prescribed their access, they've limited it, they've, but if you're saying you want your data to be shown on a webpage that's gonna come from our server. Right. So you have to give us transient access to that
Leo Laporte (02:02:57):
And presumably if they wanted to, they could cash that key. Right? So you're giving them a key again and suddenly Yeah. So if you really wanted be private, you wouldn't use the web.
Steve Gibson (02:03:08):
And given that turning a DP on forces a key rotation, maybe turning it off and back on again, ah, would rein rotate? That would re initialize those keys? Yeah. Yeah. So they said ADP and icloud.com web access settings can be modified only by the user. These values are stored in the user's iCloud key chain device metadata and can only be changed from one of the user's trusted devices. Apple Servers cannot modify these settings on behalf of the user, nor can they roll them back to a previous configuration. Again, not about protection from data breaches. It's all obviously about Apple going well out of their way to demonstrate exactly how they no longer have access. Then they said in most cases, when users share content to collaborate with each other, for example, with shared notes, shared reminders, shared folders in iCloud Drive or shared or iCloud shared photo library and all the users have a d p turned on. Apple servers are used only to establish sharing, but don't have access to the encryption keys for the shared data. Again, they've really done everything they could. So
Leo Laporte (02:04:23):
The blob would go an encrypted blob would go through Apple, but never be encrypted, unencrypted to add Apple.
Steve Gibson (02:04:29):
Right.
Leo Laporte (02:04:30):
And then presumably I'd have to share a key that's part of the sharing and I'd have to share a key with the recipient. Right.
Steve Gibson (02:04:35):
So it would actually actually be, it wouldn't be the encrypted blob, it would be the, the, the key would get shared to the other device and then the device would do the decryption of, of the, so the
Leo Laporte (02:04:48):
Data's device to device shared it's peer to peer?
Steve Gibson (02:04:51):
No, no, no. The the keys, right. The but
Leo Laporte (02:04:55):
The data. So I have some data on my phone I wanna share with somebody else still gonna go through Apple Has to go through Apple,
Steve Gibson (02:05:00):
Right, exactly. Because it, it comes from, from your iCloud key chain that they don't have access to. Right. To the other per the other account's iCloud key chain.
Leo Laporte (02:05:10):
So I have my photos are on Apple's iCloud. I want to share a, an album with Lisa. I would send her the key and then she could get the data from Apple encrypted as it is with Apple, download it and un unencrypted locally. Yeah. Right. That makes sense.
Steve Gibson (02:05:26):
Right. So they said the co the content remains end-to-end encrypted and accessible only to participants trusted devices for each sharing operation. A title and representative thumbnail may be stored by Apple with standard data protection to show a preview to the receiving users. Okay. Also other little gotchas here, like this is why this, you know, they had to work to do this. Selecting the anyone with a link option when enabling collaboration will make the content available to Apple servers under standard data protection as the servers need to be able to provide access to anyone who opens the URL iWork collaboration and the shared albums feature in photos don't support advanced data protection period. When users collaborate on an iWork document or open an iWork document from a shared folder in iCloud drive, the encryption keys for the document are securely uploaded to iWork servers in Apple data centers.
(02:06:32):
This is because realtime collaboration in iWork requires server side mediation to coordinate document changes between participants. Photos added to shared albums are stored with standard data protection as the feature permits albums to be publicly shared on the web. Okay. So they also said so, so those are the caveats. Basically, they've done everything possible. The typical user who isn't using icloud.com and doesn't want to do like dynamic document and photo sharing, they're locked down tight when they turn this on. They said the user can turn off ADP at any time if they decide to do so. Two things. First, the user's device first records their new choice in iCloud keychain participate. So participation metadata and this setting is securely synchronized to all their devices. Second, the user's device securely uploads the service keys for all available after authentication services to the iCloud HSMs in Apple data centers.
(02:07:48):
In other words, you, you turn off adp, here are the keys Apple that you're gonna need to return to us to previous. This is the way we've always encrypted your stuff before mode. And they said this never includes keys for services that are end-to-end encrypted under standard data protection such as the iCloud key chain and health. They said the device uploads both the original service keys generated before a D P had been turned on and the new service keys that were generated after the user turned on the feature. This makes all data in these services accessible after authentication and returns the account to standard data protection where Apple can once again help the user recover most of their data should they lose access to their account. And now this is really interesting. The requirements to turn on advanced data protection for iCloud include the following.
(02:08:52):
In other words, what you have to do to get this on in the first place, and Leo, you you you're mentioning of what happens if you, if you lose your Yuba key is what put me in mind of this because again, apple can't help you. So they said the user's account must support end-to-end encryption. End-To-End encryption requires two factor authentication for their Apple ID and a passcode or password set on their trusted devices. In other words, that 5% globally who don't have what they consider two factor authentication, they can't turn on a d p, they've got a first set, you know, they better security on their device. So that has to be there. Second devices where the user is signed in with their Apple ID must be updated to iOS 16.2 i iPad OS 16.2 Mac OS 13.1 TV OS 16.2 watch OS 9.2 and the latest version of iCloud for Windows.
(02:09:59):
This requirement prevents a previous version of iOS I iPad os, Mac, OST v o s or watch os from mishandling the newly created service keys by re-uploading them to the available after authentication HSMs in a misguided attempt to repair the account state. Right? You wouldn't want I mean it used to be that all of these I previous iOS versions were using, you know, if if they, if they couldn't access something in the iCloud, they go Uhoh apple must have lost the keys and it would send them again. Well that's exactly what we don't want now. So you gotta have the latest version of everything. Finally, the user must set up at least one alternative recovery method. One or more recovery contacts or a recovery key, which they can use to recover their iCloud data if they lose access to their account. And Leo, I have not had a chance to play with this. I didn't realize it was already there. So we, we'll find out as we, as we turn on a d p what this alternative recovery method, one or more contacts, recovery key and so forth is all about. Yeah,
Leo Laporte (02:11:18):
I, I I think somebody said you should store the recovery keys in your password vault. So somebody's turned it on in our chat room and then they said that's what they, okay, so you might get now, you know, you usually do get with these things, you know, five use once recovery keys, that kind of thing.
Steve Gibson (02:11:33):
Yeah, yeah, yeah. I mean, you know, you, you, you want that when you, when you've got a, you know, a no way out scenario.
Leo Laporte (02:11:39):
Yeah. Print it out and put it in your safe or something.
Steve Gibson (02:11:41):
Yeah. I mean, I said if the recovery methods fail here it is. If the recovery methods fail, such as if the recovery co the recovery contacts information is out of date or the user forgets them, apple cannot help recover the user's end-to-end encrypted iCloud data. Period.
Leo Laporte (02:12:02):
Wow.
Steve Gibson (02:12:03):
Good. They finished good.
Leo Laporte (02:12:04):
Yep. That if they said anything else, it wouldn't be good.
Steve Gibson (02:12:07):
Right. Advanced data protection for iCloud can be turned on, only on only for Apple IDs. Managed Apple IDs and child accounts, which varies by country or region are not supported. Hmm. So I am officially 100% impressed. You know, we heard what you need to hear, which was that if you lose your device or forget your password and are unable to authenticate and none of the emergency recovery methods we made you set up when you turned on advanced data protection available after we made you jump through all those hoops and acknowledge that you know, your firstborn might be up for sacrifice. <Laugh>, there is truly nothing we can do to help you turned it on. We made you jump through hoops, you acknowledge the risks and now it's on you. So Yay. Good. You know, it sure took us a long time to get here, but we are here at last. Yeah. everything that Apple is storing for us is encrypted in our devices before it ever leaves them. They're storing keys and key chains, but they cannot decrypt those key chains because that's the one ultimate key that's being held by the user's device. So Apple has finally been willing to move the rest of the keys that they were holding into the key chain to which only its users have access.
Leo Laporte (02:13:31):
Very good. Very, very good. Right. Can you see any holes in that?
Steve Gibson (02:13:39):
No. No. The only thing might be that apple could say to the fbi, well, if the user logs into their icloud.com, then we could get a snapshot. Right? But unless the, but it's, so in that sense, you know, they're, they're having to, in order not to lose the feature entirely, they're saying, okay, well if you still want icloud.com, we'll give it to you. And we, we double pinky swear that we're not going to, you know, do anything with the data that we shouldn't. We've
Leo Laporte (02:14:09):
Talked about this before. It's why Dropbox and, and OneDrive and Google Drive, none of them do this end to end encryption, because you lose capabilities when you do it. And I think what Apple's done is actually kind of interesting,
Steve Gibson (02:14:21):
Actually, it's why I like sync sync.com does have true end-to-end
Leo Laporte (02:14:26):
Fully encrypted, but then they, then it's hard for them to de-dupe. I can't remember what all the features were, but there were features that you lose if they can't see the data. Right. Chiefly de-duping, which is only for their benefits. So you don't, you know, waste their storage needlessly. Yeah. But I think the ability to give them a temporary one hour key so that you can look at the stuff, you just have to trust that they'll delete that key. Or as you said, you could rotate the keys. We should play with that and see how long it takes, for instance, to rotate the keys. Yeah, yeah, yeah. You know, if it takes an hour, well, that's no good. If it's instant, no, then you could do that all the time.
Steve Gibson (02:15:00):
I think. I think it'll be instant.
Leo Laporte (02:15:01):
You should be right.
Steve Gibson (02:15:02):
Yeah. Yep. Yep. Absolutely.
Leo Laporte (02:15:04):
Yeah. this is why you listen to the show. I don't need to say this, but I say it every week. This is the best stuff. And when I see stories like Apple is ending and adding end to end encryption, all I can think is, well, I can't wait to hear what Steve has to say about this. Well, now we know. Now we know. That's why we count on 'em. Mr. Gibson, you'll find him@grc.com. The Gibson Research Corporation. Somebody was you mentioned this, this apple light pen video that was going around. Uhhuh <affirmative>. Somebody posted it I can't remember where, probably on Macedon and said, that's not Steve Gibson, is it <laugh>? Yeah. Yeah. It's, it's Steve Gibson a long time ago. It's great. That's I guess where GRC came from, the Gibson Research Corporation. These days, the research is mostly around spin, right? Getting your solid state or hard drive back to normal working fine. It is the world's finest mass storage, recovery and maintenance utility. It's a good thing for maintenance as well. And he is working hard on 6.1, as you've probably heard. 6.0 is the current version. Don't be put off by the fact that it's been there since 2004, bug free since 2004. How about that bug
Steve Gibson (02:16:13):
Free? That's what we're trying, that's what we're trying to do on six one.
Leo Laporte (02:16:16):
Yeah. You will get a copy of six one if you buy 6.0 right now. You also participate in the development. It's just a matter of well, I, I won't make any promises for Steve, but it's just around the corner. How shall how should we put that by the end, end of next year? <Laugh> for sure. <Laugh> 6.1. <Laugh>. No, I, no, I don't even gonna say that. <Laugh> poor Steve. He's, you know what? God bless you. You're just putting in the effort to make sure it's absolutely robust. You got a $40 all in one in the trunk of your car, <laugh>, just so you can check, check it.
Steve Gibson (02:16:51):
Actually, while, while Lori was down last week with the flu, I worked 18 hours a day. Oh yeah. On spin ride. She wa because I couldn't get near her and we couldn't have any fun or didn't
Leo Laporte (02:17:00):
Have any anything, so didn't have anything else to do. So, yeah.
Steve Gibson (02:17:02):
And she was really worried by like the end of the fifth day. She said are you okay?
Leo Laporte (02:17:06):
You're self-sufficient. She should know that. Yeah. Yeah. You spent most of your life self-sufficient. That's, that's true. It's the same thing. You have to balance a, a li life work balance. And it's not easy for us geeks, cuz we get no tunnel vision and that's all we can think about. I'm looking at some code right now thinking I could probably simplify that <laugh>. All you have to do is go to grc.com, pick up a copy of Spin, right? That's Steve's bread and butter. While you're there, take a look at all the other free things he offers, like shields up and on and on and on. Plus of course, the podcast, he's got 16 Kilobit audio versions that's for people who really want a small download. He made that for Lane Ferris, who is, you know, in a bandwidth constraining environment. She downloads it and makes a human beautifully written, crafted transcription.
(02:17:55):
Somebody said the nine hundred's not up yet, but it takes a few days. Takes a few days. So as soon as it's done, it'll be up on the website there. Yep. He, he also offers, offers 64 kilobit versions for those who have ample bandwidths. Go to the GRC site to get that. And lots of other great stuff. You can also leave feedback there, grc.com/feedback. He's also a twitterer. He's still on the Twitters at sg grc and his dms are open. Talk about Brave. So you can leave him a message there at SG grc and he posts a, posts a link to the show notes there every week. So that's another place you can get those. Those are good if you, if you listen to the show, get the show notes, they're either on his website or you can get 'em from, because that you could read along, but it's got links, it's got pictures. The show notes are a really great resource that Steve puts a lot of effort into it. It's basically his weekly column. We do <laugh>. I shouldn't now look sad. He's like, yeah, I don't wanna put you in. You know, it's good. You're good. You do good.
Steve Gibson (02:18:55):
No, I know how much work. Work,
Leo Laporte (02:18:57):
You're
Steve Gibson (02:18:57):
Right. It is a weekly
Leo Laporte (02:18:58):
Column. It's a weekly column. Yeah, but of how many thousands? It's probably 5,000 words if it's a, if it's a penny. Yeah.
Steve Gibson (02:19:04):
This one is 23 pages. It was a long
Leo Laporte (02:19:06):
One. Holy cow. Look at that, folks. Yeah. we have copies of the show at our website, tweet tv slash sn. If you're a Club TWI member, you can get an ad free version of this show. Seven bucks a month, one buck less a blue check on Twitter. What do you get? Ad free versions of this and every other show you get access to shows we don't put out anywhere else like HandsOn Macintosh with, with Micah, Sergeant Hands on Windows with Paul Throt. We've got you know kind of fireside chats with people like Steve in our club at the, that's the Discord, which is wonderful. You also get of course the Discord access, which means you can chat with people. We're doing our code. We have a coating section in the Discord, and we're, everybody's going crazy over the advent of code problems. It's been great. I I've twice now gone in there going,
Steve Gibson (02:19:53):
Guys I don't understand.
Leo Laporte (02:19:55):
And they go, well, lingo <laugh>, if you just what you gotta do is carry the frame it and post it over there and you're great. And I said, oh, thank you. Syk, who is our current champion, he's the fastest in there. He does 'em in minutes. And Tom Reins, thank you both for helping me out in there. See, being a member of the club's great, a lot of fun. We also have a yearly subscription if you want to give it as a gift. What a great holiday gift that'd be for a geek in your life. And their corporate subscriptions too. Hey, you want to bonus your employees? Give them a give 'em a club trip membership. They'd appreciate that. It's all available at twit tv slash club twit. You can watch us do the show every Tuesday right after Mac Break Weekly.
(02:20:36):
If Mac Break weekly goes long, it might be a little late. It's supposed to be at one 30 Pacific, four 30 Eastern, 2130 UTC live.twit.tv. That's a live audio or video stream. Then you can chat live in the Discord or on our free IRC server. We have a lot of open, you know, Steve, I've gotta get in your forums. Everybody says, oh, you should be in the Gibson's forums. They're great. So Steve has his own forums@grc.com. We have our twit wide forums for all the shows@twit.community. The Mastodon instance, which I am now officially opening only the listeners. So you gotta you gotta say in your, I want to join. Don't say I want to join. Say something like Steve sent me, or, or Leo sent me. And then I, cuz I it, I don't want it to get too big. I want it to be, it's a community.
(02:21:26):
Four listeners at Twit Social, so twit.community for the Discourse Forums, twit Social for the Mastodon. Let's see, is that IRC twit TV for the irc? I think that's all. I think that's everything after the fact. You can get the show on the website, twit Do TV slash sn and as well as on Steve's website, there is a YouTube channel for security now. And this full-time YouTube security now shows all of them. And then of course subscribing your favorite podcast player might be the easiest thing to do. Just subscribe and you'll get it automatically the minute it's available. At no, at no cost. No salesman will call Steve. Have a wonderful, what are you reading these days? I'm
Steve Gibson (02:22:09):
<Laugh>, I'm on, let's see,
Leo Laporte (02:22:12):
Book 73 of the <laugh> Silver Ship Saga. Yeah.
Steve Gibson (02:22:17):
And I, I do agree with your criticism. I heard you talk about it on Sunday that, I mean, it is a, it's a,
Leo Laporte (02:22:23):
It's Tom Swifty. It's, it's the hero. That's all I, the only thing about the hero, he is so perfect. Yeah. He, Alex Yeah. Alex, Alex Al, Alex Racine. Yeah. A as opposed to Jim Holden, who's like a real person. Yeah. Or better yet, the Detective Miller who's really to Yes. Oh, Miller's got problems. Oh, but I tell you what, I just finished Leviathan Wakes of the Expanse Saga. And you've been telling me, all the listeners have been telling me how great that is. It is really well written. I was surprised I got a kick out of you. Say, God, the, the, the series is so long. I go, Leo, you haven't done a 75 book series yet. Wait, <laugh>, when Rick Brown's series goes to a, when the Frontier Saga goes to film, then you'll know, Steve, it's always a pleasure. Thank you so much. Have a wonderful, we'll be, I should explain, we'll be back for one show before Christmas next week on the 20th, and then it's a best of on the 27th. Nice. And then January 3rd, we're back on the third. All new shows for the all new. Yeah. Have a great week, Steve. We'll see you next time. Okay. Ciao. Bye.
Jason Howell (02:23:29):
Don't miss all about Android. Every week we talk about the latest news, hardware, apps, and now all of the developer goodness happening in the Android ecosystem. I'm Jason Howell, also joined by Ron Richards, Florence Ion and our newest co-host on the panel When To Dao, who brings Her Developer Chops. Really great stuff. We also invite people from all over the Android ecosystem to talk about this mobile platform we love so much. Join us every Tuesday, all about Android on twit TV
... (02:24:02):
Security Nooooow.