Security Now Episode 848 Transcript
Leo Laporte (00:00:00):
It's time for Security Now, Steve Gibson is here. We're gonna talk sci-fi recommendations, smartwatches for children that are really super smart, spies on your kids' wrists. Bugs in Mozilla's signature verification and a whole lot more than a new tool, which has revealed a flaw and pretty much every browser on the market. Xsinator it's all coming up next on Security Now.
Steve Gibson (00:00:27):
Podcasts you love, from people you trust. This is TWiT.
Leo Laporte (00:00:31):
This is Security Now with Steve Gibson episode 848 recorded December 7th, 2021. Xsinator. Security Now is brought to you by worldwide technology and Fort net. When was the last time your company updated your security strategy are your business assets protected, WWT, combined strategy and execution to secure your organization and drive business outcomes. Visit wwt.com/twit To get started. And by ITProTV start or advance your it career with the wonderful instructors at ITProTV, visit it pro.tv/security. Now for an additional 30% off all consumer subscriptions for the lifetime of your active subscription. Just use the code S N 30 at checkout and by bit warden, get the password manager that offers a robust and cost effective solution that can drastically increase your chances of staying safe. Online. Get started with a free trial of a teams or enterprise plan or get started for free across devices as an individual user at bitwarden.com/twit. It's time for Security Now the show you wait all week for here. They are the Security Now guys, and Steve Gibson. Welcome. It's good to see you, the guy, the man in charge of Security Now.
Steve Gibson (00:02:04):
Leo, great to be with you as we plow into December plowing I tell you plowing. Yes, yes. This is the first Tuesday of the month, since the month began on Wednesday last Wednesday. So this is, as I've mentioned before, the latest in the month that we can have patch Tuesday, that'll be next Tuesday. So we'll wait to see what happens. The hope is that we're gonna get printing back for windows. <Laugh> we've been hoping that for a, a while haven't we <laugh>, it'd be a real Christmas present. Yes. Oh man. Yes, Virginia, someday. You, you can print. Yes. so a, a group of five German researchers took a look, a new look, a different kind of look at, at a means by which a site we're visiting can work behind our backs. Using deliberately created features of JavaScript and the state of the art of webpages, the so-called document object model to infer privacy, violating things about us and our relationships to other websites.
Steve Gibson (00:03:26):
So today's topic is the site they created, Xsinator. XS as in cross site, X, X, S I N a T O R. And anybody who wants to jump ahead can go to xsinator.com and click the test, my browser button and within a minute or so you will see a whole bunch of red, which are specific, says this thing runs, I think it's 37 or 38. It's. They start numbering at zero, bless their hearts. So I, I don't remember whether it's 37 or 35 and you add one for the zero based counting, but you'll see all of the places where their test has verified that the browser you're using can fall to some of these tests. We're going talk about that in some detail at the end. But Tavis Ormandi has been busy. He found a bug in a bad bug in Mozilla's NSS. That's their, their own. I, I assume stands for Netscape privacy or Netscape security suite, cuz it's always been part of the Firefox. And then they, they split it out a very nice and actually widely used open source security library. He found a problem, a bad problem in their signature. We're also gonna look at the horrifying lack of security in something that I didn't know existed. Leo smart watches for children. Oh yeah. Oh yeah. Oh, bad idea. It's not a smart watches.
Leo Laporte (00:05:16):
We were talking about this on MacBreak Weekly, the life 360 app that you put on your phone to track your kids and your family members, just a horrific privacy nightmare.
Steve Gibson (00:05:27):
Well, and wait till you just wait till you hear how bad these things are. We also have another six VPN services have been banned by Russia and we got, we get to say Ross con Mondor. Many times we also have Microsoft happily softening the glue between Windows 11 and Edge, which so we have a bit of good news there, but bad guys have found a new way of slipping malware into our machines. There's a botnet using the bit Cho the Bitcoin blockchain as its backup communications medium. We have HP with more than 150 printer models in dire need of firmware updates, doubtless affecting some of our listeners. I'm gonna then briefly touch on a, a little sci-fi note and update our listeners about spin rights. Some an interesting thinW will be happening, maybe not tonight, but tomorrow for sure. Like such, which is to say as soon as I'm done with a podcast that have recovered and then we're gonna look at this new research into an entirely new class of cross site privacy breaches, which affect every browser, mobile and desktop. And as I said, a test, everyone can run. And I got a picture that was posted in the spin ride development news group yesterday that I immediately knew I had to share. So, you know, Lori looked at it and said, is that yours? I was like, no, honey, that's not, but it's, it's a dedicated tester. <Laugh>
Leo Laporte (00:07:09):
All right. We're gonna take a little break before we do though. I wanna actually make a pretty special announcement and I wanted to get you involved in this, Steve as well. I, I don't know if you know of a company you probably don't called RMC, the resource management concepts. They help manage fleets and security for government agencies like the air force and the department of Homeland security and the Navy and other commercial entities. They're a really cool company. And we got an email. I was a few weeks ago from David Hickman over there, he's a VP at at RMC saying he would like to sign up. He says, he's a big fan of Security Now and really appreciates the information he gets for his business. He would like to sign up. He said for Club TWiT for his employees and they have purchased, I, I don't know if people know this, we have corporate membership plans, they purchased 300 licenses for their company and I, we were just so blown away and so impressed.
Leo Laporte (00:08:11):
And David, I just wanted to thank you and let Steve know about it because it really is because of you, Steve and the, and the really valuable information you pass along that their security and it professionals wanted this information and, and his company wanted to give them security. Now basically it's you know, a gift for the holidays, so, wow. Isn't that amazing? So David, hello to everybody research management concepts. Guess what, you're gonna be listening to a lot of this guy in next year, <laugh> and welcome to Club TWiT and for anybody who wants to know more, we really love the corporate memberships. If you go to twit.tv/clubtwit, it's the ad free versions of all of our shows, but you'll see, we do have a, a corporate plan and it gives you a significant discount. You can get as many seats as you want.
Leo Laporte (00:08:58):
If you go to twi.tv/clubtwit it starts with five seats. So it can be a small business and it can go up from there. But David bought 300 copies of our show ad free because he, he really appreciates it and we appreciate you David, and every research management resource management concepts great company RMC, and I think they're gonna be even smarter. Thanks. Thanks to you, Steve. So we just wanted to say hello and welcome. Very cool to the club our show today let's, let's, let's get some ads in and the people of resource management concepts will not be seeing these ads, but the rest of you will, our show today brought to you by worldwide technology. And we are also big fans of WWT and forte net. And I know a name, you know, very well.
Leo Laporte (00:09:50):
Steve WWT offers security solutions and services to protect your business. Attackers are always updating their strategies. This is one of the things that's scary. You know, the zero day, that means something has come down the pike. No one's seen before. Are you updating your security practices because that same old strategy you used last week, isn't gonna work next week. WWT helps your organization prepare and combat next generation threats, and what a great company to partner with a company that has a vision, the services, the capabilities needed to deliver security controls to reduce the risk for your organization. WWT does all of that. Their team provides resources and platforms that make it possible over three decades of experience. They have a proven track record to truly help you succeed. We know it because Lisa and I went out in March of last year, gosh, seems like a <laugh> an eon ago, right before COVID to visit the advanced technology center.
Leo Laporte (00:10:48):
And we were just blown away. Some of the case studies you'll find at the WWT website really tell you what WWT can do. They worked with a large healthcare organization. The, the healthcare organization was as many are moving to a certified electronic health record technology, and they wanted a security risk assessment by the way, good idea, prudent thing to do WW T's consultants came in, they used their expert knowledge state of the art tools analysis to complete assessment. They found that 90% of the vulnerabilities that there were many findings, but this is one of them that everybody should listen to. 90% of the vulnerabilities that were found could be fixed just by putting in a comprehensive systematic approach for patching. Well, you knew that, and then WWT came back cuz you stay with you forever. They really are there to help you to do training and repetition with the staff so that they would know how to, you know, what the best practices were.
Leo Laporte (00:11:46):
They would know how to be secure in this healthcare system. They worked with a very well known, I won't say the name retail bank. They wanted an infrastructure that could survive a catastrophic cybersecurity event. I think that's what everybody wants these days. WWT helped them do that. They also, and this is almost just a kind of a side benefit. They also reduced system outages by 40% <laugh> and then they did infrastructure. Your automation also very useful, which saved the bank 48%. So in effect, they saved the bank so much money that paid for itself. WWT can do a lot to help your security posture, risk management, endpoint, security, network, security identity, and access management, cloud security. They work on every front. And as I mentioned, training as well and security assessments, seeing how WWT and Fornet can protect your business assets and intellectual property with a holistic security approach. And as always, and I always emphasize this WWT understands your business is not security. Your business is your business and everything WWT does is about making your business more successful. They wanna make sure they're, they're, they're exactly congruent with your business goals. That's really important and they know business so they can do it. Wwt.Com/twit, let worldwide technology help you improve your security posture, improve your performance, wwt.com/twit worldwide technology make a new world happen. And we thank you so much for supporting Security Now. All right, Steve, let me cue up the picture
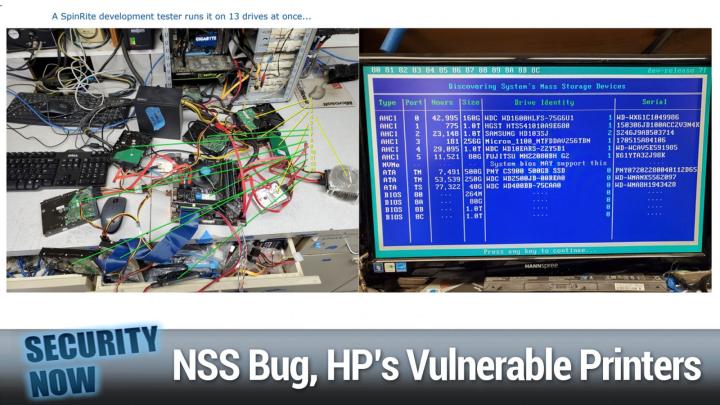
Steve Gibson (00:13:25):
Of the way. Okay. So this is not something that we expect all of our testers to do. Let me just make that clear. Most people just, you know, boot a machine they have with a USB thumb drive and run, run the development release to see how it does and then report their results. This individual is clearly a technician or of some sort. If you look Leah, if you scroll down to the top of the next page, you'll see the, the spin right screen that he was
Leo Laporte (00:14:02):
Seeing, look at all the different devices.
Steve Gibson (00:14:04):
Yeah. So he's got 13 drives hooked up to this system. And there there's a little extra goodies that, that users will never see, which are here for development. You can see along the top, it says 80, 81, 82, 83, those are up up through eight Charlie. Those are the bios designations and they're white because Spinrite was able to figure out which one of the drive that it has hardware access to the bios is referring to. There's no UN unfortunately in the bios, there's no way to, to associate bios designations with, with physical drive designations yet spin, right. Has to, so that it's able not to confuse users by showing them a drive that the bio sees and that it sees. So that, so one of the challenges has been to, to create this association between the bios designations and the, and the, and the drives that Spinrite has, has direct hardware access to.
Steve Gibson (00:15:14):
So you can see, for example, down at the bottom is, is 80 the fourth from the bottom. So that's that, that would be the drive that he booted from a little, 264 megabyte thumb drive. And then there's eight, a eight B and eight C, which are other drives, which are accessible only to the bios and not to spin. Right. But anyways oh, and then, then also there's a little cyan column to the, on, down the right hand edge of the drive identity that shows how many seconds it took for spin, right? To identify and qualify that drive for operation. It performs a whole bunch of confidence testing, you know, gets the name, the serial number, all the smart data. It also then performs a series of reads and rights in order to verify that it's able to do so. When we were having, I R Q problems, some, some of those tests would take a long time.
Steve Gibson (00:16:12):
And so they'd sometimes say, you know, 26 seconds or something. So that was another little clue that, that, that would allow us to know what was going on. But in that, in that first picture, we see a little, it looks like a mini ITX form factor, other board, and drives, just spread all over the table. He actually numbered them. You can see a little yellow column of numbers on the upper, on that first image N labeled one through 13. And then he drew lines to show where all of these 13 drives are, that are scattered around the table. Anyway, it was just so unusual that I, I really like this drive with the, a massive heat sink. <Laugh> he made some, yeah. Bubba above and below it, if you, you can see it's sandwich between heat sinks and he made some comment saying this used to run hot, but apparently not anymore, apparently not anymore.
Steve Gibson (00:17:09):
No. Do it. Heat sinks. I love it. Just a fun, little, one of the crazy test bench. Look at that. <Laugh> wow. Yeah. It's spin Wright found all the drives and is working correctly on us, all of those. So we're getting there. I'll talk a little bit about the past weeks adventure in a minute, butts found a bad bug in NSS. Of course this is Tavis Ory at Google. He he's part of their zero day group. He discovered and quietly reported an important bug in Mozilla's widely used open source NSS security suite. Last Wednesday with the bug quickly patched TAs tweeted. He said, quote, this is a major memory corruption flaw in NS, almost any use of NS is affected. The Mozilla advisory is here and he provided a link. And and then actually there's two links, Twitter shortened.
Steve Gibson (00:18:15):
One of them anyway, UHS is used by Mozilla. Of course it is the it's the reason for example, that that Firefox sometimes behaves, behaves differently on windows than other browsers, because every other browser uses windows intrinsic security library that built into windows, whereas Firefox brings along its own and, and that's sort of a mixed blessing. It means there's a lot more for them to maintain, but it does give them sort of a, a more of their own containment and and more portability. But aside from just Mozilla red hat, Susi, and many other products also uses of course Firefox, but so Thunderbird C monkey and the Firefox OS there's the open source client applications evolution pigeon Apache open office and Libre office are also NSS clients, server products. As I mentioned, red hat, their directory server certificate system and the mod NSS SSL module for Apache is also NS based.
Steve Gibson (00:19:39):
Over on the server side, Oracle is using NS including their communications messaging server and Oracle directory server enterprise edition. And as I mentioned, Susi, their Linux enterprise server supports NS as does Apache. So it's important if there's something bad there in other locations, Tava that is other than Twitter, Ts commented quote, if you are a vendor that distributes NS in your product, you will most likely need to update, or backport the patch Mozilla plans to produce a thorough list of affected APIs. But the summary is that any standard use OFS is affected, the bug is simple to reproduce and affects multiple platforms. So in other words, the anyone usings should focus less on worrying about which specific APIs are vulnerable. I would just argue, you know, don't worry about that. Just update your use of the security sweets versions prior to 3.7, three or 3.6, 8.1 in the ESR are vulnerable.
Steve Gibson (00:20:59):
And that's all versions since October of 2012, until those releases Tavis said, we believe all versions of NS since 3.14, which was released October, 2012 are vulnerable. However, for what it's worth, according to Mozilla, this vulnerability does not impact Firefox for whatever reason, but all PDF viewers and email clients, which uses for their signature verification are believed to be impacted. That's where the problem is it's in the signature ver verification component. Mozilla said applications usings for handling signatures in, in coded with CMS S mime peak KCS seven, or PKCS 12 are likely to be impacted applications usings for, for certificate validation or other TLS X dot 5 0 9 OCSP or CRL functionality may be impacted depending upon how they configures. So just for the record, the exploitation of this during signature verification can lead to a heat based buffer overflow when handling D R encoded DSA or RSA PSS signatures in email clients and PDF viewers, the impact of success full heap overflow exploitation can range from a simple program crash to potentially arbitrary code execution up through bypassing security software, if code execution is achieved. So again, if anyone is usings for some project, be sure to get an updated build. So that's, you know, all of the past nine years OFS up until this was patched. So essentially I'm sure anything anybody has been using until very recently when they just fixed it.
Steve Gibson (00:23:03):
Okay. I didn't know you did Leo, but I didn't know that there was a thing such as cheap, smart watches for kids and babies, to which we would have the refrain, what could possibly go wrong, Dr. Webb, which is an, an AV firm security firm based in Russia recently examined full or inexpensive smart watches, designed and marketed specifically for kids. Now, before I go any further, allow me to just suggest to anyone listening to this podcast, that if they have that on their Christmas list, avoid any temptation whatsoever. You might have to purchase a $50 smart watch for anyone. You know, Dr. Webb's report is very detailed, so I'm not gonna bother to describe what they found for each of the four devices, but discussing representative example will be informative and should be sufficient <laugh> to, for all, any desire. Anyone might have to put one of these little spyware Beasties onto the wrist of anyone they know or care about.
Steve Gibson (00:24:21):
So Dr. Webb introduces the subject with a little bit of background, which I've shortened a bit. They wrote parents always strive to take care of their children. Technology innovations, help them reach this goal through various wearables like smart watches and GPS trackers. These devices are getting close to smart phones in functionality. For example, many of the M can track the child's location and travel route. These devices can also make an answer phone and video calls receive SMS and voicemail, take pictures and listen to their surroundings. It's even possible to enable the remote control of the device. Okay. I don't know what that means, but they but said Dr. Webb has analyzed the potential threats that such gadgets can pose to parents and their children during their daily operation. They wrote these devices collect and transmit data to the manufacturers servers and available to parents through their personal accounts.
Steve Gibson (00:25:30):
The information obtained with smart watches is very sensitive. If malicious actors get their hands over such information, it can put children in great danger to understand the vulnerability and dangers of children's smart watches. Webb's specialists analyze several, several popular models chosen based upon public popularity, ratings and purposefully selected models from different price ranges. We purchased all smart watches anonymously from an online store. We carried out both static and dynamic analysis during the inspection. We searched for potential implants in, in the software and possible undocumented features as well as checked network activity, transmitted data and how it was secured. Okay. So one of the four devices they examined was the, the Lary kid phone 4g smart watch. And yes. And isn't it pretty Leo. I mean, it's, it's beautiful. That's like mommy. And daddy's exactly. Okay. Get a load of that. This is what this beautiful looking device, several versions they wrote of the LAR kid phone.
Steve Gibson (00:26:52):
4G watches exist. They're based on different hardware platforms, but they all run an Android OS and their firmware differs slightly. The primary threat of this model comes from its installed software. Its firmware has a built in app for over the air updating. And this app has Trojan functionality. Firstly, they wrote the application, sends the child's geo and data to its own remote server. Secondly, we found malicious code inside it, which is detected by Dr. Webb that, you know, remember these guys are AV people it's detected by their antiviral anti malware technology as Android dot down, loader dot 38 94. Every time the watch turns on or network connection changes. This code launches two malicious modules, Android dot downloader dot eight, 12 dot origin and Android dot downloader dot 10 49 dot origin. They connect to the command and control server to ver to transmit various information and to receive commands by default, the modules connect to the server once every eight hours because of this, a long delay exists between the first connection.
Steve Gibson (00:28:24):
And the first time the watch is turned on, thus reducing the chance of discovery, the Android dot downloader eight, 12 dot origin module sends the user's mobile phone number and SIM card information, geolocation data and information about the device itself to the command and control server. In, in response, it can receive commands to change the frequency of subsequent requests to the server, update the module, download install, run, and uninstall apps and load webpages. The Android downloader dot 10, nine dot origin module, send card information and mobile phone number information, geolocation data, a number, a large number of data about the device and installed apps as well as the in info info about the number of SMS phone calls and contacts in the phone book to the command and control server, thus Android downloader 38 94, hidden in this watch that's that parent can be used for cyber espionage, displaying ads and installing unwanted or even malicious apps.
Steve Gibson (00:29:42):
Okay. Now you put the picture on the screen before. I mean, which is for me, it's sort of disarming it's a consumer product and it's adorable and appealing looking. You know, our, our, our listeners who don't have video, can't see what you and I are seeing Leo, you know, but their very professional looking attractive consumer devices, they look like toys, but they're definitely not anyone who purchases. One of these little devils is not only exposing their children to remote anonymous attackers and track, but also bringing an open microphone into the lives of those children's parents. You know, who knows what might be overheard and what's presumed to be a private setting and who would be to blame. Now, I, I fully recognize that the likelihood of any specific child or their parents being targeted through this is diminishingly low. I don't mean to suggest otherwise, but knowing what we now know, who would feel comfortable strapping one of those loose cannons onto their child's wrist.
Steve Gibson (00:31:02):
And that's my point, the photo of these devices is utterly at odds with what's going on inside them. It it's deeply unsettling because they look so cute and harmless yet inside that colorful soft plastic shell is a communicating computer, running a Trojan and droid OS, which autonomously connects to a remote command and control server. And Amazon sells these things. The bullet points on Amazon's page says under security and peace of mind for parents monitor child's location, set safe zones and use remote audio monitoring through free parent controlled app. Get alert. If the child uses the builtin SOS button under easy communication, stay in touch, have a two-way voice call, use voice chat, or send emoji emojis limit contacts of those authorized through the app to avoid UND desired communication under user friendly and comfortable kids. Phone watch features math game and interface with emoticons. And then finally, under other features, class time mode, alarm call pedo up to four days, standby time, LAR safe family free multilingual Android iOS compatible app ability to add other LAR smartwatch users to friends list.
Steve Gibson (00:32:41):
So the watches that the Dr. Webb researchers examined had default passwords of 1, 2, 3, 4, 5, 6, and most of them don't bother to employ encryption in their communications. They just use plane text. What this brings to mind is the glaring gap in consumer protection that currently exists in our tech industry because you know, the difference between purchasing a well designed wifi router that might still have an inadvertent security vulnerability, this colorful plastic child's watch that communicates without encryption with remotely located command and control servers, continually sending back all of the child's movements and is able to autonomously download any additional software at any time. To me seems extreme. I mean, it's, it'll like it takes the consumer way down to sort of a, a different lower level and who knows what they're doing in the us, the engineers and scientists at underwriters labs are able to test toasters and vacuum cleaners because they're able to carefully examine and stress test the important functional safety aspects of those consumer products. But today's text gadgets. You know, tech gadgets are closed black boxes, which are actively hostile to reverse engineering. I don't see any solution to this mess, a other than to take every possible precaution. You know, we're able to place our I O T devices on their own segmented network. If these wrist watches also have wifi radios placing them on the, I O T wifi would help, but they can still, oh, and
Leo Laporte (00:34:42):
Yeah, the whole point of this is to follow your kid when they're out and about not in the home network.
Steve Gibson (00:34:47):
Right, right. Exactly. Yeah. I mean, and, and so, you know, to me, I just, I would stay as far away from this LAR brand as possible. And I guess the only advice I would have, I mean, I could, I could imagine the, as, as you listen to these bullet points, these seem like, like cool things. Yeah. But the kind of features you'd want in a watch that's tracking your child. Yeah. Like, but, but use Garmin or, or use, use a company
Leo Laporte (00:35:18):
American company to begin with, I would say, yeah. Yes. Apple has watches that do all of this probably at a much higher price, but they're available.
Steve Gibson (00:35:27):
Yeah. Yeah. Yeah. I, I, I just gotta chill when I looked at these beautiful looking consumer devices for 50 bucks and, and imagine, and, and we know how much kids like to emulate their parents. Right. So, so I'm sure Johnny would love to have a watch like daddy has. Right. You know that the, well, daddy,
Leo Laporte (00:35:48):
Them watch Johnny to have these capabilities. That's the thing daddy and mommy want to track the kids. The problem is who else is doing it.
Steve Gibson (00:35:56):
Right.
Leo Laporte (00:35:58):
Right. I, so you're gonna turn on all those features cuz that's why you bought the watch.
Steve Gibson (00:36:03):
Is there a really low end apple
Leo Laporte (00:36:06):
Iphone? No, there's a, there's an I apple watch se that they make that you can configure for kids. And that's probably the way to go, but it's a few hundred bucks. It's not, yeah. It's not
Steve Gibson (00:36:17):
Cheap cheap. Yeah. I, again, to all of our listeners buy or beware. Yeah. If, if you want this, I'd go apple. I mean, we know, we know that it will be as well designed as it can be. I just don't know how you do any, I mean, you know, maybe Samsung, maybe, you know, maybe another, someone other high end Android device, if you, or, or what about any of the garny sorts of things? Do any the activity trackers do, do
Leo Laporte (00:36:45):
Locations come, is there are a lot of kids trackers in this category because they're inexpensive. You don't want to give a kid a $300 watch they're small, they're built for kids. They're they're functionality is cuz considerably more limited cuz parents don't want kids, you know, making random phone calls either. Right? So there are, you know, there's this great, you
Steve Gibson (00:37:07):
Know, look at all the spam we got on our phone. Jill, want you a kid answering the phone, like some random stranger hearing Lord only where, Hey, how's
Leo Laporte (00:37:15):
Your R warranty? What?
Steve Gibson (00:37:19):
Yeah,
Leo Laporte (00:37:19):
That could be a problem.
Steve Gibson (00:37:23):
Anyway, I just, I just, for me, this was a wake up call and I wanted to share it because boy, you know, it's, it is however bad you think it could possibly be. This suggests it's a lot worse than that. You know, the people selling the just don't give a crap about security or privacy and you don't wanna strap that on to any child's wrist under any circumstances. Last Thursday, speaking of Russia, Russia's internet policing agency, <laugh> Ross NANS or announced the ban of an additional six VPN services bringing now the total number of band VPN providers to 15, the most recent six bannings were better. Net lantern, X, hyphen, VPN, CloudFlare, warp tack, eon VPN and private tunnel. Ross koan sent a request to inform the center for monitoring and control of the public communications network about the removal of those additional six services from the systems of all registered Russian companies and public organizations, they can no longer be used.
Steve Gibson (00:38:45):
So the list of band services now reads Ola, VPN express VPN keep solid VPN unlimited Nord, VPN speed, VPN IP vanish, VPN Viper, VPN, opera, VPN, and proton VPN, to which we add those other six. These services collectively have all been banned due to, to their principled refusal, to abide by Ross code mans demands, to connect their systems to the F G I S database, because doing so would defeat the entire purpose of using a VPN connection, which is that purposes to bypass access or restrictions and obtain anonymity, which is a level of individual freedom, which apparently makes Russia's leaders uncomfortable. Back in 2019, Russian authorities gave all VPN vendors operating in country, the ultimatum to comply with their rules or else B banned. The only vendor who responded positively before the deadline was, I guess not surprisingly the Moscow based Casper ski with their secure connection product.
Steve Gibson (00:40:07):
You know, they were already terminating the VPN, you know, in country. So they, they had nothing, you know, they didn't have to change anything. The nonlying VPN vendors either established new servers just outside the Russian borders or attempted to employ traffic masking techniques, which are known to work well against the great firewall of China. But the Russian authorities gradually caught up with those services also, which you know, were to bypass the new regulation and have banned them in multiple action rounds as Russian users, uninstall band products and turn to what few remaining products remain, Russian authorities evaluate, which ones have Remi have, then emerged as the most popular and add them to the growing block list. So, you know, if you're in Russia, good luck, it's gonna be very difficult for you to have private and secure communications or you, you aren't gonna be able to use one of these mainstream high profile VPNs. I'm sure there are ways around this, that people inside of Russia aware of, and Leo I'm aware of my need to take a sip. Okay. You like our our holiday day core, by the way, it's all. Oh, it's very nice. Yes. I like
Leo Laporte (00:41:33):
You got, you got a, a sock on the, on the door behind you, a stocking, I think. Yes. There's a stocking. There's a couple of stockings and we have some points set here is I see. Very nice. And yeah, one of the stockings is for Ozzie. One of them is for, is, is an angry bird stocking. You'll notice that the the Mr. Robot mask has a, has a El hat on a very, very, very fast. I think he should keep that. That looks good. It looks good on him. Doesn't it? Yeah, no, I actually like this time of year, I look forward to it all year long. You'll be getting our your TWiT Christmas card soon with oh, cool. It's the it's Meta version of our Christmas card. I you've been talking about. It's gonna, we're seeing it.
Leo Laporte (00:42:18):
We're all virtual. <Laugh> cool. Our show today. Thank you, Steve. Our show today brought to you by it pro TV. We love these guys. It's a great time to be in it. I mean, COVID just made it more important, not less, right. That's the thing. It is a necessity. And if you want to get into one of the many it careers out there, or even if you're already a seasoned, it pro it pro TV has something for everybody. It's a great way to get that first certificate. The certificate you need to get that job make yourself desirable to because it pro TV is the official training partner of compt. It's a good place, really good place to get those certs that, you know, many people start out with the a plus or security plus or network plus there's actually Linux plus there's lots of these.
Leo Laporte (00:43:10):
Those are really good SEARCHs to start with, but it doesn't stop there. If you're already in it. It's a very good way to expand your knowledge enhance your skills to re-certify for those certs you already have, and to get new certs as well. And the best part is it's easy. You can watch anywhere computer tablet, they've got apps for Roku and apple TV. It just, couldn't be easier to watch 20 to 30 minute chunks. So watch during the lunch hour, still have time to play a little Frisbee afterwards. It's, it's gonna fit in with your schedule. And also because they have transcripts, by the way, I should mention 5,800 hours of downloadable content. And all of it has transcripts, which you can search. So you can jump right to the thing you need to know. You know, I don't understand question four on the a plus test, by the way, they have that two practice tests.
Leo Laporte (00:44:03):
Let me go look into that a little bit more and you can jump right to that part. I just, it's got everything you need to be really easy. Every month. This year they've been doing special events. This is December is Python month to wrap up 2021, which I love. I mean that this is a great language very useful language for automation in it. They're gonna do a webinar day after tomorrow, December 9th, 2:00 PM, Eastern most in demand. It jobs for 2022. Ronnie Wong is gonna host that. If I know Ronnie, he's gonna be dressed to dressed to the nines. It should be a lot of fun. And that, of course, all of their webinars are available for watching later. It's nice to be their live cause you can ask questions and so forth. This coming weekend, December 11th and 12th, their free weekend feature courses like introduction free, by the way, introduction to programming using Python, Python, programming, Python, data model Python for security.
Leo Laporte (00:44:59):
This is great stuff free this weekend. So look, start or advance your it career with a wonderful instructors. They call 'em EDU entertainers at it, pro TV, visit it pro.tv/security. Now they've got, we've got a great discount still for you. This would be a, by the way, a great holiday gift for somebody, you know, somebody maybe in your family or a friend who has got the, you know, got the knowledge and the desire to work in it, but maybe he doesn't have that job yet. And you're gonna get 30% off. They're gonna get 30% off all consumer subscriptions for the lifetime of their active subscription with the offer code SN 30. Why do we do that? Well, cuz they're great. They're nice people, but also that lets them know you saw it here. So please use that offer code SN for security. Now three zero for their 30% discount it pro.tv/security. Now offer code SN 30. It's a great deal. And it's a great company, great people, Tim and Don. And I just really love them. If you're looking for it training, in my opinion, there's just nowhere better to go it pro TV build or expand your it career and enjoy the journey. We thank 'em so much for supporting security. Now they're big fans, all the folks over at it, prot back to you, Steve.
Steve Gibson (00:46:16):
So windows 11 has loosened its grip on edge. Oh thank God. Yes. Still last doesn't
Leo Laporte (00:46:24):
I know doesn't convince me,
Steve Gibson (00:46:25):
But I know last week's windows weekly was a bit depressing listening to Paul and Mary Jo holding Microsoft to account for many of the, of choices Microsoft has made for the behavior under windows 11, among other things. Microsoft is clearly turning edge from its original clean user benefiting browser into another Microsoft profit center. And then adding insult to injury is having windows 11 actively its users desire to switch away from edge to any other browser. Now in fairness, we've probably all seen my we've seen Chrome promoting itself whenever it has the chance. At least I do, you know, Firefox is still the browser that, that handles my URLs by default. And I'll manually often launch Chrome and use it. Oftentimes Chrome notices that it's not the default and you know, gives me some grief for that fact, but it's like, sorry, you know, I like microphone mic.
Steve Gibson (00:47:28):
I like Firefox's down the left hand column vertically oriented tabs, much better than, you know, and I've, I've used edges too. I've I've turned that on and still Firefox is my go-to browser. And, and, and it's annoying that there's no obvious way to tell Chrome that things are already just the way I want them to be. Thank you very much. But now that Microsoft is pushing the adoption of edge quite hard, we're seeing the same from them. Bleeping computer located the key in the windows registry, which contains the contents of the various popup messages that Microsoft has prepared for edge. There are five currently first one that may pop up reads Microsoft edge runs on the same technology as Chrome with the added trust of Microsoft browse securely now. Okay. <laugh> I don't know what that means. Mm-Hmm <affirmative> mm-hmm <affirmative> or how get this one? That browser is so 2008 exclamation point. Do you know what's new Microsoft edge? Ooh.
Leo Laporte (00:48:43):
Wanna be with the hip kids?
Steve Gibson (00:48:46):
Come, come to the future. <Laugh> okay. Number three. Looking for speed and reliability. Microsoft edge is the only browser optimized for windows 10. What? Try a faster browser today. Okay. How about number four? I hate saving money. <Laugh> said no one ever that's
Leo Laporte (00:49:09):
Because they're building in and buy now pay later. And I on searches all
Steve Gibson (00:49:14):
No crap. I hate saving money said no one ever Microsoft edge is the best browser for online shopping shop smarter now. Oh, Leo. And finally Microsoft edge is fast secure and the browser recommended by Microsoft <laugh> well, duh, discover, discover more benefits, learn more about Microsoft edge. Now bleeping computer has been unable to trigger some of, I think they've only been able to see two of these five, but those are in there waiting to spring out
Leo Laporte (00:49:51):
Annoying. Cuz it gets triggered when you try to download Chrome. When you go to Chrome, when you, I mean anything you do, Microsoft feels a necessity to nudge you and say, oh no, no, no
Steve Gibson (00:50:01):
You want edge. Yeah. Now there are therapists <laugh> that could help with this form of insecurity. Yes. Okay. In any event I've already very quickly clearly articulated my feelings about windows 11 and I'm feeling quite confident that none of my hardware will run on it. So I'm good. Good. You know, it's like, sorry you can't run windows 11. Fine. I'm that's good. That's right. Outcome for me. Anyway, I've been shying away from any further kicking of that dog, but in fairness, I wanted to mention a bit of balancing good news that I imagine Paul will also be noting tomorrow. The way things were originally set up in windows 11 is that Microsoft had eliminated the simple ability of the user to change their systems default browser by removing the UI option to do so. Instead they granular eyes, the web browsers handling settings by file type, you know, like HTM dot, HTML, PDF and so on and by protocol HTTP, HTTPS.
Steve Gibson (00:51:16):
And so you, you could, you had to specify, you know, which browser would handle all of those things individually. And they buried all of those options deep in the registry. This forced any determined windows, 11 users to search through the registry extension by extension and protocol by protocol to manually change each one in order to unhook edge happily with last week's release of the windows 11 insider build to oh nine. Microsoft has restored the presence of a single set default button and has also surfaced all of those individual file and protocol types in the UI. So a non edge browser can now be set as default easily. And then if desired, for some reason, other browsers can override that default for specific file type and protocols. So good on Microsoft for listening to users. I mean, you know how they'd have to be really deaf, not to have heard the outcry O over how difficult they had made it not to use edge under windows 11.
Steve Gibson (00:52:35):
So I just wanted to acknowledge that they had okay. Also on the Microsoft side, the earliest windows had the clean and simple note, a app, which was useful for displaying and editing unformatted and unformat text VI. I still use notepad every day. You know, it's just right there. No BS. If I, when I wanna like, you know, take line wraps out of a block of text notepad, you know, and I like notepad plus, you know, just to prevent everyone from telling me about it. I know about it. I have it. I love it. It's annoying that it's constantly updating itself. It's just like, would those guys just please leave it alone? But no, anyway, Nopa is there, it was implemented as a very lightweight UI around a simple windows text box container. Basically it's the, it's a, it's a control a, a, a UI control widget with a little bit of, you know, load and save UI around it.
Steve Gibson (00:53:44):
Hm. But when those also offered WordPad right from the beginning, which allowed for a richer textual for batting experience, it was possible to set the text, color, the size and treatments such as bolding and its and so forth and, and the text alignment. And just as no notepad was a UI wrapped around the windows, text box container, word pads, richer textual formatting experience was a UI wrapped around the windows, rich text format or RTF container. I've long been a fan of windows, RTF control, and anyone who's ever used any of my windows software will have seen its embedded pages with some text formatting. That's what I use. I, I like being able to set some colors and alignment and, and font sizes and things. All of that in my apps are RTF controls. Okay. And any of that, unlike notepad, the RTF container can also contain embedded things.
Steve Gibson (00:54:54):
It can be a host for Olay, the original object linking and embedding objects, because why not? One of the many features of this embed is the use of so-called formatting templates, which can be loaded on the fly from a file. And wouldn't, you know, it, malware deployers have figured out that these RTF embedable template objects will also accept URLs <laugh> oh Lord. In other words, not just loading them with something local, loading them with something from anywhere in the world, sounds like a terrifically flexible feature. What could possib possibly go wrong? Well, how about three different state sponsored threat actors aligned with China, India, and Russia all now having been observed adopting this RTF template injection as it's now being called as part of their new fishing campaign to deliver malware into targeted systems. Researchers at Proofpoint have published the results of their research under the title.
Steve Gibson (00:56:18):
Injection is the new black <laugh> novel RTF template, injection technique poised for widespread adoption beyond a P T actors. They said threat proof, threat research, I'm sorry. They said Proofpoint threat. Researchers have observed the adoption of a novel and easily implemented phishing technique by a P T you know, advanced persistent threat actors in Q2 and Q3 of 2021. This technique referred to as RTF template injection leverages the legitimate R F template functionality. It subverts the plain text document formatting properties of an RTF file and allows the retrieval of a URL resource instead of a file resource via an RTFs template control word capability. This enables a threat actor to replace a legitimate file destination with a URL from which a remote payload may be retrieved. The sample RTF template injection files analyzed for this publication currently have a lower detection rate by look AV engines when compared to the well known office based template injection technique.
Steve Gibson (00:57:51):
In other words, this has been adopted because it slips under the radar. At this point, Proofpoint has identified distinct Phish campaigns utilizing the template, which have been attributed to a diverse of advanced persistent threat actors in the wild. While this technique appears to be making the rounds among a P T actors in several nations, Proofpoint assesses with moderate confidence based on the rise, the recent rise in its usage and the triviality of its implement that it could soon be adopted by other cyber criminals as well. They wrote RTF template. Injection is a simple technique in which an RTF file containing decoy content can be altered to allow for the retrieval of content hosted at an extra URL upon opening upon opening an RTF file by altering an RTF files, document formatting properties spec, specifically the document formatting control word slash slash asterisk slash template struck actors can weaponize an RTF file to retrieve remote content by specifying an a URL resource instead of an accessible local file resource destination.
Steve Gibson (00:59:20):
And they go on at some link to it to explain this more clearly. So anyway, we know the tune pretty well. Once again, an arguably unnecessary and seldom if ever used feature of RTF containers has been found to be exploitable by attackers. And as now being used with growing popularity, as Proofpoint suggests, it's too easy to use and too powerful not to become much more widely adopted. I guess what we can hope is that all of the AV scanners and windows defender and other tools, which are currently not seeing this abuse will be quickly updated in order to catch it.
Steve Gibson (01:00:11):
We have an instance of a malicious botnet using the Bitcoin blockchain, get a load of this one, a botnet, which Google says has infected more than 1 million windows machines globally and continues to infect new machines at a rate of thousands more per day is using the public Bitcoin blockchain to stay in touch. Google is suing up pair of Russian individuals. It claims are behind this sophisticated botnet operation in a complaint filed in the us district court for the Southern district of New York, Google names, Russian nationals, Dmitri OV and Alexander F of as the two main operators of the group Tiba botnet, citing Gmail and Google workspace accounts. They allegedly created to help them operate the criminal enterprise. Google claims the defendants use the botnet network, which it describes as a modern borderless technological embodiment of organized crime for illicit purposes, including the theft and unauthorized use of Google users, logins and account information.
Steve Gibson (01:01:36):
Google is demanding that Dimitri and Alexander pay damages and are permanently banned from using Google services. According to Google the GL the Glu Tiba <laugh> G U P T E B a, I guess that's Glu Tiba B Teva. I think you got it. Yep. I think which Google has been tracking since last year in 2020 has so far, in fact that approximately 1 million windows machines worldwide, it is growing at a rate. As I said, of a few thousand new machines a day, once a device has been infected typically by tricking users into downloading malware via third party free download sites, the botnet steals, user credentials and data secretly mines, cryptocurrencies, and sets up proxies to funnel other people's internet traffic through the infected machines and routers in its complaint. Google says, quote, at any moment, the power of the Glu TBA botnet could be used in a powerful ransomware attack or distributed denial of service.
Steve Gibson (01:02:47):
Google also noted that the Glu TBA botnet stands out compared to conventional botnets due to its technical sophistication and use of blockchain technology to itself from disruption, as well as launching the litigation against this so-called glute botnet, the company's threat analysis group, that tag team, which has observed the botnet targeting victims in the us, India, Brazil, Vietnam, and south Asia announced it has worked with internet hosting providers to disrupt the botnets key command and control infrastructure. This means its operators no longer have control of the botnet though. Google has warmed that Glu TBA could return due to the fact it uses blockchain technology G as a resiliency mechanism, Google explained that the glute botnet does not rely solely on predetermined web domains to ensure its survival. Instead when the botnets C and C server is interrupted, the Glu of malware is hard coded to search the public Bitcoin blockchain for transactions involving three specific Bitcoin addresses that are controlled by the Glu TBA enterprise.
Steve Gibson (01:04:16):
Thus, the Glu TBA botnet cannot be eradicated entirely without neutralizing its blockchain based infrastructure, which I thought was, you know, quite clever. So, so presumably the bad guys, if they lose control of the command and control servers, they're able to create transactions, which host to the blockchain. The blockchain of course records the, the, the signatures of, of the entities, who that are posting transactions there the, the, the bots then look there and pick up their instructions from details of the transaction. The so where there's a will, there's a way. And obviously, unfortunately, there's a lot of will here. HP has been shipping vulnerable printers for the past eight years. The guys over at F secure, carefully examined one HP printer. It was an M 7 25 Z multifunction device MFP. But once they reported their findings to HP at the end of April, HP found that their of common firmware across printers meant that at least 150 other printer models were also affected across the laser jet PageWide and scan jet families updated firmware has been available from HP since November 1st.
Steve Gibson (01:05:57):
So anyone having any HP printer who might be a target of either inside or outside attack will definitely wish to update all of their HP printers firmware. The first of the two problems tracked a CVE 20 21 39, 28, 8 with a vs rating of 9.3 describes a vulnerability that can be used to create wearable exploits that can self replicate and spread to other HP printers inside internal networks or over the internet. The trouble is particularly worry because it's a buffer overflow in the printer's font parser. So just causing a vulnerable printer to print a specially crafted page or PDF could take over the printer. The F secure researcher said that the flaw can be exploited to gain control over a printer's firmware to steal data, data, or assemble devices into botnets all while leaving little evidence of exploitation behind presumably just operating in Ram. They also indicated that attacks that abuse the vulnerability in various other ways, such as attacking internet exposed devices or by loading the exploit code on a website or inside an ad can also be successful users on corporate networks are those who view the ad will have the code reach out to ports on their internal network to exploit local printers.
Steve Gibson (01:07:37):
Wow. The second vol vulnerability is a, excuse me, local physical USB port attack being tracked as CVE 20 21 39, 2 37, which impacts the printer's communications board. Fortunately, this bug can only be exploited with physical access to a device. And an attack takes up to five minutes to execute compared to the first one, which only takes a few seconds. On the other hand, if you've got printers with exposed USB ports, that's an inside job attack. Some, you know, in a, in a very large corporation where you've got a disgruntled employee or maybe they've been subverted by an, an outside entity, you know, Hey, you know, we'll, we'll pay a $10,000. If you insert this USB stick into one of your company's printers and walk away you know, wipe off any fingerprints you know, that would be a model that could also be successful. So, as I said, if your enterprise uses HP printers, which are still the world's number one printer by market share do make some time to update the firmware throughout your organization. Again, it's been available since November. Okay. Just a quick touch on sci-fi. My nephew is going nuts over Rick Brown's latest novel.
Leo Laporte (01:09:12):
How old is your nephew? Is he 10? Is he 30?
Steve Gibson (01:09:15):
No, no, no. He's one of the top performers at Salesforce. Okay. Got it. Okay. So, so he's a grownup. Well, that makes
Leo Laporte (01:09:23):
A difference. If a 10 year old says they love Rick brown. Okay. I'm gonna take that like a 10 year old would like it, but he's a grownup. Okay.
Steve Gibson (01:09:31):
Yeah. I'm more than twice his age. Okay. And I, I can't wait. Anyway, he, he keeps texting me in all caps. <Laugh> the, the new novel is so good. Now we've read Rick
Leo Laporte (01:09:44):
Brown before this is not a new name.
Steve Gibson (01:09:48):
Oh yeah, yeah, yeah. Yes, yes, yes. It's spelled R Y K. This is that frontiers saga. Yes. This is the frontiers. Oh, a is. Oh, okay. Yes. This is the 31st book. And I know that John is up to speed. He's probably already read this, this 31st book. <Laugh> anyway, I, I will get there. I you know my nephew is making me DRL for this book, but I'm gonna go do the Baba verse first, be in, in honor of all of our listeners who have said, you know, check it out,
Leo Laporte (01:10:19):
Frontiers. The frontier Sug is kind of one of those space, battle type sci-fi books, right? A lot of laser fire and things.
Steve Gibson (01:10:26):
It, it is, but what it, what it is is it's character driven. Oh, good. It is so well. I mean, in fact, I have here in my show notes, I said, Rick's, Brown's latest novel, which presumably details the continuing adventures of Nathan Cameron, Jessica Vladimir tells Josh Loki and all the rest of the wonderfully articulated characters that Rick has created. I mean, that's really what it is. It's you it's so well done because you, you really get to know these people. Mm-Hmm <affirmative>, and, and it's a, it's an interesting, you know, the, the, the best sci-fi is, is about the characters, but it, it also creates some interesting and engaging new technology. So, and this isn't giving anything away. This is set in the far future after the, the earth and a number of its neighboring settled planets are recovering from the so-called bio digital plague.
Steve Gibson (01:11:32):
That's never, Rick never goes into great detail about it, but it's something, it was a, it was some sort of a digital VI virus that crossed over into the biosphere and almost wiped out humanity, not only on earth, but everywhere. It was able to travel. And a bunch of colony ships went out that were ahead of this bio digital plague and, and so humanity dispersed through the universe. So now we're in the process of like getting ourselves, pulling ourselves back up by our bootstraps. What was discovered in this Swiss Alps was an archive of all the stored human knowledge from pre plague time, which was locked up. So the bio digital plague couldn't get in. And so a new drive technology called the so-called jump drive allows us to jump a great distance and an accident, which occurs at the very start of the first book, which is why this is not a spoiler has surprising consequences.
Steve Gibson (01:12:42):
And I, anyway, it is, it is, I, I was glad to see some reference elsewhere to it being one of the most popular like science fiction space operas of all time. So it's not just me. I, I didn't have any sort of calibration, but it is just, and I've read the whole 30 books twice now, actually, the be, you know, and, and I'm, I'm finishing up 30 that I'm gonna switch the Baba verse, but it's just, if you, if you know, it's not gonna ch you, but if you just enjoy, you know, really well done adventures it is definitely that nice. Okay. So the, that heuristic hardware interrupt handling solution that I mentioned last week, which I developed for spin, right. Appears to have solved a number of current and doubtless future troubles. You know, as I've mentioned, I take every single problem that our testers can find absolutely seriously, cuz I learned a long time ago, if it happens to one person it'll happen to, you know, a hundred.
Steve Gibson (01:13:53):
So thanks to additional feedback from our testers and my hours of staring at code we have, you know, and, and then a number of additional tests and incremental improvements, you know up in the very far right corner of that screenshot, it said developer or development release seven F. And so, and I, you know, and so we had seven and then we quickly had ABC D E F cuz they didn't feel like they were big enough to go to jump to eight. But I kept hoping I was gonna, you know, hit the magic solution for a whatever problem I was. I was trying to track down. So we've had a bunch of tests and incremental improvements what's been so gratifying is that as testers have swung by the development group over the weekend one after another they've reported that this or that trouble, their systems used to have is now gone.
Steve Gibson (01:14:53):
And that spin writes latest development release is now working perfectly for them. So we've seen a lot of progress, but there are a few exceptions and their nasty, a couple of people have reported that the size of the first drive in is being confused with the size of the last bios drive in their system. It doesn't happen to me nor to most people, but it reliably happens to a couple of our testers. So something different is going on in their systems. One person has a 70 terabyte Drobo directly attached to their system and is bio accessible. And that was crashing spin, right? Because I wasn't ready for a 70 terabyte drive, which is overflowing some register space. So I'll expand that. The other thing with Drobo is they're not always reporting the actual yes. Space. Yes. That's exactly what we saw. He, he said he only had 32 terabytes, but it's saying 70.
Steve Gibson (01:16:00):
Yeah, that's true. So it's like right there. <Laugh> yeah. And a few others are reporting something really odd, spin rights, own division overflow pop up is popping a up. Now the popup tells us where the division overflow occurred. But when I look there in spin rights code, there's no division instruction at that location. So the only conclusion is that something is causing spin rights, own code, be overwritten. Fortunately what's being overwritten contains either an F six or an F seven, which are the X 86 division op codes. So I know where the first drives size is stored, which something is changing later when it shouldn't. And that err division overflow pop up tells us where a division instruction has mysteriously appeared in spin rights code. So we need to track down what's going on with the drive size being changed and the code being overwritten to do that.
Steve Gibson (01:17:12):
We need to catch the overriding action in the act as it's happening. The problem is I've never been able to reproduce any of those problems myself. It's only happening on a few distant machines. The sir, which I will immediately implement a few hours from now, <laugh> maybe in the morning, depending about how I'm feeling after the podcast is to build a native debugger directly into spin, right? And that's actually easier than it sounds. The Intel X 86 architecture has always incorporated built in hardware debugging assistance. It has 4 30, 2 bit breakpoint registers, which can be set to point to any region of the system's memory. Each of the four breakpoint registers can be set to interrupt the processor upon the execution, the, or the writing of that memory with a two, four with a 1, 2, 4 or eight byte span. So this next text test release of spin, right, will add a couple of new command line options to load and enable those debug registers.
Steve Gibson (01:18:28):
Once a tester has scene where spin right reported an erroneous division instruction, they'll be able to immediately rerun it, setting a right break point at that spot in spin rights code, which will allow us to catch in the act. Whoever is overwriting spin, right? I'm assuming it's me with some of code of mine. It might be their bias again. I can't make it happen. They're gonna be, they can make it happen. And this will allow anybody to, to work with me, essentially doing remote debugging of the code using the X 86 debugging instructions. So we're gonna to have an interesting time in the next week. And I probably report that spin right. Is, you know, got these problems solved by a week from now. Wow.
Leo Laporte (01:19:20):
That's amazing. <Laugh> that's amazing. Meanwhile, I'm still playing bingo with some squid on my submarine. <Laugh> so,
Steve Gibson (01:19:28):
Or as Lori says, I made the <laugh>
Leo Laporte (01:19:34):
I got something done today, you know, that's good. That's good. Steve, let's take a break then we're gonna get into the the meat of the matter, whatever vaccinate,
Steve Gibson (01:19:43):
Her, whatever
Leo Laporte (01:19:44):
You mean by nature vaccinate, we will find out in just in, just in just a moment, but first a word from my favorite. And I have to say, this is a relatively new situation this year, mostly password manager. So I always, first of all, there's not even a question. Use a password manager. Okay. Just use it. We had a caller on the radio show on Sunday who said, yeah, my bank password was guest guest. I said, I said, was it monkey 1 23? He said, no, no, it was a <laugh> it's a good password. I said, well, I got a question for you. Do you think you might have used that password anywhere else? And he said, oh yeah, I use it all the time. I said, well, that's how they guessed it from a, a breach of your password somewhere else. He says, well, I use a password manager, but I didn't use it to generate my passwords.
Leo Laporte (01:20:34):
So that's very important. What is a password manager? Well, in case of bit warden, it's a totally secure encrypted password vault where all of your passwords and by the way, anything else you, you want? I keep my vaccine certificate there. I keep my passport there. My driver's license. Anything else you wanna keep secure? I keep everybody's social security number there, cuz you wanna keep that secure. So it's an encrypted blob only you have access to, but that's not all a password manager does a password manager should also generate good, strong, totally random. And of course, as a result, completely UN memorable passwords and you, and that's what bit warden does so well. And I also should point out bitten. Warden will go through your passwords and say, you reuse that one. You reuse that one and help you change it. So they have a security audit as well because you don't wanna reuse.
Leo Laporte (01:21:28):
That's what happened to this guy? I said, go Toon. Toone enter your password. I bet you anything. It's been seen a number of breaches. But if you just use a good password vault, if you use bit warden, you don't have to, you don't have to worry about it. Now bit warden is of course the only open source cross platform, password manager that could be used at, at home at work on the go it's trusted by millions. And it's a great choice for your business too. That's what I wanna pitch you on right now. What's cool about bit warden is the individual bit warden account free forever because they're open source. Their business model does not require them to convert free users to paid users. That's not how it works. They're an open source password manager. So in fact you can, even if you want, they've open sourced the server, you can run your own server.
Leo Laporte (01:22:18):
If you want, you know, you can you can do it all. In fact, it's it's open source. So there's a, there's a, a guy who's written a really nice, lightweight bit warden server in rust, super secure. You've got complete flexibility and I love it for that reason. And if you wanna have a business bit warden account, the way it works is you have all your employees set up their individual account and then they join your organizational vault. Now of course, when we're talking enterprise, there's a lot more you want from password manager. For instance warden for business is fully customizable. You have all sorts of policies. You can enforce, you can adjust features to adapt your business needs. You also get bit warden send, which is a fully encrypted method to transmit sensitive information, whether text or files, if you are an accountant, if you're a physician, this is the way to transmit private data.
Leo Laporte (01:23:13):
The recipient does not have to have a bit warden account to access it. Bit warden for enterprise let's team members generate of course, unique, secure passwords for every site. You get to set Paula about that as well. And it's enterprise grade security that is fully compliant with GDPR, California, CCPA HIPAA for health providers SOC two. And because it's storing passwords, it mitigates phishing attacks. People sometimes ask me, well, how does that help? Well, you go to a site that pretends to be your bank bit warden can see the difference and will not autofill that Phish site. So you don't have it's it's you, you want your employees to use this bottom line two new features for enterprise. They just announced this for this month. If you are currently a part of a bit warden cloud based enterprise plan, all of your users will be granted free bit warden family accounts that give premium features step to six total family members.
Leo Laporte (01:24:13):
That's a great, great thing. In fact, that's something we did as a business. And I think really you should do cause you wanna encourage password security, not just at the business, but at home too. Also they've added login with single sign on log with SSO. This is a new option for customer managed encryption. It enables a self hosted enterprise and Steve you'll understand this and appreciate it to use a local key server to manage vault encryption keys. So it gives you SSO at work. Employees can access and decrypt their bit involved through their SSO credentials. This solves that one little problem with any password manager, you have to remember how unlock it. Now you've got SSO, no additional passwords or login information, and it's more secure. Fantastic. If you're interested in a business plan that warden has a number of plans for your organization, the team's organization opts $3 a month per user, you could share private data securely with your coworkers department or entire organization.
Leo Laporte (01:25:13):
That's a big part of any business password manager is secure sharing of passwords. People are gonna share passwords. You don't want 'em texting them. You don't want 'em writing. 'em On post-it notes. You, you don't want 'em emailing them. So bit word makes that possible. If you're a larger enterprise bit warden's enterprise organization plan five bucks per month per user, and there's always the free organization plan. That's two users you can store and secure passwords. And of course, as I mentioned, they have family plans and they have individual plans. And honestly I pay for bit warden cuz I love it so much. It's for me, it's less than a buck a month and I wanna support 'em. I really do, but you, but it's but the personal plan is free forever. Last chance to register for their free open source security summit. You're gonna like this panel it's coming up December 9th, day after tomorrow, Nicole Pearl Ross, Steve WAAC and Bruce Schneider are the keynotes.
Leo Laporte (01:26:09):
Wow. December 9th, 7:00 AM to 10:00 AM. Pacific 10:00 AM to 1:00 PM Eastern time. What a that's three people I'd love to hear from bit warden believes everyone should have access to basic pass security to tools. Individuals can use their basic free account. As I mentioned forever for an unlimited number of passwords and it works in all your devices, you get all the benefits of a real password manager for free. You can upgrade to a premium account for less than a buck a month. That's my account. If you're looking for secure password storage for the family, the family organization options, six users premium features $3, 3 cents a month, not per person, but total I think bit warden is just great. And of course you can use the bit warden cloud to store your vault, but the personal plans you can use your own, you know, Dropbox or whatever you want for the vault.
Leo Laporte (01:27:00):
If you don't wanna if you really want, you know, trust to no one <affirmative> become monitor and manage security vulnerabilities using their vault health reports from bit warden. As I mentioned, you can identify exposed reused week or potentially compromised passwords as well as any items in your vault within active two FA we really love that two FA you wanna turn it on? It'll say, no, you, you could use two FA on this account. Do you wanna on, I think that's really important. And again knowing that your password's been compromised and reused, would've saved this guy. A lot of trouble get started with a free teams or enterprise trial, a teams or enterprise plan. All you gotta do is go to bit warden.com/twi, or try it for free across all your devices as an individual user. That's how I started using bit warden. And I tell you no turning back. I love it. Bit warden.com/twi. I'm a believer in open source. That's why I'm a big believer in bit warden. If they can never take it away from you. All right, Steve, let's talk about what is it? Six Dick Dick. Good.
Steve Gibson (01:28:06):
<Laugh> what are you talking about? I would assume we would pronounce it. Ator X S I N a T O R vaccinator
Leo Laporte (01:28:14):
Ator sounds right. Yeah.
Steve Gibson (01:28:16):
Okay. Their paper is titled ator.com from a formal model to the automatic evaluation of cross site leaks in web browsers.
Leo Laporte (01:28:31):
Oh, excess as in cross site. Okay.
Steve Gibson (01:28:33):
Exactly. Cross site. It's a result of a comprehensive work conducted by a team of five German university researchers. And as a result of their work, they discovered 14 new types. Excuse me, 14 new types of cross site data leakage, which are effective against, well, I think every browser tour Firefox Chrome edge safari opera, and others, both desktop and mobile, as I said, and going to vaccinator.com allows you to run the test that they've designed, which will profile your own browser. And then, and it shows up in the left hand column and then allow you to compare it against all the other browsers which have been profiled. So they call the bugs Xs leaks, you know, as in cross site leaks because they enable malicious websites to harvest the personal data from their visitors as they interact with other websites in the background that is as the hostile website you go to, or for that matter, an ad that that is, you know, running script, all that has to happen is script is run in your browser, then reach out using JavaScript you know, you using Ajax to create connections to other browsers with which you have a relationship in a recent statement about their research, which was presented during last month's 2021 ACM CIG SAC conference on computer and communication security which by the way, their presentation garnered a best paper award.
Steve Gibson (01:30:19):
They explained, they said X leaks bypass the so-called same origin policy. And whoops, we know how crucial that is in our browsers for browser security. One of the browsers, they wrote main defenses against various types of attacks. The purpose of the same origin policy is to prevent information from being stolen from a trusted website. In the case of excess leaks, attackers can nevertheless recognize individual small details of a website in these details. If these details are tied to personal data, they said those data can be leaked. Now our listeners probably know by now that I'm a sucker for formally proven security findings that, you know, there's certainly a place for fuzzing, which is probably the other end of that spectrum from formal proofs and formal proofs won't help when modeling cannot be applied, but whenever possible, creating a mathematically formal model of a system, then using that model to reach and or demonstrate security conclusions is in my mind the gold standard.
Steve Gibson (01:31:37):
So here's how this team describes what they've accomplished in their abstract for their paper. They said a cross site lead describes a client side bug that allows an attacker to collect side channel information from a cross origin HTTP resource. They wrote, they posed a significant threat to internet privacy since simply visiting a webpage may reveal if the victim is a drug addict or leak a sexual orientation, numerous different attack vectors, as well as mitigation strategies have been proposed, but a and systematic understanding of cross site leak root causes is still missing or at least was before they began this. They said recently, SU Hode NA at all, gave a first overview of a cross site leak at the net at the network and distributed system, secure symposium that's NDSS. They said we build on their work by presenting the first formal model for cross site leaks.
Steve Gibson (01:32:50):
Our comprehensive analysis of known cross site leaks reveals that all of them fit into this new model with the help of this full normal approach. We one systematically searched for new cross site leak attack classes, two implemented vaccinator.com a tool to automatically evaluate. If a given web browser is vulnerable to cross site leaks and three evaluated mitigations for cross site leaks, we found 14 new attack classes evaluated the resilience of 56 different browser OS combinations against a total of 34 cross site leaks and proposed a completely novel methodology to mitigate cross site leaks. Now, in the show notes, I have my own results using Firefox and Chrome Firefox 94 on the left Chrome on, on the right. And red is bad. <Laugh>, there's, there's a lot of red there both Firefox and Chrome in their paper. And I did not include it in the show notes.
Steve Gibson (01:34:11):
I, I forgot they have some, some other tables where they show all of the tests and all of the different browsers and version numbers and for what it's worth Firefox has fewer reds than anything else. The tour browser, which of course is based on Firefox has even a, a few fewer. But yeah. So Leo now you have on the screen the, I guess that's the pretest page and up at the top, there, you're able to click a blue button, which is like right there and click it and it will begin the, it will initiate the test, which is now underway on your browser. So we'll see how that comes out. How long is this gonna take? That's only a few minutes. Okay. I'll be back with you in a minute. <Laugh> and I think that opened another tab, switch back to the first tab.
Steve Gibson (01:35:07):
Yeah. And you, you might, you might be able to see it operating if, if, if, if it opened a second. Yeah. Oh yeah, there it is. And you're, and you're seeing your beginning. Oh, these are the red initial. Okay. Yeah. Yep. There, I think it's yeah. What are these, what are these things? Is there something I should be worried about here? Yeah. That's why we're talking about this today. I'm in Firefox doing this. Okay. Yeah. Okay. So in a web application, they explain a web browser interacts with several different web servers, HTTP or web socket connections. The client side logic of the web application is written in HTML, CSS and JavaScript, and is executed inside a tab of the browser or inside an inline frame in another application or an ad. The execution context of a web application is through the concept of web origins.
Steve Gibson (01:36:00):
Web applications may call and embed other web applications to enhance functionality. For example, a hotel reservation site might embed Google maps and public transportation sites as an easy method to allow its customers to determine how to reach the tell in such situations, cross origin, HTTP requests between different web origins, meaning the hotel's origin and the maps, the maps server origin are necessary to retrieve data, to embed and display in the web application. When interact with a website, a user has a well defined state. This state typically contains the information such as whether the user is logged into the site currently or not. Besides the login status, the user state may contain account permissions, such as admin privileges, premium members ship or restricted accounts. The number of different user states is potentially unlimited. For example, in a web mail application, a user may or may not have received an email with the subject top secret.
Steve Gibson (01:37:16):
Okay. So they say under privacy risks of cross origin requests consider the following situation. The attacker has lured a victim to a malicious web application that executes hidden cross origin HTTP requests to different drug counseling sites. If the attacker could learn whether the victim has logged in at one of these drug counseling sites, the attacker could gain highly privacy critical information about the victim to distinguish between two user states. The attacker's JavaScript code must be able to identify differences in its own execution environment, resulting from different responses to cross origin, HTTP requests. These different responses must correspond to different user states at the target. That's sort of the victim web application. If this differentiation is possible, we call this vulnerability a cross site leak. The attacker could then craft a malicious website, which triggers the cross site leak once the victim visits it. Okay, we'll get it's specific here in a second in the fall.
Steve Gibson (01:38:37):
So then they give two real world examples, an excess leak on GitLab. They wrote GitLab is a popular web application for collaborative software development. Hosted by many companies. Gitlab provides a profile URL, which is H D E DPS colon slash slash gi.company.com/profile. If the user is not logged in this URL, redirects the user to HTTPS colon slash GI dotcom.com/user/signin. If the user is logged in the comp, the current user's profile is shown. However, since the attacker embeds GitLab cross origin into the attacker's own webpage, the attacker cannot directly read the URL in listing one above. And I included it in the show notes. We use the window dot length property, which is readable cross origin to determine the user's state at the other site. The profile page does not in any eye frames, but the login page includes three eye frames. If this property window dot length has the value three, that means the user is not currently logged in.
Steve Gibson (01:40:11):
If it has the value zero, the user is logged in by different company websites, hosting GitLab. The attacker can collect information on a programmer's affiliations. So there's an example of true cross origin information leakage, where a site you visit or an ad hosted by a Ben insight is able to determine things about you and your current state with other domains, with other websites. And it works on Google mail. They give an example of a cross site leak on Google mail. They say Google mail, one of the most popular web mail applications in 2019, Turgen T E R J a N Q reported across site leak, which could determine whether an email with a certain subject, for example, drug counseling or content, which could, or, or, or content was present in the user's inbox, cross origin. In other words, it's possible to reach into a user's Gmail this way, the cross site leak abused the common cash that of applications share by using the advanced search option, which can be called cross origin, Google mail marks, search results.
Steve Gibson (01:41:43):
If any exist with a dedicated image to perform a cross site leak, attack the attacker first empties, the web catch, the cash, which can be done locally, then calls Google mail, advanced search using a URL which can be done. And finally checks if the dedicated image is available in the cash, if true, the search was successful. And the attacker learned that an email can, whatever search term, the attacker queried exists in currently exists in the targets, the, the victims inbox. Okay. So let's make sure that everyone understands where we are. Any Gmail, user visits, some random nosy website, without indication of any kind that nosy website running JavaScript on the user's web browser is able to use subtle and clever tricks to perform as many go, no go searches of the users, Gmail inbox, as they wish against, against their current content entirely, entirely behind their backs.
Steve Gibson (01:42:59):
And without their knowledge, we've talked about this general class of web browser hacks. A number of times in the past broadly speaking, it is incredibly difficult to robustly prevent any cross domain leakage. We've seen that initially benign seeming convenience features such as changing the color of previously visited links can compromise privacy when website a uses the user's browser to display website off screen, and then probes website BS, Dom the document object model for the colors of various links in this way, information that is none of website A's business leaks from users from the users' previous use of website B. What this team has done is further explore and rigorously map brand new forms of subtle side channel, cross origin information leakage, and the have come away with a surprisingly large number of new ways for clever attackers to leverage deliberate features of JavaScript like using the window length of some other website's page to infer information.
Steve Gibson (01:44:24):
That's none of their business about the browser's owner. We've seen that previous cross domain cookie and cash attacks have led browser developers to segment all cookie storage by domain and to similarly segment all browser cash by domain, since the performance impact of this is negligible. The great impact is upon browser complex and maintenance, which have skyrocketed. You know, if you've looked at the number of processes today running, when you launch your web browser, it's like clearly a huge burden now on, on browser developers, like today's operating systems, web browsers are no longer something that can be casually assembled, but the nature of the leakage, these guys have uncovered and demonstrated is different from that because it leverages the non gray area features of our browsers. They're employing features that are there by desire. This suggests in turn that in the future, our web browsers may choose to deliberately strip these side channel features and limit JavaScript's interaction with cross origin domains. And that would probably be a good thing. It's gonna be tough, cuz it's gonna ch change some functionality. But you know, what we've seen is that the, the browser vendors are extremely conscious of this kind of cross origin, privacy leakage, and this paper just unveiled a huge new assortment of ways that can be done. <Affirmative>
Leo Laporte (01:46:14):
Really interesting. Yeah. Yeah. So presumably Chrome Firefox the browser guys, all of them will fix of this. Yes. It's
Steve Gibson (01:46:24):
Fixable, right? Yes. And that's, that's the upside of this kind of research and this kind of testing site, this, I mean, this will immediately subject the browser vendors to significant pressure, which they, they need it's, this is not their fault, but they do need, wanna fix
Leo Laporte (01:46:41):
Pressure now, gray and pet in our discord chat as a question, which I think is, is Jermaine. If you're using a browser that sandboxes tabs, does that keep the cross site scripting from happening, they can't communicate with another one another. Right.
Steve Gibson (01:46:59):
I don't think tab sandboxing would work because in a tab, the JavaScript is using HTTP queries and web sockets to contact to, to, to bring another domain into it. Right. So it's not having to, to talk
Leo Laporte (01:47:18):
Across the tab, the tab it's in one tab, it's in one process.
Steve Gibson (01:47:20):
Exactly. It's all happening on that's on the page. The user is currently visiting.
Leo Laporte (01:47:25):
Apparently there's some sort of container method for Firefox
Steve Gibson (01:47:28):
Well, and Leo, the, the fact that we're seeing red when we click that button yeah. That is, those are effective, successful cross domain probes, right. That, that have just occurred occurred. Right.
Leo Laporte (01:47:43):
Okay. So Grayson, is there a spec special version of a Firefox that container is the various instances? I don't even know if that had help cuz it's all happening within one instance, right?
Steve Gibson (01:47:55):
Yes. It it's on the current it's on the current tab there. He's certainly referring to the tab isolation.
Leo Laporte (01:48:03):
Yeah. That's what I thought he was, but yeah,
Steve Gibson (01:48:04):
Yeah, yeah. And that, and that, that, that's a great point, but here it's, it's in your, you know, in, in, on the page is, is poking at other domains behind your back. And, and so the, the problem is that those domains know about your browser. So when JavaScript on your, on, in your browser pokes at those domains, that the cookies that you have, the other information that your browser has about those domains go along with those queries. And so that's how those, those foreign domains respond differently to you. It's because your browser via the JavaScript running on that page has a ask them something and their behavior subtly changes. When it's you asking versus somebody else asking
Leo Laporte (01:49:00):
So interesting. What that's good research nicely done. It's really well done. Yeah. and of course, so is this show thanks to this guy right here, Mr. Steven Tiberius Gibson, if you wanna we have lots of ways to get this show. Of course you can go right to Steve site, grc.com and get 16 kilo audio as well as 64 kilo audio, if you wanna save on download bites also the transcripts, which he commissions from Elaine Ferris are really good and a great way to search any sec security. Now episode you've got transcripts for all 848. No. Yeah, we, we went back, did them from that's amazing from beginning really makes this a very valuable resource grc.com while you're there pick up Steve's bread and butter, the one and only thing that makes him money. So buy a copy of spin, right? The world's finest mass storage, maintenance and recovery utility 6.0 is, is the current version. But as you can tell, he's working hard at six one, you'll get to participate in the development and get a free upgrade. If you buy it a GRC do com it got lots of other stuff there it's a really completely
Steve Gibson (01:50:10):
Rewritten. And I didn't even change the major
Leo Laporte (01:50:12):
Version number of the darn thing. Yeah. <laugh> yeah. Why didn't you make it spin right. Seven
Steve Gibson (01:50:18):
Cuz I promised everybody a free upgrade, so
Leo Laporte (01:50:21):
Everyone's getting free upgrade. Okay. And, and you also made some promises about what seven might mean and so right. Yeah. Yeah. Seven
Steve Gibson (01:50:28):
Will definitely go further and it'll run on U E F I
Leo Laporte (01:50:30):
Systems that's the big differe and have, and have
Steve Gibson (01:50:32):
Nate well and also have native drivers for USB attached devices and NVMe, which
Leo Laporte (01:50:38):
We're also seeing. So, and it'll basically open it up to Mac users, which is great. Yep. Yeah. So you'll get 6.1 <laugh> but then it's time for 7.0. And if Steve lives long enough <laugh> if I live long enough we'll deliver that as well, but not for free. There you go. Leave feedback at grc.com/feedback. You can also slide into his DMS as the kids say on Twitter, he's SG GRC and his DM are open. So questions or comments could be left there proposals for the picture of the week, that kind of thing. Let's see what else? We have copies of the show on our website. We have 64 kilo auto audio also, but we also have a unique format. We have a video, if you wanna see Steve's mustache in action you can go to TWI to TV slash S N you can also subscribe in your favorite podcast client, which is probably the best way that way you'll get it automatically.
Leo Laporte (01:51:37):
Now let's not forget. And we talked about it earlier. Club TWI is a way to get ad free versions of all the shows at seven bucks a month, you get ad free versions and you get the discord access to the discord, which is great. Just really a great community. That's where Stacy's doing her science fiction book club. That's where we've got the untitled Linux show. Mary Jo Foley just did it ask me anything and we are, I don't know if they've contacted you, but aunt who's our community manager really wants you to do a vitamin D thing for the for the discord. Oh, for the club. That'd be fun. Oh yeah. Okay. Well expect an email cause now he's gotta do it. <Laugh> and all of that stuff ends up. You can watch it live, participate, live in the discord, but it also ends up on the special TWI plus feed, which is also available ad free only to club members.
Leo Laporte (01:52:27):
So take advantage of that and it sure helps us. And, and yes, we have corporate memberships at a reduced rate twit TV slash club TWI. The show we do live Tuesdays right after Mac break weekly, one 30 to 2:00 PM Pacific let's make it 2:00 PM. 5:00 PM Eastern time 2200 UTC, if you wanna watch or listen, live, the stream is@livedottwi.tv. The streams there's several of them. People are watching live are often in the discord in our club or on our free IRC server irc.twi.tv. That's a community run resource, thanks to all of our mods. They're really amazing in there. Starting with OzNet and scooter X and just a great bunch of people in there. That's always a lot of fun and that's free and, and wide open. You can use a browser or, or an IRC client, irc.twi.tv.
Leo Laporte (01:53:20):
We also have forums. Steve's got forums. We had to have 'em. So we have discourse, forums, discourse, not discord@twi.community. We have a Masson instance@twi.social. If you want, if you feel like tweeting in a nice group of people, twi.social, we don't call it tweeting and maam. We call it tweeting. So too long. Don't no, I know. I know what you're thinking. <Laugh> oh, I should also mention beam the one. Yeah, they, yes. <Laugh>, that's exactly what I thought that there, I forget to mention. And I want, I wanna mention this little, it's almost like a tech support note, but we also offer ad free versions of all of the shows as individual subscriptions, iTunes app through apples podcast client. I think there's 2 99 per show. So if you just want security now three less than three bucks a month, it gets security now.
Leo Laporte (01:54:15):
But, and this is a, I think it's a bug in apples system don't be too in much of a hurry to get it there because what happens? We upload the thing and then we, and then the, I there's some disconnect, but it's, but for a brief moment of time, I don't know. It might be like 30 seconds if you, if you're, if you're there, right. When we upload the show, you'll get the version with ads. So a number of people said, wait a minute, I'm gonna, I pay 2 99 there, no be no ads. Yeah, because the way apple does it, it doesn't switch over to the ad free version right away. There's a lag. And we don't know why that is. We've talked to apple. We hope they fix it. But in the meanwhile, don't be in a hurry. If you pay for the ad free version through a podcasts, the apple podcast, apple let Apple's podcast get it.
Leo Laporte (01:55:06):
And I think that should work out our right don't force it. In other words I think that's it. I think we've done everything. <Laugh> Steve, you're the best while you were talking. I was able to find the bug in my day, four solution of advent of code, moving on. Cool. Nice. Oh, I just transposed some lines, you know, it's one of those things I kept getting a weird, I do. Yep. I do gotta put the break higher up in the fourfold. What was I thinking? So we'll see you next time next Tuesday on security now. Thanks buddy.
Speaker 3 (01:55:38):
Have you ever read a tech news story and thought to yourself, man, I would love to talk to the person who wrote this to find out more information. Well, that's exactly what Micah Sergeant and I, Jason, how do E each and every week on tech news weekly, we read the stories that matter to us. We reach out to the people, making a break in the tech news and we invite them on to tell their story and you can find it@twi.tv. Look for tech news weekly, every Thursday
Speaker 4 (01:56:03):
Security. Now