Security Now Episode 914 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for security. Now, Steve Gibson is here. We're gonna talk about the delicate and brittle crypto technology, the elliptic curve technology that has allowed hundreds of Bitcoin wallets to be drained of their value. The latest in the Plex Media server defect that caused the last pass hack and Sony's lawsuit against Quad nine, all over an Evan Essence album. It's next on Security Now,
... (00:00:33):
Podcasts
(00:00:33):
You love
(00:00:35):
From people you trust. This is TWiT.
Leo Laporte (00:00:43):
This is security now with Steve Gibson. Episode 914 Recorded Tuesday, March 14th, 2023. Sony Sues Quad nine. Security now is brought to you by Fortra. The cybersecurity landscape is full of single solution providers, making it easy for unexpected cyber threats to sneak through the cracks. That's why Forres created a stronger, simpler strategy for protection. They're your cybersecurity ally, working to provide peace of mind for every step of your journey. Learn more@fortra.com and by BitWarden. Get the password manager that offers a robust and cost effective solution that drastically increases your chances of staying safe online. Get started with a free trial of teams or enterprise plan, or get started for free across all devices as an individual user at bitwarden.com/twit. And by Plex, the premier cybersecurity reporting and collaboration platform. With PlexTrac, you'll streamline the full workflow from testing to reporting to remediation. Visit plextrak.com/twit to claim your free month at the PlexTrac platform.
Leo Laporte / Steve Gibson (00:01:57):
Today, it's time for security. Now, the show we cover the latest news in the world of security with this guy right here, our master of ceremonies, Steve Gibson. Happy pie day. Steve. Happy pie day to you, Leo. And I was saying before the show that we need a pie day on a Friday, but we don't, we don't have that this time. So this week we've got fewer questions, which required longer answers. And so we're going to answer some questions. What, if anything can be done about the constant appearance of malicious chrome extensions? What's the latest country to decide to pull Chinese telecommunications equipment out? What's the number one way that bad guys penetrate networks? And how has that changed in the past year? What delicate and brittle crypto requirement is responsible for protecting nearly 1 trillion in cryptocurrency and TLS connections? And how can we trust it?
(00:03:04):
What's now known about the Plexed server defect that indirectly triggered the exodus from last pass? And why would the, in the world would Sony Entertainment Germany bring a lawsuit against the innocent nonprofit? Do-Gooder Quad nine d n s provider? Well, stay tuned. The answers to questions you didn't even know you had will be provided during this March 14th pie day 914th episode of security. Now, how many how many decimals of pie can you can you do off the top of your head? We had a, we had a serious geek in high school who used to just bore us with, you know, he was just, and of course we didn't know if he was right or wrong, right? It's like, okay, Richard. Yeah. He said at some point just saying, I, I can do cuz there's a monic. I think George Gamma the physicists came up with it.
(00:04:04):
How I wanna drink alcoholic, of course, after the heavy chapters on quantum mechanics. So 3.1 4 1 5 9 2 6, of course, after five. Wow. Three six, no, seven q u a n t u m seven mechanics, whatever that is. <Laugh>. So I used to, I I, once upon a time, I could rattle it off for like a while. I thought you could. Yeah, yeah, yeah. That was, that was a thing on Pie Day in the grade schools here. When, when Abbey was a kid some years ago, they would have a memorized pie thing and the, they'd have a competition to see who could memorize the most digits of pie, <laugh>. Oh. Which is crazy. I was pretty good with what was that thing that went boo and beep? And it, the, the pattern got longer every time. More Simon Simon, remember? Oh, Simon. Yeah. That's so bad. Bradley Simon.
(00:05:03):
That was a tough one. Yeah. And the advantage was that you, it kept you, you kept reinforcing what you burp, burp, burp, burp and burp. And it only extended by one, one beep each time. Then they came out with, and you probably, you would only know about this if you had kids, something called bop it, that was like a Simon. But you had to do different motions and, and rotate it around. And you had same thing. You had to memorize the order and it would tell you what to do. And then if you got it wrong, I'd go, oh, <laugh>. I'm sure there are people in our audience who remember that. I only know cuz of, cuz again, this was something the kids are into our show today, I should mention, we have a fine sponsor a company you may have heard of before, under a different name today, their fork.
(00:05:47):
But for 40 years, they were known as Help Systems, which actually in some ways was a good name because they were known for helping organizations become more secure, more autonomous. Over the years, customers have told them it's gotten harder and harder to pre protect their data. You probably know that if you listen to this show at all cyber threats, it constantly evolving to become more sneaky and more powerful than ever before. In an industry where the only cons is change, adaptability is the best way to grow in the right direction. You would agree, right? That's why Help Systems listened to their customer's concerns, problem solved and delivered with impressive results. They're a different company today. That's why Help Systems is now for F O R T R A, your cybersecurity ally. Now, some things don't change and should never change. Over the years. Fork continues the same people first support and the best in class portfolio you've come to expect from health help.
(00:06:51):
Systems. You probably know some of the help systems tools. In fact, some of you probably have used Agari or the Fish Lab solutions. We've talked about Fish Labs on the show. Their quarterly threat trends and intelligence report is incredibly valuable. Used all over the industry. They transformed the industry really by creating a stronger line defense. I mean, 40 years ago, were we even thinking about security? But over the years, they have learned that they can do better by giving you everything you need from a single provider. And it's one of the reasons for is used by all 10, the top 10 Fortune 500 banks in the world, all 10 of them use forres to stay secure for infrastructure powers, nuclear power grids, <laugh>. That's pretty important. You get that right, isn't it? And other important infrastructure and utility services. Fortress key area of emphasis is where technology meets, meets people, meets humanity.
(00:07:53):
That includes securing infrastructure, securing data, raising security awareness, operational support. This is important. Nowadays, it's really hard to get the security team you need, right? Portrait offers professional security services to supplement what you've got. Or even in fact, completely replace it. Do you have a pen testing team? You have a red team. They will do pen testing services, security consulting services. They come in, they take a look. It's always good to get a outside perspective on what you're doing, right? Social engineering services, boy, we need that more than ever. We're all subject to spearfishing. It's weird. One of our newest employees, I mean, literally brand new. He is actually our newest employee already. Steve, you'd be interested in this got us text message from somebody purporting to be Lisa Laport, C e o mm, from a Pennsylvania number right now. Now, fortunately, and this is why Fortress so important, our people are well trained to think twice when they see those instead of jumping in.
(00:08:56):
And he did thank you. And let in fact, let Lisa know that's how I know about it. But that's, they're out there. They are really aggressive. I mean, he was just added to our people page like literally a day ago and immediately started getting spearfishing attacks, right? They will help you do your red teaming exercises. They've got managed, managed security services. A lot of people, that's the most cost effective way to get those security professionals in the door. Managed detection and response, managed data loss prevention, IBM Eye security services. Throughout every step of your journey, fork experts are determined to help increase security maturity while decreasing the operational burden that comes with it. If I had to put it in one sentence, that's what they do. And Fortune knows we're all more powerful when we're in it together. So they prioritize collaboration with customers throughout every step of their unique cybersecurity journeys for organizations.
(00:09:51):
Fortune knows the road to creating a stronger, simpler future for cybersecurity. Begins with a daily commitment to listening to each individual concern in providing integrated, scalable solutions. They are customer first, right? Check out all those critical solutions and experts that the for family has to offer. The gari, the Fish Lab Solutions, the quarterly threat trends and intelligence report, which is a really useful resource that provides you with an analysis of the latest findings and insights into key trends shaping the threat landscape. It's kinda like a quarterly security now, right? Forger's approach is different and pursuit of a better future for cybersecurity. They're driven by the belief that nothing is unsolvable fork positive. Changemakers and your relentless ally providing peace of mind through every step of your cybersecurity journey, set yourself up for success, go right now to fortra.com. Check out one of their free trials or demos today, F O R T R A fortra.com. Here's to a stronger, simpler future for cybersecurity. Visit fortra.com to learn more for F O R T R a.com. You knew Help Systems know 'em now, as for, and we thank him so much for supporting the work Steve's doing here at Security Now. And you support us course when you hear this ad and you go to fortra.com, that helps us out a lot too. Do we have a picture? I didn't even look yet. <Laugh>, you're gonna see for the first time right now. So, <laugh>. Oh God. <Laugh>. Oh Lord. <Laugh>.
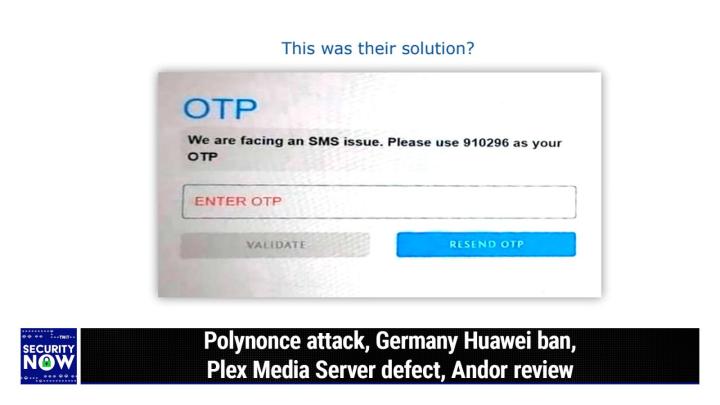
(00:11:27):
Oh, <laugh> set us up. What, what are we gonna see here? Okay, so my, my caption for this is this was their solution <laugh>. And so, so this, and it looks kind of hazy and grainy because this is, one of our listeners took a picture of the screen and and tweeted it to me. And he said, oh, this has gotta be a picture of the week. And indeed, so this is a, you know, you're logging in and you get to the, the one time password prompt for your login. And there's a field where it says enter O T P in red, but above that, apparently they're having some sort of problem. So, so it says we are facing an s m s issue. Please use 9 1 0 2 9 6 as your what time password, <laugh> and Oh, okay. So, and, and what occurred to me was, okay, first of all this is weird, you know, but why not just disable the onetime password challenge for like, while there's an s m s issue, whatever that could be.
(00:12:43):
Rather, rather than hard coding the proper answer for the onetime password field. Wow. Anyway, it's not a fishing, it couldn't be a phish thing, right? I mean, it, there wouldn't be bad guys doing that. No. I can't see how this could do anything. Yeah. Except just be like, well, you know, use this number because, you know, we'll accept it. Now what would really be interesting would be to remember that number and see if it still works. Like after forever we got this problem forever. Yeah. Like after they've got this problem solved, <laugh>, maybe that's the back door. And they thought, well, we'll, you know, we'll change it. In fact we'll see an instance later in the podcast where there's a concern over people having put something in during testing and which they forgot to remove later. But, okay, so first after seeing the details of another Chrome extension that was seriously compromising the privacy and security of more than 160,000 Chrome users, you know, stepping back from this, it feels as though we need a better solution than we have currently.
(00:13:53):
And I don't know of what that would be, but, you know, we have a need for assuring what extensions are doing. Okay? So in this case, the extension was called and, and, and, okay. And it was a little sketchy to begin with, I guess get cookies dot text was, it was actually the name of the extension. And it was being offered by, you know, through the official Chrome web store. So it had been, it had been vetted and, and approved. It allowed users to export from Chrome the content of their cookie files in the old Netscape browser cookie format for presumably so that you had a copy of it. A record of it, you know, or for like, I I, maybe Im importing it somewhere else. Okay. But concerns about the extension were brought to light first of all, a couple months ago in January when a Reddit user discovered that beyond just allowing people to export their cookies from Chrome and, and you know, you'd do that once, right?
(00:15:00):
And then remove the extension. Oh, apparently people weren't. This Reddit user discovered that the extension was tracking users by collecting user and browser data and uploading it on the fly to a remote server. At the time, the Reddit user posted version 1.5 0.0 of the get cookies dot text extension is sending details of every page you visit, not just video sites, but every page back to its developer at the domain. CK dot get cookies text.com. He says specifically for every page you visit, it sends a unique ID for your browser installation, your browser's user agent string, which shows what os you're using and the browser version number, your language setting, the platform you're on the current date time and your current time zone as well as the U R L that, that you're visiting. So that's not good. The u URL you're visiting with a unique ID tracking you, you know, by an extension that has no business whatsoever doing any of that.
(00:16:17):
But then it later came to light that the, after the version was changed, the extension was not only performing that bit of tracking that had been seen in January, I'm sorry, yeah, in January, but that it was also proactively sending entire user cookie files that you had given it permission to acquire in the first place. Sending the entire cookie files back to the extensions publisher. In an update to that Reddit user's initial posting last week, they wrote the situation is now even worse. The extension is now also sending all your cookies to the developer too. When that was confirmed, get cookies dot text was immediately pulled from the store. But that wasn't until the extensions upgrade had been in place for some time. And many users, we don't know how many of the 160,000 who were using it had obtained the update and probably had their entire cookie files, their, you know, all of their Chrome cookies sent to the extensions developer.
(00:17:31):
You know, and of course, after all, what are we constant telling everyone they need to do, stay current with all updates. So update to the latest, get cookies dot text, and unfortunately that <laugh> that hurt you rather than helped you in this case. So, you know, as we know, anytime we either explicitly enable the keep me logged in on this machine checkbox, or anytime a website chooses to do that for us, for whatever reason, you know, on our behalf, this logged on persistence, which is a convenience, you know, significantly since now we're using the web more and more for apps and things that convenience is accomplished by causing the web browser to accept and store a long life persistent cookie in our browsers cash. That cookie identifies us to the site and has the effect of keeping us logged on when, you know, because in individual browser events are separate transactions, the cookie accompanies each one of those queries to the, to to the site, which says, oh yeah, that's Steve again.
(00:18:44):
So anyway, since this is exactly the data that the get cookies dot text extension was caught sending home to its publisher, the publisher was obtaining the static session data needed to impersonate all of the users of its extension at any of the sites where a persistent session cookie may have been set, which is increasingly what's being done. Cuz as I said, we're using browsers more and more as apps. And since the cookie file indicates its expiration date, if any, in the future, it's trivial for the attacker to determine where you're currently logged in. That is to separate the cookies, which are just session, you know, transient session cookies and persistent cookies you being used to permanently log you in. So, for what, for what it's worth, if by any chance you or someone you know as one of that extensions 160,000 users, you should seriously consider taking the time to log out of any websites where you might, where, you know, having some unknown bad guy logging in as you could be a problem if you just, you know, log yourself out, that will render any of those stolen cookies that that ha that may have been exfiltrated from you.
(00:20:05):
Useless. And this takes us back to the question I posed earlier. Like, this is happening all the time, you know, variations on this theme. How do we solve this sort of serious problem? We want our benign browser extensions to be both powerful and capable. You know, otherwise they're not that much used to us. So they need to know how and be able to do dangerous things like have access to our browser global cookie cash, but how could we safely trust extensions from unknown authors, which might have a hidden agenda? You know, I mean, obviously we're putting some trust in the vetting process, which presumably occurred in order for this thing to originally get itself listed. And even though it had a somewhat dubious purpose even day on day one, the fact that it was then able to change what it did, like it, it earned some transient trust for being there for a while.
(00:21:09):
It also earned 160,000 users. And you might be thinking that the, if the extensions developer was always, if their intention was always nefarious, then they may have been, well, they may have well been biding their time waiting for the total user count to get up to a point where they would then incrementally change what this thing did in order to get additional information on their user base until they finally said, okay, it's time for us to cash out and grab everybody's cookie files and see what mischief we can get up to. You know, so today's browser ecosystem doesn't really provide any mechanism for deeply vetting an extensions operation. You know, I mean, that would, that would require more effort than is obviously being put in and, and may be available for free extensions created by unknown people in who knows where you know, it would be prohibitively expensive to be able to fully examine every extension in detail.
(00:22:15):
And, you know, to do that, you'd really have to provide source code, which some extension authors, you know, might feel was putting a bit of a chill on the whole idea. Are they, they're in JavaScript though, aren't they? Or can they be b a binary blob? They, they, there, there was some, there was some requirement that was added after this became a real problem, that the, that the, the extensions not be obfuscated, right? Like, you know, not, not be minimized in order to deliberately make them smaller and to cram out all, all of the, the text and they, and they couldn't be encrypted. But it's still, you know, I mean, you'd have to like, through, you have to deminimize it. You'd have to know how to an obfuscate it. Exactly. And read through every line of this thing. And, and, and it's sort of clever too, cuz I mean, if this was always the guy's goal, then he first came up with something that needed the permission to have access to the cookie cash and had a, you know, a, a valid reason for wanting that.
(00:23:22):
So that would've meant that there was all of this code in there that was, you know, reading and parsing and working with cookies, right? So somebody who casually looked over the script would go, well, yeah, okay, it's doing cookie stuff, so fine. Right? Right. You know, extensions are hazardous. I mean, that's what Tavis Ory was saying when he said, don't use your password extension. And now of course we know Bit Warden has an issue with its extension because it, it gets tricked by eye frames. I I suspect that's a problem with many ex password extensions, but, right. Yeah. Right. Yeah. It's better than just use the app. Interesting. Interesting problem. And yes, exactly, if you can, I mean, but at the same time, look at all the, look at how much, and you gotta cut and paste. Now we're using <laugh>. Yeah. Yeah.
(00:24:09):
Which could be problematic. And also look, look at how much we're using our browsers, right? For we live in them, like, yeah. Yes. Yeah. Yeah. I u I have a ton of browser extensions on Yeah. Including you, block origin, we've talked about that. Yep. Yeah. Yep. in fact, I've got one I love. It's it's a session. It's a session save and restore for Firefox. I'll, I'll, I'll use it in order to, to move all of my work in progress while I'm working on the podcast on, on, on Monday here. I like save all of the tabs that I've got in, in acute little Jason file and send it over to my other location where I'm able to, to op, to open essentially the, exactly the, the, the same state that I was in before, I guess remove any extension you don't need and you're not sure of and Yep, yep.
(00:24:57):
That kind of stuff. And, and here again, for example, are, is it w would it have been those, those users persistent need to export their cookies? You know, it seems to me that's a one time thing. I don't know why you would want to, right? But, you know, install the extension, use it to export your cookies and remove the extension. Yes. Clearly, right? 160,000 people just left it there because, oh, you know, it's not hurting me well mm-hmm. <Affirmative>. Except it was, okay, so following the us, Australia, Canada, New Zealand, Sweden, and Britain, according to reports in German media, the German government is planning to ban the use of Huawei and Z T E equipment from their national 5G telecommunications network. German officials cited the increasingly common fears that Huawei and Z T E equipment could be used for Chinese sabotage and espionage. The German government had previously given the green light for Chinese equipment to be used for its 5G network.
(00:26:02):
And some has already been installed, but the recent Russian invasion of Ukraine of all things, and Russia's attempt to blackmail Germany from aiding Ukraine through its Nord stream natural gas pipeline, excuse me, led to a major change of thinking in Berlin. And, you know, the reporting was that those were the factors, which seems odd, you know, Russia's not China but, you know, apparently the two are a little too close for comfort. According to German media, telcos that previously installed 5G technology from the two vendors may be forced to rip out and replace the equipment. You know, China's understandably unhappy and said that they hope Germany will make their decision one way or the other without any outside interference, meaning primarily from the US trying to be persuasive here. The collection of countries are already on various schedules to remove any existing Huawei and ZTE e equipment from their networks.
(00:26:59):
And, you know, I continued to be distressed that this, because, you know, this seems xenophobic given the lack of concrete evidence, but the argument always is there could very well be no evidence despite equipment being compromised, and congressional expert testimony confirmed that it is virtually impossible to know one way or the other. The good news is the world does appear to finally be waking up to the broad potential for the abuse of today's advanced technologies. You know, I'm hoping that what we're seeing, maybe just a bit of a reflexive reaction to this new awareness, you know, we've all had it right from like, for the last 18 years of this podcast, knowing what was possible. You know, back in the early days of viruses, Leo, we were often just sort of musing over the fact that all they really seemed to do was propagate.
(00:27:58):
They didn't really do anything bad, but we all knew they could. And every so often, one would be a low level formatter or something, which would definitely ruin your day. So I hope that this is gonna calm down over time, and that we'll end up get, you know, reaching some balance point, which is sane. The abbreviation, D F I R is a term in the security industry, stands for Digital Forensics and Incident Response. And there is an annual D F I R report, which is released obviously annually, <laugh>, it came out last week. The report contains a bunch of interesting statistics but probably the most interesting fact because it's like maybe the most significant fact was its breakdown of the way bad guys are still gaining their initial entry into our systems. And I've got in the show notes, a <laugh>, a big pie chart, which is hugely dominated by one big slice of pie.
(00:29:06):
In fact, it's not a slice of pie, it's the pie leftover after you take out the slices of pie. Yeah. Here is an overwhelming sea of blue which represents fishing. The total, the, the way bad guys are still getting in, holding a 69.2% share of intrusion methods where a victim was induced to click on a link or open a document, which in every case was received via email, either through a a, a mass mailing to an, to a, to an organization's employees, hoping that one of them will click on it to get in, or sometimes targeted to a specific individual if in order to make the email, you know, more, more like something that they're expecting to see. So virtually you nearly just shy of 70% of the way the, the, the, the forensic studies are showing people are getting in is somebody on the inside clicking on a link, inviting the bad guys in the D F I R report noted that as in 2021, the previous re re reporting period, also, now last year, 2022, the majority of intrusions originated from mass email campaigns spreading malware in this way.
(00:30:33):
They also noted, and I thought this was very interesting, that one of the biggest shifts in this space was the discontinuation of macro based attacks, leveraging Word and Excel, which was the result of that decision that we talked about at the time last year of Microsoft finally choosing to disable the default execution of macros for Word and Excel. I mean, all, all they had to do and finally did was pop up a warning notice rather than just having them run by default. You know, think about how long that has been the default case, and for how many years before Microsoft did not take this decision. Their users, you know, windows users were being hurt by this widespread use of default execution of macros in Word and Excel. You know, throughout the years before this, we kept lamenting Microsoft how, how they left scripting enabled in email, despite the fact that no one wanted scripting in email, and only the bad guys were abusing that, that battle, that battle to finally disable scripting was won.
(00:31:57):
And now at long last we have, you know, another change was made that, that this report demonstrates re markedly changed the, the, the nature of the attacks. So boy, it just, it's, again, one of the, one of the things we have seen in so many different ways in this podcast is the, the nature of inertia that there, it's just inertia is amazing in all of its many forms. Taking second place in the intrusion entry methods at 15.4% is drive by compromises, which, so those are the watering hole attacks where a malicious website is first set up, and then victims are lured to visit. Or in some cases just opportunistic where, you know, a a malicious site is set up and, and somebody who, who jumps in compromises themself. So that's 15.4%. The remaining two major ways of gaining entry into networks, which completes our pie.
(00:33:07):
They're, they're, they're actually, they share the remaining 15.4% split in half each, getting 7.7%. That's p public facing applications is one of those by which they actually meant the exploitation of Microsoft Exchange when you drill down in the report further. And the abuse of valid accounts is the other 7.7%, meaning brute force remote desktop protocol or SQL server entry in order to get onto a network. So that rounds out a hal all the a hundred percent, but that big blue slice of pie representing nearly 70% of all intrusions and arguably preventable it would take some effort, but it could be done, you know, and we could hope that at some point, somebody at Microsoft will wake up one morning and say something like, Hey, you know, email phishing attacks are a big problem. Why don't we, I don't know, run email in its own sandboxed virtual machine so that bad stuff from the outside is contained and can't take over the entire machine.
(00:34:24):
What do you think? Well, <laugh>, maybe in another decade, we'll get email in a, in a protected sandbox virtual machine. Okay, now Leo, this next one is a biggie. So I think we need to take a break. And then fair enough. Then we'll move pow into, plow into something known as the poly NAS attack. Ohoh. Yeah, uhoh. You don't ever want your NAS to be plowed. I know what a Nance is and I don't wanna be messed with no way. You don't want Polly Nas. Uhuh Security now is brought to you by Bit Warden. Actually we are talking about Bit Warden. I have to say it's really impressive. Bit Warden is the only open source cross platform password manager that could be used at home, at work, on the Go is trusted by millions. Steve used it, I use it. But open source is such an important thing for me.
(00:35:19):
We were talking some, not so many months ago about pbk DF two and how it wasn't maybe the ideal password derivative function that there were memory hard functions like S Script and Argon two. And one of our listeners Ston did a poll request on Bit Warden and, and provided code to add s script as a key derivative function and then provided code to add Argon two as a key derivative function. A couple of weeks ago we were talking about this and I guess Bit Warden came back to him and said, we don't wanna make it too complicated. Let's pick one. And they decided to pick Argon two cuz that was the winner of the, you know, key derivative function competition. And it's added, it's in, if you're using Bit Warden 2020 3.2 or later, which I am, you go into your settings on the website, go to the, the advanced settings and go to Keys and Security and, and you can choose your key derivative function.
(00:36:17):
And yes, there's pbk DF two, but there's also Argon two. I switched over bit Warden has sensible defaults. In fact, I did some research. Everybody agrees Sensible defaults. And it's done and it's fast and it's, and it just gives me a nice feeling, Chris, if you have a good master password, you're probably protected no matter what you do. But still this is, that's a just a nice little extra thing. And that's what Open Source gives you. There's nothing Open Source gives you Bit Warden's basic account is free and free forever. Free forever. So in fact, I asked him, I said, well, you're ever gonna charge for this? Like those other guys didn't. They said, no, no, no, no. That's not our business model at all. Free forever. It's open source. We can't make, we can't charge you for it. <Laugh>. It also means that if you're running a personal account, you can have, you can host your own vault.
(00:37:10):
You don't have to let them host the vault. You can host your own vault and your personal account. And there are even a alternatives servers for that. So you can use Bit Word's official one, although a lot of people like the Rust server that that I think that's probably the most popular among the Geeks. Anyway, then you can host your own vault. Look at that. It's a, it's cool, but it's also really good. It's really good. Now, I don't have to explain to you why you need a password manager. Really the only question in your mind should be, which one should I get? And many of us have switched over to Bit Warden. It's an easy switch. You can export your passwords, import 'em right in, you'll be good to go in minutes bit Warden makes it very easy for you to install it on anywhere you work.
(00:37:57):
It's completely cross-platform. There's even a command line version of it, which I played with the other day. It's awesome. And of course, because all your data is in an end-to-end encrypted Vault. Oh, this's one other thing, one other difference. They encrypt everything. Even the sites you go to visit and the metadata and all that stuff, it's all encrypted. So there's no no information being leaked by Bit Warden. Now, bit Warden accounts they announced are all the new accounts are starting with 600,000 K D F iterations. That's what the o OSP recommendation is now. So you can continue to use pbk DF two and it will be set fine if you want. I set it to 2 million back when that was the only choice worked fine. It's fast. Argon two ID is now an optional alternative. Again, don't do it unless everything everywhere you're using Bit Warden, you're using 2020 3.2 or later.
(00:38:50):
Cuz in the earlier versions it's, it'll say, I don't know what this key derivative function is. That's nothing I know about. So you wanna make sure you're up to date everywhere. A stronger master password, of course, is much more important. And Bit Warden wants you to know that than K D F iteration. So make sure you use as I do, as Steve has explained, a long, strong, unique master password. Where did I see? Oh, so there's a, there's a video very popular video game that you can play. And and it's, let me just get this story cause I want to, I want to tell you the story, right? It's called Roone Scape. And one of the players on Roone Scape he got it to 20,000 hours of playing it, okay? 20,000 hours of playing this game.
(00:39:36):
Single character. His, his name was Dittle Boy, apparently, according to a PC gamer, not a notorious and not a especially beloved figure in the Roone scape community. Why am I mentioning this? He got hacked and, and they renamed his account from Dittle Boy. One two. Same password everywhere. Oh, do <laugh>, don't reuse passwords. But with, with it's easy, with Bit Warden, you don't have to bit Warden will generate great long, strong passwords according to whatever parameters you want for every site. Remember them so you never have to remember them auto fill them if you want. It does master password security checks. New users who create their accounts on mobile apps, browser extensions and desktop apps can automatically check for known data breaches for their master password via H I B P. That's nice. Logging in with a device is now available. That's, I love this.
(00:40:42):
Login requests can be initiated from browser extensions, mobile apps, and desktop apps. So you can just have, I guess I haven't done it yet, I'm gonna do it. It's like a single sign on bit Warden popup and say, you wanna log into this device? Yes, I do. That's much better. I love that. Certainly better than sms. If you are a business, we're moving over to Bit Warden. You should take a look at their teams organization option, which is a $3 per month per user plan. Bigger organizations, I suspect we're gonna use this. Use the enterprise plan $5 a month per user. There's some additional features. Things like sharing private data across departments, making it easy to share passwords across departments. There's always the basic free account. Now, I started with that. I liked it so much, I decided to pay $10 a year just so I could use my YubiKey and to give 'em a little extra funding.
(00:41:33):
There's a family plan too. Six up to six users. They don't even have to be in your family. Up to six users, $3 33 cents a month for the whole thing. That's a great deal. I do use my YubiKey exclusively with my Bit Warden, which is a great feature. I love that. Look, I, it's not a question of whether you should use a password manager, it's only a question of which one you should use. In my opinion, it's a no-brainer. Bit Warden is the only open source cross-platform password manager that can be used at home on the go at work, trusted by millions of individuals, teams, and organizations worldwide. You get started right now with a free trial of a teams or enterprise plan or get started for free forever across all devices with unlimited passwords as an individual. Bit warden.com/twit please, I beg of you, use that address so they know you saw it here.
(00:42:24):
Bit warden.com/twit. We are huge fans of Bit Warden and I think because it's open source, it's just always gonna be ahead of the competition just because users wanna make it better all the time. And it, and it does this, this, this is so exciting, this argon too. Bit warden.com/twit. Now back to Mr. Gibson. And, okay, so this is his Nu not, this is not the Polynesian attack. <Laugh>, this is the, this is the poly NAS attack. <Laugh>. Okay, just to be clear the guys at Kuski Security Research, we've spoken about them before. They've discovered a new and novel attack, which they call poll and we'll see why here shortly which enables this attack. Okay? It is available in instances where a weak pseudo random number generator was used to create a well was, was used in the, in the, in the use of a digital signing algorithm.
(00:43:39):
This allowed them among other things to recover the private keys for hundreds of Bitcoin wallets that which were, which were for transactions that were signed using weak pseudo random number generators. Okay? So I'm gonna sort of give away the story here in, in in their upfront summary, but I think that's a good thing to do cuz then we'll understand where we're headed with this because this is, this is gonna be a bit, a bit of a deep dive, you know make sure that your propeller spring is wound up on your beanie cap. So they said in this blog post, we tell a tale of how we discovered a novel attack against EC D S A. I'll explain what that is in a second and, and <laugh> and why it's important cuz like it's everywhere And how we applied it to data sets we found in the wild, including the Bitcoin and Ethereum networks.
(00:44:43):
Although we didn't recover Satoshi's private key, they said we'd be throwing a party instead of writing this blog post <laugh>. Yeah. They'd be in an island somewhere. <Laugh>. That's right. They said we could see evidence that someone had previously attacked vulnerable wallets with a different exploit and drained them. We cover our journey findings and the rabbit holes we explored. We also provide an academic paper with the details of the attack and open source code implementing it. So people building software and products using E C D S A can ensure they do not have this vulnerability in their systems. Huh? And how they, they said part of the kolsky security research team's activities includes looking into new vulnerabilities and exploits. A few months ago, while researching E C D S A nons attacks, a member of our team discovered a more general way to exploit complex relations between, between NONSENSES to receive to retrieve the signing key.
(00:45:56):
And I'll explain a lot of this here as, as we go along. They said a review of existing literature seemed to confirm that this was indeed a novel insight. So we started digging into it. If you're interested in the math and details surrounding the attack, there's a link to the paper. Okay? So we're about to be hearing a lot about EC D S a, EC D S A is an abbreviation for elliptic curve digital signature algorithm. It is now even still the current state-of-the-art choice for efficiently producing a secure signature of a hash of a message where the signer's key is kept secret and they've published their matching public key, which is then used to verify their signature. So E C D S A is used everywhere. It's the algorithm used to sign Bitcoin, Ethereum, and other cryptocurrency blockchain transactions. It's one of the signature algorithms available to TLS connection handshakes when a site is using an elliptic curve certificate.
(00:47:17):
So the exploitation of poorly chosen random nuances could and would have far-reaching consequences. Okay? So I'm not, I I I'm gonna read what they wrote and not all of it cuz they'd really get into the weeds later. But a and not because I expect anyone to exclaim Oh yes, of course. How obvious No, but because it will give you some sense that this was not trivial and that these guys are geniuses. Oh, and, and if you're listening to this while operating any heavy equipment, please consider pausing your work, what you know during this rough patch. Okay? So they wrote in a nutshell, and yeah, this is the nutshell version. They said the attack looks at the fact that you can always define a recurrence relation among nos used in different E C D S A signatures as a polynomial of arbitrarily high degree with unknown coefficience moo, the order of the curves, generator point <laugh>, we're gonna take their word for that.
(00:48:35):
They said if you have a set of N E C D S A signatures under the same private key and this recurrence relation is of degree D, then under some caveats we'll talk about later, you can use the E C D S A signature equation to rewrite the polynomial in terms of the private key and the recurrence unknown coefficience. Okay? That was the insight that one of these guys had. Obviously they're, they're way deep in the weeds of this. So they said, we have found that the unknown coefficience can be eliminated from the polynomial, which always has the signer's private key among its roots. So if the degree D is low and you have enough such correlated signatures where you, the, the, the number of of signatures is N and you need n to be equal to D plus three, at least then you can perform a key recovery attack.
(00:49:48):
And of course that's the, the key, the, the, the, the, the <laugh> the, the key term here. The, this all boils down to a key recovery attack. They say by simply finding roots of polynomial with known coefficience over a finite field, which they note is an easy task on a computer to run the attack in practice, they said the following is required a minimum of four signatures generated by the same private key, the associated public key, the message hash associated with each signature. And note that all of those will be available anywhere that EC DSA is used. And they said if the nonsenses then the, the what are supposed to be pseudo random, completely random. They said if the NUS obey the recurrence relation, we retrieve the private key used to generate the vulnerable signatures. They said the more signatures, the more signatures used in the attack, the slower it gets, but the more likely it is to succeed.
(00:51:07):
Cuz you know, they've got more information. They said if you attack n signatures with their ns follow a recurrence relation of degree at most N minus three. And the higher the degree of the polynomial, the more the slower and more difficult the attack. So then, but they said if you attack n signatures with their n nos with a recurrence relation of D degree, at least at least N minus three, then you can perform a key recovery attack on EC d s a exclamation point they wrote because that's their discovery. Okay? So, you know, it's big news because it means that the choice of repeated nonces, that is the, the, the choice of the nouns, which is used as part of elliptic curve digital signing must be of high quality for any given repeated signer. Their chosen noes you know, must really be random and by the way, must absolutely never be reused.
(00:52:31):
Reusing anot is like the biggest no-no. So is this related to, remember when NIST kind of cracked an earlier elliptic curve function, not cracked it, but provided constants? Yeah. right. It, it was the, the the, the dr b, the deterministic random bit generator that, that be safe had that RSA was publishing as their default P R N G. And it was shown not to be that good because they used starting seeds that the NSA had specifically chosen <laugh>. Yeah. They used magic numbers and didn't tell anybody where they came from. So this is not the same thing at all. Not, not the same thing. Okay. but, but, so, but, but the, but, but, but so, so far what we've learned is that the E C D S A is everywhere. It is the preferred fast small digital signature algorithm.
(00:53:36):
And it, it, where it is known to be exquisitely sensitive to the quality of the nouns announce must be chosen for each signature and they have to be chosen. Well, what these guys have, what their inspiration was, they basically came up with the attack of if the nos were not being chosen, well now we know actually how to take advantage of that. Ah, so I wonder if I can get it in my wallet this way. <Laugh> <laugh>. This is interesting. Okay. So you can sort of think of it as the price of doing business with EC D S A. Yes. It's a terrific algorithm. It's super secure using very short keys, but it's also quite finicky. It's well known that even a single inadvertent reuse of an EC DSA nos will completely expose the signer's private key. You know, you still gotta do a bunch of math, but it is available so you reuse, announce, and you sacrifice all of the money in your cryptocurrency wallet.
(00:54:52):
Oh, this wouldn't be useful for me though, because they're, look, they can't choose the wallet that they wanna look at. They need to look at all of 'em and look for matches. Right? Is that kind of the way they put, if couldn't just give 'em a wallet and say, is this easy to crack? If you ever transacted with that wallet, if, if you I have, yes. Then there's a possibility. Oh, because the earlier uses, which was when you and I both were messing with this in the beginning Mm. Long time ago. That's why I forgot the password. Yeah. There tended to be a reuse of private keys. In theory E C D S A, you should all, you should have an ephemeral private key also for each signature. You, you, you should just make one up because the, you're able to then tell people what the public key is.
(00:55:40):
You keep the private key secret, but you don't need to always use the same private key. Back in the beginning we were tending to do that. Oh, you were probably doing that. Yeah, I was using the Bitcoin defi, you know, default. Yeah. implementation. Bitcoin core. Bitcoin core. Yeah. Yeah. Oh good. There's hope <laugh>, they said we, yeah. This may be a, this may be a quarter of a million dollar show for me. <Laugh>. Okay, keep going, keep going. Thought they said we tested the attack on a specially crafted set of signatures to verify that it works. It does. In simpler words, they said What our attack means is that every time an E C D S A signature is generated, the signature itself gives us a relation between the NOS and the private key. If the nos are truly randomly generated, this should never be a problem.
(00:56:36):
Because the chance that a number of nos picked at random fit on a low degree polynomial recurrence relation is negligibly small. But there's a catch. They said nos are usually output by a pseudo random number generator rather than being really random. And PR N gs are deterministic algorithms with relatively low complexity in the best scenario. The PRN G used is complex enough and cryptographically secure meaning among other things that any polynomial correlation between its outputs will have such an astronomically large degree that you can safely consider it indi indistinguishable from Truly random. But they said weak PRN gs are basically everywhere. Take for example, the simple case of a linear congential generator that they said L C G, which is the typical textbook introduction to PR n g implementations. Rcgs are to PRN gs what wrote 13 is to encryption <laugh>. And, and 1, 2, 3 is to secure passwords <laugh>.
(00:58:03):
Okay, good. Good. In other words, not good. Not, yeah, not good. And they said despite that due to their simplicity and popularity, they're the default choice for many non critically secure applications. And even that I would be skeptical of. And they said, and it is totally possible that a placeholder L C G implementation slipped into production code without being replaced by a secure one. Okay, now I'm gonna interrupt, I'm gonna do a little segue here for a minute cuz I happened to like linear CONGENTIAL number generators. So I'm gonna talk a little bit about them and how I just used one and then we'll get back to this. So they are, they're very handy for many purposes, but in no way imaginable would anyone consider them secure for any purpose. The entire L C N G linear congruent number generator algorithm is to simply take the current seed, you know, the, the previous number generated, multiply that by a fixed number whose binary representation has a complex bit pattern and sometimes a prime number is used, although it's not necessary, then add a second constant value.
(00:59:31):
That's it. And that's its attraction. A single multiplication followed by, by a constant number, followed by a single edition, by a different constant. So it's not random at all. Oh god, no, Leo, it's just not obvious where it came from, but it exactly, yeah. It's basically, it's jumping forward in the, in, in, in, in its number space by a certain amount. So, you know on the negative side it's entirely predictable given any output it's possible to immediately produce all future and even all previous outputs because you run it backwards, <laugh>, wow, you know, it's awful. So as a source of randomness, the term random, you know, doesn't apply at all. It should never, there should never be an R anywhere near it. What it has going for it however, is speed since nothing could produce a noisy pattern of data faster, which is why as it happens, spin right.
(01:00:37):
Received one a few months ago and since I think everyone will find this interesting, I'll take a minute to explain. A couple months ago we hit an unexpected problem with spin, right? When some very troubled hard drives would encounter some damage they could not handle. Now the proper behavior would be for the drive to stop the transfer and return an error code along with the number of sectors that were successfully transferred prior to that error to prior to it encountering that error that's in the api, that's in the spec. That's what hard drives are supposed to do. And that would allow spin right to then zero in on the one sector that tripped it up and, you know then it would work to recover that sector's data. That's what Spin Wright does. So as I said, that's what drives are supposed to do, but it turns out that many drives, which our testers have, will just hang and wait for spin right to time out the, to to give up and time out the transfer.
(01:01:44):
Or sometimes they'll return a c command, aborted error without any indication of where they were when they became upset. So now we had a problem, previous versions of spin, right? All previous versions of spin, right? Which did all of their work through the system's bios were therefore limited to the bio's maximum 127 sector transfers, which is about 64 K. So spin right would drop out of transferring those 64 K blocks at a time and switch over to single sector mode to locate whatever the, wherever the trouble was that might be occurring at that particular sector. It would, so it would just switch over to and do them one sector at a time to find the problem. Well that worked great for finding one or more troubled sectors within 127 possible problem sector block. But 6.1 achieves its tremendous speed increase by transferring 32,768 sectors at once, which is 16 megabytes rather than 60 4k.
(01:03:01):
So dropping out of that to switch over to one sector at a time was really no longer an option that would, I mean it would take forever. So the solution to this dilemma is why I added a simple linear congruence number generator to spin right, spin right zooms along running at a, at the maximum speed that the drive can go transferring 16 megabytes at a time until it hits a problem. If the drive returns the number of sectors that were successfully transferred as it should then spin, right? Immediately zeros in on that sector, works on its recovery, reaches the con conclusion, then resumes the interrupted transfer with the next sector after the one that caused the interrupt. But if the large transfer stumbles without indicating where among those 32,768 sectors that were requested spin right uses its new linear congential number generator, what it does is it fills that 16 megabyte transfer buffer with one sector of noise pattern repeated over and over 32,768 times.
(01:04:25):
Now spin right, has a known pattern of noise throughout the transfer buffer. So it re-request the same 16 megabyte transfer and this time when the drive craps out without saying where spin right can determine that for itself. It scans forward through that transfer buffer searching for the first sector that matches the noise sector pattern. That will be the first sector in the transfer that was not overwritten by the drives successful reading of sectors. So that's where the transfer was interrupted and that's the sector that spin ride then needs to work on recovering. That's quite clever. That's cool. It's, it's so cool and but it has to be random or you wouldn't know, you wouldn't be sure that you were in right spa place. Exactly. Yeah. You, it has to be random or you wouldn't be sure that the drive might not have contained that data that, that that sector of data uhhuh.
(01:05:25):
Yeah. And you and you'd get a false positive match. So if anyone's been wondering how all this time is being spent, there's an example 6.1 is gonna be far better than spin right? Than, than any spin right. That ever existed before, which is why I'm getting so excited that it's also getting very close. So it's a perfect example of where a linear congential number generator can be useful and come in handy. You, you know, cuz if, for example, there we have zero need for security, you would, you know, you would ne you just don't even consider it a random number generator. We just want noise. Okay. So picking up on this, on, on this team's investigation, they said the Bitcoin blockchain <laugh>, I love this, Leo. The Bitcoin blockchain is basically a large public mine of EC D S A signatures. Oh, <laugh> <laugh>.
(01:06:26):
In fact, they wrote, EC D S A has been used as the default signature algorithm since Bitcoin's creation in 2009. We know that in principle, most ec D S A signatures in the Bitcoin network are ephemeral. That's what I was mentioning before, in the sense that the generating secret key is only used once. But we also know that this practice is not always in place, especially for the older transactions. And also Bitcoin has the advantage that the blocks follow a temporal history, which puts a certain degree of order on the signature generation, although that's only approximate because there's no way to determine the order in which signatures in the same block were generated since the timestamp is only recorded for a block, not per signature. They said, the problem is that these are mainly speculations and we have no clue how accurate all these speculations are.
(01:07:36):
So it's time to verify. We downloaded, they wrote and installed Bitcoin core, the official Bitcoin client, and let it synchronize the whole chain. <Laugh> get loaded. This, the sync process took about a day on a fast fiber connection, and the total blockchain size was about 430 gigabytes up to block number seven, 752,759 on September 5th, 2022. It's bigger today. Yep. Uhhuh <affirmative> dumping all the signatures and original messages from the raw blockchain data took 24 hours. The resulting output file size was 271 gigabytes and contained 763,020,390 unique signatures. This file contained on each line, the output address, the elliptic curve, DSA signature, r n s values, public key transaction id, original message, and block timestamp. We group the signatures by public key and then within each group sorted signatures by timestamp to have more chances of picking consecutive ones. At this point, we had a data set ready to run the attack, but first, here are some statistics about the data set.
(01:09:24):
And actually these are important. So I included them. They said these signatures were produced by private keys associated with 424,549,744 unique public keys. Okay, so 424 million plus unique public keys. Of those 442 million public keys, 390 million, or about 92% produced only one signature. That's good, right? Yes. Okay. Okay. Exactly. Remember that for Bitcoin, private keys are supposed to be ephemeral and are supposed to only be used once. So it's to be expected that 92% of all those signatures would use a completely unique key. Well, you'd like it to be a hundred percent, you would. Yeah. that means there's still hope here. Okay. <laugh>. And, and, and so that means that there's no attack possible on those since, you know, these guys are looking for weak nonsenses occurring during key reuse with the same private key. So they needed to find instances where multiple signatures used the same key.
(01:10:48):
And they did, they wrote there were 34 million public keys with at least two signatures. The, that used in at least two signings, two signatures. Mm-Hmm. <affirmative> 18 million with at least three signatures, 12 million with at least four signatures. Oh boy. 9.6 million with at least five signatures and 7.8 million with at least six signatures. And they said that means six seen elsewhere, five seen elsewhere duplicating six other signatures. Correct. Yeah. Okay. Yes. Yes. So, so that, that is to say the same private, the the same private key was used to sign six transactions. You have a collision with six transactions when you'd expect to have no collisions in trillions of transactions. Right, right. Yeah. Right. So they said there was a considerable number of public keys with over 200,000 signatures. Ooh, <laugh>. Wow. Yeah. Somebody just didn't ever change their public key or, or their, their, their, their private key because the, the, the private key and the pub public keys match.
(01:12:04):
Right, right. It's a one for one relation. The public key associated with the most signatures <laugh> had 3.4 million. Oh my god. Signatures. Yeah. So there was one key shared by 3.4 million accounts. They had the same public key 1, 1, 1 key used in 3.4 million transactions, transactions, not accounts. Okay. Right. Transactions. Transactions, okay. So they said the the attack is generic and can be run with at least n equals four. That is to say where you've got a single a, a single private key used in at least four transactions n equals four signatures. And they call that the linear case. That, that, that, that, that is to say if Ed equals four, then they're solving a, a linear function. Okay. But can also be run with more signatures. And the more you have, the better your chances is. Of course. Yeah. You said, for example, five signatures for the Quadra case and six signatures for the cubic case, or even more signatures.
(01:13:16):
So it gets easier to, to crack with more signatures. It, well, actually it gets harder to crack, but more likely Ah, ah, okay. Yeah. So, so they said the linear case will also detect repeated nuances, but is the, is more general because it can exploit any linear recurrence relation. They said. However, we wanted to go even further and run the Quadra case with n equals five because we thought it might give more interesting results. We considered the cost benefit ratio of performing cubic or higher order attacks to not be worthwhile. So we stopped at the Quadra case. So they'd cost too much compute time, right? Yeah, exactly. Yeah. Meaning batches of five signatures. But notice if you had, if you, if you, you're doing five at a time, but if you had seven signatures, you could slide a window along those seven, taking them, taking them five at a time.
(01:14:19):
Right. Ah, so they said, since we sometimes have more than five signatures associated with a given public key, we decided to perform a sliding window over the signatures sorted by timestamp and run the attack on each window of size N where n equals five. So they said, how did it go? We ran the sliding window attack with n equals five on a 1 28 core vm, and it was completed in two days and 19 hours. The estimated cost of the attack was about 285 US dollars. Probably did it in the cloud. Okay. Oh, they did? Yeah. We broke 762 unique wallets. Oh, is mine in there, <laugh>? Oh, please. I don't think so. Because although you probably haven't checked yours. No. Of these, I don't know even know how to run this attack. Right. Yeah. All of these had a zero balance. Oh, oh. Because they were not the first people there, Leo.
(01:15:32):
Oh, interesting. They'd already been drained. Yes. They said, interestingly enough, we could break all these wallets, not because of a linear or quadra recurrence, but because there was at least one repeated NS in the signatures. So they wrote, it looks like the common mishap of EC D S A implementations using a repeated NS was the cause of the trouble. Oh. So they went to all this effort to try to find a very sophisticated attack. Yep. And what they really uncovered was there was a trivial attack, which had already been uncovered and used Yeah, exactly that. Wow. In other words, these guys developed a highly sophisticated and subtle attack, which they showed would've worked <laugh> and which would've been able to detect subtle failures in NA's choice. But what they stumbled upon during this work was the biggest no-no in the use of elliptic curve dsa, which is a single reuse ever of a nonce when signing under the same private key.
(01:16:50):
Wow. This meant that a trivial attack against those wallets was possible. And what's more, somebody had already done that and Leo, they tracked him down. Oh, my oh, my, because the bit the, you know, it's a ledger. Right? Well, they Cause you transfer the stuff from this account into another account. Exactly. And that account number is not private, it's not hidden. It's public. Exactly. It's a public, it's a blockchain public ledger. They said, this is this exciting, this is great <laugh>. We could have made a whole podcast series out of this <laugh> this should have been security Now season 20. This could have been amazing. Keep going. This is great. They said so since they said, since we only ran the attack using a window of size five so far, we may have missed a few vulnerable wallets that would only have been found for public keys that had exactly four signatures.
(01:17:45):
So we reran the attack with n equals four on only the signatures from wallets with exactly four signatures. We were able to break 11 new wallets with a zero balance and at least one repeated knots, thus increasing the total amount of broken wallets to 773. But the, so in other words, they didn't find any new wallets because again, there was a sim, you know, the, they, they, they were finding a, a superset and it turned out well, there was other repeated non instances. So unfortunately, there were a bunch of people out there who had a bad, you know, who had a, who had a bad Bitcoin client that was reusing nas. When they were doing transactions, and they lost all their money. They said, we suspect, and in some cases have evidence. And they said, as we will discuss later, that all these wallets have zero balance because they have already been hacked in the past due to the repeated nons vulnerability.
(01:18:56):
We also estimated the total theoretical amount of tokens that may have been stolen from these seven hundred and seventy, seventy three wallets to be 484 Bitcoin at a value of approximately 31 million US dollars at Bitcoin's peak. Well, one thing that's good is, since I know there's still Bitcoin in my wallet, I'm not one of those You're not Yes. Duplicated nons wallets. Yes. Yeah. Okay. So anyway, I then they go on at length talking about various other attacks. Those are the rabbit holes that they refer to, and they talk about all the evidence of, you know, they identified a number of actors and they found the person who, you know the, the Bitcoin address that, that essentially made these transfers. Anyway, they, they conclude saying, so since we aren't sipping mojitos on a beach in some exotic location, <laugh>, you can tell we did not gate access to Satoshi's wallet <laugh>, but we recovered the, well, they might have, it's just that somebody got first It could, I guess.
(01:20:08):
No. Oh, I guess actually, doesn't Kohi have an insane number of Bitcoin? Oh, yeah. Billions. Bitcoin billion, billions and billions of dollars. Yeah. Yeah. So he, they, they said, we recovered the private key of some Bitcoin wallets showing that the attack works. We only scratched the surface by looking at Bitcoin, Ethereum, and some TLS connections with this initial look. We wanted to ensure that an attacker could not cause financial damage before releasing the details. But there are many other locations where elliptic curve DSA is used, such as additional blockchains, batches of PGP signatures, other TLS connections and embedded devices just to name a few. We release this information along with code so that people and organizations can proactively ensure they're secure against these attacks and create more robust systems. We hope you find this useful. What would be your fix for this? Somebody's asking in the chat room.
(01:21:11):
It wouldn't be changing your password. You'd probably transfer it out of your old wallet, make a new wallet and transfer it into a newer wallet where presumably this not won't be reused. So, yeah. So you absolutely. Well, so nons reuse is never a problem if as long as you're do, as long as you're not reusing your private key, the easy thing to do Oh, is make sure you get a new private key for e for every transaction. Okay? Okay. Yes. And that's why 93% or 92%, whatever it was, of all transactions are using unique private keys. Everyone should have a client doing that. Okay. In the, in the earliest days, people were not doing that. So these are all older wallets. Yeah, yeah. Yes. They, they, they, well, they're older transactions. Transactions. Right. And so the, so those would've been older transactions using older Bitcoin clients.
(01:22:04):
I wonder if bitcoin core now, I'm sure it now re keys each time, I would say, given that 92% of all transactions are that, that must be the case. And they're, and they're supposed to be, but they're, you know, they're not always right. You know, again, everybody, you know, there's like all these different bitcoin gizmos out there, right? And some of them just aren't well made. And some of them are apparently, not only are they U reu not bothering to, to use a, a new private key for every transaction. They're also who knows how, how could you reuse a nonce? How, how, how could you get anything that you thought was even, that you even thought was supposed to be random <laugh> and get it twice <laugh>? Wow. Wow. So, you know, is, there are a couple of takeaway lessons here. One is that details really matter, right?
(01:22:53):
The crypto gurus who invent and create these algorithms, admonish their implementers that if they wanna take advantage of the elegant though quite finicky E ec d s A algorithm, they're gonna really need to be double damned certain to only ever use it with truly high quality random nos in an application where they need to have a static signature. And most signature, most elliptic curve DSA signatures are static, right? It's like if, if you have an elliptic curve TLS certificate, that's not changing. So you're depending in that instance on the quality of the nouns being highly random. But, so the point is, yes, it's a great algorithm, but you gotta use it correctly. And the second takeaway takeaway, I think, is in the form of a question, if details like that really matter that much, if a critical algorithm is so brittle and sensitive to difficult to control implementation mistakes, should it be chosen and used mm-hmm. <Affirmative>
(01:24:08):
In critical applications, you know, because it's no longer the case that only one of these is ever made. Bitcoin went crazy and everybody said, oh, I'm gonna create a wallet. I'm gonna, you know, I'm gonna create my, you know, my own, because why not? Let's write it in JavaScript <laugh>. So, you know should it be chosen and used in critical applications such as to protect the storage of hundreds of billions of dollars in cryptocurrency wealth. And by the way, huh, I was curious if anybody else is as to as of the beginning of this year, total wealth stored in cryptocurrency was 804 billion with around 320 billion of that in Bitcoin. Hmm. So, you know, this is the sort of way these things happen, right? We see it over and over. The inventors of the packet switching internet could have never foreseen what their experiment grew into.
(01:25:17):
And yes, for all that, it's amazing. It also has some weaknesses in the face of deliberate abuse. And with Bitcoin as a proof of concept, Satoshi invents and designs an intriguing system, and he chose elliptic Curve DSA to sign transactions because Sure. It's the best though. It also needs to be handled with extreme care. Little could he have possibly known what his experiment would to grow into. And in retrospect, choosing something less fragile, some less fragile crypto would've probably been a better choice for something that has, you know, was to grow into a global phenomenon. And of course, he could have never predicted what was to come. So I use curve 25 5 19. That's an elliptic curve, but that's not, it's different. That's probably not using dsa. Right? well, although it is the default signing so we, we'd have to look and see which of, so, so 2 55 19 is one particular very popular elliptic curve.
(01:26:30):
Mm-Hmm. <affirmative>, there are other elliptic curves. But, but all of them then share the, the same set of algorithms right. On these d which are put on these different elliptic curves. So I use it in my, with SSH primarily. I shouldn't be announcing this, but that's what I use primarily use it for. Yeah. Every, I mean that, that, that's what squirrel uses. Yeah. Same. I, I, I also chose 2 5 5 19. It's, it's also because the keys are short and easily copied and pasted. In my case, it was because it had some particular proffers properties that Dan Bernstein, who is the inventor of, of 2 55 19. It's got some really cool properties that enabled the use of, you know, en enabled squirrels. Crypto. Yeah. Okay. I won't worry. Very cool. And I, and since my coins are still in my wallet, I guess I don't have to worry about this attack either.
(01:27:24):
Wow. It doesn't really matter. I can't get to him anyway, so I think we, we we're at an hour and 18. Let, let's a break. Let's take our third break. Yeah, yeah. And then we will continue. Yeah. And you know, what, if, if the wallet had had been emptied, I would say, well, I'm glad somebody got the use of <laugh>. Oh, Lord, what a world. Huh? This this episode of Security now brought to you by a great sponsor. We love so much. Plextrac, the purple teaming platform. Plextrac is your security team's secret weapon, the premier cybersecurity reporting and collaboration platform. It transforms the way cybersecurity work gets done. If you've got a red team, if you've got a Blue team, if you've got a purple team, you need PlexTrac. You know, you do assessments. If you do pen testing, you make reports, you need PlexTrac.
(01:28:18):
If you're ready to gain control over all those tools, you use all that data you're generating, and you're, and you're your pen testing and your security testing if you're in interested in building more actionable reports, and then allowing you to focus on the right remediation. If you're working to mature your security posture, but struggling to optimize efficiency and f facilitate collaboration within your team, I got the solution for you. Plextrac, P L E X T R A C. It's a powerful and yet easy to use cybersecurity platform that centralizes all your security assessments, your pen test reports, your audit findings, your vulnerability tracking, it transforms. The risk management lifecycle, let's your security team generate better reports with less typing faster you can aggregate and visualize analytics. Yeah, it's very visual. You can collaborate on remediation in real time. It just streamlines the security process.
(01:29:20):
It, how does it do it? Well, the PlexTrac platform has addressed specific pain points within the spectrum of security team workflows. Things like, well, let's talk about offensive testing. It's second to none for managing your offensive testing. And then reporting security findings. And when I say report, I don't mean just like a lot of paragraph of pros, I mean code samples and screenshots. Even videos can be added to any finding. You can import findings from all the tools you use, Nesta, burp, whatever you use. You can export to custom templates with a click of a button. So once you've set up that templates really easy to get the reports in there. Analytics and service level agreement functions let you visualize your security posture so you can quickly assess and prioritize. Make sure you're tracking remediation efforts to show progress over time. It's got complete built-in compatibility with all the industry tools that you would use are frameworks, including vulnerability, scanners, and pen testing.
(01:30:23):
As a service platforms and bug bounty tools and adversary emulation plans, it lets you improve the effectiveness and efficiency of your current workflow. Robust integrations with Jira and ServiceNow mean you're always closing the loop on the highest priority findings. Fixing those tickets. Enterprise security teams can use PlexTrac to streamline their pen tests, their security assessments, their incidents, response reports, and much more. Plextrac clients tell us they love it, up to 60% reduction in time spent reporting 30% increase in efficiency and a five x R o I in year one. All in all, PlexTrac provides a single source of truth for all stakeholders, transforming the cybersecurity management life cycle. So here, here's what I want you to do. Book a demo today, you, you will see how much time PlexTrac can save you. Try PlexTrac free for one month, see how it can improve the effectiveness and efficiency of your security team.
(01:31:24):
All you have to do is go to plextrak.com/twit, claim that free month, P L E X T r A c.com/t i t plex, track your security team's secret weapon, and we thank 'em so much for supporting security. Now, I hope we've got the message out, and if you heard it and you wanna try it out, please do us a favor and use that special address so they know you saw it here. Plex track.com/twit/twit. All right, fair enough. Now, let's get on with the show Mr. Gibson. Now there is no relation between PlexTrac and the Plexed server. No. Oh. So let's hope not make that clear. Oh, no. Last week we were talking about the growth of S'S K E V database you know, where K E V is the abbreviation for known exploited vulnerabilities and how, while it grew much faster last year than in any previous year, an examination of the dates of the CVEs that were added during this most recent past year revealed that the large majority of these were not new problems being exploited.
(01:32:39):
Oh. But rather old problems that had never been patented. So I noted that CISA had just added C V E 20 20 57. 41. 2020. That's three years old. That's three years old. That's right. Old. And what is 57 41? You might ask. Well, it's a derealization flaw of untrusted data, which was found as we noted three years ago in the Plex Media server for Windows. But who would be, who would be running three year old unpatched versions of Plex on their Windows machines? Who indeed, who indeed my friend. It happened that an unfortunate LastPass developer. Oh, <laugh>, yes. Was doing so after which a distinct lack of fortune was visited upon all last pass users. That's a good way to put it. <Laugh>,
(01:33:42):
A remote unauthenticated attacker is able to execute their arbitrary Python code on the victim's computer. Can we make it any easier? Only so we now, now we know that this developer was using a publicly exposed Plex media server, which was three years out of date since of course, C V E 20 20 57 41 had been found, was known and had been fixed. I've been saying for a while now that any serious cyber warfare agency or group across the globe must be maintaining a vulnerability and exploit database indexed by target vendor. So in the instance of this second last pass attack, last passes, developers were identified probably with the eight of the first attack on that developer network. Right? Then they were tracked down and identified at home, and their home IP addresses were scanned. When Port 32, 400 was found to be accepting inbound TCP connections at one of those ips, that port was looked up and the Plexed server was found to be the most common user of that port.
(01:35:11):
Then the attacker's master vulnerability and exploit database was queried for Plex. And a three year old remotely exploitable vulnerability stood out. Could we be this lucky? The attackers probably thought to themselves, and indeed they were. And we weren't. I know a little Python take advantage of this governor. That's right. And I don't know if anything was more has been learned, but I did hear something about North Korea being the oh, really? The pres the presumed source of the attack. Yeah. The thing that makes me scared. It was so clearly targeted against last poet. Yeah. And that means they knew what they wanted, which is the vaults, which means I presume they knew what to do with them.
(01:36:05):
Yeah. Yeah. Which is the reason <laugh> we're no longer all using Last pass. Yeah. okay. One quick random note, and then we're gonna talk about Sony suing Quad nine. I wanted to mention Andor Leo. Yeah. It's good, isn't it? In a word. In a word. Wow. Yeah. And, and of course there'll be no spoilers here, but I wanna set the stage a little bit and give our listeners just a bit of background to raise their curiosity level. And if you're someone who wants to hear absolutely nothing in advance, then skip forward 60 seconds. Andor presents the story of an orphan Cassian Andor. The series is set well before the events of Luke and his princess sister. It tells the story of the early rise of the Empire as it gradually displaces corporate rule for imperial rule and tightens its grip on the galaxy's citizenry, which is increasingly becoming stratified into upper and lower casts. Mostly Cassian just wants to be left alone. He grew up hard and survives by reselling tech that he steals from around the fringes of the imperium. Despite being raised by an adopted mother who's been seeing what's happening to the galaxy and wants to rebel, he has zero interest in any cause. He holds no such ideals. He just wants to be left alone and not be told what to do. Over the course of these first 12 beautifully crafted episodes, we watched that change.
(01:37:50):
If you don't already subscribe to Disney Plus, I cannot imagine that you would regret subscribing just long enough to watch this first 12 season or 12 episode season. There might even be a free, you know, trial period available to new subscribers. I was not offered one because a year or two ago, after watching the first season of the Mandalorian, I canceled my subscription. The Mandalorian wasn't horrible, and Lori loved Baby Yoda. I kept hearing Oh, but neither did it strike me as being all that great. It's just a rubber puppet <laugh>. That's so cute. Oh, anyway, but, and or is another thing entirely. And Leo, I think that this very sober and serious series may be the best Star Wars property I've ever watched. I agree. And I, I think it is because it's very little Star Wars <laugh> in a way. Right? Right. There's no, there, there's no, who is that Ussa, WSA Gua thing?
(01:38:57):
No, none of that stuff. The floppy ears. No. Jar Jar. No. The Jar Jar bins. There's no Ewoks. I haven't seen the last episode yet, but I don't even think there's any lightsabers. Maybe there is towards the end, but, oh, but Leo, that the, that fight scene in the second to last episode, so good. Oh my God, so good. Yeah, <laugh>. So it's, and a number of people told me this, it's a good Star Wars show if you're not, if you don't really want a Star Wars movie, but, but there is that undercurrent, which you mentioned of we're seeing the Beat Rise of the Empire. Yes. So if you're a Star Wars fan, you'll like it. And there's a lot of, you know, there's Tie Fighters, there's Star Wars technology unit, but yeah. And, and it's said, it's a good story. As Lori said it, it has a lot of pew, pew, pew, pew, pew, pew, pew, pew.
(01:39:42):
It does. And the stormtroopers are still lousy shots, but, okay. You know, oh yeah. I thought it was really, really, really good. Yeah. Very, very good. Anyway, so, you know, we talked about The Expanse. We love the Expanse. This is, and, and again, if you hate Star Wars, I would say, I think you're right, Leo. Forgive it for being set in that universe. Yeah. Cuz it's barely Star Wars. And the other thing I thought was really interesting is the rebels are shown to be, they're just as ruthless as the Empire in their own way. I mean, it's not, it's not, you know, sugar coated and lollipops. It's, it's, it's a, it's more of a gritty kind of real. Yeah. Somebody says like a spy story, don't It is, it's a little more like, it would be a, if you took away the Star tour Star Wars trappings, it'd be the same story.
(01:40:30):
Same show. Oh. And, and boy, it is, there are some people you love to hate. I mean, there's beautifully, there's bad people in it. Bad, yeah. Yeah. So, by all means, watch the last one. It has a great ending. You won't be disappointed. Yeah, yeah. No, I've been saving it and I just can't wait for the next season. It's like, oh, come on, <laugh>. Let's keep going. Yeah. Okay. So I chose the news of Sony's lawsuit against a well-known and well-respected d n s provider because a very dangerous legal precedent threatens to take hold on the internet. Here's how the defendants Quad nine summarize the situation and its danger. They wrote Sony Music Entertainment. Germany is litigating against Quad nine, requiring us to block access to a website that links to a site containing files that Sony asserts are violating their copyright. We maintain that Sony's request essentially amounts to content censorship and risks cracking the foundations of a free and open internet in Europe and potentially worldwide censorship in turn, can lead to undue restrictions on freedom of speech.
(01:41:58):
And just, I'll, I'll just briefly say that for, for those of our listeners who were not here, Leo, for episode 12 of this podcast, this is not the first time Sony has earned some negative coverage and been named, oh, I'm starting to hate them, to be honest, in this po in this podcast's title. Yeah. Episode 12, dated November 3rd, 2005, ran all of 24 minutes. Its title was Sony's Root Kit Technology, d r m, copy Protection Gone Bad 24 minutes. Really? <laugh>. Yes. <laugh>, you said, Hey Steve, why don't you come, you know, maybe just like half an hour and tell us what's been going on every week. Not much to say, but that's right. We do it in half an hour. Yeah. Since those early days, Sony has had their troubles, and they do tend to be litigious When they confine someone, anyone to sue. They're happy to throw their, their weight around without much provocation.
(01:43:05):
So now to this issue today, we've talked about Quad nine in the past. They're a bunch of good people. Quad nine is a free global public recursive, d n dns resolver, meaning that anyone in the world can ask them to look up the IP address associated with a domain. And they will do that by asking whatever other d n SRS may be needed to come up with a final answer, thus recursive. But Quad nine is also explicitly a filtering d n s resolver. In fact, that's its purpose. It aims to protect its users by not returning the IP addresses of sites known to be malicious. Quad nine is operated by the Quad nine Foundation, a Swiss public benefit nonprofit foundation headquartered in Zurich, Switzerland, whose sole purpose is improving the privacy and cybersecurity of internet users. Quad nine has 200 points of presence globally spread around 90 countries from which they provide these services to individuals and organizations at no charge.
(01:44:15):
Here's the language from the court, which supports the position that Sony's attorneys have described. This is, this is taken directly from the official court order. They said the defendant is ordered to refrain from selling on the territory of the Federal Republic of Germany. The music album Evanescence the Bitter Truth fine with the sound refr fine. <Laugh>, exactly. Okay. Don't want it. Don't want it. Happy not to, not, not to sell that with the sound recordings contained there on to be made publicly available by the defendant providing its users with a DNS resolver service, which the domain, excuse me, Canna, c a n n ato and or the subdomain yuu.canna.to it translates into numeric IP addresses so that it is possible for the users of the defendant with the help of these numerical IP addresses to reach the internet service under the domain Canada to and or the subdomain eu.canada.to and or the further domains, and to call up their links to unlawful storage of the album as happened by the defendant offering its users the DNS resolver service Quad nine at the IP address, 9.9 0.99 with the help of which the users with the links.
(01:46:05):
And then the court order has four links. Two of them are eu.canada.to links, you know, with some, you know specification of in the url. And Canna SX and Canada do power to, they said numeric IP addresses were transmitted, which enabled them to access the hyperlinks provided at the A four mentioned addresses to the storage locations of, and then there's two links@shareplace.org and some, some hicks stuff. So that's the actual pirate site share place.org that is offering up this material. And they finish and call up the illegally stored copies of the Affor mentioned album. So, in other words, there's no misunderstanding here with the court about the essentially passive role that D n s and A D N S service provides. Another piece of the official proceedings was also interesting. They described the efforts that Sony first went through in doing what we would all agree was the right thing for them to do.
(01:47:24):
Here's where the document, the court document describes. They said, music content is listed and categorized under the domain. Www.Kana.To the domain of the website is Kana Power in a letter dated March 23rd, 2021. Okay. So note that this has been going on for two years. The plaintiff, meaning Sony drew the defendant's meaning Quad nine, attention to the infringement and also pointed out the U R L. The defendant was requested to put an end to the infringement. The defendant Quad nine was warned after it failed to remedy the situation the plaintiff Sony had made every here it is. The plaintiff had made every conceivable effort to remove the infringing offer with the involvement of primary liable parties. The Can of Power website has no imprint. Entries on the, on the domain owner were also not available. Oh, requests for deletion to the hosting provider went unanswered. Oh no.
(01:48:46):
Nobody answered the phone. Their two ips were named The company Infinium. UAB B with an administrative and technical contact in the Ukraine was identified as the responsible Organization. Organization. The company was allegedly based in villainous Lithuania. There, however, a delivery by courier could not take place due to the lack of a traceable signature in Ukraine. Delivery was not possible because the address was located in a high security area, to which it was not possible to accept deliveries without express consent. This consent had been refused. Okay. <laugh>. So, in other words, the actual copyright infringers are out of reach of Sony's wrath from, from what the court wrote, it doesn't really sound as though Sony tried that very hard to go after the primary sources. The court wrote that Sony had made every conceivable effort to remove the infringing offer with the involvement of primary liable parties.
(01:50:01):
But can a powers hosting provider what didn't answer the phone? So that was it. There we can't, we can't serve them. Yeah, we could. So Sony unwilling to be stymied and denied, decided to attack someone who was within their reach. The court wrote, the plaintiff is of the opinion that is Sony <laugh> is of the opinion that the defendant is liable as a tort fior. Now I had to look that one up. The short ver the short version of the definition of tort fior is a tort fior is a person or entity who is found to be responsible under civil law for an injury caused to another person or entity. In other words, Sony is claiming that because Quad nine provides some of the internet glue mechanics that are required for users to reach the Canna Power website, given its domain name and, and note only Quad nine users not out, not all the rest of us, they Quad nine, are thereby responsible under civil law for the injury caused to Sony.
(01:51:20):
Wow. The court wrote, according to recent case law, it meaning Quad nine is also liable as a perpetrator of a copyright infringement. Okay. Now, unfortunately, we would not be talking about this insanity. Ifer heads had prevailed and, you know, today's podcast would then have a different title. The final decision of the leap Zig District Court was to rule in Sony's favor ordering Quad nine, to block all access to the count to canna powered domains globally. Now, as we all know, quad Nine's action of complying with this court order will have zero effect on anyone who does not have 9.9 0.99 configured as their DNS resolver all of the rest of us. Of course, it won't have any effect on those people Anyway, listening to this podcast, we're cuz we're not gonna be pirating music from can power. All of the rest of us can access those can power URLs without any trouble.
(01:52:29):
So this action by Sony only makes any sense if this is just the first such legal actions, which Sony intends to use as to set a precedent, a legal precedent for other similar actions against other d n s providers. And that's another thing that doesn't, doesn't really make any sense because the world is also full of d n s providers, many of whom do not care and couldn't care less about making Sony happy and they're not gonna take this action. What would've made much more sense from a technology standpoint would've been for Sony to contact the responsible and definitely reachable top level domain provider for the dott. T L D dot T is the internet country code top level domain for the Kingdom of Tonga and is administered by the Tonga Network Information Center. And they do pick up the phone by changing the d n s name server entries for those KANA power domains.
(01:53:44):
D n s would've disappeared globally once downstream cash has expired. But that's not what Sony chose to do. Five days after this judgment, which came down on March 1st, presumably having recovered from the decision, quad nine posted their response. They said Quad nine has been part of a potentially president setting legal case involving Sony music On March 1st leap, Zig Regional Court ruled in favor of Sony Music. This ruling means that Quad Nine has no choice but to block the domains in question at a global scale as directed by the court that said Quad nine is far from ready to give up the fight in terms of protecting users access to information. Quad nine is shocked that the court ruled in favor of Sony music, but they are not disheartened and will continue fighting for the freedom of access to information by citizens around the globe. Quad nine feels they were chosen as a target because as a nonprofit player with a limited budget and small market share, Sony potentially did not expect Quad nine to have the means of fighting back.
(01:55:00):
This would be an easier means of es this would be an easier means of establishing legal precedent to potentially control domains served by all d n s recursive resolvers. Although Quad Nine is complying with the ruling in the interim, there are several points that they feel should be brought to the attention of citizens around the globe who value privacy and freedom of access to information on the internet as the potential implications of the ruling could reach a global scale. German court decisions are normally limited to Germany, which is why Quad nine has implemented G O I P on its infrastructure in Germany to restrict the domain names in question from being resolved for users querying from Germany. However, there are loopholes such as VPNs beyond Quad Nine's control. The court deemed this not to be sufficient. The court's decision ignored the VPN concept. It implies that Quad nine must block these domains regardless of how users reach them or from what nation those intentionally disguised queries originate.
(01:56:16):
Quad nine believes this is an exceptionally dangerous precedent that could lead to future global reaching, commercialization and potential political censorship. If d n s blocking is applied globally without geographic limitations to certain jurisdictions, the court did not apply the rules of the German Telemedia Act. Consequently, which sounds a little bit like our Section two 30 said, they said consequently Quad nine does not enjoy the associated limitations from liability. Quad nine also believes that it should benefit from these exemptions from liability, particularly since the European lawmakers have noted in the recently adopted Digital Services Act that providers of services establishing and facilitating the underlying logical architecture and proper functioning of the internet, including technical auxiliary functions, can also benefit from the exemptions from liability and explicitly mentioned providers of D N S services. In other words, it sounds like they have a strong case here on appeal.
(01:57:25):
The court established that Quad nine accepted the wrong doer liability. Quad nine feels this application of the wrong doer liability is absurdly extreme given the circumstances to, and that must make an exception to the German Telemedia Act to put this into perspective, applying wrong dire doer liability in this setting as akin to charging a pen manufacturer with fraud because a stranger forged documents while using the manufacturer's writing utensil. Yeah. Anyway, I agree with they go on, but you know, it's very annoying. I mean, it is really, really wrong. So oh, and I wanted to share one additional posting that Quad nine published two days later since it contains some important points and principles about responsibility with dns. They said the Sony Music Entertainment Germany versus Quad nine Foundation case has brought to light a concerning issue regarding the implementation of blocking measures by d n s recursive resolvers.
(01:58:32):
In addition to concerns around sovereignty and judicial overreach, it is essential to recognize that d n s recursive resolvers are not the appropriate place to implement this type of blocking. Dns recursive resolvers play a crucial role in the functioning of the internet by translating domain names into IP addresses. However, they should not act as gatekeepers for content, which can be subjective and varies from jurisdiction to jurisdiction. Users of Quad nine opt in to our service and want the cyber protection that we enable for them. Blocking a domain for distributing malware is motivated by the desire prote to protect users from malicious or harmful content such as viruses, phishing scams, or other threats. These types of protective d n s services. Blocking a domain from malware is a form of user opt-in filtering. The intention is to protect users from harm and does not necessarily involve restricting access to specific types of content.
(01:59:42):
Blocking a website based on its content is censorship since it involves restricting access to specific information based on someone else's standards or values. Rather than allowing individuals to choose what content they wish to access, most people would like to avoid ransomware on their computers. Still. They might wanna browse a website with a specific set of content or an ideological perspective with which we disagree. Blocking a website based on some or all of its content is often motivated by a desire to restrict access to specific types of content. Recognizing that DNS recursive resolvers are not the appropriate place to implement content Blocking measures is critical. Arbitrary blocking of content related domains places an undue burden on dns, recursive resolvers to police online content. Dns recursive resolver operators don't have the legal expertise or access to additional information that might be required to decide what content is legal or illegal.
(02:00:56):
And finally, in this ruling, dns, recursive resolvers end up with more culpability and liability for content than social media networks. Concerns around copyright infringement and online privacy are valid and the courts should address them. Inappropriate venues fighting solutions that do not compromise internet user security and respect other nation's sovereignty is crucial. So, oh, and, and in a, in a, in a little, in a one line, one sentence transparency report that they published. They said quad nine's domain blocking policy blocks, malicious domains associated with phishing, malware, stalker wear and command and control botnets. Our threat intelligence data comes from trusted cybersecurity partners, not arbitrary corporations or governments. Our policy has been to block malicious domains and not moderate content disputes. So I am certainly glad that they're gonna appeal the decision and I hope that this ruling will have caught the attention of many other larger entities who share a vested interest in not allowing this single ruling to establish what is clearly the wrong precedent.
(02:02:20):
You know, it's so clear that pursuing legal remedies against the actual publisher of the infringing material, which is what it we've always done before, right? I mean, that's, that's what's happened before. That's the right thing to do. The law should not be about the easy target. It should be about the infringing target. The fact that it may be difficult to hold the infringer to account should not mean that arbitrary and completely unrelated components of internet infrastructure should become an alternative, an alternative target. You know, that's just nuts. Although, you know, as I'm saying that Leo occurs to me that we have seen the situation where, where the, the copyright holders are going after the downloaders of the content, right? I mean they're, well that's sensible, right? Those are the ones who were actually you're infringing and you're exactly, you're obtaining the content Yeah. At, at each end from the person who is serving it and then the person who's consuming it, what the Yeah, it's hard for them to do that.
(02:03:20):
They tried a bunch of John Doe you know, cuz it's hard to get the identity right. They have the IP address, that's all they have. And they've tried a bunch of John Doe lawsuits. Remember that didn't go very well for the music industry. It turned out to be a black mark for them. Then they went after the ISPs. They still do with that three strikes thing. It's a long, ugly history of, and it, and as far as I can tell, it's, it's accomplished zero. Right. And that's really the main thing to say is it doesn't stop piracy. It doesn't work. It just makes it bad for the rest of us.
(02:03:52):
Yeah. Oh, well anyway the, they are asking for help and support. I'm hoping that, you know, the e f and and other Yeah. Other organizations that have some deep pockets would be able to, to, to, you know, to help these guys. And I, I'll promise to Sony, I'm never gonna download or even listen to an Evanescence album at all. Ever. Yep. Congratulations, <laugh>. And if and if you're evanescence, you might wanna look for a new label. Yeah. because they're doing this on your behalf. This is what happened is the rec is the, is the artists told the record companies knock it off. You're punishing our, our our audience, our reputation and and hurting our reputation. Exactly. good stuff. Thank you Steve. This is a good show. A lot of good information. You could easily have made that electric curve story, the story of the week.
(02:04:47):
But you had two good ones. Two, two, count 'em two. And that's why everybody waits with baited breath for Tuesday so they can listen to security now. Now, a couple of ways you can do that. Of course you can watch us do it live. If you want the very freshest version, we record the show right after Mac Break Weekly. Usually that's between one 30 and 2:00 PM Pacific. That'd be around about 5:00 PM Eastern time, 2100 utc. The livestream audio or video available at twit tv slash live. If you're watching live, of course there's a chat room, couple of chat rooms chatting live, the irc IRC TWIT tv and our club members chat in the club. Twit Discord, that's a great hangout. All of us in there really enjoy it. The social network of the hour. If you would like to be in there and you would like to support us and let you get ad free versions of all the shows here's shows you can't hear anywhere else.
(02:05:41):
Join the club. It's seven bucks a month, a very affordable amount of money, couple of cups of coffee, and you get the warm and fuzzy feeling to know you're supporting what we're doing here. Just go to twit.tv/club twit and a big thank you to all of our Club TWIT members already who have made such a big difference for us. We just relaunched Home theater geeks thanks to the Club. It's a club only cool show. It was a show we couldn't keep doing cuz there wasn't a big enough audience. Not enough advertising, but we can do it because a club pace work got Scott is a wealth of information. Yeah, love Scott. And I'm really glad we could get him on. So that's an example. After the fact. You can get a copy of this show at twit tv slash sn.
(02:06:25):
You can also get it from Steve. In fact, Steve has two unique versions of the show. You might want to check out a 16 kilobit audio version for people who just don't want to download anything too big, maybe even smaller, is the human written transcription of the show. That's a great adjunct to this show. You can read along as you listen. You can use it to search. In fact, you can search the whole corpus at steve's website, grc.com. While you're there, pick up a copy of Steve's Bread and butter Spin, right? The world's finest mass Storage, maintenance and recovery utility. That's there A lot of freebies, a lot of other great stuff. Grc.Com. You can leave comments for Steve there, that he has a really good active forum. He also has a, a comment form at grc.com/feedback. You can also DM him on Twitter.
(02:07:12):
His dms are open. He's at SG grc. Leave your comments there. Let's see what else. You can also, there's a YouTube channel dedicated to security. Now if you wanna share a clip, that's probably the easiest way to do it cuz everybody can watch it and YouTube makes that pretty easy to get a little clip and share it out. That's a good idea. Of course the easiest way to get it is to subscribe to the RSS feed, cuz that way you'll get it automatically the minute it's available. The best way to do that is to get a podcast client. Frankly, you don't even need to know the RSS feed url. You just search for security now and almost every client will immediately pop up and you can subscribe and get it automatically. Whatever you do, we hope you'll come back and join us next week for another thrilling gripping edition of security now. Thanks Steve. Thank you my friend. See you next week.
Mikah Sargent (02:08:07):
Oh, hey, that's a really nice iPhone you have there. You totally picked the right color. Hey, since you do use an iPhone and maybe use an iPad or an Apple Watch or an Apple tv, well you should check out iOS today. It's a show that I Mikah Sargent and my co-host, Rosemary Orchard host every Tuesday right here on the Twit Network. It covers all things iOS, tv, os, home, pod, os, watch, os, iPad os. It's all the OSS that Apple has on offer and we love to give you tips and tricks about making the most of those devices, checking out great apps and services and answering your tech questions. I hope to check it out.