Security Now Episode 872 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for Security Now, Steve Gibson is here. Well, well, what do we have to talk about? We're gonna say hello to clear view. AI's facial recognition. They're using it in Ukraine, but is it okay? And then it's the results of Vancouver's poem to own competition. We'll talk about Steve's bizarre theory about what's going wrong with Voyager one and then a look at the Kati ransomware operation. It looks like they've gone out of business, but have they it's all coming up next on Security Now, podcasts you love from people you trust. This. Is TWiT..This is Security Now with Steve Gibson episode 872 recorded Tuesday, May 24th, 2022. Discontinued the end of Conti. This episode of security now is brought to you by Barracuda. Barracuda has identified 13 types of email threats and how cyber criminals use 'em every day fishing conversation hacking ransomware. Plus 10 more tricks.
Leo Laporte / Steve Gibson (00:01:11):
Cyber criminals use to steal money from your company or personal information from your employees and customers. Get your free ebook at barracuda.com/securitynow, and by PlexTrac the proactive security management platform that helps you focus on winning the right security battles with PlexTrac, you'll streamline the full workflow from reporting to remediation. Visit plextrac.com/twit and claim your free month and by Net Foundry. Reinvent the network and eliminate the wan by decoupling security from infrastructure to protect our applications and data with open source zero trust, grab your free swag and free tier. Now by going to netfoundry.io/twit it's time for Security Now the show where we cover your privacy, security and safety online with the man, the myth, the legend, Steve Gibson. Hello. Apparently we are a well caffeinated team is, ah, yeah, a little bouncy right now. Yes I am. Or this early afternoon, rather, whatever, whatever it is.
Leo Laporte / Steve Gibson (00:02:17):
So you agreed with me that the title for the show is a bad pun. Scott. Awful. Yes. It's God ha disti nude disti nude. Yes. Yes. The end of Conti question mark that's this has become, I think, kind of a new Mo for these, these bad guys and what's yes, thank you for the perfect foil sway Leo, because that's actually what hooked me on the story and what I thought may would make it so interesting for our listeners is that, is that there is evidence that this whole Costa Rican debacle was a setup designed to obscure the reformation of KTI. So and oh, it's really interest. Yes. Which is, and remember how it didn't like something seemed off about it. Yeah. It was like what, you know exactly. It was weird when we talked about it last week, actually for the last couple weeks in various aspects and it's looking like it was actually, well, okay.
Leo Laporte / Steve Gibson (00:03:38):
I don't want to, I don't want to give it all away here at the beginning because we have lots to talk about. We're gonna follow up on Microsoft's patch Tuesday after Dr. Active directory domain controller mess. We're gonna look at several instances of the clear view AI facial recognition system, making news, and at the systems which fell during last week's Vancouver own to own competition. We cover some welcome news from the us department of justice. They're rethinking what it means to be an ethical hacker, which is really good news and some disturbing news about a relatively simple and obvious hack against popular Bluetooth linked smart locks. We've got some closing, the loop feedback, actually only three pieces, but one of them ends up being well, actually two of them, both <laugh> two or the three end up really big being, you know, expanding into something.
Leo Laporte / Steve Gibson (00:04:32):
Cuz we're gonna take a look at what's going on with the Voyager one space probe, which has just started to act a little wonky. You mean VRE? Oh, please. Don't say VRE. That was God. Was that an awful movie? Thank, thank goodness. Somehow we were, they were forgiven for producing that first atrocity and then we got con so <laugh> yes. Vire I have a theory about what might have happened, which you're gonna get a interest you a kick out of. Yeah. well anyway, I'll save that too. And another interesting look into the looming impact of quantum crypto. We then are gonna finish by sharing an in-depth examination of the surprisingly deliberately orchestrated shutdown of the KTI ransomware operation. Mm. It turns out it was far more well planned than was known. And essentially the guys that have been watching this have spoiled what Conti was trying to do.
Leo Laporte / Steve Gibson (00:05:40):
Oh good. And it's real. Yeah. Good. Okay. And we have a pretty funny picture of the week. So I think another great podcast for our listeners. What a shock spoil the spoilers <laugh> all right. All coming up on the show before we go too far load, let's talk a little bit about our sponsor for the segment Barracuda. And let's talk about email because that really is becoming a prime vector for malware into an organization. Spearing specifically in a recent survey, Barracuda found out that 43% of their response said they'd been victims. 43% had been victims of a spear fishing attack. And maybe it's not a surprise. Only 23% said they have dedicated spear fishing protection. I'm happy to say we do thanks to you Barracuda. How do you keep your email secure Barracuda has identified in fact, a total of 13 different kinds of email threats, not just spear fishing and how cyber criminals are using every day to pound on your door to trick your employees, to PO your system, there's fishing there's conversation, hacking there's ransomware and 10 more tricks.
Leo Laporte / Steve Gibson (00:06:52):
Cyber criminals use to steal money from your company or personal information from your employees, which could be just as valuable and even customers, right? And then they blackmail you, are you protected against all 13 types? Email cyber crime is of course becoming more sophisticated because there's more money in it and attacks are getting more difficult to prevent. They'll use social engineering, of course, urgency and, and fear to prey on victims, social engineering attacks like spear fishing business, email compromise, cost businesses and average of $130,000 per episode, $130,000. I mean, here's an example as a demand for COVID 19 tests increased at the start of this year. Barracuda researchers saw an increase in COVID 19 test related fishing attacks increased by 521%. It's very opportunistic, isn't it? They're they're, they're very clever. They've gotta get your employees to jump without thinking. So they prey on their fear.
Leo Laporte / Steve Gibson (00:07:51):
There's anxiety cryptocurrency, another hot topic as the price of Bitcoin increased last year by about 400% Barracuda research found impersonation attacks growing 192% in the same period directly correlated in all of 2020 last year, the internet or two years ago, I guess the internet crime complaint center, I C three received 19,369 business email compromise or account compromise complaints, B C, or email account compromise E C with adjusted losses of 1.8 billion oh dollars. You gotta secure GA email. And it's just, it's not enough just to secure the gateway. Of course you've gotta have, you know, perimeter, gateway security protect against the traditional tax viruses zero day ransomware spam and other threats, but targeted attack fishing is gonna go right through. So you gotta protect at the inbox level as well, including, and this can't be just like your spam, Andy spam filters. Now you need AI and machine learning to detect and stop these threats that are evolving.
Leo Laporte / Steve Gibson (00:08:58):
They're sophisticated. Here's the thing to do. Get a free copy of the Barracuda report. 13 email threat types to know about right now. You'll see how cyber criminals are getting more and more sophisticated every day and how you can build the best protection for your business data and people with Barracuda. Find out about the 13 email threat types. You need to know about how Barracuda can provide complete email protection for your teams, your customers, and your reputation. And if you're in it just, you know, you know this, but get the pamphlet and give it to your boss, give it to the board, let them know about this. Cuz I think it's really important as you know that your efforts, your security efforts are supported by the people who are signing the checks. They've gotta give you the budget you need. The good news is Barracuda is easy to back up.
Leo Laporte / Steve Gibson (00:09:45):
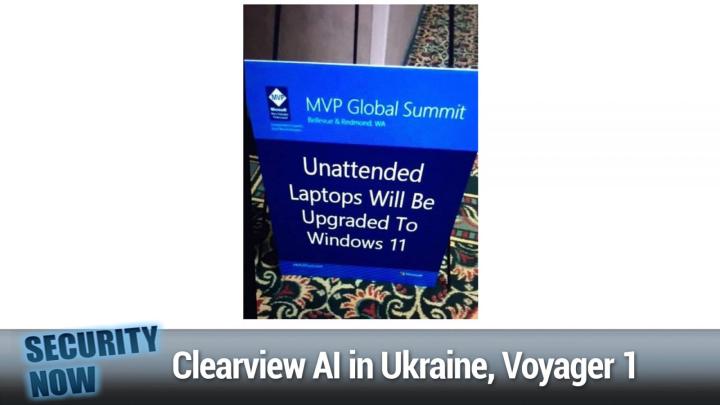
You're gonna love it. Get your free ebook at barracuda.com/securitynow this begins your conversation about this stuff. Barracuda B a R R a C U D a.com/Security Now Barracuda your journey secured. And if you're the C level or the CISO or the CIO or the board member, get it from them too and give it to your it. People see if they, if they're, what are they? This is a question I'm always asking. Are we safe? What are you doing? Barracuda.Com/Securitynow picture of the week time Mr. Gibson. So, okay. So everything about this picture to me looks authentic. It's this is it. It it's showing a, a standup card, sort of a, a not an ad a, like a it's a table card. They put 'em on the table or a yes, a placard to put outside the event, the conference for a Microsoft MVP global summit.
Leo Laporte / Steve Gibson (00:10:52):
And again, it, you know this, so this was in a conference in a hotel. You can see this God awful hotel carpet UN underneath it. Isn't it always ugly <laugh> oh, it's always the worst. It's I think it's so that it hides barf and like anything else that's exactly right. That's chewing. You know, it spilled cocktails. Exactly. You know, it just, you know, no nothing is gonna, you know, no spots will, will show through this horrible print that this thing has anyway. So, so we have this sign and it's, so it, it was originally boring signage. It probably said, you know security summit conference, 2 0 3 B or something. Anyway, some person with a sense of humor changed around the normal heading and everything, which is looks a hundred percent authentic. They change the sign of the Microsoft MVP global summit announcement to say, or to caution unattended laptops will be upgraded to windows 11.
Leo Laporte / Steve Gibson (00:12:01):
Ooh. Which you know mean not what, not what anyone wants <laugh>. So do, do not leave your laptop, unattended children or you make, find out that your menu can no longer be docked. The left hand side of the screen. You must have it in the center because we're sure that's better for you. Okay. So speaking of Microsoft last week, we noted that the previous week's patch Tuesday had been overly eventful with admins reporting that the month's patch roll up had adversely affected the operation of some of their enterprises, critical authentication infrastructure. The Malfa the malfunctioning patch was intended to close an actively abused security vulnerability. And while there were some pre-PA workarounds, most admins were choosing to simply roll back their systems by removing the entire Mayday patch bundle. So that's where we were last week. Last week, I wondered out loud whether Microsoft would attempt to fix the fix and hopefully detest it more thoroughly this time, or whether they would prefer to wait until June's patch.
Leo Laporte / Steve Gibson (00:13:14):
Tuesday. One problem with waiting is that June begins next Wednesday, which places June's patch Tuesday as late in the month as possible, nearly in the middle, on the 14th. And in the past Microsoft's patching logic has been well calling it inscrutable is being kind. Sometimes they wait half a year before patching something. Other times they patch it in a hurry. Fortunately for active directory users, the latter was the case here with Microsoft fixing the trouble in about a week and releasing a mid cycle emergency patch last Thursday. However, presumably since it was only domain controller servers that were being adversely affected that point, that Microsoft took great pains to point out throughout all this as like, oh, oh, you know, it's all fine. Don't worry about it. It's only these people like, you know, the admins of the largest enterprises in the world who are, you know, <laugh> been brought down by this.
Leo Laporte / Steve Gibson (00:14:21):
So as a consequence, the emergency update is not being made widely available through the regular windows update channel. You know, they're not wanting to like update everybody again, cuz most people aren't affected. So enterprising users, if you'll bar the pun will need to get it from Microsoft's update catalog by going there directly. But you can also those users in the enterprises who have windows server update services or Microsoft's endpoint configuration manager can import the update from the catalog into those services and then it'll fix their networks. So since SISs a, was forced to pull the requirement of patching this flaw from their catalog of known exploited vulnerabilities, due to May's debacle, we can assume that it will, will be returning to the catalog now that it is possible to actually patch against this. Remember actively exploited flaw in in active directory in any event it's O it should be obvious to everyone these days that more than ever patching has become everything, you know, patch, patch, patch, patch, patch, you just, I mean, it's, it's better to patch and regret it than it is not to patch at all because you know, well that should be pillow or something.
Leo Laporte / Steve Gibson (00:15:48):
That's good. <Laugh> that's, that's a good motto. <Laugh> well, it's the motto that evolved from this podcast because just look around. Wow. Okay. We've talked about clear view AI on several occasions, recall that they're the company which provides would've turned out to be quite controversial. Facial recognition services to apparently anyone who wants them. The controversy surrounds the perceived privacy invasion created when an army of both visible and invisible cameras might be scanning and cataloging the real world identities of everyone who crosses through their fields of vision. 30 years ago, we lacked the ability to automate anything like this at scale, because it all comes down to economics. We didn't have inexpensive cameras. We didn't have inexpensive communications, bandwidth or inexpensive, and apparently endless amounts of storage or computation. Today. We have all of that at Essent, essentially for next to nothing. So what could not be done in the recent past is now feasible at a mass scale global, during a recent interview, clear view, AI's CEO, a guy by the name of hone to fat explained that he intends to have 100 billion images in their database within a year.
Leo Laporte / Steve Gibson (00:17:23):
Currently they have about 20 billion and 100 billion would represent 13 photos of each person on earth. Obviously not all equally represented, but the, the, you know, the probably the more important you are, the more photos you've got in the database. Okay. So the potential for the abuse of this technology is breathtaking due to its sweeping scope. One of the times we've talked about these guys in the past was when the a C L U the American civil liberties union and others brought a lawsuit against Clearview AI in Illinois. Thanks to Illinois's very restrictive biometric information, privacy act B IPA or BIPA, which became law in 2008. Thanks to BIPA any entity wishing to collect biometric identifying information, you know, and a photograph is that I, I knew it was you Leo, when you sat down just by looking through the camera very high intelligence <laugh> for any Illinois citizen, any entity wishing to collect biometric, identifying, identifying information for any Illinois citizen must first obtain their explicit consent before doing so, which of course clear view AI never does.
Leo Laporte / Steve Gibson (00:18:57):
You know, they're scanning online image sources. So consent is never requested nor received. Thus, you know, they immediately fell foul of Illinois's very restrictive BIPA earlier this month, Clearview AI agreed to a settlement in that lawsuit, which, which was brought by the a C L U that would largely prohibit sale of services to private companies, which previously weren't prohibited and people similarly. And you were just talking recently about how it turned out that you could get location in, like individuals could purchase location information on other oh yeah. Individuals. It's nothing. Data brokers are amazing. Yes. And so clear view AI clearly a massive cloud based broker that also provides image matching. So the, the, the terms of the suit prohibit the sale of Clearview AI services to private companies and people in the us as well as to law enforcement throughout Illinois for the next five years.
Leo Laporte / Steve Gibson (00:20:10):
However, Clearview AI CEO said that the settlement would not change anything on a material level because they could continue to sell to any government clients elsewhere. So they took what they consider to be a little hit and they'll continue <laugh>, you know, unabated at the same time clear view, AI is increasingly facing pressure from various nations privacy regulators who are pushing clear view to remove their data on their citizens from its systems, both Australia and Canada last year ordered the company to delete information on their residents. And now last week, the UK's government announced that they are levering a fine of more than 7.5 million pound Sterling that's around 9.4 million us dollars against clear view AI and have ordered it to stop collecting information about UK residents and to delete all of the data that it already has from its database. The UK's information commissioner John Edwards said in a press release, quote, the company, not only enables identification of those people, but effectively monitors their behavior as, and offers it as a commercial service that is unacceptable. People expect that their personal information will be respected regardless of where in the world their data is being used. That's why global companies need international enforcement Edwards added that he would be meeting with European regulators and Brussels later this week to collaborate, to tackle global privacy harms. So, and, and I didn't mention they, these guys are the biggest now globally. They are the number one facial recognition service provider in the world.
Leo Laporte / Steve Gibson (00:22:21):
These recent moves by the UK's information, commissioner's office follow a joint investigation by the agency and the office of the Australian information commissioner, which launched in July of 2020. So that's been going for some time and was completed last November, a provisional notice from the information commissioner's office to clear view that month warned the company to stop processing and to delete UK resident data, as well as suggesting a substantially larger at the time they were saying they wanted 17 million pound Sterling. It ended up being seven and a half, but still, you know, it'll get your attention. In reply again, clear views founder and their chief executive that hone Tom fat said he was quote, deeply disappointed that the UK data authority misinterpreted his company's technology and their intentions Uhhuh. He said, I quote, I would welcome the opportunity to engage in conversation with leaders and lawmakers, so that the true value of this technology, which is proven so essential to law enforcement can continue to make communities safe. He said, okay, so there's one side. There's also been clear view, although not by name until recently in the news relative to Russia and Ukraine.
Leo Laporte / Steve Gibson (00:24:00):
There's no question that facial recognition technology has the potential to be quite useful. It is clear view AIS, facial recognition technology that has been allowing the Ukrainian government to identify both their own citizen casualties of war. You know, in obviously in their war with Russia, as well as the Russian soldier casualties who been left behind by their comrades. Thanks to Clearview AI's knowledge of Russian citizens. Ukraine has been able to Mount a potentially powerful political counter offensive by identifying these Russian war casualties, notifying their families of their demise and offering to allow them to travel to Ukraine, to reclaim their fallen family member. Some 400 Ukrainian investigators are currently using Clearview AI's technology to build much more airtight war crimes cases. As a consequence, it really helps to know who you're talking about. And certainly Russia's not providing that information. The, the, the publication, the record recently interviewed Clearview AI's founder and CEO, this hone Tom fat whom I, whom I referred to before.
Leo Laporte / Steve Gibson (00:25:27):
And I think that the details reveal by that interview are worth sharing. So I've, I've edited it a bit to bring it up to the level of our listeners. So in the interview, the question is posed. How did clear view come to play such a major role in Ukraine? Hone replies? When the war started, it was really shocking to me and a lot of members of our team to see, especially the video footage of women and children suffering. And it made me think, how can we help originally? I would see photos of captured Russian soldiers. And I realized that with that kind of photo quality, our facial recognition technology could be helpful. So I reached out to a lot of people on our advisory board to ask them, do you know anyone in Ukrainian government and one person Lee Olasky he's on the national security council, under three presidents, he quickly said, yes, we thought that it could be helpful in identifying deceased soldiers and track misinformation.
Leo Laporte / Steve Gibson (00:26:34):
So how could it be useful to track? Misinformation is asked. Hone says, you'd see a lot of things on social media saying this is a captured Russian soldier, but you might see people on the other side saying, actually that's a paid actor and here's the name of the paid actor. So with this technology, the level of accuracy can be used to identify if someone is who they say they are. So the questioner asks who in Ukraine has logins to clear view AI hone it's in six different agencies, including the national police of Ukraine. Then the people on the ground would be using it. So we gave a demo, we'd give them training on how to use facial recognition, technology responsibly. So part of the training is that they would send photos of unidentified people and run it through the system and we could show them, Hey, this is how you verify who it is.
Leo Laporte / Steve Gibson (00:27:37):
So for example, if they have a tattoo that matches online, there's a very high chance. It's the same person. So the questionnaire, you inserted this technology into a war zone, which presents a lot more problems than having a police department in the United States using it. How are you accounting for that hone responds. You want to be careful to make sure that they really know how to use it properly. And so there are all these scenarios that we wanna make sure don't happen. For example, what if someone takes a photo of someone and says, Hey, I think you're a Russian trader. And then they detain them. And it's all incorrect based on incorrect information. So we'd never want something like that to happen. As long as these investigations are done by trained investigators, this can be a very useful tool if it was used by everybody.
Leo Laporte / Steve Gibson (00:28:35):
I think that's when problems happen. So the interviewer what's the most surprising use you've seen in Ukraine hone says war crimes investigations. We were talking to people in the national police of Ukraine and others, where they have video video footage from surveillance cameras, smartphones are more prevalent. So there's a higher chance of something being recorded. Now with this technology, if it's easy to identify someone, I think people are gonna think twice about war crimes. So that was a surprise to me. He was that, okay. So the interviewer asks, so this is a subscription service. And you say that gives you more control. If someone is misusing it, how does, how does clear view AI work? You said we vet every person to make sure they're a government official who is using it. There's also two factor authentication. So they still have to verify their device before they log in.
Leo Laporte / Steve Gibson (00:29:39):
Once they have an account, there's an administrator for each agency. So the administrator can see who is conducting searches and what reason they're conducting the search. There's an intake form that requires a case number and a crime type before conducting a search. So people when they're onboarded and they've learned about the software, they know that their searches can be audited because we want to make sure they're using it for the right kind of stuff, because it's a cloud service. We have the ability to revoke access. If there's any egregious abuse of the technology, you wanna make sure that we have the ability to take it away. The interviewer asks the it army appears to be using it in a video. The group demonstrated the use of a facial recognition program that appears to resemble clear view AI. This is a volunteer hacking force. So how is it that the Ukraine it army appears to be using Clearview?
Leo Laporte / Steve Gibson (00:30:46):
AI hone says, all I can say is that everyone we've onboarded is a government official. We haven't onboarded anyone in the it army directly. Everyone we talk to and onboard. We give them proper training on its usage. The speculation that the it army is running a clear view, AI search does not match any information we have on this matter clear view. AI is intended for use in Ukraine, by law enforcement and government officials. So then the questioner did, maybe somebody give a username and password to somebody who's in the it. Army ho says it's possible that someone shared a screenshot or shared how it worked, but we wanna make sure that whatever the usage of the technology is say it is to identify someone deceased that is done in a way that is positive. The policy of the national police and all our users is to tell the family members in a humane way.
Leo Laporte / Steve Gibson (00:31:54):
The question had it occurred to you that the it army would use this technology to notify families of dead soldiers. As a propaganda tool, hone says, I talked to some of the officials in the Russian government and I said, look, is this something you knew about? Is that your procedure for doing that then said, that's not our official procedure. And they assured me, that's not what they want to have happen either. Again, this is war time. Tensions are really high. Those things can happen. Hone continues. If I thought it would be used in a really bad way that I don't think I'd give access to them. We think that just getting the information out in a humane way is the most important thing. What we can control as cur clear view is giving access to the right people. So for example, we don't give access to the Russians or anything like that.
Leo Laporte / Steve Gibson (00:32:51):
And we make sure Ukraine is trained as appropriately as possible question. Have you revoked any access related to Ukraine because you thought it wasn't being used properly? Ho replies no, not at this time, but the administrators of these agencies in Ukraine have the ability to do so they can go in and audit the searches, remove access to an account and give access. As they deem appropriate clear view, AI would only revoke access to an agency. If there was an egregious amount of abuse in that agency, until something really escalates to that level, we haven't revoked any access.
Leo Laporte / Steve Gibson (00:33:32):
The interviewer, the NSO group is an Israeli company that makes surveillance software that can be remotely implanted in smartphones. It has come under heavy criticism for its tech being used by authoritarian governments, to spy on their citizens with your facial recognition technology. How do you avoid the NSO trap home replies? I think NSO is a very different kind of technology than what we do. We are searching public information from the internet. So it is really just like Google. If you can type someone's name and the word LinkedIn into Google and you find their photo, then clear view can basically do the same thing, but it's searched by photo. We also work with law enforcement. NSO is different because it's breaking into phones, very private data. Also when they sell their software, they don't have the ability to take it back if they sell it to the wrong actor or government, whereas clear views software is deployed in the cloud.
Leo Laporte / Steve Gibson (00:34:46):
If we ever find anything totally egregious or abusive, we have the ability to revoke access. We also want to be aligned with democratic countries, making sure that this is a technology that can be used responsibly and across democratic nations. And lastly, can you imagine a scenario is asked years and years from now when everyone has this capability, that it would be like VR glasses or built into a phone. Hone says, I could imagine like augmented reality is an interesting where it could be deployed on military bases. So in Afghanistan, they had a situation where they were pulling out at a checkpoint. Terrorists could blow up people. They are looking up close at the IDs to verify someone at a distance in a hands freeway. I think that's a very positive kind of use case.
Leo Laporte / Steve Gibson (00:35:51):
So you know, it's obviously trivial to invent synthetic positive use cases. It's at least as easy, probably much easier actually to imagine quite privacy intrusive use cases. You know, the logic we often hear being applied by those who object to the use of pervasive facial recogni evasive facial recognition is the assumption of privacy. They suggest that someone walking in a public space can be seen by everyone. So there's no assumption of privacy, but when a meta tagged photo is taken among friends in a private setting and posted online to celebrate, is it reasonable for those images to be vacuumed up identified, cataloged and made available for F for searches globally? The argument is made that posting the photo online creates implied consent, but is that for any use whatsoever forever? So we have another new problem created by astonishingly inexpensive technology. You know, so as a society, we're gonna have to figure out what's important and what we want and how we want these things to work.
Leo Laporte / Steve Gibson (00:37:09):
And, you know, I don't have an answer it's clear from the way hone was answering that, and he's on defensive, right? Yes. That he's been sensitized to, you know, all the ways this, this technology of his, which I'm sure is generating lots of revenue for clear view AI, you know, all the ways it could be abused. So mixed blessing, thanks to the technology. Once again, and Leo my water here is a decidedly non mixed blessing. It could be misused, I think, but please use it. Yeah, well, yes. Use it wisely. You poison yourself if you drink it to extreme. Yep. It hasn't. Yeah. Be careful. Make sure you're replenishing your electrolytes at the same time. And meanwhile, I shall replenish your purple team. <Laugh> with a very, to my tool they're gonna want. And if you don't have a purple team, get one purple is a red and blue, right?
Leo Laporte / Steve Gibson (00:38:09):
So you've got a red team looking for the vulnerabilities. You've got a blue team remediating the purple team is all about communication. And that's what PlexTrac sponsor for the segment is all about. And really it's for all three teams, it's a proactive cyber security management platform. If you're ready to gain the benefits of purple teamy, which you have no idea how to get started, or maybe you're working to mature your security posture, but you know, struggling to optimize efficiency and facilitate collaboration within your team. Well, this is a perfect solution, PlexTrac. It's powerful, yet simple cyber security platform that centralizes all your security assessments, all your pen, test reports, your audit findings, your vulnerability tracking in one place. Plextrac transforms the risk management life cycle. It means your security team, your red team can generate better reports faster. They can aggregate and visualize analytics and then collaborate with your blue team on remediation.
Leo Laporte / Steve Gibson (00:39:11):
In real time, there are a bunch of different modules, but let me talk about a couple of them that specifically address the pain points that your security teams may have with their workflow, their reports module. For instance, I know this is, you know, basic stuff, but boy, it saves a lot of time. If, if you find that your red team and blue teams are spending a lot of time at the keyboard entering findings, this is the way to do it. You can easily slap in code samples, screenshots videos. They can be attached to any finding. You can import findings from all your major scanning tools. 1, 2, 3, boom, and you can create custom templates with a click of a button and then export to those templates. So if you've got a standardized form, you don't spend a lot of time formatting and typing. You just go who boom, and you're ready.
Leo Laporte / Steve Gibson (00:40:01):
The runbooks module. You'll love this. If you're on a red team, it can facilitate your tabletop exercises, your red team engagements, your're breaching attack simulations, purple teaming activities to improve communication and collaborating PlexTrac really upgrades your program's capabilities by making the most of every team member and tool. There's an analytics module. This really helps with communication, whether it's to stakeholders the board it helps you visualize your security posture. So you can quickly assess. It's great for you to assess and prioritize, which also helps create a more effective workflow. You can map risks to frameworks like minor attack, created risk register enterprise security teams to often use PlexTrac to streamline their pen tests, their security assessments, their incident response reports, keeping the red and blue teams focused on getting the real security work done. Plextrac is great for employee because it makes their life much easier.
Leo Laporte / Steve Gibson (00:41:00):
You'll get precious time back in your team's day so they can do the job you hired him to do. If you go to Plex, track.com/twi, you could see all the, all the references, all the companies that use it as an example of Jacob's engineering, they said deploying PlexTrac allowed our team to cut the reporting cycle by 65% spend less time, you know, doing busy, work more time, locking things down, look, book a demo today, see how much time PlexTrac can save your team. And they will I'm. They will love it. It doesn't add to their workload. It simplifies it. Try PlexTrac free for one month, see how it can improve the efficiency and the effectiveness of your security teams go to plextrac.com/twitt. Get that free month. P L E XT R a c.com/t w I T PlexTrac. We thank him so much for their support of security now, and the good work Steve does here, and you support him and and the team by going to plextrac.com/twitt.
Leo Laporte / Steve Gibson (00:42:06):
So they know you saw it here, Steve, what's what you looking at? I just turned my temperature down a degree. Oh, it's a little warm, a little toasty, isn't it? Yeah. Yeah. Okay. So that brings us to poem to own Vancouver 2022. Oh last Wednesday, Thursday and Friday, the 18th through the 20th was the 15th anniversary of P to own held in Vancouver. And this year, rather than enumerate the victories of many brilliant hackers who we don't know and many of their names, which I cannot begin to pronounce correctly <laugh> so I rather not mango them. No good. I'm gonna focus. I'm gonna focus upon the products which we do all know, and which fell to their best efforts. On the first day, Wednesday last week, the various hacker individuals and teams demonstrated an improper configuration against Microsoft teams. And I didn't put in all the dollar amounts in here, but as I recall, that one got them $150,000.
Leo Laporte / Steve Gibson (00:43:20):
So that was some serious improper configuration against Microsoft teams. There was also an out of bounds read and out bounds, right, which was used to achieve privilege escalation against Oracle's virtual box, a three bug chain of injection misconfiguration and sandbox escape against Microsoft teams prototype pollution and improper input validation against Firefox an out of bounds, right? Escalation of privilege on windows 11, two bugs on a Buntu desktop, an out of bounds, right? And a use after free were used, there was a zero click exploit of two bugs, an injection, and an arbitrary file, right against Microsoft teams, an outbound right against Microsoft safari and a use after free elevation or privilege again against Microsoft windows and a use after free exploit on Ubuntu desktop. That was just the first day, day two, the hackers and some teams demonstrated two unique bugs, a double free and an out of bound, right?
Leo Laporte / Steve Gibson (00:44:35):
With collision on a known sandbox escape on a Tesla model, three infotainment system, they were able to basically take over the Tesla model three's infotainment system. There was also a use after free bug leading to an elevation of privilege on a BTU desktop, an improper access control bug leading to an elevation of privilege on windows 11 and a use after free bug leading to an elevation of privilege on a BTU desktop, and on the third and much less active day, there was a escalation of privilege via an integer overflow on windows 11, a use after free exploit on Ubuntu desktop, an elevation of privilege via improper access control on windows 11 and an elevation of privilege via use after free on windows 11. So the big targets and losers were Microsoft's teams, windows 11, and Ubuntu desktop with virtual box Firefox safari and Tesla's infotainment system.
Leo Laporte / Steve Gibson (00:45:42):
Each taking one hit a piece. Overall for this 15th anniversary event, there were a total of 21 exploitation attempts, three of which failed from a total of 17 contestants with trend micro and their zero day initiative awarding a total of $1,155,000 in poem to own prize money. So another great competition, and, you know, all of the de the details of the exploits as always for P to own are provided to those whose products fell. And here we are, where are we? We're, that's not gonna probably make it into next month's patch round. But, and, you know, windows 11 isn't even released yet still in, in dev channel mode. So wait, what, no the, the current version is you know, will, will, will be updated. Probably, well, maybe not by next month, depending upon how, you know, the nature of these problems and how quickly Microsoft's able to fix it.
Leo Laporte / Steve Gibson (00:46:56):
Okay. under the heading of sometimes they get it right. We have last Thursdays, very welcome news that the us department of justice, our DOJ has revised its policy on how federal prosecutors should charge violations under the computer fraud and abuse act, creating, get this an explicit, carve out exemption, covering good faith security research. So this is huge. What this means is that the us government is altering how vigorously it enforces a central cyber crime law, that security researchers, civil Liberty advocates and others have long argued is overly broad. And to that, I say, amen. Under the change to enforcement of this CFA, the computer fraud and abuse act, which became law back in 1986, the DOJ will amend its char, excuse me, amend its charging policy to explicitly discourage going after so-called good faith or ethical security researchers. The DOJs deputy attorney general Lisa Monaco said in a statement accompanying the revamped policy.
Leo Laporte / Steve Gibson (00:48:31):
Computer security research is a key driver of improved cyber security. The department has never been interested in prosecuting good faith, computer security research as a crime, and today's announcement promotes cybersecurity by providing clarity for good faith security researchers who root out vulnerabilities for the common good, wow. Federal prosecutors who seek to bring charges under C FAA must now first consult with a computer crime and intellectual property unit inside the DOJs criminal division. If that office recommends going forward with charges, prosecutors must then inform Monaco's team and even then may need special permission to proceed. However, you know, it's still not all clear sailing, ethical researchers who, who scour for and discover software vulnerabilities could still face prosecution under existing state laws or be sued in civil court. So this update, this updated guidance comes a little over a year after the Supreme court ruled in a major C AA case that the 1986 law does not apply when an authorized user uses data in improper ways.
Leo Laporte / Steve Gibson (00:50:10):
In that case, the court said that a Georgia police officer did not violate the hacking law, maybe some others, but not the CFAA. When he took money from an acquaintance to search a license plate database. In other words, someone paid a police officer to access the license plate database, to which the officer himself had authorized access. Even though the purpose of that specific instance of access was unwarranted. The officer was sued under the computer fraud and abuse act. And the Supreme court ultimately said, Nope, the DOJ explained that the CFAA should only apply in instances when an outside hacker or authorized user. So even an authorized user, but, you know, external actually breaks into a secure portion of an organization's network. So clearly the instance of a police officer using his authorized access for an unauthorized purpose would not be a CFAA violation as expected.
Leo Laporte / Steve Gibson (00:51:23):
The news of this updated policy was broadly welcomed among both federal cyber security of officials and the research community, Jen easterly, whose SISs director tweeted huge news, well done, team GOJ and Chris Chris Vicary a prominent cyber researcher tweeted that the new guidance will quote, hopefully improve the lives of people like me, who fear retaliation for trying to do the right thing. So, as I said, sometimes they get it right. We still have a ways to go since local government and private parties who take offense at the discovery of their own cyber failings being revealed will still be able to somewhat unjustifiably exact their revenge, but perhaps a competent defense attorney will be able to point to the changes which have just been made at the federal level as a basis for applying the same reasonable protections more locally, we can hope. Okay.
Leo Laporte / Steve Gibson (00:52:32):
So you have a fancy car or a residential or office door lock, which operates as follows your smartphone containing the locks matching app, and essentially, or effectively it's key is in your pocket. You approach your car or your homes or offices front door, and just touch the lock. The lock's capacitive sensor senses your touch. So it emits a Bluetooth, low energy, a BLE ping to query for any nearby. In this case, quick set, Kevo smart lock apps that may be nearby. The app in the phone in your pocket receives the Bluetooth low energy ping and responds. So they engage in a super crypto, triple scoop, post quantum impossible to crack handshake negotiation. And now satisfied that one of its authorized owners is indeed nearby the lock disengages to allow entry and all is happy.
Leo Laporte / Steve Gibson (00:53:55):
But now we have a different scenario. A bad guy team wants to gain entry into that smart lock, protected car or residence or office. So one of them arranges to place a Bluetooth, low energy relay near the user's phone, perhaps in an adjacent office cubicle or next to their locker while they're working out or in the coffee break room, which they frequent wherever. It doesn't matter. The other member of the team waits some discrete distance away from the car, the residents or the office that's about to be breached when the first team member messages to the second that the unsuspecting user's smartphone is within range of their Bluetooth, their remote Bluetooth relay. The second member of the team simply walks up to the locked car residence or office and touches its lock exactly. As before the lock sends out a BLE discovery, ping, which the BLE relay forwards to its matching endpoint, that distant endpoint simply and blindly rebroadcasts the ping it received, which the user smartphone picks up and acknowledges it replies.
Leo Laporte / Steve Gibson (00:55:29):
And its reply is similarly forwarded back to the BLE relay, which is now positioned near the lock. So once again, they engage in the most unbreakable bazillion cubit quantum entangled crypto that the world has ever hosted until the lock becomes satisfied that only the user smartphone can possibly be at the other end of the link. So it disengages its lock to admit the individual whom it presumes is authorized to gain access. Unfortunately, this is not fiction, except in this example for my overkill use of dip deeply entangled, quantum crypto, the point being this, oh, so simple, Bluetooth, low energy relay attack, entirely defeats any systems crypto, no matter whether it's pre or post quantum. And as I said, this is not fiction last September after successfully executing exactly this scenario in the field, the UK's NCC group notified several smart lock makers that they had a problem.
Leo Laporte / Steve Gibson (00:56:47):
Their systems were vulnerable to a simple BLE relay attack. And the NCC group notified these lock makers that they would eventually be publishing the news of this, which they did last week. The accompanying security advisory simply explains quote, an attacker with BLE SI within BLE signal range of a smartphone or key fob authorized to unlock AVO smart lock can conduct a relay attack to unlock the lock over long distances. And the problem is there is no obvious in band way of detecting and preventing this abuse, which is to say that Bluetooth low energy does not offer robust endpoint proximity protection. Various out ofAnd solutions have been considered one being for the smartphone to use its own GPS, to ascertain whether it's physically near the lock it has been paired with, but concerns over GPS's availability and speed have been a concern and local GPS jamming and spoofing technology is available.
Leo Laporte / Steve Gibson (00:58:15):
Another outand solution considered was to have the app monitoring its owner's physical movement and to disable any lock negotiation with the smartphone. Oh, sorry. If the smartphone was motionless immediately before the negotiation began, since that would never be expected in the system's normal use case, but any scenario where the user would be moving, even if many miles away would defeat such anti spoof protection. So GPS would seem to be the best if still imperfect solution, but the nature of the problem suggests that the loo the use of Bluetooth low energy convenient, though it is, was not the best idea in the first place. If our smartphones were equipped with radios, which incorporated reliable time of flight measuring capabilities, that it would be possible to obtain spoof proof data and direct physical proximity assurance, but today's smartphones are not yet that smart. So again if apparently the manufacturer scrambled around, I looked at the time at the timeline that these guys, the NCC group posted in their advisory and, you know, the, it, the, the issue got escalated up to the AC, you know, from the, the manufacturers and retailers up to the, behind the scenes designers, whose company name, you never learn where, you know, this was all actually created.
Leo Laporte / Steve Gibson (01:00:00):
And there was a lot of hand scratching going on and consternation for, you know, it to be discovered and would be published that their system was susceptible to this kind of spoofing again obviously not widespread, it would be used in a targeted attack case, but, you know, if bad guys knew that this was possible this BLE relay technology is not difficult to create and it, you know, robustly unlocks a target at some distance. So probably not such a good idea to have designed a system that could be spoofed like that. Okay. A couple of closing the loop pieces. Two of them, as I said, are bigger than usual Brian Phillips tweeted. Hi, Steve. Quick one. Don't know if you've covered this already, but do you have an alternative for actually he said unlock origin.
Leo Laporte / Steve Gibson (01:01:03):
He then created his, he, he corrected his, his typo. It was probably a, an autocorrect. He meant unblock origin on, or, or, sorry, you block. Do you have an alternative for you block origin on safari? He said recently got myself a MacBook pro and now want to use safari over Chrome. And that is to say instead of Chrome and Leo, I said suggested ad block plus no, there for safari. Good on safari. There really isn't. And that's what I wanted to ask. Yeah. Cause I knew you would know that that, you know, ad block plus was the only thing I knew as like sort of a equivalent to to you block origin. Safari changed its plugin model and gore hill did not like it and is not supporting safari. I would just use Firefox. I use it on all platforms, including the Mac and it supports hub block origin is fine and also gives you additional ations very, I hope Brian, I hope you're listing I'll I'll see if I can find, I think, I think this was an exchange via DM, so I'll I'll forward that to Brian that's, you know, there are filters ad block has always been, they're a bazillion of them.
Leo Laporte / Steve Gibson (01:02:16):
Right. Cause they're the ones that have the what do they call it? The policy for approved ADSS, you know? And I, and I really don't like to support that. Right. Yeah. I mean, I, I can't remember the one I used had three different plugins, but it's the problem is the iPhone you're really, there's nothing you can do on the iPhone. So in that case, I just use next DNS and block it at the DNS server, which is pretty effective as well as an ad block. And that blocks everything you know, at the DNS level instead of on the, on the device. Yeah. And you know, he is Mac Brook pull pro. So as you said, Firefox Firefox is great alternative. Yeah. I use Firefox on everything, including all my on my max it's iOS, that's problematic cuz you have to use red kit.
Leo Laporte / Steve Gibson (01:03:01):
Right. And so you know, then you have to block it at the source instead. So Dave Badilla asked, can you give a shout out on security? Now that Voyager one is still happily trotting along after so many years he says, and I just read, it goes into safe mode if things get out of whack. So the programmers on earth can fix it. Okay. Well, so what's interesting is that Dave sent this last week either before or more likely just exactly because things just started to go wonky with Voyager one now. Okay. Believe it or not. Leo Voyager one has a Twitter account. Of course it does. Of course it does. That's <laugh> though being 14.5 billion miles away with light requiring currently 21 hours. Wow. 34 minutes and 38 seconds to traverse the distance, you know, for a matter of convenience NASA's public relations. People have been posting on Voyager's behalf.
Leo Laporte / Steve Gibson (01:04:12):
Yes. Good thinking <laugh> yes. So last Wednesday Voyager posted on Twitter. Do you ever feel misunderstood? My team is investigating an issue with my data, even though I'm sending signals and operating normally some data readouts don't exactly match what's happening out here while they investigate. I'll keep doing my thing. <Laugh> okay. Voyager. So this made me curious about what was going on. So I dug around and found some commentary, which I've lightly edited for the podcast. It reads NASA Voyager. One space probe was launched 45 years ago and continues its journey as the first ever human made object to leave the vicinity of our solar system. Now this is, I think critical to my theory. It says it's heading out there to study the outer heliosphere and the inner stellar medium. The iconic probe has sent hugely important data back to NASA since its launch on September 5th, 1977. But now the new strange data being sent by the Voyager from the edge of the solar system has left scientists shocked since until now, there have been no significant errors reported by the probe.
Leo Laporte / Steve Gibson (01:05:51):
And I have a somewhat chilling theory for what might be going on, but I'll finish this before sharing that. So this continues since the Voyager one data is of critical importance. The engineering team is trying to solve the puzzle of mysterious data. Now being sent by the space probe NASA said in a statement quote, the inner stellar Explorer is operating normally receiving and executing commands from earth, along with gathering and returning science data. But readouts from the probes, attitude, articulation and control system, the AACS do not reflect what's actually happening on board. But what does this data received back on earth actually mean? NASA says an antenna attached to Voyager, which is pointed at earth to send data back, appears to be working, but is sending back invalid data. The AACS controls the 45 year old spacecraft's orientation among other tasks. It keeps Voyager ones, high gain antenna pointed precisely at earth, enabling it to send data home and to receive new instructions.
Leo Laporte / Steve Gibson (01:07:11):
All signs suggest the AACS is still working, but the telemetry data it's returning is invalid. For instance, the data may appear to be randomly generated or does not reflect any possible state. The AACS could be in thankfully the issue with the NASA Voyager one has not triggered the probes onboard fault protection system, the system, which is designed to keep the spacecraft in its safe mode, which maintains a state where only essential operations are carried out while giving engineers time to analyze and diagnose the issue and Voyager one's signals have not weakened, which suggests the high gain antenna indeed remains in its prescribed orientation to earth.
Leo Laporte / Steve Gibson (01:08:09):
Okay. So Leo, nothing manmade and certainly nothing sending back telemetry from such a distance has ever been this far from earth and our son. Mm. What if Voyager is approaching the maximum radius supported by the simulation? <Laugh> are you, are you saying it's gonna fall off the edge <laugh> and that's why it's falling off the edge of the simulation <laugh> it's leaving reality Leo. Well, well that's well it's reality is beginning to break down and why it appears to be returning random data. That makes no sense. Everything else we see out there appears to just be inbound radiation. Hmm. It's not interactive, right? Voyager is. Mm. Or at least it was. I like that theory. I like it. Yeah.
Leo Laporte / Steve Gibson (01:09:12):
So it'll be interesting to see what happens and whether perhaps the same thing happens to Voyager two, once it gets around the same distance away, how long will that be? It's about 2.4 billion miles, closer to earth than Voyager one. Mm. So we have some time to wait. I do have a link in the show notes. You can click on that and it will bring up the, the Voyager mission status that is live from JPL, showing their respective distances the time that they've each that, that each mission's been running and how far away they are from the sun and so forth. So they need the entry for how close to the edge of the simulation are they? Yeah, I know <laugh> yeah.
Leo Laporte / Steve Gibson (01:10:02):
I'm sure there's a simpler explanation than that, Steve, but that is the simple explanation. <Laugh> what could be simpler than you. You you've got, you've gone too far away <laugh> and you know, the simulation can't handle distances that great. It's doing everything up to that. I mean, think about that 14.5 billion that's a lot miles. Yeah. What's the cubic space of that, right? I mean, that is a ton of space to simulate, you know, with all the chemical reactions and molecules bouncing around in there that would tax any big simulator. So if you know, it makes sense that there would be some maximum radius, right. Very 2001. So I like it. I love, I love this Voyager probe, you know, it's reminiscent of the Mars rovers, right. That we were talking about for quite a while, spirit and opportunity. Okay. Voyagers. Remember how Gilligans island was an adventure that started off as a three hour tour, right?
Leo Laporte / Steve Gibson (01:11:04):
Similarly, the two voyage your spacecraft were originally intended to only study Jupiter and Saturn their moons and Saturn's rings. And for that two planet mission, they were built to last five years. That was 45 years ago. Their 45th anniversary of launch will be coming up this August and September and after their initial successes, NASA's engineers doubled the missions objectives to include two more giants, Uranus and Neptune. So now between the two two craft, they've explored four planets, 48 moons, a host of planetary magnetic fields and rings. They are each powered by a trio of radio isotope. Thermoelectric generators known as RTGS, which convert the heat generated by the radioactive decay of plutonium 2 38 into electricity. And while they are super reliable and have no moving parts, I mean just super robust electricity generators that decay itself decays over time. Right now, the Voya's power is gradually dropping at a rate of four Watts per year.
Leo Laporte / Steve Gibson (01:12:28):
This has been limiting the total number of systems that can be powered up at once. And the voyage or mission teams have been turning off more and more non-essential equipment to con to reserve power and keep these things going. But so far, none of the voyage or science instruments have been, have needed to be powered down. And the latest of the continually extending goals has been to keep both of these Vos running for at least another three years beyond 2025. Now I did not do the velocity calculations to tell us whether voyage or Ellis, whether Voyager two would be at the same end of simulation radius by 2025, when presumably we would still be watching it. But you know, if it spontaneously disappears, well, that will be because it crossed the other side of the simulation boundary. So the simulation is just the solar system.
Leo Laporte / Steve Gibson (01:13:25):
The rest of it is just pictures. It it's like a apparently is just meant to scrum it. Just backdrop <laugh> yeah. It's to give us something to scratch our heads and think about and something to aspire to. But yeah, it pretty much covers everything it needs to, you know, to keep us busy running around in our little cave. It is kind of amazing to think that there is a manmade object out there that, oh, Leo is amazing and it's alive and it's still reporting back. Yeah. Wow. 14.5 billion miles away. So that light takes 21 plus hours to get back. Wow. That is far away. And think of the accuracy of that antenna, you know, that's the dish, right? That is, think of how, I mean, it's just astonishing to me that it is able to maintain alignment on the earth at that distance.
Leo Laporte / Steve Gibson (01:14:21):
Yeah. You, I, you couldn't calculate the fraction of a degree. Oh yeah. Of, you know, off it would be. And in which case it's beam would just completely, you know, miss us really an amazing story. Alright. I like your theory as good as any <laugh> I'll go, I'll go for it. <Laugh> yeah. Yeah. We don't. And the good news is none of us have to worry about getting that far away. Right. You know, so that's right. We're all good. Yeah. We're still just, you know, well, within the simulation, you do not wanna go further than 14.5 billion miles away. <Laugh> it could be bad.
Leo Laporte / Steve Gibson (01:15:01):
You'll start speaking. Random gibberish. So Tom feller said, hi, Steve. I came across an interesting article. I ran across on quantum computing and the article was titled Q day is coming sooner than we think. Okay. As we've discussed before, I, I should mention this was published in Forbes and Forbes has had a somewhat spotty record for their presentation of technical subject matter over time. But assuming that the editors don't butcher it, the contents veracity will be a function of its author. In this case, the article's author is a guy named Arthur Herman, whose bio tells us that he's a senior fellow at the Hudson Institute, the director of the quantum Alliance initiative and the co-author of risking apocalypse, quantum computers and the us power grid. So sounds like he may know what he's talking about. Arthur is very clearly of the opinion that we should be much more worried than we currently are having read what he wrote.
Leo Laporte / Steve Gibson (01:16:11):
And even though I'm far from able to render any opinion on the subject, I know that our listeners will find this as fascinating as I did. So once again, I've edited what Forbes published so that it better fits our higher end audience. Arthur said Q day is the term some experts use to describe when large scale quantum computers are able to factor. And he said factories. And I thought, well, I don't know. Maybe he does not quite know what he's talking about, but anyway, I fixed it to factor or maybe factorized is just, you know, British or something. I don't know the large prime numbers that underlie our public encryption systems, such as the ones that are supposed to protect our bank accounts, financial markets, and most vital infrastructure. And this is where he's tying it into the power grid saying that, eh, power grid may not be safe if, you know, if you can break crypto, I'm sure he is right about that.
Leo Laporte / Steve Gibson (01:17:12):
He says, that's a feat. That's all but impossible for even the fastest super computers, but which the unique features of quantum computers, which I I've looked at several things he's written. And he certainly understands this using the physics of super positioning and entanglement will be able to deliver. There's a growing consensus that this quantum threat is real. There's no agreement on how long it will take before a quantum computer has the 4,000 or so stable qubits. It will need to meet the requirements of Shore's algorithm for cracking those encryption systems. But it turns out there's a different way to do this than using shore, which we'll get to here in a second. He says, for example, it would take a classical computer 300 trillion years to crack an RSA 20, 48 bit encryption key. A quantum computer can do the same job in just 10 seconds with 4,099, stable qubits again, stability. So the count and stability are two important criteria he says, but getting to that number is the main problem. Quantum computer engineers face since the stability or coherence of qubits lasts for only microseconds. And again, we need 10 seconds of stability from 4,099, stable qubits. He says today's most entangled computer Google's bristle cone has just 72 stable qubits.
Leo Laporte / Steve Gibson (01:19:09):
Nonetheless. He says, I have been arguing for the past four years, including in this column, that Q day is likely to come sooner than even quantum scientists predict. And that the time to get ready to protect our vulnerable data and networks is now others prefer to procrastinate, citing experts who say that a threat is at least a decade or more away. The fact that the national Institute of science and technology N won't have its quantum re resistant algorithm standards ready until 2024 and expects the rollout to take another five to 15 years has helped to encourage complacency disguised as confidence, but new developments in quantum science suggest that this complacency may be misplaced. So called quantum Ennis, like the one Canada based DWA systems Inc uses are able to calculate the lowest energy level between the qubits different states of entanglement, which equates to the optimal solution.
Leo Laporte / Steve Gibson (01:20:23):
These machines have proven their worth in solving optimization problems that usually stump classical computers. As I explained, he wrote in a previous column, he says, not surprisingly scientists have been quietly finding ways to turn factorization into an optimization problem. Thus bypassing shores algorithm, the paradigm for discussing quantum DEC description since the 1990s. And of course, which we talked about last week in 2019 scientific papers emerged that showed how to do this, including factoring integers, using noisy qubits I E swarms of quantum bits, that aren't perfectly entangled the way a large scale computer requires. In other words, no longer requiring stable qubits. One was authored by Chinese scientists who found a way to factor a large number using only 89 noisy qubits. They then showed it's possible to factor an RSA 7 68 bit private key, which is the current factorization record accom accomplished using classical computers with 147,454 noisy qubits, a fraction of the millions of noisy qubits.
Leo Laporte / Steve Gibson (01:22:07):
A large quantum computer would need to reach the 4,000 stable Qubit threshold and within reach of the architecture of an kneeler like DWA systems. Also in 2019, a pair of Google researchers and the Royal Institute of technology at Stockholm published a paper showing how to crack 20, 28 bit RSA integers in eight hours using 20 million noisy qubits. Given the fact that 2012 scientists that, that in, in 2012 scientists speculated, it would take 1 billion qubits to perform this feat. It will likely not long before researchers show they can get there with a lot fewer than Google's 20 million noisy qubits. And sure enough, in 2023, Chinese researchers found a way to use the DWA quantum computer to factor large integers, completely bypassing shores algorithm. Thus they concluded post quantum cryptography should consider future the potential of the DWA quantum computer for deciphering the RSA crypto system in the future.
Leo Laporte / Steve Gibson (01:23:39):
In effect Arthur Wrights. These researchers found a way to turn decryption using quantum technology into a straightforward process on a timeline much shorter than 10 years, perhaps four to five years is more likely. This was what Chinese scientists were openly publishing. He writes, we don't know what's happening behind the scenes, but we can bet if there's a shortcut to achieve what a large scale quantum computer can do using a kneeling technology, their military and intelligence services will wanna find out all of this should change the timetable for Q day. And for our strategic calculations, not only is quantum based decryption coming our way sooner, but thanks to a kneeling, this code cracking feature will be more accessible to other machines than the hugely expensive, large scale computers, Google, Microsoft, and others are working on, which in turn puts the capability within reach of small state or even non-state actors. He finishes why gamble with the quantum future. A kneeling technology makes becoming quantum ready, more important and getting started now more imperative than ever. So, okay, I'm gonna take his word for it. I don't, I can't argue the pros and cons. I'm programming an assembler on a machine with 32 or 64 bit bits, not qubits binary bits, but wow. Interesting stuff. And the good news is I'm sure that the academics and those who are deciding these things are aware that this other, these other breakthroughs are occurring.
Leo Laporte / Steve Gibson (01:25:45):
We should know. Yes. Taking a sip of water will be a breakthrough. We're gonna go dis discontinue our show in just a bit. But first <laugh> word from that Foundry, I've got a game changing, open source security tool for you. And even though it sounds like a delicious pasta dinner, it's not, it's open Zeti every week. Steve guides us through the minefield, the minefield of ransomware, cyber espionage hacking. And it all, you know, I mean at its root is being driven because it's so difficult to secure networks, but networks are insecure. That's their nature period. That's why you need open ZD. It gives your applications, superpowers and, and encryption, private DNS, dark and outbound only and host anywhere. It's. This is the ultimate zero trust foundation. Stop Dedos attacks, brute force credential, stuffing CVE, or zero day exploits, BGP, hijacks, fishing, and more use open Zeti open ZD O P E N Z.
Leo Laporte / Steve Gibson (01:27:01):
I T. I to isolate your applications and data, making the security of the network completely irrelevant. It's zero trust done right open Zeti created and maintained by net. Foundry provides an open source free and easy way for the world to embed zero trust, networking into anything. It provides everything you need to spin up a truly private zero trust overlay network in minutes across anything, you can do it directly in your app on any device, on any cloud built on principles of extensibility, flexibility, and scalability. You know, we, I think we started talking about Hitachi. What is more than 10 year him hamachi I mean, remember hamachi more than, yeah. More than 10 years ago. The idea of having this network overlay is not new, but the idea of a zero trust overlay network is very exciting. With open CD, you can isolate your absence systems.
Leo Laporte / Steve Gibson (01:27:58):
So they're just impenetrable. They cannot be subject to external network level attacks from malicious actors while protecting from internal or even OS networks like being a immune to network side channel attacks like fishing. It's it's quite literally zero trust and zero trust for all networks, internal, external, no matter where the traffic originates no need for expensive and risky, reactive patching agnostic design patterns ensure you only need commodity internet without bound ports, without needing networking engineering skills. To implement it, say goodbye to complex firewall rules, inbound ports, public DNS, static network, access controls, VPNs. All of that perimeter protection goes poof. You don't need it. Open CD is port knocking on steroids. And I thought you'd like that. Steve they've recently embedded private zero trust networking directly into Prometheus that's. The second most popular after Kubernetes cloud native compute foundation project opens ed is poured directly into Prometheus, but you don't have to use it that way.
Leo Laporte / Steve Gibson (01:29:06):
You can eliminate the tug of war between developers and security. We've we've talked so much about zero trust. I know it's on your mind, but it's a journey. So you gotta start wherever you need to start based on your priorities. And that's why open Zei is such a great choice. Numerous SDKs, numerous tunneling apps for all the popular OSS edge routers in cloud marketplaces. You don't even have to host it. If you don't wanna host your own open, Zeti use the Net Foundry, SAS. They even have free forever tier with up to 10 end points. Just think about some of the most recent CVS like spring for shell or windows that windows RRP C RCE. You know, the solution, you know, Microsoft will say is, is cloud inbound ports with open Zeti. You don't have inbound ports at all, nothing to cloud it's all zero trust.
Leo Laporte / Steve Gibson (01:29:58):
It's all secure. I want you to know more. So go to netfoundry.io/twitt netfoundry.io/twit. Get some free swag. I have my open ZD mug, my open ZDT shirt, my open ZD stickers for my laptop. You can get those two netfoundry.io/twit. Get your free swag and your free tier right now. Open Zeti is a great idea. Net Foundry is a place to find out more netfoundry.io/twitt. It's better than pasta it's it's it's open Zeti okay. Port knocking on steroids. I love that. That's good. Yeah. So, so unfortunately I think disti nude is the best way to say that I've been looking at that since dis nude, discontinue disti nude, discontinue nude dis continued. So last Thursday, advanced Intel is the name of this organization. ADV I NT E l.io is their domain advanced Intel's yellowy bogus Ky tweeted today. The official website of Conti ransomware was shut down.
Leo Laporte / Steve Gibson (01:31:18):
This is last Thursday making the end of this notorious crime group marking the end of this notorious crime group. He says it is truly a historic day in the intelligence community. And the day after that last Friday, they published their report about exactly what happened. There's so much more to it than just someone turned the site off that I felt certain our listeners would find the details fascinating and their report is titled don't blame me. Although I did perpetuate it disti nude, the end of CTI's brand marks new chapter for cyber crime landscape and the top of their report, teases reading from the negotiations site, chat rooms, messengers to servers and proxy hosts. The KTI brand, not the organization itself is shutting down. How does this, how, oh, he says, I'm sorry. However, this does not mean that the threat actors themselves are retiring.
Leo Laporte / Steve Gibson (01:32:24):
Okay. What does that, what does it mean? Advanced Intel apparently rushed out their report. It contains some typos, misspelling and grammatical awkwardness, and they may not be native English speakers. So in order to share, in order to share it with the podcast, I've cleaned it up a bit, but otherwise it remains what they wrote. And I think everyone's gonna find it interesting. They said on May 19th, the admin panel of the KTI ransomware gangs official website, KTI news was shut down. The negotiation service site was also down while the rest of the infrastructure from chat rooms to messengers and from servers to proxy hosts was going through a massive reset KTI news. A shame blog is the last beacon of the group's public operation, where victim data was being published. It also served as a media tool that Kati used for their endless public statements.
Leo Laporte / Steve Gibson (01:33:25):
One of which led to the gangs downfall. We'll get to that in a minute. I have a snapshot of it later in the show notes, they said this publicity function of the blog is still technically active. And this activity as shown below is highly strategized. At the time of this publication May 20th, 2022 KTI was even uploading anti Americanist hate speech, claiming the USA to be a cancer on the body of the earth. This however only manifests that the website became an empty shell at the same time, the crucial operational function of KTI news, which was to upload new data in order to intimidate victims to pay is defunct as all the infrastructure related to negotiations, data uploads and hosting of stolen data was shut down.
Leo Laporte / Steve Gibson (01:34:26):
Okay? So, and this shutdown, they wrote highlights a simple truth that has been evident for the KTI leadership. Since early spring of this year, the group can no longer sufficiently support and obtain extortion. The blogs key and only valid purpose is to leak new data sets. And this operation is now gone. This was not a spontaneous decision. They write instead, it was a calculated move signs of which were evidence since late April two weeks ago, on May 6th, advanced Intel explained that the KTI brand and not the organization itself was in the process of the final shutdown as of May 19th, 2022. Our exclusive source intelligence confirms that today cantis of is CTI's official date of death. In this retrospective analysis, we will not only take an in-depth look into the reasons behind the KTI shutdown, but perhaps most importantly, assess and project the future of a new threat landscape that is already on the horizon.
Leo Laporte / Steve Gibson (01:35:44):
But first we need to review how KTI prepared for its own demise and how this group notable for its soft sophistry continued to utilize information warfare techniques to orchestrate the shutdown until its final days in order to ensure the legacy of its surviving members. They explained shutting down ransomware's iconic criminal brand is a long and complicated venture. A notorious and prolific threat group cannot simply turn off its servers only to pop back up the following week with a new name and logo design, even a whisper of novel threat group activity. Following the announcement of CTI's demise would likely spark immediate accusations of poorly executed identity theft at best immediate comparisons between the two would, would permanently leave the new group in CTI's ghostly shadow, the collective that fell and the one which emerged. And I'll note that, you know, we've seen and commented on exactly this pre with previous ransomware operations.
Leo Laporte / Steve Gibson (01:37:01):
So these guys said RAL dark side and countless other collectives attempted the disappearing act. The simple approach failed miserably as what was one of the predominant ransomware groups active at the time. KTI realized that an element of performativity they wrote would need to be involved where other groups had been attempting a grand stunt with smoke and mirrors. KTI would try a slide of hand. KTI would not be itself without its project front man, an individual operating under the alias REEV AKA gangster besides being a talented coder. They were behind that. This REEV was behind the original REU payload. This person was an outstanding, an outstanding organizer. It was REEV who set the foundation for CTI's dominance in the cyber crime business by creating an organizational system based on skill teamwork, clear business processes, hierarchy, and clear foresight. It's not surprising that Russia was the first who saw CTI's structural challenges due to the group's public allegiance to Russia.
Leo Laporte / Steve Gibson (01:38:25):
In the first days of the Russian invasion into Ukraine, CTI was unable to be paid since February. Almost no payments were given to the group while CTI's locker. You know, the, the, the slang for malware became highly detectable and was rarely being deployed. The only possible decision was to rebrand for over two months. KTI collective has been silently creating subdivisions that began operations before the start of the shutdown process. These subgroups either utilized existing KTI, alter egos and locker malware, or took the opportunity to create new ones. This decision was convenient for Conti as they already had a couple of subsidiaries operating under different names, Kara Kurt, black bite, and black BAA, the rebranded version of Conti the monster splitting into pieces, but still very much alive ensured that whatever form CTI's ex affiliates chose to take, they would emerge into the public eye before news of CTI's obsolescence could spread thus controlling the narrative around the dis the dissolution, as well as significantly complicating, any future threat attribution.
Leo Laporte / Steve Gibson (01:40:04):
And then they wrote, this is where the plans for what was left of KTI became increasingly complex in order to hide the fact that KTI was now dispersed in operating via smaller, more novel brands. The former affiliates of the gang had to now convincingly simulate the actions of a dead brand CTI's remaining infrastructure operated like an army preparing for an ambush lingering actors were left to keep their fires lit visible from behind enemy lines. Meanwhile, hidden from view CTI's most skilled agents were instead laid low in a nearby encampment, biting their time while watching their great and empty camp send out smoke signals, parti emulating the movements of an active group. KTI continued to publish documents stolen from victims. Most likely targets hit earlier with attacks and lined up in a sort of queue waiting for public release and campaigned hard for themselves on criminal forums, their public persona boasted, a strong and enduring foundation, even one that was willing to further expand the group's operations from the perspective of CTI's posting history, the group appeared to be as strong as ever.
Leo Laporte / Steve Gibson (01:41:30):
Okay. Then they shared a snapshot of a long and quite rambling chest thumping post from March 30th, where a county representative talks up the group's successes, even seeking to recruit new affiliates, all apparently just smoke screen. Then they continue. However, in order to pull off their ultimate tactical maneuver, the agents left behind to operate from within CTI's massive empty shell. Now had to ensure that their antics would be, would successfully lure attention away from their escaping comrades to do this. They had to be certain that they left bait big enough to satisfy all of the opposing forces stretching. This analogy. Conti would have to perform a grand finale one big enough to live up to the group's name. And finally, on May 8th Costa Rican president Rodrigo Chavez declared a national emergency as the result of a major cyber attack executed by the KTI ransomware gang. The massive attack which took place against multiple Costa Rican government agencies seems almost like a last ditch effort by the group to squeeze a few more drops of riches from foreign government funds.
Leo Laporte / Steve Gibson (01:42:52):
However, advanced Intel's unique adversarial visibility and intelligence findings led to what was in fact, the opposite conclusion. The only goal Conti had for this final attack on Costa Rica was to use the platform as a tool to publicly perform their own death. And subsequent rebirth, advanced Intel has been tracking the preparations for this attack since April 14th days before even the initial compromise. Our prevention alert was sent on April 15th, three days before the first incident compromising Costa Rica's ministry of finance occurred their report. Oh, and, and so, okay. So, so they said that now then their report links to a tweet thread in Spanish, but it appears to be dated from the 18th, but they then provide a screenshot which indeed appears to substantiate a three day early warning of an impending attack. So they explain in our pre and post attack investigation, we have found three things first, the agenda to conduct the attack on Costa Rica for the purpose of publicly, instead of ransom for, oh, I'm sorry.
Leo Laporte / Steve Gibson (01:44:23):
For the purpose of publicity, instead of ransom was declared internally by the KTI leadership. Second internal communications between group members suggested that the requested ransom payment was far below 1 million us dollars, despite unverified claims of the ransom being 10 million us dollars followed by CTI's own claims that the sum was 20 million, a low demand such as this made to a state entity, no less was only made with the knowledge that the group would never see payment for the ransom either way, you know, because their payment pipeline had been completely foreclosed on by the sanctions against Russia and by their pro pronounced affiliation with Russia. And third KTI was very vocal about the attack, constantly adding new political statements. And, you know, that's this kind of junk that we talked about last week. They say the attack on Costa Rica indeed brought Conti into the spotlight and helped them to maintain the illusion of life for just a bit longer while the real restructuring had already taken place while KTI had been busy with its diversion tactics, other brands such as Kara, Kurt, black bite, and numerous other groups, which existed as extensions of Conti, but without taking the group's name were extremely operationally active.
Leo Laporte / Steve Gibson (01:45:56):
Although working in silence, working concurrently with them, talented infiltration specialists who are in, who are ultimately the backbone of CTI's gang were also more active than ever forming alliances with black cat AVOs locker hive, hello, kitty five hands and a whole other cadre of ransomware groups. These pen testers maintain personal loyalty to the people who created Conti, but ultimately continued their work with other gangs in order to fully shed CTI's name and image. The situation presents the first and foremost reason for CTI's timely end toxic branding. Indeed the first two months of 2022 left a major mark on the KTI name while there's no tangible evidence to suggest that the well known KTI leaks had any impact on the group's operations, the event, which provoked the leak CTI's claim to support the Russian government seems to have been the fatal blow for the group despite being revoked almost immediately.
Leo Laporte / Steve Gibson (01:47:12):
And we noted that at the time re remember that KTI posted the KTI team is officially announcing a full support of Russian government. If anybody will decide to organize a cyber attack or any war activities against Russia, we are going to use all our all possible resources to strike back at the critical infrastructures of an enemy. That statement had several key consequences advanced Intel wrote all of which deeply reshaped the environment KTI was operating within first, by engaging in political discourse, KTI broke the first unspoken rule of the Russian speaking cyber crime community, which is not to intervene in state matters in advanced Intel's public blog regarding Re's ultimate take down by the Russian government. Advanced Intel provided an in-depth analysis of this unspoken agreement, making case studies of the two most notable groups to break it Avadon and Don and Reval with the ongoing Russian invasion of Ukraine.
Leo Laporte / Steve Gibson (01:48:25):
It may be very plausible that Russia's state security apparatus is attempting to exert governmental control over its cyberspace, even taking down groups that appear to have been allies, but who exhibited undue independence with their actions? Advanced Intel has seen internal communication of the Conti leadership suggesting that the Russian FSB had been pressuring the group. And even though non-factor evidence was involved, the Regal scenario may have simply repeated itself with Conti the group's brand becoming a target for Russian authorities despite their pledge loyalties. Second con's allegiance to the Russian invasion of Ukraine provoked internal conflict and brought shame on the Conti name from members who were either ethnically Ukrainian or were Russian, but supported Ukraine, or simply wanted to maintain an anti-war ethic. Considering that one of these members decided to betray the gang and leak private Kante chat logs. We talked about that too. Not long after the conflict began, this illustrated the final nail in CTI's self-made coffin, the third and most important factor by pledging their allegiance to the Russian government KTI as a brand became associated with a Russian state, a state that is currently undergoing extreme sanctions in the eyes of the state.
Leo Laporte / Steve Gibson (01:49:59):
Each ransom payment, going to Conti may have potentially gone to an individual under sanction, turning simple data extortion into a violation of OAC regulation and sanction policies against Russia. This liability came to a head on May 6th when the us state department offered rewards up to 10 million us dollars for information that led to the take down of the KTI group, as a result of these limitations, KTI had essentially cut itself off from the main source of income. They wrote our sensitive source, intelligent shows that many victims were prohibited from paying ransom to KTI other victims and companies who would've negotiated. Ransomware payments were more, were more ready to risk the financial damage of not paying the ransom than they were to make payments to a pro Russian state sanctioned entity. As advanced Intel previously stated the end of the Conti brand does not equal the end of KTI as an organization, as seen with the Costa Rica case.
Leo Laporte / Steve Gibson (01:51:07):
KTI has been carefully planning its rebranding for several months, preparing a comprehensive strategy to execute it. The strategy is based on two pillars. First KTI is adopting a network organizational structure, more horizontal and decentralized than the previously rigid KTI hierarchy. This structure will be a coalition of several equal subdivisions, some of which will be independent and some existing within another ransomware collective. However, they will all be United by internal loyalty to both each other and the KTE leadership, especially REEV at this point, this network includes the following groups, the first type being autonomous, no LA no malware locker involved, pure data stealing that's car, Kurt, black Basta and black bite. The second type being semi-autonomous acting as KLO collective affiliates within other collectives in order to use their malware locker, that's a, a V or a five, maybe black cat hive, hello, kitty five hands and a AVOs locker.
Leo Laporte / Steve Gibson (01:52:29):
The third type being independent affiliates working individually, but keeping their loyalty to the organization. And finally, the fourth type being mergers and acquisitions where KTI leadership infiltrates a preexisting minor brand and consumes it entirely keeping the small brand name in place. The small grapes, the small group's leader loses their independence, but receives a massive influx of manpower while KTI obtains obtains a new subsidiary group. This is different from ransomware as a service since this network, at least at the time of writing does not seem to be accepting new members as part of its structure. Moreover, unlike ransomware as a service, this model seems to value operations. Being executed in an organized team led manner. Finally, unlike ransomware as a service, all the members know each other very well personally, and are able to leverage these personal connections and the loyalty they bring. And I implied in that of course, would be some protection against us based bounties against their members.
Leo Laporte / Steve Gibson (01:53:41):
If they're, you know, maintain a loyal cohesive group, you know, one turns one in and they they're subjecting themselves to similar reprisal. And finally they finish this model is more flexible and adaptive than the previous KTI hierarchy while also being more secure and resilient than ransomware as a service. And finally, the other major development for this new ransomware model is the transition from, and this is really interesting from data encryption to data exfiltration covered extensive covered extensively by advanced Intel in our analysis of care, Curt and black bite. In a nutshell, relying on pure data, exfiltration maintains most major benefits of a data encryption operation while avoiding the issues of a locker together. Most likely this will become the most important outcome of CTI's rebrand. The actors that formed and worked under CTI name have not and will not cease their forward movement within the threat landscape.
Leo Laporte / Steve Gibson (01:54:55):
Their impact will simply leave a different shape. So to our listeners, if anyone in your cyber sphere announces that Conti has shut down and disbanded, well, now we know better. It appears that earlier this year, as a consequence of, of, you know, you know, we we've talked previously about the entire reason that ransomware has, has come into existence whether it be encrypting malware or exfiltrating and holding that data for ransom, it's the ability to get paid, thanks to cryptocurrency, which has, you know, made that practical from a, from an underworld standpoint, but the sanctions against Russia, CTI's original proclamation that they were standing with with, with Russia, essentially cut them off from extra Russian payment of cryptocurrency into them. And that set them on a multi month course to, to basically killed KTI off while continuing to function as a viable ransomware organization, learning from the mistakes they'd made before, changing their structure, and probably apparently changing the nature of, you know, what they do maliciously.
Leo Laporte / Steve Gibson (01:56:22):
Well, they're not fooling anyone. Okay. That's the truth we know better. We know better. Thanks to you, Steve Gibson and this fabulous security now program every Tuesday, about one 30 Pacific four 30 Eastern, 2030 UTC, you could turn in at live, do TWI, do TV and watch it happen. Audio and video available at that site. You could chat while you're watching@ircdottwi.tv or in our club, TWI discord after the fact on demand versions are available from a variety of places. Steve has two unique versions of the show. He has a 16 kilobit audio, which he's been doing for years for the bandwidth impaired. That's the smallest audio form of the show. There's an even smaller version, the transcripts, which are plain text, and you can read along they're well done because they're written by an actual human being. <Laugh> a court reporter who can keep up with Steve.
Leo Laporte / Steve Gibson (01:57:17):
Thank you, Elaine. Those are available@grc.com that's Steve's website while you're there pick up a copy of oh, he also has a 64 kilobit audio version, by the way, while you're there, pick up a copy of spin, right? The world's best mass storage, recovery and maintenance utility version six is current, but soon 6.1 is gonna come out. If you buy today, you'll get a copy of 6.1. The minute it's available, you also can participate in the development of 6.1 leave messages for Steve at grc.com/feedback or on his Twitter page. He's at SG GRC and he takes DMS. So you can ask him a question in his direct messages as well. We have audio and video of the show at our website, TWI TV slash SN. There's also a YouTube channel devoted to Security Now the video, and of course you can also subscribe. In fact, that's probably the best thing to do in your favorite podcast application, pick the audio or video version and you'll get it automatically every Tuesday evening after the show's over. So you can listen@yourleisuregrc.com that's Steve's place, twi.tv. That's our place. We will see you back here at this place next Tuesday. Thanks Steve. Righto. Bye.
Mikah Sargent (01:58:33):
If you are looking for a midweek update on the weeks tech news, I gotta tell you, you gotta check out tech news weekly. See it's all kind of built in there with the title. You get to learn about the news in tech that matters every Thursday, Jason, how and I talk to the people making and breaking the tech news, get their insights and their interesting stories. It's a great show to check out twit.tv/tnw. Security.
... (01:59:00):
Now.