Security Now Episode 884 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for security. Now, Steve Gibson is here. We conclude our 17th year of podcasting. With this episode, we start year 18. Next week. We'll look back at patch Tuesday. How many years have we been doing that? Yes, some more Microsoft stuff. We look at Facebook's intention to increase end to end encryption in messenger. It's about time. And then Steve answers a very interesting and puzzling question. Can a remote server's private key, be derived simply by monitoring a sufficient number of connections. The answer might surprise you. It's all coming up next on security. Now, podcasts you love from people you trust. This is TWI.
Leo Laporte (00:00:50):
This is Security Now with Steve Gibson episode 884 recorded August 16th, 2022 TLS private T leakage. This episode of security now is brought to you by BitWarden. Get the password manager that offers a robust and cost effective solution that can drastically increase your chances of staying safe. Online. Get started with a free trial of a teams or enterprise plan or get started for free across all devices as an individual user at bitwarden.com/twit. And by NewRelic use the data platform made for the curious, right now you can get access to the whole NewRelic platform and 100 gigabytes of data per month. Free forever. No credit card required. Sign up at newrelic.com/securitynow. And by Secureworks. Are you ready for inevitable cyber threats, Secureworks, detects ever-changing threats and defends against them with a combination of security analytics and human intelligence. Visit secureworks.com/twit to get a free trial of contagious.
Leo Laporte / Steve Gibson (00:02:00):
XDR it's diver security. Now the time to talk about all those things to protect you and your loved ones on windows and Mac, and there he is living long and prospering the great Steve Gibson. Hello Steve. Yo Leo. Great to be with you. I frightened you a little bit before we began recording. When I said that this was the final podcast. Yes. Don't say that. And I needed to follow that up with of our 17th year. Oh, what a relief now finished 17 years. That's amazing. That is amazing. Next week. We're next week, we're gonna start to get serious <laugh> because you know enough, this figure out how to do this enough of the silliness. Let's let's do a show. Yes, no more fooling around Uhuh. So we've only done 883. This will make 884 of these little things. That's amazing. That's just, it's kind of, we, neither of us had any idea would go on this long.
Leo Laporte / Steve Gibson (00:03:03):
This was all your fault too. Of course, of course. Course I take full, full blame you in that, you know, leaning against the set up in Toronto. You said, what would you think about doing a, what about this podcast? And I remember thinking, oh, I hope he doesn't bring this up again. Really? You really didn't wanna do it. I just didn't know how fantastic it was gonna be. It's the best thing that ever happened. Oh, okay. So you're glad now in hindsight. Oh, I am so glad. Oh, I'm relieved. Okay. Absolutely. Cause you never told me you didn't wanna do it. <Laugh> is it late? We're going in? We're going into 18 years. Yes. Many of my various exes have said, oh, he doesn't ever do anything he doesn't want to do. Yeah. So that's, that's good. Actually. I like that because then I know I'm not imposing on you because no, if you didn't wanna be here, you wouldn't be.
Leo Laporte / Steve Gibson (00:03:50):
So I like, I appreciate that. I am. That's good. It is AB it is truly the best decision that I didn't make you, you made it. And I'm really glad. Well, and I agree. I mean, you're, you're, you're the bold work of of the whole podcast network. So thank you. I appreciate it. Okay. So really, really interesting thing. I noticed on Mac break, you covered some of the oh man security issues that I skipped over. Yeah. Because they were like okay. You know, like zoom fixed their, you know, remote code execution, vulnerability, and the whole Mac security layers bypass has, has been resolved. And there was, so of course this is, this is the first podcast after the big Vegas summer, it's considered hacker summer camp that whole week in Las Vegas with, with Def con and, and besides and all the other stuff, black hat.
Leo Laporte / Steve Gibson (00:04:50):
So yeah. Yeah. Black hat, of course. So but the big news came out of the used Nick's security symposium. I felt we've talked about several stories already. There was another one which ended up replacing what I sort of thought we might talk about, which was Bernstein's suing the NSA O over a freedom of information act because he wants to know where they came up with some of the decisions that they've made. And I said, you know, if something big, bigger than that happened, we would talk about it. Well, a, a group of four researchers at UC San Diego and in Boulder, Colorado two from each university did some watching of the internet and what they found really needs to get our attention. But first we're gonna talk about <laugh> last week's patch Tuesday, which also needs to get our attention to learn how much better Microsoft's various products are as a result.
Leo Laporte / Steve Gibson (00:05:59):
Actually, it didn't turn out to be so bad, but boy was there a lot that happened. We're also gonna look at Facebook's announced intention to creep further carefully, apparently with a lot of caution toward end to end encryption by default in their, you know, built in native messenger app. Also at the puzzling result of a recent scan of the internet for completely exposed VC servers, not something I think we've ever spoken of before. I also wanna take a couple of minutes to talk about the importance and I'm sure you're gonna have fun chiming in Leo, the importance of planning ahead for a domain name's future. Several things have happened in my, off the podcast life that sort of brought this to my attention. And I thought I just should take a minute to talk about that. Also, I wanna share my tip for a terrific website, cloning tool and, and additionally, a few more updates.
Leo Laporte / Steve Gibson (00:07:03):
Then we've got some feedback from our ever attentive listeners, and we're gonna wrap by addressing the question, believe it or not, can a remote servers, TLS private key, which is the thing they guard more than anything else. I mean, how many hours of podcast time have we talked about, you know, the, the issues surrounding protecting the private key warning people, if it leaks out how do, how do we revoke it? How, I mean, just like nothing more important, can a remote service TLS private key be derived simply by monitoring a sufficient number of its connections? What we all know that everything has been designed around that not being possible, but edge cases turn out to be a surprising problem. And the details of this research are quite interesting. Ah, so today's topic is TLS private key leakage. And we do have a fun picture of the week.
Leo Laporte / Steve Gibson (00:08:08):
Somebody sent this who, you know, know some of my gripes about graphing. So I think another great podcast for our listeners. <Laugh> yeah. We've griped about graphs with no origin and all, you know, yeah. Every, every apple event I have to gripe again about those. So good. That'll be fun. I look forward to it. Our show brought to you today by a product I'm happy to talk about all the time BitWarden, which is my favorite password. Manager's the one I use. The one I tell people when they ask me unsolicited I say always use BitWarden. Why? Well, you know, I believe that security software should be open source, so you can examine it, make sure there's not a back door for the NSA, for instance, that kind of thing. But BitWarden is it's open source.
Leo Laporte / Steve Gibson (00:08:56):
It's cross platform means it'll run everywhere. You want it to run windows, Mac, yes. Linux iOS, Android. I haven't found anywhere. I can't install BitWarden. They've got browser plugins, but there's also a standalone app. There's a command line version. If you want that, you can host it yourself with the personal edition or you can have them host it. I like the idea that, you know, if you, if you really wanna be in a trust, no one environment bit, warden's a great solution. It's in fact, the only open source cross platform, password manager that could be used at home at work on the go and is trusted by millions. So I don't, I shouldn't, I don't think have to explain a password manager. You know, it's a, it's a strongly encrypted vault where you keep all your logins, your passwords, not just that.
Leo Laporte / Steve Gibson (00:09:42):
I mean, I keep my PA my driver's license, my passport images, you know, documents, you know, social security numbers that you wanna keep track of, but you don't want anybody else to know. It's a great way to start credentials. And now, of course, not only is it the personal vault, but also they have business products. And that's what I wanted to talk to you a little bit about today. The enterprise and business editions, all BitWarden accounts, enterprise are otherwise begin with a personal vault. And this is what I should say about that because BitWarden's open source and I've talked to them about that. You may remember there have been fewer RS in the past about companies offering trial versions that turned into paid versions and, you know, lost features and so forth BitWarden is an open source product. They have told me their business model does not require them to convert you to a paying customer.
Leo Laporte / Steve Gibson (00:10:27):
There will always be a free personal vault that has all the features that you want. And so you can always use this as a free open source project, but if you're gonna use it in business, there are additional features that you might want. And it all begins with a personal vault. Every employee creates a personal vault, which I kinda like, cuz that means they have password management everywhere, right? They are also adding features, fantastic features all the time. Remember that when Firefox got rid of Firefox send, I moved immediately to BitWarden send, which actually I prefer a fully encrypted method, transmit sensitive information, you know, tax returns, medical documents, that kind of thing binary as well. You will be able to generate unique and secure passwords for every site and the enterprise grade security. And this is important. I know for a lot of businesses is compliant with GDPR CCPA, the California privacy act, HIPAA SOC two.
Leo Laporte / Steve Gibson (00:11:25):
And of course end, end encrypted vault means it mitigates phishing attacks as well because you can't be sent to a site. That's not really the site. And it auto fills. No it won't. You'll say no, but this isn't what you think it is. They've even added more security enterprise capability by adding. And maybe Steve, you could tell me how to pronounce it. S C I M skim support, which yeah, that makes it easier to provision and manage users. It's not something I deal with, but if you're an enterprise you'll like this, they've done something else I think is really cool. And I wanna mention this. Somebody sent me an email saying until you mention it, I've been using BitWarden forever. I didn't know they had this feature recently added a username generator. So of course passwords are the thing, you know, that only, you know, but often people just use their regular email for a login and that's something that's easily guessed.
Leo Laporte / Steve Gibson (00:12:13):
Unlike a password I hope. And it integrates with the three most popular email forwarding services, simple login, a non Addie and Firefox relay. They'll help you with another layer of security. If something, you know, a unique username, you can actually create an email alias. That's the alias you use, it'll go to your email, but it is not something easily guessed. You enter the API key for your individual account. With the chosen service. I mentioned those three select the options you want. And once generated a new alias is instantly registered to your account and automatically forwarded to you. But again, not guessable. So now you're using unique username and email addresses, unique passwords for every account. That is a, that is a very good first defense against online fraud security, privacy, data, breaches, leaks, all of the little things that are getting, you know, getting to us.
Leo Laporte / Steve Gibson (00:13:07):
Now, this is available by the way, on the web vault, the desktop app browser extensions, they are gonna add mobile soon. It's not there yet. Just, you know, let you know. So let me talk a little bit about the business options. As I said, personal vault free forever teams. Although there is a premium version which I pay for just to support them, which is, I think it's 10 bucks a year. The teams organization, that's $3 a month per user additional features let you share data privately and securely with coworkers across departments of the entire company, cuz it knows you a company organization, right? If you're a bigger enterprise, you can use BitWarden's enterprise organization plan. That's five bucks a month per user individuals. Again, the basic free account forever. That's an unlimited number of passwords upgrade any time to the premium account for less than a buck a month.
Leo Laporte / Steve Gibson (00:13:53):
Oh, there's one more plan. The family plan. Then you get for 3 33 a month total up to six users. So that's a really good way to get the premium features for less. If you have a family, look, you know, Steve said it many times, you gotta use a password manager. You just have to, there's no way you can come up with it as many unique passwords as you need. And remember them, <laugh> just not and you probably shouldn't be writing 'em on sticky notes. Putting 'em on the screen. I was watching better call Saul. Everybody seems to have their passwords underneath their desk, blotter <laugh> or under a lamp. No, no password vault and bit word is the only open source cross platform password manager that could be used at home on the go or at work it's trusted by millions of individuals, teams and organizations worldwide free trial of teams or enterprise plan awaits you or just get started for free across all devices as a free personal user BitWarden.com/twit.
Leo Laporte / Steve Gibson (00:14:50):
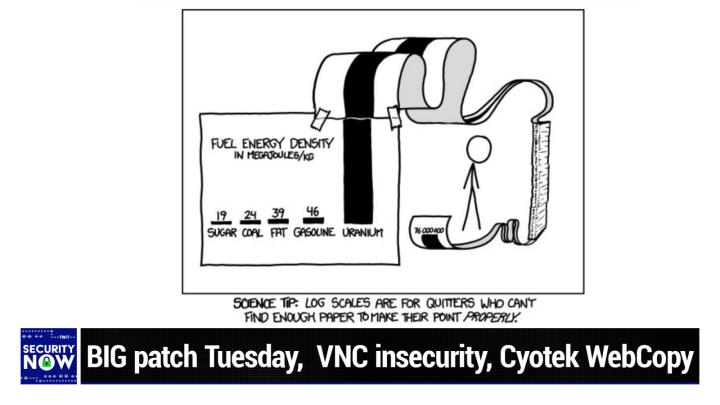
This is the one, this is the one. This is the one you wanna use. I like all the features it's reliable. It works well. I can totally vouch for it. Bit warden.com/twit. We thank him so much for supporting the show and Mr. G and the hard work he does to keep us safe and secure and laughing with our picture of the week. Yes, indeed. So we've often complained. My biggest gripe is when something is trying to show like how big something has gotten or small something has gotten like, you know, the, the, the amount of change and it looks like, oh, like a lot. And then you realize, wait a minute, the scale goes from 111 at the bottom to 112 at the top. Right? And it's like, what? So if you put it on a zero based scale, you couldn't tell the difference between the two bars, which is just it's, you know, it's cheating anyway this, this is just a beautiful piece.
Leo Laporte / Steve Gibson (00:15:51):
And, and is this XKCD sure. X like Randall's work. Yeah. Yeah. I thought that was his style. And you know, one of the things, I think one of the reasons he, his work appeals to techies is that his attention to detail. And this has that. So, so, so this is a chart of energy fuel energy density in mega jewels per kilogram. And it's got five bars cuz he is got five different sources of energy. We've got sugar at 19 is the lowest bar. Then coal at 24 is the second fat at 39 mega jewels per kilogram is the, is in the middle as the third bar. Gasoline is up at 46, but then we hit uranium now properly handled. I might add, yes. I mean you could say the same thing about, you know, hydrogen, but it takes a little to get that power.
Leo Laporte / Steve Gibson (00:16:57):
It does. So uranium has a mega, a, a graft mega jewels per kilogram. Whereas the others are at 19 24 39 and 46. Uranium is 76 million <laugh> yeah. Now, okay. Now we have a problem. If this is a non log rhythmic scale. And so the, the, the, the punchline here, the, the, the title of this is science tip log scales are for quitters <laugh> who cannot find enough paper to make their point to, to make their point properly hysterical. And so what we have is we have a, it looks like, oh, it's probably several miles long strip of paper, which has been scotch taped to the top of the, of the uranium bar, which of course immediately shot off the top of the chart because, you know, you've got a chart that, that shows a modest, a modest size bar for 46 mega jewels per kilogram for gasoline.
Leo Laporte / Steve Gibson (00:18:09):
Well, that chart cannot hold 76 million using a linear scale, but no, this person said, no, I'm not switching two log rhythms. I'm just, I'm gonna stay linear. So what we have is this insanely long piece of ribbon paper, which it goes off into the distance, then it fan folds itself about seven feet down to the floor, comes back off the bottom and the, and the end of it curls up so that we're able to see the top of the bar properly labeling the height of 76 million mega jewels per kilogram for uranium. So, yeah, anyway, another nice little science E picture of the week. And, and it, it put me in mind to the fact that one of the things that I have, and I mentioned on the podcast a couple times, cause I love the app is it's monitoring the SMT, not SMTP.
Leo Laporte / Steve Gibson (00:19:09):
What's the <laugh>, I can't think of the, the acronym for things. Oh SI S MES, M I B S that the, but there's a name for the counters in net networking gear. That's I'm, it's escaping me right now, but it's it's so the, the, the router that I have running PF sense is, is maintaining total bites in and total bites out and also rates for counters. And so the, the app that I've got run running in windows is pulling that and graphing it. And the point is that I've got, I think 300 megabytes or, or 300 megabit down and 30 or 40 megabits up, which is plenty for me, but on a linear scale, it's it it's inconvenient because from time to time, I will pin that 300 megabits. And if I wanna have 300 megabits, be the maximum point of the chart, when not much is going on, it looks like a flat line.
Leo Laporte / Steve Gibson (00:20:14):
The point is that I have it set to an, to a log rhythmic scale, which is one of the options this cool graphing tool has. And, and what that has the effect of is of course, compressing the top so that I get relevant looking graph all the time, regardless of what scale my bandwidth variation is, is running in. So I I'm sure everybody knows log rhythms certainly do have their place, although XKCD had fun without it <laugh>. I think that he was, that was his, his point is use algorithms. He was being sarcastic. Yes, yes, yes. Use a log scale, please. So after last Tuesdays monster Microsoft patch event so far, it appears that nothing new was badly broken, which given how much they did is a little bit of a miracle. It was quite a month in which 121 new patches were delivered.
Leo Laporte / Steve Gibson (00:21:17):
In fact, so many things received updates that it's unclear whether there was anything that didn't there were identified CVEs in windows and windows, various components, Azure batch node agent, real time operating systems, site recovery, and sphere, Microsoft dynamics, edge browser exchange server office, and its many components P PTP SSTP remote access service P P TP hyper V system center, operations manager IIS. And of course the bridge Pooler didn't escape being fixed some more and we've got Microsoft windows defender, credential guard. And on top of all of that, there was an additional 17 CVEs which patched edge plus another three patches for secure boot. So that brought the month's total CVE patched count to 141. And if you were thinking that that seems like a lot. Yes. It's nearly triple the size of last year's August release. Talk about year over year inflation and it's the second largest release of 2022.
Leo Laporte / Steve Gibson (00:22:33):
So this has been a big month of those 121. New CVEs 17 are critical, 102 were marked as important. One was only moderate and there was the last one was in was, there was one last one that was low in severity. Two of the bugs are publicly known with one of those affectionately known as dog walk is, or at least was actually, it will be until everybody gets themselves patched under active attack. At the time of the release. Not long ago, we were talking about the trouble with Microsoft's custom protocol handlers and how they could be readily abused this particularly critical zero day remote code execution. Vulnerability is another one of those. And as before Microsoft was responsibly informed of this problem and declared that it was not a security problem. <Laugh> yeah. Oh, were they wrong? <Laugh> oh my God. You, you know, and I, I suppose it wasn't until it was yeah.
Leo Laporte / Steve Gibson (00:23:49):
Since, since now it is. Yeah. And it's being exploited in the wild to damage Microsoft's users, for which, as we know, they take no responsibility because we all give that up when we start using any their stuff that's fault. It's your fault. That's right. Yeah. That's right. So the trouble is known as dog walk because it's another path traversal flaw, thus, you know, walking the directory hierarchy when a targeted victim opens a especially crafted dot D cab. So it's a file ending in dot D I a G C a B archive, which contains a diagnostics configuration file. It allows an attacker to save their malicious executable file into the, I have a hard time even saying this into the user's windows startup folder, which you know, is really not where you want attackers malicious executable files to be stored on your computer. At least it's easy to find.
Leo Laporte / Steve Gibson (00:24:57):
I mean, they're not hiding it <laugh> so, so of course, the next time, this hapless victim logs into the system, after a restart, that file will dutifully be automatically run by windows, right? And this vulnerability affects all windows versions, starting from seven on and from server 2008 and on, so, okay. Get this. The problem was originally, as I said, responsibly reported to Microsoft on December 22nd. <Laugh> 2019 by security researcher, Emery rad, even though a case was opened by Microsoft the next day, acknowledging the receipt of his report. Six months later, Microsoft declined to fix the issue they told rad that to make use of the attack. An attacker would need to create what amounts to a virus O okay. Convince a user to download the virus. Yeah. And then run it. Oh yeah. Gee like maybe some malware. So Microsoft said this wouldn't, I'm quoting this.
Leo Laporte / Steve Gibson (00:26:18):
Wouldn't be considered a vulnerability. Okay. <laugh> they said no security boundaries are being bypassed, meaning, well, we, we Des we designed it to work this way. It's supposed to be doing this. Right. It did it didn't bypass anything it's working the way it's supposed to. Yeah. and they said the proof of, of concept doesn't escalate permissions in any way. Okay. I guess it didn't need to, but it would be bad if it did, but it doesn't, or they said, do anything the user couldn't do already because you know, users are perfect and they never clicked something that they shouldn't. So what's the problem, right. Microsoft had said to rad. So apparently because the proof by their logic, because the proof of concept was only a proof of concept and not, and not an explicitly and massively destructive bug. And since in, in a sense, it was by design.
Leo Laporte / Steve Gibson (00:27:26):
Microsoft said not a problem. In fact, they wrote quote, there are a number of file types that can execute code in such a way, but aren't technically executables. What, and a number of these are considered unsafe for users to download slash receive in email, even from there dot dag cab. Okay. In other words, again, this is what we told you it was gonna do. And they said even dag cab is blocked by default in outlook, on the web and other places. Wow. So, you know, okay. So much for layered security and defense in depth, they're saying, well, outlook blocks it. So what's the problem. Okay. Back then, <laugh> I know Microsoft essentially said that yes, these sorts of files are indeed unsafe for users to download and receive, and they should not do that, but don't worry. Our email client outlook, which as an aside, has recently been crashing so badly for many users that it has been unusable, but that's a different story that we'll get to in a minute.
Leo Laporte / Steve Gibson (00:28:50):
They said our email client outlook blocks these by default to <laugh> consequently, despite Microsoft's assurances two and a half years ago today we have CVE 20, 22, 34, 7 13 identified as a critical zero day remote code execution, vulnerability. And this is exactly what that is, which they said, oh, no, this is what we wanted. Okay, okay. Since that was finally fixed this month, this, you know, two LA LA last week with August's patches, it would appear that Microsoft's position on allowing attackers to execute their code uninvited on a victim's windows machine has since changed and not a moment too soon, though, about two and a half years too late. And of course, many people were hurt. In the meantime, this leverages this CVE windows support diagnostic tool, S D T, and it's not the first time an MSD T bug has been exploited in the wild. Just this year.
Leo Laporte / Steve Gibson (00:30:09):
We previously talked about this. This bug allows remote execution when Ms. D T is called using the URL protocol from a calling application, typically from Microsoft word. So perhaps Microsoft missed that other way to invoke this very dangerous diagnostic feature. Wasn't just outlook word could do it too. Well. Now there isn't even worse. This is exactly the kind of thing, those evil you know, call center guys do, they would say yes. Oh, you know, we see you have problem on machine, please launch diagnostic tool. Yeah, that seems sensible. Doesn't it? <Laugh> geez. What could possibly go wrong? What could possibly go wrong? They're trying to help me. Yeah. So it's exactly, as you're saying, there's an element Leo of social engineering to this, you know, because a threat actor would need to convince a user to click a link or open a document.
Leo Laporte / Steve Gibson (00:31:09):
Yeah. But how harmful could the Microsoft diagnostic tool be? Yeah, that means we have nothing to worry about. Nice. Because all users are smart and they would never click on a link or open a document that they weren't supposed to, you know, even if their mother sent it to them or because their mother sent it to them anyway. Okay. Recall that. We were also just talking about files, downloaded from the internet being tagged with what I love this the O T w the mark of the web, the idea being that this would cause windows to refuse to proceed, or to at least issue a popup warning. Well, we wouldn't not want that to confuse people using Microsoft's support diagnostic tool, which fields, these dot diag cab files. So it was designed not to check for the mark of the web so that its files can be opened without any warning. Zero patches founder told the hacker news that outlook is not the only delivery vehicle such files are cheerfully downloaded by all major browsers, including Microsoft edge by simply visiting a website. And it only takes a single click or missed click in the browser's downloads list to have it opened. No warning is shown in the process in contrast to downloading and opening any other known file capable of executing an attacker's code.
Leo Laporte / Steve Gibson (00:32:47):
Wow. That was fixed. Finally, the infamous SMB server messages block protocol is back with another remote code execution, vulnerability. This one's a server side bug, which allows a remote unauthenticated attacker to execute code with elevated privileges on effective F SMB servers. Well, that's not good. There is some good news is only windows 11 is affected. Oh, great. So only that's what only the, oh, oh, I, I had here in my notes, only the five people using windows 11 six. Now that would be six. We will be at risk. But seriously, although we don't have any details about this one, it does suggest that some new functionality added for windows 11 also introduced a new vulnerability. You know, if code keeps changing, it is never going to be secure. The concern about this one, since it affects windows 11 systems that are publicly exposing their SMB service is that it would potentially be wearable.
Leo Laporte / Steve Gibson (00:34:06):
So disabling SMB version three compression is a workaround, but why do that just apply the update from this month in order to, you know, squash this bug and this again, reinforces my admonition against ever publicly exposing any windows service that does not need to be offering its services to anonymous public users, which as I've said before, pretty much limits us to web and email. Those need to be public and anonymously available. Pretty much nothing else does SMB, as we know, has always been a catastrophe. It's the reason I created shields up when windows was first put on the internet, which was sharing everyone's sea drive to the world and they just broke it again with windows.
Leo Laporte / Steve Gibson (00:35:01):
Okay. Then we have three CVEs for exchange server because it has multiple elevation of privilege vulnerabilities. And it's a bit unusual for elevation of privilege, you know, E O P bugs to receive a critical rating. But these qualify, these three bugs could allow one authenticated attacker. He be an authenticated user who was in attack mode to take over the mailboxes of all exchange users on a server. This attacker could then read and send emails or download attachments from any mailbox on the exchange server. Administrators must also enable extended protection to fully address these three vulnerabilities, but you know, another mess, Microsoft has also been having constant problems with their network file system, you know, NFS code and we have another remote code execution vulnerability fix this month, making it the fourth month in a row that NFS has received a patch to close a code execution vulnerability.
Leo Laporte / Steve Gibson (00:36:17):
This one has a CVSs of 9.8. So it could be among, I would argue the most severe of the month's patches. Fortunately, there is not a huge population of people, windows users with NFS exposed to exploit this, a remote attacker would need to make a especially crafted call to a vulnerable network file system server. But this would grant the attacker elevated code execution privilege. And oddly enough, despite its CVSs of 9.8, Microsoft has this one categorized as only one of those hundred and two important in severity problems. But of course, anyone using NFS should take this very seriously, cuz your system can be scanned for and found on the net. And speaking of outlook, Leo, you're gonna love this one. This is CVE 20 22 35, 7 42, which addresses that annoying Microsoft outlook, technically denial of service is what you would call it. Vulnerability, which I mentioned earlier, if an outlook user were to receive a specially crafted email and a great many did recently their outlook executable would immediately crash and it could not be restarted upon an attempt to restart it.
Leo Laporte / Steve Gibson (00:37:47):
It would immediately terminate again, once it retrieved and attempted to process that invalid message, oh, what a mess. And every time you tried to start it, absolutely it would just crash. Yes. it's not even necessary for the targeted victim to open the message or to use the reading pain, just its presence in the inbox keeps outlook from starting. The only way to restore Outlook's operability is to access the email account, using some other email client, perhaps webmail to remove the offending emails from the mailbox before then finally restarting outlook. But don't worry as Microsoft explained, outlook is your first line of defense against executing any of those malicious diagnostic tool, extension files. So you should feel completely safe. And I know, yes, I'm being tough on Microsoft, but there's a large and growing that they're generally losing control of this beast that they've created.
Leo Laporte / Steve Gibson (00:38:59):
I, I love windows. So I sincerely hope it's just a phase they're going through as a result of what was in retrospect, just a phase. You know, it's just a phase, turned out to be a poor decision to outsource windows, quality control to their early adopter consumers. Most of those people just wanna screw around with Microsoft's latest crap. They're not actually interested in controlling anyone's quality and we've noted how in the past, at least Microsoft often ignores those outside please, to repair problems that have been identified in this process. They're just pesky. You know, they don't work for Microsoft to buzz off. So this new scheme is clearly not working. And again, let's just hope. It's a phase last week, Paul and Mary Jo were observing that there are growing indications that consumers are not making Microsoft any money. So Microsoft appears to be more or less abandoning the consumer for the enterprise. Now speaking as a consumer, that would be fantastic. <Laugh> please leave us alone. Ignore. Ignore us. Microsoft. Just leave us with windows 10 forever. Like you originally promised just patch its flaws and don't change anything else. It's fine for us now. The way it is, don't break it please. And meanwhile, add all the new features you want to the enterprise. Really just give that your entire focus and all of the rest of us, lowly consumers will just quietly be getting stuff done. It sounds like a great plan.
Leo Laporte / Steve Gibson (00:40:56):
Okay. Leo, I have to have a sip of water after that. <Laugh> okay. Take a breath. <Laugh> relax. It's gonna be okay. Of course. I came in my windows said something went wrong. You better reboot. So windows, what, what was that? Windows 11. 11. It got, oh yeah, yeah. 11. You know, you know, I have to use 11 for the same reason you have to use windows. It's yeah. It's what everybody's using. Yeah. Our show today brought to you by NewRelic. I know a lot of devs and a lot of you are devs and of course developers are the most curious people. They're brilliant people, right? The first to you know, get on the new Gidget gadget, bandwagon, digging into documentation. Even they read it. Yes. Not only wanting to know how things work, but why Steve's a perfect prototypical developer type.
Leo Laporte / Steve Gibson (00:41:54):
That's why so many engineers turn to NewRelic because NewRelic is a way to know what's going on in your software life cycle. It gives you data about what you build shows. What's really happening. It's a single place to see the data from your entire stack. So you don't have to look into 16 different tools and, you know, connect point a to point B manually NewRelic does it all for you with a single pane of glass. They pinpoint issues down to the line of code. So if you know, something went wrong, you know exactly what it is and where to fix it. You go jump to that line and fix it. It's just a, it's a solution that gives it's suddenly like you can see like you, somebody cleaned your glasses and you could see what's going on in the entire stack, including the cloud and servers endpoints everywhere your software is running.
Leo Laporte / Steve Gibson (00:42:44):
That's why devs and op teams at door dash use NewRelic. Github uses it. Epic games uses it. I mean, imagine if you're epic games, all the servers and stuff. You've got clients all over the place, all sorts of stuff going on. It's great to know what's happening. Where, and when more than 14,000 companies rely on NewRelic to debug and improve their software. And when teams come together around data, it allows you to triage problems, be confident in decisions and reduce the time needed to implement resolutions. Using data facts, not opinions. Use the data platform made for the curious people like you get access. And I love this to the whole NewRelic stack all, all the apps and a hundred gigabytes of data per month free forever. You don't even give 'em a credit card free forever. The entire NewRelic platform in a hundred gigs of data a month, you could sign up right now, new relic.com/security.
Leo Laporte / Steve Gibson (00:43:44):
Now E w R E L IC just do it. New relic.com/security. Now new relic.com/security. Now maybe Microsoft should give it a shot. <Laugh> alright Steve, when we go so face yeah. Facebook is cautiously creeping toward default end to end encryption in a movie kind, cuz they have to, you know yes. At this point, yes. In a move that should of turn up the heat on the question of whether consumers have the fundamental right to have their interpersonal communications end to end encrypted, you know, making them truly an irreversibly, private Facebook's Sarah Sue. Their there's actually a position called the director of trust for Facebook's messenger app posted last Thursday. She said this week, we'll begin testing default end to end encrypted chats between some people. If you're in the test group, some of your most frequent chats may be automatically end to end encrypted, which means you won't have to opt in to the feature.
Leo Laporte / Steve Gibson (00:44:58):
You'll still have access to your message history, but any new messages or calls with that person will be end to end encrypted. You can still report messages to us. If you think they violate our policies and we'll review them and take action as necessary as we know, this is a big deal that, that the keyword is default, right? You know, I call it the tyranny of the default. Even though WhatsApp, you know, based upon the beautiful signal protocol offers nothing other than end to end encryption Facebook's native messenger app, which offers end to end encryption as an option has never had that enabled by default. And even now they're moving toward that cautiously. They're saying that the move is unrelated to the recent outrage and backlash from privacy advocates after Facebook complied with an order to reveal the content of private messages between a mother and her daughter, the order came from a Nebraska police department as part of their investigation into an abortion related case.
Leo Laporte / Steve Gibson (00:46:06):
Of course, in the wake of the us Supreme court's reversal of its previous decision made under different justices in Roe versus Wade. So, okay, fine. Whatever, despite Facebook's denial, the timing of this move is at least suggestive, but it's a welcome move, nonetheless. And since most Facebook users just use, Facebook's built in native messenger app, much as mom and daughter did. In that instance, you know, if encrypted by default is eventually true, it will go a long way toward protecting the privacy of many more of Facebook's 3 billion users. And from Facebook's point of view, they would, you know, regardless of the politics, they would like to be able to say, we don't have access to that information. So, yes, sorry that, that can't, that's what apple, that, that, that's what apple has said over and over and over. Right, right. And it upsets our law enforcement personnel, but you know, really the question comes down to, I think, how, where, how is the greater good served is the greater good served by truly honoring privacy that you are, that you are presumably providing.
Leo Laporte / Steve Gibson (00:47:22):
And yes, some small minority of people will abuse that small, you know, there will be criminal use of the abuse of that privacy or are you actually not gonna give privacy to everyone and open thus everyone open, you know open everyone to the potential of abuse by, you know, not open non-criminals to the potential of abuse, you know, by you know, suppressive governments and so forth. So anyway, as I've said, often, I think this question of, of how we actually deal with this, the technology will do anything we want. The question is what do we want? And, and where is the greater good served the security firm? CBLE C Y B L E CBLE recently scanned the internet for instances of and it's just hard to imagine this completely open VNC servers lacking any password protection, a any authentication of any kind you connect to them.
Leo Laporte / Steve Gibson (00:48:31):
And you're looking at a desktop with mouse and keyboard access. They found more than 9,000 of those, which they were able to freely log into. And as I'll get to in a moment, these were not all safe to leave open. Okay. So first of all, for those who don't know, VNC stands for virtual network computing, it's a very old open platform, independent and very popular remote console access system, which implements a protocol called RFB, which is remote frame buffer. So one runs a VNC server on some machine, typically any random desktop operating system. And this server allows a remote networked user with a matching client to view the machine's console and use its keyboard and mouse remotely. It's, you know, it's essentially windows RDP, you know, remote desktop protocol, but it's, non-pro proprietary. It's not Microsoft's. So this firm Kial scanned and found more than 9,000 machines openly exposing their access without any form of authentication.
Leo Laporte / Steve Gibson (00:49:47):
So this begs the question why, how well, like what, what could the possible reason being, how is it possible? Is it the result of negligence or error or maybe a misguided deliberate decision for convenience? Most of the exposed instances are located in China and Sweden. Those are the top two by far, but the United States, Spain and Brazil were also well represented. Kial identified 1,555 passwordless instances in China, 1,506 in Sweden with the us coming in third at 835 followed by Spain at 555 and Brazil with 529. And as if having, you know, just having consoles exposed was not bad enough. They found that some of these exposed V and C instances, which obviously making accessible industrial control systems, they wrote during the course of the investigation, researchers were able to narrow down multiple human machine interface, HMI systems, supervisory control, and data acquisition systems, you know, SCADA, workstations, et cetera, connected via VC and exposed publicly over the internet.
Leo Laporte / Steve Gibson (00:51:15):
In one of the explored cases, the exposed VNC access led to one of these human machine interface and HMI for controlling pumps on a remote SCADA system in an unnamed manufacturing plant. So anybody could like literally go there, bring up this control panel and start turning things on and off. And like, maybe it's just a spoof. I mean, it occurs to me that could be a honey pot, right? To see if someone does that. Being curious to see how often attackers are targeting VNC servers, C used its tools to monitor for attacks over port 5,900, which is VC's default server port. They found that there were over 6 million connection attempts in a month. Most attempts, I mean, think of 6 million attempts in a month. I don't know how many IPS they were monitoring, but wow, most attempts to access VNC servers. They were able to, to determine that originated from the Netherlands Russia and the United States.
Leo Laporte / Steve Gibson (00:52:36):
So nothing to be proud of here in the us, unless, you know, it could be security services, benignly scanning, but you don't do that 6 million times. It's worth noting that this was just a scan for VNC servers requiring no authentication C's report noted that if they had raised the bar just a bit by including VNC servers, using weak and easily cracked passwords, you know, like password or probably monkey the number of exposures would've skyrocketed. And to that end, sadly, many VNC products are old and not super securable at best many, for example, offer only passwords of up to eight characters. That's no longer enough when you're able to conduct a brute force attack on something that looks juicy. Like I said, much of this stuff is old, so they are inherently insecure. And so once again, we face the rule of the internet that really needs to take hold.
Leo Laporte / Steve Gibson (00:53:41):
The only servers that should ever be made publicly accessible are those that have to be accessed anonymously by the public. Everything else should be behind a VPN SSH login or an overlay network like tail scale. I, we have to do it. I wonder if my, my, my favorite VNC is is one of the affected ones, chicken of the VNC. Have you heard of that one? <Laugh> chicken of the VNC. I, I, I do not. That's great. That's it was windows VNS. I had, I don't use VNC anymore, but no, I actually when I was two, couple years ago, when I was getting my world set up to do spin right. Debugging, I, I was looking for like the best way to, to do remote debugging. And so I was looking to see if there was any, like text based VC that I could, that I could use.
Leo Laporte / Steve Gibson (00:54:37):
Oh, that would be cool because yeah. And so I, so I dusted off VNC and took a look at it and, and looked at various ways of, of using it. And I ended up not finding anything that was better than just good old windows networking, but anyway, well, and our AP has had its problems too. It's not like it's oh, it's it's failed for either. No. And, and, and, but in the case of VNC, one of the problems is its age. But of course, it's, you know, the fact that you even know of chicken of the VNC demonstrates, you know, it's been around forever <laugh> oh yeah. Oh yeah. It's I didn't make that up kids <laugh> in my day. That's what we used chicken of the VNC. It was, and it was really good. And it's mercury content was low, very low, very low.
Leo Laporte / Steve Gibson (00:55:21):
So it was line cut line cut. Okay. So for the third time, in the last year, a neighbor who had heard that, I knew my way around computers stopped Lori and me during our nightly walk. Oh Lord. To ask what she should do about her website, the common denominator in all three instances, which is why I'm benching this today is that these people were not web masters, nor were they people who were content with having Facebook host their pages. They were professionals who wanted to have their own website located at their own domain. So they got a referral from someone else, or perhaps noticed at the bottom of someone's website, a mention that the site was created by, you know, websites or us or Johnny's websites or whatever one way or the other, they found a service. And they used that third party service.
Leo Laporte / Steve Gibson (00:56:28):
You know, typically it's a one man shop, right? A, a, a DBA firm to function as an intermediary between the different things. They needed a domain name, registrar and a hosting provider to register their domain name of their choice, create a website and populate it with their content. These relationships are almost always problematic because a, a great deal of time can be spent getting everything set up. Then of course, the website's owner invariably wants to make changes, which are met with grumbling of various degrees, by the webmaster who just wants his client to shut up and, you know, pay to maintain the site as is without actually doing any further maintenance. You know, the, the, since the people who own the content and are having it put, there are typically unable to manage the site themselves. It's a constant problem. So every listener here is now thinking to themselves, okay, Gibson, we all know this.
Leo Laporte / Steve Gibson (00:57:27):
What's the point. The point is what I have seen over and over is that these relationships do not age well over the long term, or are at risk of not. And in these cases have not. The reason is the domain name without exception, none of these regular nice people who have their own website under domain name that they originally chose having had it for years and having invested emotionally, intellectually, and Sally have any actual control over what they consider to be their domain name in every case, their domain name was registered by someone else for them. Yeah. In the beginning, I talk about this on the radio show a lot. Yep. I'm not surprised Leo. It's got to be a, a problem that is beginning to happen more and more because domain names are becoming, you know, they're beginning to age. So at a time when none of that accumulated value existed in the name, this was all created.
Leo Laporte / Steve Gibson (00:58:42):
And without an understanding of the way domain name property is managed, they never stopped to wonder what would happen in the future. Whoever it was, who set all this up for them, had an account with a registrar. And it was, you know, under their account that their domain name was, and probably still is registered. This all came to mind recently when I was explaining this to the most recent neighbor who stopped me you know that, and what I explained was that where their domain names were concerned, the rule is not, the possession is nine tens of the law with domain names. Possession is 100% of the law. It's the O it's the only law. The only thing, if you had a copy, if it was a trademark, you might be able to, you know, rest it back. You could appeal, you know, if it's your trademark and somebody else has the domain name that's happened in the past.
Leo Laporte / Steve Gibson (00:59:47):
True. Although at a great deal of expense and attorneys and court cases and everything. Right. Right. Well, no, I, I think I think I can has an appeal process. It's not as comp, not as bad as all that. Oh. So you don't have to actually Sue you go to, I can the, the, the right and, and, and get it right. You could say that I can't, Hey, you know, I'm McDonald's and this guy is not <laugh>. Can I have my name back? Yeah. Right. So, and, and this sort of puts me in mind we've talked about the, the problem of, of somebody, you know, dying with a whole bunch of passwords, which are not known to anyone else. The time before this most recent time the longtime webmaster of a different neighbor actually had died rather suddenly being survived by his wife, eventually the web and email services, which continued for some time were terminated.
Leo Laporte / Steve Gibson (01:00:36):
And my neighbor went in search of a solution. The man's wife was nice, but she knew nothing about technology. And my neighbor learned that all of his other clients were also furious in fuming. Mm-Hmm <affirmative> that their web domains collectively had all been allowed to expire. Oh, had then been snatched up and were now hosting click bait pages. Oh God. So I had to give that neighbor, the bad news that she really had no practical recourse. And in this most recent case, the webmaster is an 80 year old geriatric good friend of the website owner working through him. She explained, she's created an extensive website, filled with links and artwork plays and songs. It is a content rich labor of love, and she's been frantic that something might happen to it. So I told her that I could easily relieve some of her worry by cloning her entire website into a directory.
Leo Laporte / Steve Gibson (01:01:41):
So that at least it's all of its content would be archived for safe keeping. And so the next morning I did that and she was hugely relieved, but I explained the situation to her about the control of domain names and that if anything, should ever happen to this person in the absence of some sort of plan, she stood to lose any and all use of that domain because of the way it was registered. She had no claim to it whatsoever. It, it actually is not hers. It's his. And I said, so anyway, so I did a little bit of who is poking around, and I discovered that he's using a service called Enam E N om, which is for domain name resellers. Enam turns out is a branch of hover, my own chosen registrar with who I am very happy. So I told her that the best thing she could do would be to create her own account at hover, then arrange with her friend to transfer the domain with all of its existing settings intact from his hover account to hers.
Leo Laporte / Steve Gibson (01:02:54):
She said it would be a bit dicey because he was a friend and she didn't wish to offend him. So I told her, okay, in the first place, he will at least understand that it is an entirely valid concern for anyone to have. So if transferring the domain to her now is not an option, could he at least explain what he has in place for dealing with his own potential inability for whatever reason to continue. And so, as a consequence of all of this, I just wanted to take a moment to mention this to everyone who's listing. Because even though we all probably manage our own domain properties, it must be that we're all aware of others who are in a similar place, and it might be worth asking them about the plans their domain name providers have for their domain names upon any event that might cause their registrations to expire and be lost.
Leo Laporte / Steve Gibson (01:03:59):
And of course the strong advice is if you're gonna have a domain name, register it yourself, don't let some third party register it for you, cuz you're not controlling it. You don't control it. Yes. And, and I was impressed. I looked at the registration and he had renewed it two days after it, 2, 2, 2 days after one month before expiration. So that is to say it was probably set up for autorenew. Yeah, it was, it was renewing annually, you know? So like it, it was, it looked like he was tending it well, but, and of course the, the flip side is if you are registering your own domain, then you do have that responsibility. You need to absolutely make sure that it is, you know, you've that it's set to auto renew, that, that you're maintaining a, a current email address for them. So they're able to notify you any problems that you're, that they've got a credit card that they're able to charge.
Leo Laporte / Steve Gibson (01:04:55):
I mean, so the, so the point is, if you're gonna take on that responsibility, you know, there is some responsibility that comes with it, but boy you know, it's, I'm glad to hear that. You're saying you're seeing the same thing among your, your callers on the weekend. I say it all the time and she should approach. I mean, if this guy's a friend this 80 year old, guy's a friend just say, can I transfer it over to me? Cuz it's mine. Yeah, <laugh> right. You know, he did it probably as a favor to her cuz he knew how, because the reason people don't wanna do this is they don't know how to set up the DNS to point to their website. And you know, I understand this is a little techy. Yeah. So I understand why they don't do it, but yeah, you, it, you need control.
Leo Laporte / Steve Gibson (01:05:35):
You need to control it. Especially if it's a business and you know, it made me think Leo that shouldn't there maybe be an, a provision added to domain name registrations where they, where they actually have something like a next of kin, right? Like that is like part of the registration. So that, so that, for example, in this instance he could, he, he could put her, designate her as do yes. Pre designate her, right as this domains next of kin or say, I'm registering this as a third party in the domain really belongs to this. There should be a way to do that. One of our chatters PC guy, 80 88, who does this for a living, he says, whenever I create a domain for an account. I create a separate account for the domain and their information is registered in the person's name. That's their credit card number.
Leo Laporte / Steve Gibson (01:06:29):
This is that's a responsible webmaster, you know, that's the right way to do it. Yep. And I have not yet run across anyone who does. So anyway, just be, because this actually happened, I thought, you know, let me just take a minute to just remind our listeners that I'm sure they, they don't have some third party managing theirs if they do, you know, get it. But boy, I bet they know people who do and the, these problems keep cropping up when something happens. Yep. And, and, and mostly, I think what people are surprised by, you know, both of the people who approached me, my, my, my neighbors were shocked that there really was no recourse. I mean, no practical recourse for some non trademarked random domain name. I mean, it, it, they don't have any rights. It is the rights of the account holder.
Leo Laporte / Steve Gibson (01:07:24):
Yep. So, okay. And speaking of making a web copy, I, I fired up my favorite cloning tool. It came up and it said, Hey, I got an update for you. I thought, oh, that's nice. I went there and I was reminded that it was do, it was free and donation wear. And I gave 'em 10 bucks. Oh. Because there's a long line of, of maintenance that that's been done over time. They are keeping it current they're they're, they're giving it new features. Anyway, this thing, I just wanted to give them a shout out. It's CIO, C Y O T E K web copy, CIO, web copy. And, and I'm using it cuz it is just so good. You, you, you, you, you, you point it to the root of a, of a website. You, you point it to a directory that, that either exists or doesn't and you say, make me a copy and this thing just go, it does all of the, you know, all the link following and, and it, it, it, it changes all the links so that you end up with a locally browsable copy of the site.
Leo Laporte / Steve Gibson (01:08:31):
And, you know, these days with drives big, as large as they are. I, I, I, you know, I've, I've, there's been discussions of this in GRCs news groups about, about people just cloning sites, because they don't want to ever lose some of the content of a site that they really care about. And yeah, the web archive kind of has it, but it sometimes doesn't have all of the assets that you wish it did. So anyway, CIO web copy is the thing that I've been using and, and really happy with it. There was a quote that I saw that I just had to share with everybody. I, I ran across it cuz Ryan Levy who's one of the security guys at Google. He retweeted a tweet from a Jen's APO Jen's APO was quoting at CRA. So boy, a three letter Twitter handle that's rare whose self description on Twitter says building a better world through open collaboration.
Leo Laporte / Steve Gibson (01:09:31):
So when Jen's quoted at CRA, he added to his retweet, I don't think I've ever seen anything more true posted. So here's the original quote of the open collaboration guy via Jen's APOs retweet and Ryan sleeve's retweet retweet. They said running a successful open source project is just Goodwill hunting in reverse, where you start out as a respected genius and end up being a janitor who gets into fights. <Laugh> I love it and think about it. It is exactly right. You know, you know, running a successful open source project is just Goodwill hunting in reverse. You start out as a respected genius and you end up being a janitor who gets into fights because that's what these things, you know, it is a thankless task and, you know, you end up exactly as these guys said, just having to like defend every decision you ever made and arguing back and forth about features or not features and, and so forth.
Leo Laporte / Steve Gibson (01:10:43):
And anyway, just a great quote. So thank you, Ryan, for bringing it to my attention via Jens. Oh, and Leo. Yes. Progress from ed Cano, the father of the sand, Sarah, which is that thing you and I both invested in years ago. Oh, wait a minute. <Laugh> this was the, like the the, the garden, the Zen garden thing. Yes. It's the Zen garden thing. It, it, it's a beautiful wooden round table filled sort of a, a, a, a, a, a, well, Zen garden is a great description round filled with very fine sand and a ball bearing is rolling around in the sand, leaving its wake behind it all controlled by a very clever two stepper motor mechanism that allows this ball to be moved in really cool geometric patterns ed just sent. Hi everyone. Recently I posted a comment stating that the Sam Sarah app was available in the app store.
Leo Laporte / Steve Gibson (01:11:54):
We had to make further improvements for the Android users. So it took us more time, but now it is also available in the Google play store. You can follow the links below to download the app. And for anyone who's curious and Leo, you might be I've got both of the links to the San Sarah apps in the show notes. He said, the app will help you personalize your San Sarah by selecting the patterns that you'd like the most adding more designs or changing the colors of the lights. Even when we are happy with our current development, we're working on more features for the app. So please send us any feedback so we can improve our current version. And here's the news regarding shipping and manufacturing. The container with 300 sand, Sarah has been cleared exclamation point. Oh, so it's stuck in shipping. I get and custom.
Leo Laporte / Steve Gibson (01:12:46):
Yes. Yeah. It turns out for some reason, getting black sand through customs is a huge problem. Wow. Huh. Interesting. he said we're, we're only a few days away from the first orders to re the first orders, meaning you and me Leo to, and I know many of our, many of our listeners got on board also because ed and I had a conversation afterward, he listened to security now. And so he was first of all, surprised when I had discovered it and heard me talking about it. And then they got a bunch of, you know, a, a bunch of backers as a consequence of the podcast, anywhere he, he, he said the first order is to receive their units for those backers, you'll receive your tracking numbers by the end of the week. And it will take another week to receive your Samsara by your door.
Leo Laporte / Steve Gibson (01:13:33):
After clearance. The container is on its way to the us warehouse, where our partner will split everything up in orders and start the individual fulfillment. And he said for the rest of the orders, we mentioned that all orders would be completed by late August and we are on track to accomplish. So we, he said, we expect to complete all processes in around one week, depending on the courier, your package might take two to three weeks. Once we start shipping, please be wary of any messages this week because you might receive your tracking number and blah, blah, blah. So anyway, his communication has been great through these years. And as I mentioned, last time, I talked about him. He is clearly a perfectionist that the, it has been, obviously it took far longer than he expected. All kinds of problems came up, but he never quit.
Leo Laporte / Steve Gibson (01:14:20):
And I, based on everything I've seen, we are gonna be really happy with this thing when it finally arrives. And it looks like it may, I don't know if I ordered it. I think maybe you still can. I hope I didn't. Cause I don't know where the hell I'm gonna put it. <Laugh> <laugh> we have cats. Well, you have CA you have cats. Cats might see this as an alternative bathroom. Yeah. Yeah. They well now you are able to get a glass lid for it so it can be closed, although it could still be toppled over. So yeah. Yeah. Cat cats might be a problem. This might be for maybe for work. I'll have it. Yeah. Anyway, a couple bits. Oh, that'd be good. Yeah. Yeah. A couple bits of closing the loop feedback Alex T said, hi, Steve, thanks for another, the great show.
Leo Laporte / Steve Gibson (01:15:04):
I think the way airplanes restrict images, he's referring to the, the comment last week about how could the free wifi allow text messaging, but not images. And he said, I think the way airplanes restrict images in messaging clients is even simpler than that. That is to say simpler than a bandwidth cap. That's very low. He said, I believe WhatsApp and others send image blobs to a separate endpoint for storage and insert a reference to that blob into the message. A firewall block to the media storage endpoint would do the trick. And of course, given though that's true, Alex is completely correct Thomas a pale neck. I hope that's how I pronounce his name. He said, oh, he said, copy as path in windows 11. And Leo, you're able to check this out. He said, hi, Steve. I use shift, right click and then copy as path all the time since you showed us that a few years ago.
Leo Laporte / Steve Gibson (01:16:08):
So thank you for that. I don't know how much you've played with windows 11 safe to say as little as possible. He said, copy as path has finally been moved to the standard right. Click context menu. Oh, so good. In fact, I see, let me see. Let's see. No shift required anymore. Yep. Yep. It's so org hit control shift C without even a context menu and it'll get it. Control shift C is the copy is path, which is great for pasting a, a terminal or whatever. That is nice code. Yes. Yeah. Yes. Thank you. Also Brad Cochran, he said, Hey Steve, longtime Lister. First time caller. He said, I even dusted off my Twitter account to message you. Aw. <Laugh> he said regarding your most recent security now episode, it sounds like you haven't come across attack surface management. Apparently that's an acronym ASM.
Leo Laporte / Steve Gibson (01:17:04):
He said, I wanted to share a bit of info about how it works. Now he's referring to my talking last week about Microsoft's new. Apparently it was a scanning service, which they're making available to enterprise in order to, to check their, their tax service. He, that I wanted to share a bit of info about how it works full disclosure. I work for Palo Alto networks and sell a competing solution called cortex expanse. But because of that, I could explain at a high level how ASM works you're right in your assumption that this is an external scan, essentially ASM tools, scan, meaning attack, surface management tools scan the global public internet on a daily basis, which is possible now due to advances in computing resources, meaning lots of cloud and bandwidth. He says for open ports and protocols, you mentioned Showdan in the show and that's similar one important note here due to the computer fraud and abuse act, you know, the CFAA and similar laws in other countries.
Leo Laporte / Steve Gibson (01:18:12):
These do not tend to be invasive port scans, such as Nmap. He says, which would violate the law. If you ran on a network, you don't control without approval. And I'll mention, you know, that my own shields up port scanner goes to some lengths to detect an open port without ever actually completing a connection since shields up emitts packets under my control, as opposed to like just using a full T C P I P stack. I send out a sin packet. If a remote system replies to my probing sin with its answering sin act. I never follow through with the final act to actually fully open the connection. Instead, I send a reset packet to force that half open connection to be aborted and immediately closed. Anyway, he continues Microsoft's solution comes via their acquisition of risk IQ, which we talked about when that happened.
Leo Laporte / Steve Gibson (01:19:20):
He said, presumably they're augmenting the external attack surface data collected with that tool with their own intelligence. And even tying that with data from other tools in the defender suite. And he says, we do something similar here. He says other common players in the ASM space include Showdan bit site security scorecard ran Dory and psycho psych Cognito. He says, and more popping up all the time. This is definitely a growing cybersecurity market. He says, I hope that helps. And indeed, Brad, thanks very much for the, for the follow up. And lastly an interesting point was made by a Tom Maher. He said, Steve in security now 8 83, which was last week. He said, you said, quote, any new hash will need to start over from scratch. Earning the reputation that that exact code file is trustworthy. He said, how does this interact with creating unique downloads of spin ride XE for each paying customer?
Leo Laporte / Steve Gibson (01:20:31):
Aren't those in conflict? And I've replied to Tom. I said, you are 100% correct. And as something I've considered at some length, as it has always been spin rights, Xes will continue to be uniquely created for each of its users. And I now have an HSM, a hardware security module from digit cert installed on GRCs main server, which will allow it to perform automated on the fly EV code signing. Oh, how cool is that? Yeah, that's thus providing the highest integrity assurance possible. So each custom created spin, right. Will be individually and validly signed, which is the best I can do. But there will be no way for each of those signed hashes to ever earn a reputation for themselves. Since each one, they, each one will be unique. Yeah. Therefore it may become common and expected for any reputation based anti malware service to be warning its spin, right.
Leo Laporte / Steve Gibson (01:21:40):
User that their freshly downloaded copy of spin. Right. Has never been seen before as indeed. It would have been. Yeah. But at least they will be EV code side. That's good. So you know the highest level of integrity possible. Yeah. That's really good. All right. Let's talk about TLS. Private key leakage, something you never want to have happen. You don't what you're leaking. You don't want any leakage on that one before we do, though, our sponsors Secureworks would like to put a word in your ear. What would happen if an intruder broke into your home and then moved in, you know, started eating your food, using your Netflix, lying on your couch. That's called a mother-in-law. Yeah. <laugh> well, you wouldn't want a, mother-in-law doing the same thing to your it infrastructure. Would you? How many passwords could they compromise? How many systems could they damage or degrade?
Leo Laporte / Steve Gibson (01:22:36):
How many pieces of personal or financial data could they steal? It happens all the time. I'm sorry to say. Threat actors often hide and play inside an it systems on average, more than 200 days, 200 days before they're detected. What happens when stopping at the endpoint is stopping your ability to properly defend your infrastructure. Enter SecureWorks, contagious, extended detection and response X, D R contagious enables a more comprehensive and effective security posture than ever before. With one unified singular point of view, providing unparalleled visibility and it's extensible following data, moving beyond the perimeter, helping organizations unify their prevention, detection and response. It mitigates the issue of siloed security solutions that leave coverage gaps for the adversary to leverage by organizing multiple point solutions and creating one unified clear picture of your infrastructure. Ts XDR can help teams prevent threats effectively detect them rapidly and respond appropriately.
Leo Laporte / Steve Gibson (01:23:42):
Secure works meets customers where they are with managed XDR yes, you can get it managed a SAS solution that can leverage the secure words, experts 24 7 to investigate and respond to threats on your behalf. So you can cut dwell times, increase operational burden, reduce cost. Some customers have a large security team. It can manage XDRL by themselves. Great. Bravo need minimal contact with the experts. But I think most of the time there's a shortage of security, talented companies, right? And you might need SecureWorks help to manage and monitor any potential threats in their environment. Just remember this number 1-800-BREACHED. Yes, they have an 800 number. In fact, even if you're not a customer, if, if you think there's an intruder, intruder alert, 1-800-BREACHED SecureWorks provides fast emergency response. They've got chat. They've got incident commanders who will find the root cause and then work with you to prevent future threats.
Leo Laporte / Steve Gibson (01:24:46):
When your organization experiences a breach or cyber attack, look the faster you act the better every minute counts. That's why you want to call 1-800-BREACHED one 800 B R E a C H E D. And SecureWorks emergency incident response team can provide you immediate assistance, responding to and remediating a possible cyber incident or data breach. And they're there by the way, all the time, 24 7, they're just waiting to leap into action. Secure works offers a purpose built XDR solution designed to answer today's evolving security challenges, optimized by machine learning and deep detection capabilities, but refined through human intelligence. There's no, there's no replacement for that. And insights earned over decades of experience. It's the best of both worlds, a Gartner, Forrester and IDC leader in security operations Secureworks empowers organizations with a collaborative and innovative security solutions required to achieve strong security in an evolving digital world.
Leo Laporte / Steve Gibson (01:25:48):
At Secureworks, you can learn more about today's threat environments and how they're evolving the risks they can present to your organization. They've got case studies, they've got reports from their counter threat unit and more look at they've got the intelligence. They've got the experience. They've got the tools, secureworks.com/twi get a free trial. Ofts XDR secureworks.com/twi SecureWorks defending every corner of cyberspace. And don't forget, please use that address. So they know you saw it here. Secureworks.Com/Twi. And maybe this is one excuse for a good post-it note, right on the side of the computer there 1-800-BREACHED when you, so the next time you're breached, you can call 1-800-BREACHED. All right, Steve, let's talk about TLS. Okay. So as I said at the top of the show, four researchers to each, from the university of California at San Diego and the university of Colorado in Boulder performed an amazing piece of work described in their paper, which they titled open to a fault on the passive compromise of TLS keys via transient errors.
Leo Laporte / Steve Gibson (01:27:06):
Their work was just presented during the 31st used Nick's symposium held in Boston last week. Okay. So to get everyone's attention I'm gonna first share their papers abstract. They said it is well known in the cryptographic literature that the most common digital signature schemes used in practice can fail catastrophically in the presence of faults. During computation, we use passive and active network measurements to analyze organically occurring faults in billions of digital signatures generated by tens of millions of hosts. We find that a persistent rate of apparent hardware faults in unprotected implementations has resulted in compromised certificate, RSA private keys for years, a faulty signatures. They said, I'm sorry. The faulty signatures we observed allowed us to compute private RSA keys associated with a top 10 Alexa site, several browser trusted wildcard certificates for organizations that used a popular VPN product and a small sporadic population of other websites and network devices.
Leo Laporte / Steve Gibson (01:28:36):
These measurements illustrate the fragility of RSA PKCS one version, 1.5 signature padding, which is the standard used and provide insight on the risks faced by unprotected implementations on a hardware at internet scale. And now I'll break all that down, but what they found, okay, well, I'll, I'll break down what they did and what they found. But one of the things I loved about the way they introduced the nature of the way digital systems can be fragile was to remind us of a true life example that we may all recall. They wrote during 2009 to 2011 Toyota issued multiple vehicle recalls. After hundreds of crashes had been reported relating to unintended acceleration. Remember those initially Toyota placed the blame on driver error, shifting floor mats and sticky accelerator pedals in 2013 expert witness, Michael Barr testified in the book out versus Toyota motor corporation case that a single bit flip suffused to kill a throttle monitoring task resulting in uncontrolled acceleration Toyota lost the case and began settling with crash victims out of court.
Leo Laporte / Steve Gibson (01:30:17):
The exact cause of the memory corruption in Toyota vehicles was never established. It could have been a buffer overflow, cosmic rays or hardware faults, no matter the underlying cause the existing hardware protections were insufficient and the software was brittle in the face of hardware errors. And the, the it's a little chilling how perfect this analogy is. Now we don't need to look further back than the week before last, when this podcast was titled RO Hammer's nine lives with DRAM, we have an unfortunate and persistent flaw where it's entirely possible for a bit of DRAM to spontaneously flip. It was during the 25th use Nick's security symposium in 2016 that the paper flip fun Shu was delivered. And in their summary, they noted that flip fun Shu relies on hardware bugs to induce bit flips in memory. They weaponized that unfortunate characteristic of weak memory operation.
Leo Laporte / Steve Gibson (01:31:30):
And we know that this could happen without a memory system being under active attack. The reason DRAM can be equipped at extra expense with parody checking and ECC is because DRAM memory is not perfect. Parity checking cannot correct, but it will at least catch a single bit flip and ECC can correct such an occurrence and, and all internet packets contain check sums to detect any simple errors introduced between the time a packet is created and the time it is received at the other end, these measures, and many others are in place because in reality, computers can and do make mistakes. While we would like to believe that every time we multiply the same two large prime numbers, we're gonna get the same result in reality. That's true almost all of the time, but it's that almost that can be weaponized. So with that bit of background, here's how these guys describe their work, what they did and what they found referring back to their Toyota example.
Leo Laporte / Steve Gibson (01:32:47):
They begin cryptographic software engineering is fortunately less often considered to be a matter of life or death, you know, than crashing a Toyota. They said, nonetheless faults can have a similarly catastrophic impact on cryptographic systems. As prior work has shown attacker induced or naturally occurring bit flips, can corrupt cryptographic computations causing them to produce incorrect results or even leak secret information or keys. In this paper, we show that these attacks can be implied, can be applied entirely passively, allowing a network adversary to derive TLS RSA private keys, simply by observing network traffic. When errors occur during a server's RSA signature computation, the resulting failed handshake can give an attacker sufficient information to derive the server's long term private key now. Okay. To clarify, before I continue, when a server makes a mistake during its computation of a TLS handshakes, RSA signature, that handshake will fail, but due to some known vulnerabilities in the specific cryptographic operations, actually that something known as the Chinese remainder theorem, the way the signature is <laugh> I learned about that last two years ago in the advent of code the Chinese remainder theorum I very never knew it even existed.
Leo Laporte / Steve Gibson (01:34:41):
<Laugh> geez. Yep. So the way the signature is wrong, leaks a bit of information about the private side of that RSA computation. So they continue. We demonstrate these attacks by collecting 5.8 billion TLS handshakes from two different university networks. These handshakes included 3.3 billion connections using TLS 1.2 or earlier, and 2.7 billion server signatures. Over a few months, we found nearly 2000 non-valid digital signatures from failed handshakes. Okay. Now, again, to be clear, that number should be zero, but some fault in the servers were resulting in a very low, but non-zero number of failed signature computations, nearly 2000 out of 2.7 billion, but that's all it took. They said some of these failed handshakes allowed us to compute three RSA private keys associated with Baidu, a multinational technology company in top 10, Alexa, these three keys were used to secure more than a million connections to hundreds of hosts in our data set corresponding to dozens of buy dues cloud based services.
Leo Laporte / Steve Gibson (01:36:37):
This passive attack is particularly concerning in the context of nation, state adversaries, conducting mass surveillance, unlike active attacks or remote compromise, which risk leaving evidence of tampering, passive fault analysis leaves no trace on either the client or the server. A network adversary only needs to observe network traffic passively, which again reminds us of the NSA that was tapping major exchange points. We didn't know why a network adversary only needs to observe network traffic passively and perform simple cryptographic calculations capabilities that modern nation states are known to possess and employ for the purpose of network surveillance. This attack is exacerbated when TLS servers and clients negotiate non forward, secure ciphers, allowing the network attacker to passively decrypt, encrypted TLS payloads using the servers private key without leaving any trace of compromise. Okay. Again, interrupt, we've talked about this before. Recall that I observed that expired and no longer valid web server certificates should be securely destroyed and not allowed to escape, even though they were no longer valid. The reason for that is when protocols without forward secrecy are used. The private key CA if it's later disclosed can be used to fully decrypt any conversations that may have been archived while that key was in use for possible future use. So these guys are observing that if all of a server's traffic is stored, and if that server later makes some mistakes during its RSA signature computation, then all of the stored communications can be retroactively decrypted.
Leo Laporte / Steve Gibson (01:38:56):
They continue in addition to demonstrating passive fault attacks. We also carried out active scans of TLS hosts and performed a retrospective analysis of historical TLS scan data between 2015 and 2022, that included tens of thousands of non-valid signatures. In other words, this is actually a problem, tens of thousands of non-valid signatures. In total, they said we computed 127 private RSA keys from these active scans. So by active scan, they mean that rather than passively collecting server handshakes being initiated by random clients, they became a TLS client and actively initiated a great many of, of TLS connections to specific servers. And sure enough, by doing lots of their own TLS connections, they were able to essentially force the remote server to eventually make a mistake. And they were able to then capture its security certificate. They said, we compare our results to active scans from a 2015 technical report by Florian weer of red hat.
Leo Laporte / Steve Gibson (01:40:26):
He appears to have been the first to observe that active scans could be used to detect or trigger these types of RSA signature fault at scale. So this was known in 2015, it's still happening today. He found that several open source TLS libraries did not implement countermeasures against signature faults and performed active TLS scans over a period of months, that resulted in a few hundred invalid signatures that successfully compromised private keys, mostly from devices, from several vendors. They said our passive analysis and recent active scans show that these problems are still present. In current implementations, we were able to compute the browser, trusted private keys for a handful of user facing websites from sporadic faults as well, observing dozens of certificate, private keys, compromised by devices. These certificates span from untrusted device default certificates to CA signed browser, trusted wildcard certificates for entire organizations. Although all of the open source libraries we inspected have implemented counter measures.
Leo Laporte / Steve Gibson (01:41:54):
It appears some proprietary TLS implementations are still vulnerable to this attack, and I'm not gonna go deep into the math because it's not really relevant to understanding the impact of this attack, but there is some historical background that I think everyone will find interesting. They said the flaw we exploit is well known in the cryptographic side channel literature first described in a 1997 paper about an RSA key recovery attack, almost all RSA implementations use the Chinese remainder theorem optimization for modular expon in RSA signing, but errors that occur in one of the half expon in this algorithm can result in leaking information that can be used to derive the RSA private key. A researcher named a K Lera had published a technical report the year before in 1996, titled just memo on RSA signature generation in the presence of faults.
Leo Laporte / Steve Gibson (01:43:13):
LENR improved the attack to require only one signature. When the message is known, this attack works against any deterministic, RSA signature scheme using the Chinese remainder theorum optimization. The countermeasure to these attacks is to validate the RSA signature before sending it. And I should mention that I saw another reference in this that, that Peter Gutman indicated that that incurred about a 10% overhead in performance. So you've gotta do it, but it does cost you a bit prior to Florian. Weks at work in 2015, they said almost no implementations validated RSA signatures before sending. So it was just in the technical crypto literature until Florian noted this working for red hat in 2015 before then nobody was doing RSA signature validation. And even after that, even though, well, they said following the report, all of the software libraries weer contacted, implemented countermeasures.
Leo Laporte / Steve Gibson (01:44:30):
You bet. And Cavium issued a patch for their cryptographic accelerators, which appeared to be at fault for several of the vulnerable devices he discovered. They said in this work, we find that spontaneous faults compromising RSA keys through PKCS one version, 1.5 signatures continues to be present at a low but persistent rate in both passive and active network measurements over time, despite the attention drawn to this vulnerability in 2015, in other words, it should hardly come as the surprise to anyone, not everyone got the memo and fixed their code, or since then perhaps new code was created. And the wisdom of the past was lost. They said in the present era in 2022, we find that this flaw is not just present in the types of network devices that have already been observed to suffer from cryptographic implementation flaws in previous studies, but that it also affects user facing websites and infrastructure that receive significant amounts of network traffic.
Leo Laporte / Steve Gibson (01:45:46):
They finish. These vulnerabilities are due to a hazardous combination of cryptographic libraries vulnerable in the face of computational errors and the brittle nature of the RSA PKCS one version 1.5 signature padding scheme used in TLS. 1.0 through 1.2 PKCS one, 1.5 signature padding makes key compromise trivial in the presence of Chinese remainder theorem faults. Prior to TLS 1.3 handshakes take place in plain text, providing all the information is pass all the information. A passive network adversary needs to validate signatures on observed connections or derive keys when errors occur. But on a more positive note, TLS 1.3 provides multiple counter measures against these issues, including moving the key exchange earlier in the handshake, in order to ensure that certificates and signatures are sent encrypted and using RSA PSS signature padding, which prevents this type of key compromise if implemented correctly. So a long ago, discovered and known yet still present and haunting the internet, significant weakness.
Leo Laporte / Steve Gibson (01:47:21):
The current implementation of some TLS handshake stacks exists. The eventual migration to TLS version. 1.3 will finally fix this, but TLS 1.2 support will not be disappearing for a long time. So an active adversary could insist upon negotiating under TLS 1.2 while its support continues, which as I said, won't be going away soon because there's gonna be lots of clients that don't yet do 1.3. So a bad guy negotiates under 1.2 and hopes to get the remote server to stumble over its RSA signature computation. If that were to happen, its private key could be disclosed. And at that point well, you know, it's, it's security is completely compromised just by listening or in some cases actively attacking. Wow.
Leo Laporte / Steve Gibson (01:48:30):
It's so fantastic that I could finally use my Chinese remainder theor <laugh> yes. For more than, you know reheating your kg P chicken the next day. Yeah. Getting, getting Santa Claus to the elves in time. That's great. That's great. All right. I don't think I understand, but I, I, I will listen a again and maybe I'll understand it on the second time through Steve is a genius that is clear. And by listening to him, we all benefit. I hope you enjoy this show. Hope you come by again. Next Tuesday, when we do security, now let me give you some of the information you might need to stay in touch. Of course, Steve has a copy of the show at his website, grc.com, the Gibson research corporation. He actually has two unique versions of the show, a 16 kilobit version. In addition to the normal 64 kilobit version, it sounds a little scratchy, but it is a lot smaller.
Leo Laporte / Steve Gibson (01:49:26):
So if you have a limited bandwidth, that's a great place for you. I think we, you started doing this years ago, cuz we had listeners in Australia who had extreme bandwidth limits and they wanted to listen to the show and this was the only way they can do it. And I I'd hate to get rid of it. Somebody probably using it. Do you see any downloads on it? Well, I, as far as I, I know Elaine is still using it that's she made it for, she had a satellite connection. Right. And the files were, were uncomfortably large for her. Perfect. Yeah. So for anybody with bandwidth KES and Elaine does take the 16 kilobit version listens carefully to the scratch. And it sounds like Thomas Edison's first Dictaphone recording, but anyway she then makes a very good transcript of every show. So you can search the transcripts or read along as you listen, both of those are@grc.com along with the 64 kilobit version when you're there do check out spin, right?
Leo Laporte / Steve Gibson (01:50:21):
As you hear it's in, it's in active development right now, current version of spin, right? The world's best mass storage, maintenance and recovery utility is 6.0, but six point one's on the way you buy 6.0 now you'll get 6.1 free when it's available, you can also participate in the development that's grc.com and then when you're there, gosh, there's so much other wonderful stuff worth checking out. Steve. Steve is of why, what did they say about Isaac Newton? Well, a mind ranging freely. He is all over the place would be another <laugh> another way to talk more good. Temporary way to it. Yes. what, there was a great quote about Newton and I can't remember exactly it was originally the apple logo. That's the only reason I I know it anyway. Cool. Yeah. I think it was a mind forever.
Leo Laporte / Steve Gibson (01:51:17):
Voyaging. Thank you. I think that's a good name for you actually a mind for voyaging, right? I'm bailing water. Leo <laugh> through a mind through ever forever voyaging through strange seas of thought. That's what Williams Wordsworth said about about PS, Isaac Newton, ah, alone. Oh, I, I left off the most important part. Oh I, I think this is not for you. You can put it on your tombstone. Maybe a mind forever voyaging through strange seas of thought alone. No that's not. Steve he's community is good thing. Yeah, exactly. Community is a good thing. We have the show as well. On our website, we have audio and video at twit.tv/sn you can download it there. If you wanna watch us do it live. You'd like you want the very freshest copy of security. Now there is a live stream every Tuesday, about one 30, between one 30 and 2:00 PM, Pacific four 30 and 5:00 PM. Eastern 2030 UTC. That's at live.twi.tv. You could chat there. Live with us@ircdottwi.tv or in the club TWI.
Leo Laporte / Steve Gibson (01:52:29):
We also have on demand versions, as I mentioned on the website and there's a YouTube channel. Of course, the easiest thing to do, whether you use Steve's feed or our, it doesn't really matter is subscribe and your favorite podcast player. And that way you get it automatically and you don't have to think about it. You just just know you've got security. Now start your collection. Now you only have 883 other episodes to get <laugh> and I do watching get downloaded. Oh yeah. Yep. Oh yeah. You're 18 next week. Next week. Very exciting, Steve. Woo. Thanks for being here. We'll see you next time on security now. Thanks buddy
... (01:53:07):
Security Now.