Security Now Episode 893 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte / Steve Gibson (00:00:00):
It's time for security. Now Steve Gibson is here, man, Microsoft has really blown it. This time, take a look at why you should never use the office encryption technology and why you maybe shouldn't trust their device driver security. Oh boy. We'll also talk about Cloud flare and the largest DO DDoS attack ever. The White House's proposal on an iot cyber security seal of approval. And then we'll talk about proposals for a better way to change all your passwords. It's that and a whole lot more. Coming up next on Security Now podcasts you love from people you trust. This is tweet,
(00:00:50):
This is security now with Steve Gibson. Episode 893 Recorded Tuesday, October 18th, 2022. Password change Automation Security now is brought to you by Worldwide Technology and Cisco. When was the last time your company updated your security strategy or your business assets protected wwt Combined strategy and execution to secure your organization and drive business outcomes? Visit wwt.com/twi to get started and by Thinked Canary detected attackers on your network while avoiding irritating false alarms. Get the alerts that matter for 10% off and a 60 day money back guarantee. Go to canary.tools/twi and under the code TWI in the how did you Hear About US Box. And by express VPN using the internet without express vpn, it's like walking your dog in public without securing 'em on a leash. For three extra months free with a one year package, go to express vpn.com/security Now it's time for security. Now. Oh boy, I look forward to this all week long cuz I just gonna, every time I see a story about security, we've ransomware viruses.
(00:02:12):
I say, I wonder what Steve will say and now we know Steve Gibson is here. grc.com.com. Hello sir. Great to be with you for episode 893. Wow. Yep. We're getting the hang of this <laugh>, maybe <laugh>. So this week's topic is password change automation, which is an overstatement of what we're actually getting. But as I explain here before we wrap up today's podcast, it does represent a baby step in the right direction and a potentially exciting new standard. So we're gonna talk about that. But first we're gonna look at several more serious Microsoft security failures, which have just come to light. And a new useful window security feature that was just added with Patch Tuesday's. Last Tuesday's updates. We also have a new pass keys L well, I'm sorry, the new PAs keys log on technology has received its own website, which we can use to monitor passkey progress moving forward.
(00:03:28):
CloudFlare logs another record breaking DDoS attack. Just insane levels of traffic, which if you didn't have one of the main DDoS mitigators in front of your server, just even pouring ice on it wouldn't help. It would just melt down. <laugh> we've got the news of Signal, the pre one of the premier end to end encryption me messaging platforms dropping their legacy support. I didn't even know they still had it of SMS and mms, you don't know you use an iPhone, but on the Android it's a big deal because then I can use it as my sole messenger, which I won't be able to going forward. Nope. Also, the company Fornet has so sort of attempted to keep a new bad authentication bypass quiet. It was a zero day that was affecting their customers. We'll talk about how that turned out for them. Also, the White House proposes work on an i t cybersecurity seal of approval and the US Treasury Department has L, Yeah, God help us has levied a heavy fine against a cryptocurrency exchange for not caring who they sent money to.
(00:04:50):
I also have some updates on my work on spin, right? And on my just discovered, and I'm more in love with it than ever Zima board that we talked about last week. I'll share two pieces of listeners feedback. Then we're gonna finish by examining, as I mentioned, this new standardized means of accessing websites, password change pages. And we have the first ever security now video of the week, not picture of the week. Cuz this what needs to be animated to and seen to be believed <laugh>. It is so good. I can't wait <laugh>, In fact, I made it our shortcut of the week, but not given a number. It's grc.sc/gate for any of our listeners who want to jump ahead. Anyway, lots of fun today. Can't wait. It's gonna be a great day for Security Now fans and we're gonna get to that in the moment.
(00:05:50):
But first, what are you laughing about? It's true. It's true. Okay, but first a word from worldwide technology. We are big fans of worldwide technology as well. In fact, I've been using World or not using, but I've been a fan of worldwide technology since we went out there with Mary Jo Foley actually in March of 2020. Remember that month was our last trip for some time. But boy, it was a great one. We got to see their amazing advanced technology center. Our show today brought to you, which is second to none. I'll get to that in a bit. But it brought to you by Worldwide Technology and Cisco wwt, of course on security. Now this is appropriate also, it offers all the enterprise technologies, but it really knows security solutions and services that will protect your business. I think this is important because you could go out and try to vet them yourself, but WWTs done all the work ahead of time so they can be your trusted advisor when it comes to choosing security for your business.
(00:06:54):
And you do need security for your business. As you know, if you listen to the show, attackers are always updating their strategy, which means you need to do the same. And WWT is a great partner for this. They'll help your organization prepare and combat for the latest next generation threats. You're looking, I think for company that has the vision, the services, the capabilities needed to deliver security controls and reduce the risk for your organization. But you're also looking for a company and WWT is fits the bill for this that understands business because the execution installation of technology into a business has to match your strategy to, it has to align with what your business is all about. WW WWTs team provides resources and platforms that make that possible. And they've been doing it for three decades. So they've got a proven track record that really can help you. I can give you some examples. They worked with a big retail bank. You'd know the name to help them achieve their primary goal of establishing an infrastructure capable of what? Surviving the catastrophic cybersecurity event, right? Isn't this a good idea? Instead of coming after the fact saying, We got a problem, Houston, we got a problem. Prepare ahead of time. Can we survive? What are the risks? What do we need to do? Wwt, help them reduce system outages by 40%.
(00:08:18):
It actually saved the money, the bank, because WWT was able to implement infrastructure automation that gave them an ongoing cost savings of 48%. And this doesn't have to cost you money. This may be about just improving your business process in such a way that you save money. They work with a large healthcare organization that wanted to do electronic health records, right? Privacy, hipaa, this is a big one. WWT knows compliance, by the way. They are experts in compliance. And that's another thing. You don't just want some company that's gonna come in and say, Here's a solution. You want a company that knows how to integrate that solution and how compliance is affected and impacted, especially if you're a hospital, right? WWT has a variety of security solutions and services that will help you have more effective outcomes with risk management. Again, focusing on your organization's business goals and objectives, but giving you technical solutions that reduce the risk for your organization.
(00:09:16):
And it can go hand in hand with your objectives. They've got endpoint security solutions that can improve visibility and compliance while defending at the edge. Many of the companies we've talked about in the past on this show, I mean they do it all. They know it all. Especially Cisco. They're real experts at Cisco. Network security, really important. Protect network traffic while decreasing your attack surface. Improving threat detection and response, reducing overall risk. They can help you with iam, know that the right people and devices have the right access at the right time. Zero knowledge frameworks, things like that. Cloud security. Sure they know the cloud better than anybody. See how WWT and Cisco can protect your business assets and intellectual property with a holistic security approach. If you haven't done it yet, the time is now. Go to wwt.com/twi to get started. Let worldwide technology help you and ask about joining the ATC platform in the advanced technology center, cuz that's amazing.
(00:10:14):
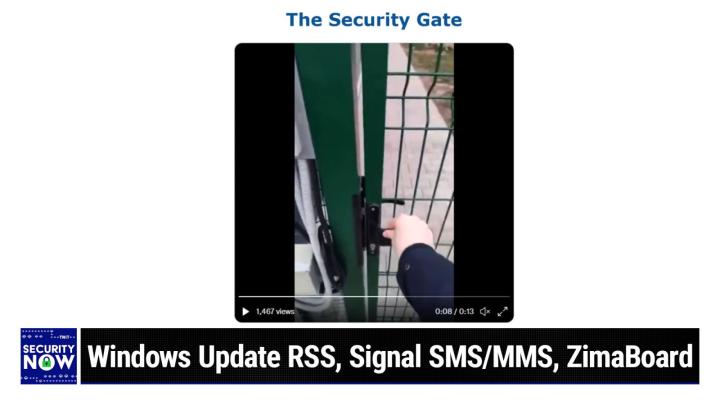
Wwt.com/twi, WWT makes a new world happen. We love them and we're so glad to have them on the Security Now program with Mr. G and the funniest video ever. So yes the does have sound, and since this is a Twitter video, it defaults to being muted. But the sound is important for those who are not watching this. We see somebody who is opening a gate and it opens just fine, right? Yeah. Well, so there's a whole bunch of technology. It's important to recognize. To the left of this is a proximity card reader a computerized gait mechanism. It's got a solenoid actuated release and it's stalled video. I wish I could play it <laugh>. All right. Solenoid release that allows the latch to be electronically opened only if this individual's proximity card permits him to go through the gate. So all this technology is in place.
(00:11:32):
And we should explain also that the gate is sort of a wire grid, so it's not a solid gate. You're able to see through it easily, and it's just sort of got a wire screen with gaps of about two inches around it. Anyway. So this individual is demonstrating to us that sure enough, the gate is locked, he rattles it and it won't open. Puts his security card up to the reader. All sorts of technology happens. The idea is read from the card, it's shot off across the planet somewhere to verify that this individual has the credentials required to allow the door to open a affirmative confirmation returns the computer processes the me, the message activates the power of the solenoid, pulls the latch back and up the gate opens. Sure enough, now to demonstrate the problem here. He then closes the gate, attempts to open it again, will not open rattles, but then he notices, wait a minute, on the other side of the gate through this wire, there's a handle <laugh>.
(00:12:44):
I wonder what happens if I push the handle down. Oops, the gate opens. So let's try one more time without the sound. I don't know if it's the sound that's screwing it up, but Alright, cuz it stops here every time with the sound on. Ah, there we go. And bingo, Bogo. Bongo <laugh>. Yes. Now this is one of those cell phone videos that's very narrow and very high, so we cannot see to the sides. We're hoping that this gate is not out in the middle of a field by itself, <laugh> it looks like it's a pretty secure facility given all the technology on that thing. Yeah, we have of course seen gates that are out in the middle with well, well trodden paths. Circumventing the gate, making you wonder why anyone even bothered anyway,
(00:13:39):
Won't open freezes every time at that point. I don't know why. And then he reaches through the gate, pushes down the handle latch, which opens it, <laugh>. So clearly anyone on the other side was meant to be able to come in. That's, or maybe that's like to, that's probably to leave this protected facility, but you can't enter. You can check out, but you just can't check in. No, wait a minute. It is just like, yeah. Anyway, for anybody who's, who's been listening and wondering what we're talking about, I gave this a GRC shortcut. So it's grc dotc slash gate, G A T e, grc.sc/gate. It's definitely worth checking out. And by the way, this guy, I would follow him on Twitter because he has a lot of similar silly things in there. Mistakes and so forth in security. So I like his I might start following his tweet.
(00:14:41):
Here's a picture of a vehicle where there's a cutout in the back exposing some wires. It says when you need to access the can bus, but a vendor has installed next gen, AI driven security controls, <laugh> towar attacks. Well, easy enough. You just cut a hole in the fiber hose. Oh, oh Lord <laugh>. Oh Lord, yeah, it's very similar. That's great. Yep, yep. Yeah. So he's a H, his Twitter name is H A M Z A H B A T H A. Again, H A M Z A H B A T H a. And as you said a good feed. Yep, yep. Okay. So I was torn between titling. This piece won't fix or secure enough. I settled on, Won't fix but we'll get to what is secure enough. So won't fix is what Microsoft told the guys. Actually guy who noted and reported his or their he is with a company, a well known company, their discovery, they said essentially, Thanks very much, but we're gonna leave it as is.
(00:16:03):
So last Friday, the pattern of Microsoft deliberately choosing not to fix a latent well understood and potentially serious security vulnerability repeated itself once again, which is redundant. Many years ago when this podcast was first laying out the fundamentals of encryption, we talked about cipher modes. Any practical encryption system starts with an underlying symmetric cipher. The one that the industry has settled upon currently is the rein doll cipher, which was chosen to be the AEs standard. Therefore we also call it the AEs Cipher. It's a 128 bit wide block cipher, meaning that it takes a block of 128 bits at a time of which is 16 bites. And under the influence of a key, which is typically kept secret. And the key is often 256 bits. It takes those 128 input bits and arranges to map every possible input combination of those 128 bits into a different output combination of 128 bits.
(00:17:29):
That's the encryption. So as long as the key remains the same, every time the same 128 bits is presented the same, different 128 bits is produced. And of course, that's required for the cipher to be useful. Obviously it must be deterministic and not generate random outputs. Same data in same data out. But this determinism also poses a problem, which we've talked about several times in the past. If the same plain text input block always produces the same cipher text output block, then someone examining the encrypted cipher text, the output who sees identical output blocks appearing instantly knows that the input blocks were also identical. They may not know what they were. But given sufficient time and statistical analysis, significant information can be leaked. And if any of the input text is known, like standard query headers, packet protocol headers, or data boiler plate, or any other overhead which is encrypted as part of this, then someone examining output blocks can see what those known input blocks encrypt to.
(00:19:00):
So this simple and straightforward, yet ineffective mode and method of encryption is known as electronic book or ecb. And no one uses it for encryption specifically because it is clearly an obviously insecure. And by now you can probably guess where we're going with this. Someone did use it anyway. The most famous and clear example of the failure of electronic code book mode to effectively protect the secrecy of data is the classic demonstration of the image of the Linux penguin. I've got it in the show notes. It's also on Wikipedia's page under block cipher mode of operation. And in the show notes we see three images. On the left is the input, the so-called plain text image of the Linux Penguin. The middle was is that penguin encrypted using ECB electronic Codebook mode, which is to say simply taking the encryption block, encrypting it into a different block.
(00:20:22):
And how would they even call that encryption? Exactly. I mean, I know it's not encryption <laugh>. I know. And Marley is a good example of y e. CB is so bad. Yes. Is it? It's just perfect. And what Leo's referring to for those who aren't seeing this is you could tell, still see that it's the ling, the Linux Penguin. I mean it's like, it's not pretty anymore. The colors are lost. But you it's, it's like it's not obscured. It's there. Because every time the same bit block of bits was Sid, it came out to be the same different block. And in an image context, it's it, the image survives. It's not great, but it's there. And compare that to the third frame here, which is just noise. All other modes except ECB result in noise. I mean no picture at all. Just static. And that's of course what you want from your encryption algorithm.
(00:21:33):
So what we actually want, as I said, is shown in that, right? Most of the three pains where the result is pure noise without any vestigial remnant of the original image there, there's no evidence that there was any information. Right? That's the key, Correct? Yeah, it is indi, it is mathematically indistinguishable from entropy. So there's no information there. Noise. Yeah, yeah. Yes, yes. And as I said, any cipher mode other than the simplistic ECB results in something like the third image, just noise actual encryption, which does not leak information about the unencrypted plain text is what we want. Now I'm not gonna delve into great detail about the other encryption modes since we have carefully and fully covered all this before. And the Wikipedia link that I've got in the show notes about this will refresh anyone's memory if they're curious. But the crucial weakness of Simple Electronic Code Book Inc.
(00:22:43):
Insightment, is that each encrypted block stands alone. The good news is this is easily resolved. Every one of the other popular encryption modes solves this simply by chaining. The most famous of these modes is, and it's as good as any, is cbc, which stands for Cipher Block Chaining. CBC simply os the result of the previous encrypted block with the plain text to be encrypted by the next block. That's all it takes. By chaining the encrypted result into the next encryption blocks, no longer stand alone. Each block is affected by all previous blocks. So what happened with <laugh> with Microsoft last Friday, the company now known as with Secure, which was formally F Secure Business, published their distressing summary of events under the title flaw in Microsoft Office 365. Message encryption could expose email contents to attackers. They explained adversaries can exploit the flaw for which there is no patch available to obtain information that could lead to a full or partial information disclosure.
(00:24:13):
So this is from Helsinki, Finland, which is where these guys are located. They said today with Secure, formerly known as F Secure Business, published a security advisory rewarding organizations of a security flaw in Microsoft Office 365 message encryption. So this is office message encryption or o e for short. So they said o e, which is used by organizations to send encrypted emails internally and externally utilizes the wait for it electronic codebook implementation and calling it an implementation is even that is kind of a stretch. They say a mode operation known to leak certain structural information about messages. Attackers able to obtain o e messages could use the leaked information to partially or fully infer the contents at the messages by analyzing the location and frequency of repeated patterns in individual messages. It's the repeater patterns, for example, that allows us to see the Linux Penguin even after it's been encrypted.
(00:25:26):
And they said, and then matching these patterns to ones found in other o e emails and files. Harry Sinton with secure security researcher who discovered the issue said attackers who were able to get their hands on multiple messages can use the leaked ECB info to figure out the encrypted contents. More emails make this process easier and more accurate. So it's something attackers can perform after getting their hands on email archives stolen during a data breach. Not notably encrypted email archives encrypted under this ridiculous electronic code book encryption that he said, or by breaking into someone's email account, email server or gaining access to backups. So according to the advisory, the analysis can be done offline, meaning an attacker could compromise backlogs or archives of previous messages. Unfortunately, organizations have no way to prevent an attacker that comes into possession of affected emails from compromising its contents.
(00:26:35):
Using the method outlined in SY ton's advisory, the advisory also highlights that no knowledge of the encryption keys is needed to conduct the analysis. Yes, cuz it's not actually encryption and that the use of B y Okay, bring your own key scheme does not remedy the problem. Meaning it doesn't matter if you privately key this, it does. This is not actually good encryption. Sinton shared his research with Microsoft in January of 2022. While Microsoft acknowledged the problem and paid sentin via their vulnerability reward program, they opted not to fix the issue. While organizations can mitigate the problem simply by not using the feature, I guess, and not assuming that they have encryption, it does not address the risks of adversaries gaining access to existing emails which were previously encrypted with o e cent. Toin said, any organization with personal, with personnel that used o e to encrypt emails are basically stuck with this problem for some such as those that have confidentiality requirements put into contracts or local regulations.
(00:27:57):
This could create some issues. And then of course there's questions about the impact this data could have in the event it's actually stolen, which makes it a significant concern for organizations because there's no fix from Microsoft or a more secure mode of operation available to email admins or users with Secure recommends avoiding the use of o e as a means of ensuring the confidentiality of emails. And I'll note that the trouble is not just theoretical with Secure's technical writeup, placed an image in an Office 365 message encrypted and sent it using Microsoft's o e office message encryption and this was the result. <laugh>, I have another picture in the show notes where you can as clearly as you could with the Linux penguin, see the word fail written quite clearly in the image because yes, that's what this is, an encryption fail. So as we've seen over and over Microsoft's industry dominance is so complete that the details of what they do no longer matter.
(00:29:17):
This won't cause them to lose a single office 365 customer and they know it. So why bother fixing it? Just call it encrypted and figure that it's encrypted enough. And this begs the question of how this could have ever happened in the first place. I mean, okay, so yeah, we're confronted with this horrible design. I mean, I'm reticent to call it <laugh>, like a D design. Why does anybody use ECB encryption? I mean, is there some useful reason or is it just old? No, it's not even old. I mean, nobody ever, The thing that you need with cbc is you need an initialization vector. Remember that? I said you take the output of the block cipher n and x or with the plain text of block cipher n plus one before encryption. But that then begs the question, okay, how do you start? Because the first encryption won't have a previous result to use.
(00:30:32):
So that's where you need a 128 bit initialization factor. It doesn't need to be secret. It does need to change with every time you use the encryption. But that's simple. Just increment it. Again, it needs to be unique, but it doesn't need to be secret. So you would have to include that with the message or in a header for the email. But that's trivial too. So I mean, okay, arguably I know how encryption works. Clearly whoever designed this, I mean the LEO mean, it's like whoever truly, whoever did this doesn't know how to encrypt things. So they just took the, some symmetric cipher, and I don't even know if it's AEs Ho, maybe. Hopefully. But they took a symmetric cipher and just said, Oh, feed blocks in, send blocks out. Which as we seen, is it good <laugh> and galling? Is that when Microsoft was told this at the beginning of the year, they said, Yeah, well yeah, it's encrypted enough. We're gonna leave it the way it is. It's not encrypted. No. And it's a lie to say it's encrypted. I know. It's baffling to me. And why would you even choose this in the first place, let alone not fix it? The only thing I can suggest is that this was given to somebody who was utterly incompetent to be given this job and they said, Okay, yeah, done. It's encrypted.
(00:32:20):
Might as well just exor it. <laugh>. Why does ECB exist or EBC exist? Why is it there? Because it can, I mean, it's just somebody demonstrate once think it was a good way to do it. So I think probably it's because once upon a time we had the Caesar cipher where you took the alphabet and you skewed it by some number of characters, right? That's basically what this is, right? Yes, exactly. That is electronic code book. The idea is you have something, you look up in a code book, what it's, it maps to, and that's what you write down. And then the receiving end, they have the reverse code book where you look up what you got and you saw what it was mapped to in the first code book. And so it's sort of there just because it completes the picture, but nobody should use it for this reason.
(00:33:25):
And how to do it right is in the next paragraph the, it's like the guy stop reading Wikipedia after three paragraphs. Just read the fourth paragraph where it says, don't do this. It's like, how does this get into, into Microsoft Office 365? And then not only does it get in, but they've said, Eh, we're we're gonna let the leave it the way it is. Good enough, unbelievably incompetent, which really does make you worry about what's happening at Microsoft. Well mean they could even say, Oh, whoops, let's fix it. They're not even gonna fix it. No. Unbelievable <laugh>. Well, the bad guys must love this. Oh yes. Too many Christmas. Yeah. Okay. But we're not quite done yet with Microsoft for the week. Ours technics coverage of this next piece bore the headline, How a Microsoft blunder open millions of PCs to potent malware attacks. With the subhead, Microsoft said Windows automatically blocked dangerous drivers.
(00:34:50):
It didn't. Okay. This was also phone headed <laugh>. Yep. Before I know Leo and well, we'll see. They even got belligerent toward those who are trying to say it doesn't work. Anyway, before we get into the details of what we discovered, recall that this is something also that we've covered in the past. The issue is that kernel drivers by their nature and position in the system run with the highest available privileges in the Windows kernel where they could do anything and everything. Root kits are an example, right? They're able to filter the API in order to make files disappear from the file system. So they must be absolutely trusted, but they also contain complex code, which requires a level of attention to detail that can sometimes be lacking. So otherwise perfectly benign drivers can have identified exploits. Such drivers will originate from valid, reputable sources and bear their reputable publisher's digital signatures, so they're entirely valid and signatures never expire.
(00:36:08):
If a signature is valid at the time that it was used for signing it remains valid. But what if a problem is identified later in an otherwise valid driver, A problem that's maliciously exploitable to gain privilege elevation? Once this becomes public knowledge, bad guys can bring and install one of these valid drivers into a system that otherwise has no need for them. It's like their own private back door. This exploit technique is known as B Y O V D. <laugh> bring your own vulnerable driver <laugh>. And it's a real concern since colonel drivers are no less subject to bugs than anything else. The only solution is to prevent known vulnerable drivers from being accepted and loaded into windows. And that requires that all such known vulnerable drivers be blacklisted. Of course, this critical protection strategy is only as effective as the list of known vulnerable drivers is kept current and so begins our story as ours technic is Dan Gooden writes, he said, for almost two years and later he says, three Microsoft officials botched a key Windows defense, an unexplained lapse that left customers open to a malware infection technique that has been especially effective in recent months.
(00:37:49):
Microsoft officials have steadfastly asserted that Windows update will automatically add new software drivers to a block list designed to thwart a well known trick in the malware infection playbook. The malware technique known as B Y O V D short for bring your own vulnerable driver makes it easy for an attacker with administrative control to bypass windows kernel protections. Rather than writing an exploit from scratch, the attacker simply installs any one of dozens of third party drivers with known vulnerabilities. Then the attacker exploits those vulnerabilities to gain instant access to some of the most fortified regions of windows. Dan writes, it turns out, however, that windows was not properly downloading and applying updates to the driver block list, leaving users vulnerable to new B Y V D attacks. Imagine that <laugh>, How could that possibly happen? Raise your hand if you're surprised. Dan flushes out with some nice background writing.
(00:39:03):
B Y V D has been a fact of life for at least a decade, probably back when we talked about it. Malware dubbed slingshot implied v d since at least 2012 and other early entrance into the b D scene included Lojas, Invis, AOL and Robin Hood. Over the past couple of years, we've seen a rash of new v d attacks once such attack Late last year was carried out by the North Korean government backed Lazarus group. It used a decommissioned Dell driver with a high severity vulnerability to target an employee of an aerospace company in the Netherlands and a political journalist in Belgium. A separate D attack a few months ago, cyber criminals installed the black bite ransomware by installing and then exploiting a buggy driver for Microstar MSI Afterburner 4.2 0.15658. A widely used graphic card overclocking utility. In July, a ransomware threat group installed the driver two sis, a deprecated cheat driver used by the wildly popular game Jen Shin impact during targeted attacks that went on to exploit a code execution vulnerability in the driver to burrow further into Windows a month earlier, criminals spreading the A AVOs locker ransomware likewise abuse the vulnerable Avast kit driver dosis to bypass virus scanning a note.
(00:40:56):
All of these were known, all should have been blocked. None were entire blog posts. He writes have been devoted to enumerating the growing instances of b D attacks with posts from security firm eclipsing and set among the most notable. Okay, so in other words, these are very real threats and attacks, which could be and should be thwarted by windows, but are not being eclipse's. Blog post is cleverly titled Screwed Drivers, Signed, sealed, delivered, and E is titled signed Colonel Drivers unguarded Gateway to Windows Core and Eclipse Enumerates. The publishers of such drivers, which include as a geac, gigabyte, wawe inside Intel, msi, Invidia, Phoenix Technologies, real tech, semi super micro and Toshiba. All good companies and all capable of making mistakes. Dan writes, Microsoft is acutely aware of the b d threat and has been working on defenses to stop these attacks mainly by creating mechanisms to stop windows from loading signed.
(00:42:32):
But vulnerable drivers. The most common mechanism for driver blocking uses a combination of what's called memory integrity and H V C I short for hypervisor protected code integrity. A separate mechanism for preventing bad drivers from being written to DISC is known as ASR or attack surface reduction. Unfortunately, rights Dan, neither approach seems to have worked as well as intended as we'll. See that statement of Dan's is actually being quite kind. He continues. Microsoft has touted these protections since at least March, 2020, some more than like two and a half years when the company published a post promoting secured core in PCs, which have H V C I enabled. Out of the box Microsoft presented secured core PCs and H VCI in general as a panacea for the Wild D attacks, stemming from either buggy drivers or wormhole drivers, which are those which were created and vulnerable by design.
(00:43:48):
Microsoft said in our research, we identified over 50 vendors that have published many such wormhole drivers. We actively work with these vendors and determine an action plan to remediate these drivers in order to help further customers identify these drivers and take necessary measures. We've built an automated way in which we can block vulnerable drivers and that is updated through Windows update. Customers can also manage their own block list as outlined in the sections below. The post went on to say rights, Dan, that Microsoft threat research teams continuously monitor the threat ecosystem and update the drivers that are in the Microsoft supplied list. This block list is pushed down to devices via Windows update. A few months later, Microsoft Senior VP of Enterprise and OS Security, David Weston tweeted that by turning on these protections, Microsoft users were safe from an ongoing b d attack that had recently made the rounds. Weston wrote, Security vendors are gonna tell you that you need to buy their stuff, but Windows has everything you need to block it.
(00:45:10):
Multiple Microsoft posts have made the same claim about automatic updating ever since one from last December said that signed drivers reported to be vulnerable are blocked by default through Microsoft's automated Windows update mechanism when Windows 10 has H C I enabled. But Dan writes, as I reported on the, he says, As I was reporting on the North Korean attacks mentioned above, I wanted to make sure this heavily promoted driver blocking feature was working as advertised on my Windows 10 machine. Yes, I had memory integrity turned on in window security, it's window security device security, core isolation, he says, But I saw no evidence that a list of band drivers was periodically updated. So I reached out to Microsoft and asked if someone would provide me with background about how the protection worked. The response from Microsoft is nothing to share. I then turned to Peter I a researcher at security firm who has had plenty to share about D attacks.
(00:46:37):
I asked Peter for help testing this driver block list feature very quickly. We found it lacking when Cal nine enabled H V C I on a Windows 10 enterprise system. In his lab. For instance, the machine loaded the vulnerable Dell driver that had recently been exploited by Lazarus. Around the same time researchers including Will doorman, a senior vulnerability analyst at security firm Intelligence had been tweeting for weeks that various drivers known to be actively used in D attacks were not being blocked the way Microsoft had advertised one dorm. One dormant observation was that even with H V C I turned on his lab machines loaded a vulnerable driver known as Wing win Ring zero just fine. Upon further investigation, doorman discovered that this vulnerable win ring zero driver wasn't present in the Windows recommended driver block rules. In the same thread, he went on to show that despite Microsoft's claims that ASR is capable of blocking vulnerable drivers from being written to disk, he could find no evidence that this feature worked at all.
(00:48:06):
Microsoft has yet to address this criticism. Order provide doorman with guidance. Doorman went on to discover that the driver block list for H V C I enabled Windows 10 machines hadn't been updated since 2019. And the initial block list for server 2019 only included two drivers. A scrutiny of this situation increased. A Microsoft project manager finally admitted that something had gone wrong with the update process for the driver block list. Gee, imagine that the manager tweeted that Microsoft was fixing the issues with our servicing process, which has prevented drivers from receiving updates, prevented devices from receiving updates to the policy. What the program manager was saying, boiled down to this, if you thought H V C I was protecting you from recent B V D attacks, you were probably wrong. Windows 10 hadn't updated the list in almost three years. Coinciding with the project manager's tweet, Microsoft released a tool that allowed Windows 10 users to deploy the block list updates themselves, which had been held back for three years.
(00:49:29):
But this is a one time update process. It's not yet clear Microsoft can or will push automatic updates to the driver block list through Windows update. I do have a link in the show notes at this point to the posting that Microsoft made that will allow end users or hopefully Enterprises to update their block lists. Dan goes on. While Microsoft's response to my questions about driver block list updating was indifference company employees have been actively dismissive to admins and researchers who began asking their own questions about the topic. Recently, for instance, when doorman pointed out a de demonstrably false claim in an August tweet from Weston that ASR ensured that updated driver blocking happened automatically. Weston did not a, this is he's a senior vp, right? Did not apologize or even admit the problems. Rather than confirming an update lapse that Spann more than two years, Westin bristled saying only that updates quote are in the servicing pipeline and that Microsoft has already provided a tool to do it.
(00:50:43):
Right now, the closest Microsoft has come to an admission of failure is a recent comment from a company representative saying the vulnerable driver list is regularly updated. However, we received feedback that there has been a gap in synchronization across OS versions. We have corrected this and it will be serviced in upcoming and future Windows updates. The documentation page will be updated as new updates are released. The representative didn't say how long the gap lasted or what upcoming and future Windows updates would fully fix this problem. So wow, Dan's coverage of this mess continues with some power shell scripting that allows individuals to take matters into their own hands. I placed a link to his entire RS technical article in the show notes, but everyone gets the idea by now. We have another example, not only of gross incompetence, but also of denial and belligerence when employees are presented with embarrassing truths.
(00:51:56):
Obviously Microsoft hasn't bothered to test themselves any of this for the last three years. They said, Oh look what we got now. But apparently it never worked. The security industry has been blogging about this and posting about this and waving their arms in the air trying to get Microsoft's attention. Perhaps now that a high profiled report has been pulled together, thanks to Dan's reporting, the pressure will have escalated to get this fixed each week. I listen to Paul and Mary Jo on Windows Weekly. They are, every bit is puzzled by the decisions that Microsoft is making. I sincerely hope that this is a pendulum swing and that we are at the Nader now and that things are gonna begin swinging back in the right direction. I'm still not yet ready to give up on Windows. It's still the best user experience in the world and I know that the enterprise world has no other choice. It's windows. Unfortunately, Microsoft knows that too. Let's hope they can and will start getting their act together. I always say that anyone can make a mistake, but this feels like bad policy from on high.
(00:53:20):
What's good policy for us is taking a break right now. Leo? Yes, and we will undoubtedly talk about this tomorrow on Windows Wow Weekly with Paul and Mary Jo. Be curious what their take is on both of these stories. Frankly. See this in my hand. This here. Well, you know what it is, it's not. It's pretty in undistinguished. It looks like it maybe could be a little USB pocket hard drive, something like that. It's not. It's the best little honey putt money buy. It's your thinked canary. If there's anything we've learned in the last year, it's that you've gotta make it a priority to secure your networks. And we always say security is a layered approach, right? You don't just do one thing, you don't. For instance, just protected the perimeter and assume that well, well nobody can get in will be fine. You need these.
(00:54:13):
You need these. These are one of the layers. Layers you have to have. This is a little honey pot that sits inside your network. See, the problem is if a attacker gets in, they get through that perimeter defense. You got no way of knowing they're around. They're not gonna announce it. They're gonna do everything they can to hide their tracks. And here's the really bad news. On average companies take 190 days to discover they've been penetrated. That's more than six months for a bad guy to wander around exfiltrate data, find all your hide holes for your backups, make sure that when they set off their time bomb, it hits every possible nook and granny and they can blackmail you later. Actually, actually it's one of many things hackers do while they're wandering around the native network. Don't forget the many, many data breaches we talk about.
(00:55:01):
Well, we don't talk about 'em cuz there's so many of them. Every week. This canary is gonna help. This canary does not look like an insecure device in your network. It looks like a valuable device on your network. For instance, you could put it on active directory. So brow. So the bad guys are looking through your active directory for file servers, for file shares, for documents. They'll, they'll be trying default passwords against network devices and web services. They'll scan for open services on the network. If they find something of interest, a document, they might open it. But every time they do something like that, they're sending you a clear signal that they're there plus information about what they know. These things, canaries are completely configurable. They're designed to look like whatever you want, anything a hacker might want to get into. You can deploy 'em throughout your entire network.
(00:55:55):
You can see there's just a plug and an ethernet jack. That's it. You plug it in, it's doing its job. That's it. You're done. But you can configure it to be a router, a switch, a Linux box, a Windows box. You can turn on a few services. You could turn on a Christmas tree of services. You could put fake files on them, give them names that hackers will maybe wanna open. Things like payroll information. You can enroll 'em in active directory. But the minute an attacker notices and tries to get in, you will be notified immediately. Actionable results, actionable alerts you could do something about. So for instance, this one's set up as an example, as a sonology. NA has the same Mac address as a sonology. NA has the same DSM login as a ology nest for to any outside eye, it looks like a network attached storage device on your network.
(00:56:49):
But the minute they try to log in, you get an alert saying, Hey, somebody with a username xyz and the password 1, 2, 3, 4, just tried to log in. They're in there. You know, can also make canary tokens with your canaries. These are little files, PDFs, documents, spreadsheets. That also can be attractive to attackers. But the minute they try to open 'em, you're notified. The canary can be installed in minutes. It takes no time at all, even in it like me can do it. And then you just put it aside. You don't have to think about it ever again because if you get an alert from your canary, something's going on, there's somebody in your network, you can do it any way you want. They of course support Syslog. They have an api. You can get Slack notifications, support web hooks. So you can pretty much do anything.
(00:57:40):
You can get an email, you can get a text message. And of course with every canary you get a consoles, you can look on your console too. Data breaches typically happen through the staff, but the problem is somebody who opens a fishing email, they don't know they've done it. You don't know they've done it. And the bad guy's now in and could be doing anything. Anything. And you just won't know until they set off that time bomb. And it's too late. Canary, these beautiful little honey pots were created by people who've trained companies and militaries and governments on how to break into networks. They know they took that knowledge and they built the canary. Something an attacker will love that you can easily put on your network. You'll find Canaries deployed all over the world. One of the best tools against data breaches. The company is called Thinks, T H I N K S T.
(00:58:33):
But you'll find all you need to know at canary.tools/twit Canary, c a n y.tools/twit. Actually, canary.tools/love has a bunch of tweets from well known CISOs and security gurus about how much they love this idea. It's just almost a no-brainer. if you want, let's say five canaries give you an idea of the pricing 7,500 bucks a year. You get your own hosted console, you get all the upgrades, all the support and maintenance. You sit on the canary, they'll replace it. No cost, just send you another one. No questions Ask. If you use the code twit, when you sign up for this at canary dot tool slash twit, you'll get 10% off the price for life. This is such a useful tool. You can see it's small, it's unobtrusive, it doesn't take any maintenance on your part, any energy at all until you get that important message.
(00:59:32):
Canary.tools/twit canary dot tool slash twi. Don't forget to put twit in the offer code box. And oh, by the way, if you're not happy, they've got an amazing, very generous two month money back guarantee for a full refund. So you get 60 days to try. But I think that tells you something. They're pretty confident you're gonna love it. We know you will. canary.tools/twit offer code TWIT in the how did you hear about this box? Thank you Canary. And I'm not telling anybody where my canaries are or how many I've got or any of that. And I think, Leo, I'll take over while you take a sip. I some. It's my turn. <laugh>. Thank you Steve. All yours. So what else happened this week? Microsoft wait for it has finally added an RSS feed for Windows updates. Yes. After endless years of pleading from its customers, Microsoft has finally made available an RSS feed for its security updates portal. I've got the feed link. That's amazing that they've never had this. I know. And there's been so much pressure on them. It's like, just can we have it as an rss? And it's like, no, no, no. We're gonna do it this way anyway, they finally said, Okay, I think Linux is kind of getting the better of them. Leo. They sort of seem to be, I'm not saying anything.
(01:01:06):
So I got a link to the show notes. I got a link to their blog posting, announcing it for anybody who's interested you can find that there. Pass keys. The industry's first agreed upon replacement for passwords now has its own useful promotional website that's at paske.dev. P A S S K E Y S dot D. The homepage has that original Google Microsoft Paske demo video that we saw back at paske launch or announcement. But the most interesting content for most of us who have been following along is probably a list. Though it's still quite short of websites where the PA keys log on experience can be explored. So under docs, tools and libraries test and demo sites, we find web often.io and pa keys.io. That's pretty much it for the moment. Uco, this guy's disappointing. I know. Yeah. Okay. Ubi CO's got a demo site and we off N Dome appears to be available for testing.
(01:02:19):
I don't know whether this list is exhaustive. I would expect that Apple, Google and Microsoft, at least it's now in iOS 16 and it's gonna be an and Android I think. Yep. I feel like probably this list is not exhaustive cuz there's probably new guys coming on every five seconds. Let's hope. Although it remember it does take some work at the server end. So again, we'll see how this goes. So hopefully Apple, Google, and Microsoft at least will be supporting their own PASKY standards soon. There is a device support page which contains a nice grid of which versions of what support what level of pass keys. So anyway, that'll be something to keep our eyes on. As I mentioned, Cloudflare's quarterly DDoS threat report for the just ended third quarter of 2022 noted that it had mitigated a large scale DDoS attack that reach an astonishing two and a half terabytes per second.
(01:03:25):
Okay. Or restated 2,500 gigabits per second, 2,500 gigabits per second. The attack was launched by a MI botnet variant and aimed at the WinCraft Minecraft service. I was curious. So I went over to the WinCraft site, W Y N nt.com, never been there before. It's kind of cool looking to see what a state of the art Minecraft service looks like. As I mentioned, at the top of the show, Signal said that it will be dropping. Its longstanding fallback support for sending and receiving SMS and MMS messages in its Android app in order to improve its privacy and security as it was SMS and mms. MMS were only supported under Android and they were a remnant from the earliest days of Signal when it was known as, Remember this text Secure? Oh yeah, yeah. Text Secure. That's what became a, That's what Signal became, or that's what Wait.
(01:04:34):
<laugh> Signal became of that or something. Oh, there was some good news for Windows users. We previously talked about Windows Remote Desktop Protocol RDP finally receiving some relief in the form of failed authentication attempt rate limiting with last Tuesdays October updates Windows 10 and 11. And for what it's worth, Windows seven and Server 2008 R two if you're, they're on the extended service plans, will have received new group policy features, which enable the implementation of similar lockout policies for local administrative account logins. That is somebody banging on your keyboard while you're away at lunch. Since I'm sure that this will be of interest to our listeners, I'll share some details. Microsoft postings explained, they said, in an effort to prevent further brute force attacks slash attempts, we are implementing account lockouts for administrator accounts, beginning with October 11th, 2022, which was last week, la last Tuesday or later Windows cumulative updates.
(01:05:51):
A local policy will be available to enable local administrator account lockouts. This policy can be found under local computer policy, computer configuration, window settings, security settings, account policies, account lockout policies that's in UN under GP edit for existing machines. Setting this value to enabled on existing machines using a local or domain GPO will enable the ability to lock out administrator accounts. Such environments should also consider setting the other three policies. Well, yeah, you kind of have to, You'll see it in a second. The other three policies under account lockout policies, our baseline recommendation is to set them to 10 10 10. This means an account would be locked out after 10 failed attempts within 10 minutes, and the lockout would last for 10 minutes, after which the account would be unlocked automatically for new machines on Windows 11, version 22 H two, which is just now coming out as we know.
(01:07:05):
Or any new machines that include the October 11th, 2022 Windows cumulative updates before the initial setup. These settings will be set by default at system setup. So this becomes a new default for Windows local account login. This occurs when the SAM database is first instantiated on a new machine that that's the security accounts database. So if a new machine was set up and then had the October updates installed later, it will not be secure by default and will require the policy settings above. If you do not want these policies to apply to your new computer, you can set the local policy above or create a group policy to apply the disabled setting for allow administrator account lockout. And finally, they said additionally, we're now enforcing password complexity on new machines. If a local administrator account is used, the password must have at least three of the four basic character types, lowercase, uppercase numbers and symbols.
(01:08:16):
This will help prote further protect those accounts from being compromise because of a brute force attack. However, if you want to use a less complex password, you can still set the appropriate password policies in local computers, policy, computer configuration, window setting, security settings, account policies, password policy. So it's also worth also noteworthy that other reporting has indicated that a similar feature to block SMB that is Windows printer and file sharing based brute force attacks is in the works. So it only took what 30 years and Microsoft is beginning to bring their systems and their network protocols up to a standard that will help protect their users. Yay. Other than that, in the past week, there were more defi and cryptocurrency bridge exploits and currency ripoffs. No surprise. As I mentioned, a nasty Fort net high end enterprise security appliance zero Day was found that was confirmed last week and has been under active use in attacks.
(01:09:33):
It's now been unfortunately fully elucidated in an unauthorized and arguably premature public disclosure. It's expected that the attacks will soon escalate. As a consequence of this, when for Dnet first learned of the vulnerability privately several weeks ago, they quietly updated their code and sent private messages to their customers, urging them to update immediately because of the seriousness of the authentication bypass that had been discovered. That broke from industry standard protocol of acknowledging an event when it's learned for net in this case, chose not to go public at the time. Well, it's certainly public now. And then a week ago, last Tuesday, the White House put out a press release saying that it's working on a cybersecurity label that would be applied to smart I o T devices similar to the Underwriter's Labs, U L C Seal of approval to help inform Americans which devices meet the highest cyber security standards to protect against hacking and other cyber vulnerabilities.
(01:10:49):
Okay. The administration said it plans to meet with vendors, industry groups, and government agencies. That's hopeful later this month to discuss how this labeling scheme would be managed. The White House said the new cybersecurity labels will first be mandated for the most common and most at risk technologies, which they feel are routers and home cameras to deliver the most impact most quickly. So it'll be interesting to see how this develops. What will be the requirements imposed upon devices to receive these cybersecurity approval labels? Are they gonna be worthless labels or worthwhile? And how will their application be enforced? We'll find out. And finally, the Treasury's Financial Crimes Enforcement Network Fin Send find the cryptocurrency platform, bit Rex 29.2 million for failing to detect and block payments to sanctioned entities and also failing to detect payments to dark web markets and ransomware groups, other financial crimes. Fin Sen said Fin Sen said bit Rex made over 116,000 transactions valued at over $260 million to sanctioned entities and connected to criminal activity. Over the past few years, apparently as few as two minimally trained employees were tasked with monitoring more than 20,000 individual transactions per day. In other words, Bittrex wasn't taking its monitoring obligations very seriously and now they'll have to pay nearly $30 million in fines. Ouch.
(01:12:58):
I got a little bit of additional good news on the spin right front. Two more of spin right's 378. Currently registered development testers weighed in since last week's podcast with some interesting performance numbers that I wanted to share. The first screen shows a 6.0 terabyte drive attached to his machine's SAT port number four, having a full drive read scan time of only 7.64 hours. So that's attached to it. It's a hci, not usb, A H C I, attached to A H C I port four. So six terabytes able to be scanned by SP right in 7.64 hours. That's not quite a terabyte per hour. It's actually one in a quarter hours per terabyte, but it's close as we can see spin, right? Really 6.1 really will be able to scream. The other recent report shows a similar level of performance through usb. This guy has 11 drives attached to his machine.
(01:14:17):
His little drive heavy. Six of them are on USB ports. One of them was the boot drive. The one that's highlighted at the bottom is an external four terabyte drive. That spin six one will be able to completely read in just 5.14 hours. We've never seen that sort of performance until now. As I mentioned before, it makes spin right practical once again on huge drives until we get to spin right seven one, which will add native hardware, USB drivers spin right's, maximum USB performance will utterly depend upon the machine's bios cuz that's what we're still going through. But as we see here, it can, given the right bios, be very fast. Like no, no reduction in speed O over A H C I at all. I'm sure that was a a USB 3.0 and in reviewing the past week's worth of Twitter communications, I encountered a spin right success story that I thought would be fun to share.
(01:15:26):
Ryan Becker tweeted from RB 1 4 0 60. He said Steve wanted to share a spin right success story. A friend of mine called me saying his four year old laptop was running incredibly slow to the point of him not being able to do any work. Upon my arrival, I found that task manager was reporting 100% disc utilization with nothing running in the background immediately suspecting a failing drive. I recommended he purchase an SS D and he gave and have me clone the drive over. However, both clone Zilla and Mac reflect gave data read errors part way through the drive and aborted the clone. He's an insurance agent with hundreds of client files and of course no backup. So I dug up my copy of Spin right and loaded it to a USB stick only to have the laptop fail to recognize that the stick was bootable. Luckily, a knit disc with its free Doss option made the laptop recognize the stick and I was able to copy the spin right XY to the drive.
(01:16:47):
I said spin right off in level two and it took the better part of the data run. That's of course spin right 6.0 he's got, after it completed, I attempted to clone the drive again in Mac and this time total success. He is now happily chugging away with an SS D and all of his data is intact. Thanks for a wonderful product. Looking forward to 6.1 and beyond. Please feel free to share this on the podcast if you wish. So first of all, Ryan, thanks for sharing your success. It's really gonna be fun to be fielding a bunch more of those sorts of stories once 6.1 is in everyone's hands and note that the first failure of spin, right zero to boot is the reason I took the time before doing anything else to create a knit disc spin, right? Six one will still be able to create a bootable, but only because all of that code is already written and it's actually kind of cool, but it's clear that the future is bootable USB thumb drives.
(01:17:55):
So 6.1 will of course incorporate a knit discs, quite robust USB boots set up technology. Of course, that's why I wrote it in the first place was to be incorporated into all future gizmos that I've got. Spin right six and seven and beyond and other stuff. Two pieces of closing the loop feedback. Giler Mo Garcia. He said Hi listeners, since episode oh oh one, he said on SN 8 92, So that was last week. You and Leo discuss the benefits of using uBlock to filter cookie popups. As I am very much aware of tracking, I take the time to configure each one to deny all if possible. I wonder on which state will a cookies be set when the popup is blocked? Maybe they remain on any thoughts?
(01:18:55):
Gil Yamo and everyone. It's interesting. One of the things that I learned caught me by surprise, which was when I was doing that cookie forensics work many years ago, closely looking at the way cookies were being handled by browsers. One of the things the cookie forensics system does is it notes the timestamp on the test cookies, which the performing those forensic tests set. What we discovered was that if you, on, depending upon a black browser you were using, if you had cookies enabled before but then you disabled them, some browsers would stop sending the cookies they already had. Whereas some browsers apparently stopped receiving new cookies but did not block existing cookies, which I sort of thought was the wrong behavior if you said, turn off all cookies, Well, I don't want anything to be sent anymore. Some browsers stopped receiving them. So it was a little bit of a glitch, which I wondered about at the time.
(01:20:08):
So anyway, that's what would happen if you turn cookies off is you know it's worth turning them off and deleting them all from your browser to make sure it's not one of those that keeps sending them. And timmo groom, he said regarding spin, right? Great to hear about all the exciting developments. Kind of frustrating to know that it can still only be used on old computers in my attic. So we currently have 378 development testers registered in our GitLab instance. So many people have machines that will run spin right on machines that still only offer a bios. But I am 100% sympathetic to the need for spin right to boot over U E F I. The bio is the past and U E F I is today and tomorrow and that's the reason for my changing plans and deferring native support for US USB and N V M E until after spin, right is able to boot and run on any U A U E F I only machine without any bios and without doss.
(01:21:19):
So I will be getting there Timo and everybody else as quickly as I can. Leo, I receive your books. Oh, thank you. Yay. Very, very cool hacker. You could throw 'em out, you can do anything you want with 'em. I just thought they looked like something you might be interested. Hacker's delight looks like it will be really fun to read through over time. And the book titled Exchange Racks, Racks <laugh>. That is really fun. <laugh>. So for people who don't know, it is the Plains Most simple book you could ever have. All it is you open it and it is three or four, maybe up to like nine, but sometimes just two, just a few lines of 64 bit intel assembly code. No explanations, no introduction, ju, that's all they are <laugh> and even the page numbers are in hex. I mean this guy is a hacker's hacker and I found some quotes from him that I thought would be fun to share.
(01:22:33):
He said initially I wanted to publish the book through a publisher, but no publisher wanted to go with the, and he has in quotes, minimalistic, which is to say the least design. He said. One publisher said he would publish the book if I added explanations for every coats snippet. No. And he said, But I was not willing to do so. He said Another friend recommended adding QR codes to the pages linking to explanations, but I wasn't willing to do this either. Good for him. He said, I remember trying to decipher each of those code snippets myself and so maybe he collected them. He says, I felt that I could not let my readers down by handing them an easy solution. Good. So then somebody reviewing the book wrote, much of the joy of the book comes from discovering the nuances of these tiny programs. Many rely on assembly specific tricks to that do not really translate up into the virtual machines defined by higher level programming languages.
(01:23:49):
And then he said something interesting. Those who have troubled deciphering can view X X or PDs. That's the pseudonym of the author of this Can View X or PDs video series oh titled Assembly Language Adventures, which teaches assembly programming beginning with the very basics, reaching a level of expertise through 29 hours of instruction. X R PD created the book as a companion piece while working on the video pulling his favorite assembly snippets together. So I've got a link in the show notes, that's X O P X O P d.net/pages/x 86 underscore adventures dot html, which will take you there. And there he says, What is assembly language? A computer only knows this is him. Writing a computer only knows how to execute a small set of commands or instructions. Those are really simple commands such as adding or subtracting numbers, comparing numbers and so on.
(01:25:05):
Assembly language is the language of those commands using assembly language. You can create computer programs that instruct a computer to do things in the most basic level possible. He says, then why learn X 86 assembly language? And he has four bullet points. You are the kind of person who really likes to know how things work. In this course, you're going to get solid understanding on how computer programs work from the inside. Two, become a better programmer. Knowing how things work down there will help you make better decisions. Even as a high level programmer. I agree. If you are all, yep, if you were always wondering what is the stack or what are those pointers everyone talks about, you came to the right place. Three, write faster code when you really wanna get the most from your processor. Writing in raw assembly is needed. We're not gonna talk about optimizations in this course.
(01:26:06):
However, you will get a solid foundation so that you can continue exploring on your own. And finally, fourth, you wanna become a reverse engineer or a security researcher. Read the code of viruses or look for software vulnerabilities. As most of the time the original source code will not be available to you. Solid understanding of X 86 assembly language is mandatory. So a Leo, again, thank you for the two books. They will absolutely find me spending some time with them. They look great. Good. And last and lastly, I wanted to share a little bit of additional ZMA board. Goodness. I know that a lot of our listeners loved learning about ZMA board last week because I got a lot of tweets and feedback. I've spent all of the last week deep into working on spin and that work has been exclusively with the $120 ZMA board, single board X 86 computer that I talked about last week.
(01:27:12):
I love it. One problem I had was that when I'm doing things at the machine level in the debugger, I might manually move the program counter somewhere out of sequence to force some piece of code to run. Or often sometimes it's like to make something run to rerun a subroutine where the result wasn't what I expected. So I want to go back to it now and this time go into it. Whereas last time I stepped over it. So at the machine level in a debugger, this is easy to do and super useful, but it can leave the machine in an unstable state if I attempt to then proceed or exit. The bottom line is that the machine is often hanging hard so that the keyboard's famous three fingered, salute, control, alt delete does nothing. And unlike most, but not all desktop machines, because it's meant to be used as an embedded appliance, the ZMA board doesn't have a hardware reset button.
(01:28:22):
So whenever the board was hanging, I had been forced to pull the power, wait a second and plug it back in. I hate doing that. And since my current test drive is a two terabyte Seagate spinner, it's being forced to spin up and down, which I also hate. But when I had disassembled the ZMA board earlier upon receiving it, of course I took it apart. That's a required part of the process of getting to know it and falling in love with it. I noticed 14 printed circuit pads arranged in a two by seven grid at the cards edge just in front of the external P C I E connector. And the case had a cutout there which allowed those 14 pins to be accessed externally. So I was hoping that among those pins might be a signal ground and a hardware reset line to which I could attach a hardware reset button.
(01:29:23):
So over the weekend, this past weekend, I decided to seek the help of ZMA board's creators. I found that they maintain a very active community on discord. So I jumped online and posted my question in the evening, I think it was Saturday evening to their support channel. The next morning when I awoke and checked, not only was there an answer but my prayers were answered. It turns out that the 14 pin pads are a complete PC front panel extension. There's a power button, a reset button, and connections for three activity LEDs. I've got a picture of that in the show notes for anyone who's interested. And a link to the page that came from over at zma docs dot zma board.com. So anyway, that's the last thing I needed. When I've been testing spin right on all these various motherboards, I've not been mounting them each in a case because there's just no need to.
(01:30:26):
But I have needed a power switch and a reset button and I found this cool little, it's like a little round hockey puck that's got a big power switch and then a little reset button. I actually use them in reverse. The big easy to press button is reset cuz I'm doing it so often and the little button powers the machine on and off. It's just got, I got it from for it was a little over $6 from Amazon that gives me a little portable, an external power switch and reset button, which is really handy. So I've got another one of those that I'll be actually two that I'll be hooking up to each of my ZMA boards at my two locations. And now my life is complete. And Leo, we're gonna make our listeners lives complete <laugh> by wrapping this up after you tell us about our last sponsor, our subject of the day password automation.
(01:31:20):
Automation will be coming up in just a bit. But first a word from express vpn, our fine sponsor and the only VPN I trust and use Love Express VPN for a lot of reasons using the internet without express vpn. How can I put this? We'll be like walking your dog going to the park with your dog but not on a leash. Most of the time dog's gonna stick by you. He's not gonna be a problem. But what if one day he runs off and disappears, dog napped lost forever. You wanna be careful. I don't know if that's a good analogy, but it's like <laugh> use the internet without a leash. I don't know if that's quite exactly what I'm trying to say. Every time you know this, you connect to an unencrypted network a public wifi hotspot and airports, hotels coffee shops, your data is flying through the air, right?
(01:32:16):
Plus the bad guys can see you on the network actually of late. That's become more of an issue than even the flying through the air issue because of course a lot of the sites you go to are encrypted. You have to worry so much about that. But if a bad guy can see you, they can attack you. Just go look about at the wifi pineapple, which is a quote pen testing device that anybody can buy. It's inexpensive. Go to a coffee shop, see you sitting there and then set up a wifi access point that's very strong and signal that might attract you something they could see, for instance that your home wifi access point's name set it up, your computer says we're home joins it. Now you're not on the public internet. Well you are, but you're going through the guy's computer and that is really starting to become problematic.
(01:33:09):
He's on your network, you're on his just one of many reasons a vpn. See it's if you use Express via VPN in that coffee shop, he can't see you. He just sees Gobbly Cook. express VPN creates a secure encrypted tunnel between you and the outside world. There's other reasons to use it. We were talking on Mac Break weekly. Alex Lindsay really wanted to watch his Pittsburgh Steelers on tv, but NFL blackouts prohibit him from doing it on the NFL app. So what do you do? You express VPN to the country of your choice. Log into your NFL plus subscription. You can see anything you want cuz they think, no, you're not sitting in California, you're sitting in Chini, India or Germany or anywhere because Express VPN has points of access all over the world. Servers everywhere. I wanna emphasize also, and everybody listens to this show, kind of I think understands this, that a a VPN provider is just becoming now a proxy for all the privacy and security issues you might have with your IS P there in effect.
(01:34:12):
Now nobody can see you except the VPN provider can. So it's very important that you pick a very good VPN provider and that's really the most important reason why I use Express vpn. There was a great article in bleeping computer La Lawrence Abrams wrote up express VPN TA and told me stuff that actually I had never known before. I know they use this trusted server technology, which is sandbox that's in ram, cannot write to the disc while you're on express vpn. That's good. That means they cannot log you no way. But I didn't know they run on a custom Debbie in distro that they reboot every day and it wipes the whole drive and starts completely from scratch every single day. So even if somehow some trace of your presence got saved to that server by the next morning it's gone. And we know this for another reason.
(01:35:01):
There are authoritarian nations who have seized express VPN servers. It makes the news from time to time. They don't use a warrant, they don't knock, they just come and get it. So no chance for anybody to change the server, right? Except there's never anything they can use on it. We know and of course Express V PN undergoes third party audits as well. So we know from many different ways this is an absolutely secure, private way to access the internet. Strong encryption, easy to use goes on everything. iOS, Android, Mac, Windows, Linux, you can even put it on some routers. It's a simple app to start up. A simple app to close down. If people have been noticing lately cuz of the way Apple does its thing, you put a express VPN on your iPhone and any service that was started prior to express vpn is continuing to communicate.
(01:35:52):
Express VPN is working on that with Apple. But you can also just reboot your phone immediately, start express VPN and you'll be in the clear. It really is the right thing to do in so many circumstances and it is affordable. Less than seven bucks a month when you take advantage of our special offer, an extra three months of service with a one year package, go to express vpn.com/security. Now you don't need it every day. Maybe although it's so fast, you might leave it on all the time. I actually leave it on by accident sometimes cuz I forget I'm using it and three days later I'll go, Oh, I still have express VPN on. I didn't even notice. But it's great to have it in your toolkit when you need it. Express vpn.com/security now express vpn.com/security now. And we thank 'em so much for their support of Steve Gibson.
(01:36:46):
Let's talk about change in your passwords automatically. Yeah, we're gonna begin with a brief refresher about so-called well known website assets. The most famous of these is the venerable robots dot text file. When automated spiders or bots began exploring the web and as websites began evolving beyond a collection of static webpages, it started becoming possible for bots to get stuck in infinite loops at a site like following a link that led to another page that had a link that led back to the first one and so forth. Or they might begin rapidly requesting all of a site's dynamically generated webpages to place an undue burden on the site's web server. So a convention was created when a bot would enter a site, it would check for a specific file named robots dot text residing in the route directory of the site. So forward slash robots dot text if present that file would provide bots with a series of hints, es essentially some guidance metadata about where they could and could not safely venture.
(01:38:02):
For example, my grc.com website has a robots dot text file. It contains, first of all, it has a statement, user, agent, colon space asterisk, meaning this applies to all who come. Then I have a disallow forward slash x that is an alias for GRCs scripts directly directory where it makes no sense for any search engine to wander. In some cases I wanted friendlier URLs without the slash x, so I translate those on the fly, but bots would see something else. So I'm also, for example, asking bots to stay away from any URL beginning with forward slash ppp since those are GRCs perfect paper passwords pages where it doesn't make any sense for a bot to go. And I also asked them to stay away from the cookies forensics page because again, same reason. It's an automated test that doesn't make any sense for a search engine to dip into.
(01:39:04):
And twi.tv has a robots dot text file, which looks like this. I have it in the show notes. It's got a big twi.tv spelled out in block KY characters. Then also has a user agent asterisk Leo's page has a crawl delay of 10, which asks spider's, bots and search engines to only pull one page every 10 seconds and also offers a site map to them, which allows them to discover things that they want search engines to see that they might otherwise not find for themselves. Yeah, that's supposedly good practice. I don't know, <laugh>. Yeah, yeah, exactly. If you say it's good, I'll keep doing it. You know, and I have comparatively simple sites, Amazon dot com's robots dot text file is 152 lines of mostly disallow URLs. Facebook's weighs in at a hefty 610 lines. Oh and it, yeah, we only have three. See <laugh>.
(01:40:10):
Yeah, exactly. You have three. We do have a Facebook TV logo in our robot subjects, but <laugh>, Yeah, yeah, Facebook 610 lines and it's sort of entertaining to browse through. It begins with an off putting block of text, which reads notice collection of data on Facebook through automated means is prohibited. This sounds like Mark, unless you have expressed written permission from Facebook and might only be conducted for the limited purpose to contained in said permission. And then there's a, it says C and then he's got a URL to cite scraping terms of service terms. Holy cow. Right? I know. Then it goes on to list by bot where they are permitted to venture and where not. We have the Apple bot, the ba bdu spider bing bot. You gotta love just saying Bing bot the discord bot. Something known as Facebook external hit also the Google bot, the Google bot image I a archiver LinkedIn bot, MSN bot, neighbor bot Pinterest bot.
(01:41:25):
And then we have, I kid you not the Screaming Frog SEO spider. We've got the cna CNA bot, something called slurp tma, the Telegram bot, the Twitter bot, Yandex and Yeti. And those were all disallow URLs in a long list. Then the file goes through the entire list again, giving them specific allow URLs. So anyway, obviously there are many bots roaming the internet these days and of course there's no practical way for any website to refuse to serve pages to any agent that wishes to request them. In other words, there's no enforcement mechanism. The whole robots dot text facility is simply advisory.
(01:42:13):
But when it was recognized that beyond a single robots dot text file, there were a great many more sorts of metadata that websites might wish to publish. Not to users, but to automated visiting bots, scanners, other tools. Who knows what. It became clear that a more mature mechanism was needed and the first order of business was to avoid cluttering up the site's route directory with a growing number of random metadata files. So the Worldwide Web consortium, the W three C standardized upon the placement of everything else into a specially designated sub directory off of the route that directory is named dot well hyphen known or forward slash dot well hyphen known slash Wikipedia explains it this way. They say a well known I is a uniform resource identifier for URL path prefixes that start with slash dot well-known slash they're implemented in web servers so that requests to the servers for well known services or information are available at URL's.
(01:43:34):
Consistent well known locations across servers. Well knowns are uniform resource identifiers defined by the I E TF in RFC 86 15. So that's a relatively recent one. They say they are URL path prefixes with the start of dot well known. This implementation is in response to the common expectation for web-based protocols to require certain services or information be available at URL's consistent across servers regardless of the way URL paths are organized on a particular host. In other words, let's eliminate website to website variations for this one particular purpose. So Wikipedia says the URL's implemented in web servers so that requests to the servers for well known services or information are available at URL's consistent with well known locations across servers. The I e TF has that they write has defined a simple way for web servers to hold metadata that any user agent, for example a web browser can request the metadata is useful for various tasks including directing a web user to use a mobile app instead of the website or indicating the different ways that the site can be secured.
(01:44:57):
The well known locations are used by web servers to share metadata with user agents. Sometimes these are files and sometimes these are requests for information from the web server software itself, meaning another url. The way to declare the different metadata requests that can be provided is standardized by the I e TF so that other developers know how to find and use this information. Okay, so Wikipedia lists 48 different items which are currently defined under the dot well known, including the one that we'll be talking about in a minute. So Wikipedia is keeping itself current cuz this was just released most of the 46 well known item names are obscure, but a few are interesting. Keybase dot text, which Wikipedia says is used by the Keybase project to identify a proof that one or more people whose public keys may be retrieved using the keybase service have administrative control over the origin server from which it is retrieved.
(01:46:08):
In other words, it's an authentication mechanism located at dot well hyphen known slash keybase dot text. The one we originally talked about when we first introduced the concept of the dot well-known sub directory was security dot text. Wikipedia reminds us that security dot text is a proposed standard for websites security information that is meant to allow security researchers to easily report security vulnerabilities. The standard describes a text file called security dot text in the well known location, similar in syntax to robots dot text, but intended to be machine and human readable for those wishing to contact a website's owner about security issues. Security dot text files have been adopted by Google, GitHub, LinkedIn, and Facebook and that was countless others. So as we know, security researchers have been frustrated in the past by the difficulty in finding the person who should receive problem reports. They'll send an urgent email to the contact us info with the only thing they can find and either never receive any reply or receive a canned.
(01:47:34):
Thanks for contacting us. Your query will be examined and the proper person will get back to you shortly if that ever happens. So the idea behind security dot text located in the well known directory is to allow a site's technical support staff, likely not upper management, but the guys who are actually down there pulling wires to prearrange a means for being directly informed of things that they want to know that someone might discover. Now two engineers at Apple, Ricky Mandela and Teresa O'Connor realized that in addition to the existing well known facility could be employed to help users and perhaps their password managers and other tools to know where to go to change their passwords for any supporting site. It's a small thing, but some of the best ideas are, as we know, the problem is that there is no commonality among websites for logging in and out and managing one's identity.
(01:48:48):
It's a completely ad hoc invention over and over again for each website we're beginning to see some coalescence of UI features. The idea of account management being located in the upper right corner of website pages. That's becoming increasingly common. But what is definitely lacking is any generic direct access mechanism which would allow a user or some automation to get to specific aspects of a site's account management. In every case it's currently necessary to click on a series of links looking at the result of it, of each click, make a best guess as to what to click on next. As we navigate toward our desired account management feature, the idea that occurred to Ricky and Therea was to add an object to the dot well known collection named change password.
(01:49:52):
Whenever that resource was requested, the reply would be a URL which the requester should then follow in order to be immediately presented with a site's password change page. Once this is caught on, you can imagine that password managers and web browsers would add a change site password feature to their own user interfaces. When the user visits a site, just as browsers currently request the fave icon to show the site's small icon identity, they would passively query for the presence of the site's change password resource in the dot well known sub directory. If the query returns a 4 0 4 not found, then the browsers or password managers change site password option would be disabled and grayed out. But if the query returns a change URL password, the client's UI feature would be enabled. And if it's user should click on change site password feature, they would be immediately jumped to the proper page at that site.
(01:51:10):
Having short circuited any and all intermediate stages to get there creating complete unification. It's true that some password managers have taken it upon themselves already to offer somewhat similar features across a limited and specific collection of sites. But this has been accomplished through brute force automation of the user facing user interface for a specific site, which is prone to failure if or when a site upgrades or changes its user's experience. What this new change password standard accomplishes is to provide a means for cutting out all intervening guesswork and intermediate stages to provide a url which will take its visitor directly to that page. And I mentioned that it's a standard because it is the WC three has taken this up and has published the first draft of this new edition to the dot well-known website metadata.
(01:52:15):
Its specification page is titled a well known URL for changing passwords, which is somewhat unfortunate since some of the tech press has apparently only read the title and assumed that this was more than it is. As we've seen, this doesn't actually change anything. It simply redirects its visitor to the website's password change page in the process, transparently bypassing all of the intervening steps. So it's a baby step. We could wish that the URL returned an XML format, soap style API endpoint, which would entirely automate the process of automating the user well, I'm sorry, the process of authenticating the user with their current username and password except the replacement password and confirm that this update has been made at the server side. But that's not what we're getting. But we're getting the first small baby steps in that direction. It has the benefit that it should be quite easy to implement and any common frameworks should be able to easily support it so that it can become widespread quickly. Again, a useful baby step. Well, we're making progress anyway. Yep. I mean you wouldn't expect a unified way of doing this, I guess maybe there could be, but Oh yeah. I mean it wouldn't be difficult for someone to specify that at all.
(01:53:54):
Someone to specify it, but then somebody else to adopt it in a million pages and it really would be cool when you think about it, if like so cute if, well if Bid Warden E, even at this level, if Bit waner last Pass for example, had in their dropdown change site password that jumped you for any site immediately to their password change pages, that would be very cool. That would be great. Yeah. So this gives us at least that much good. Anything that could automate this process would be very valuable. Would Keys help this? Could there be an automated system for that? I guess not. Cuz there's no credential to change, right? You don't. Right? PAs keys, actually thank God it obsoletes usernames and passwords, right? Completely. It replaces them both. What do you? But you must allow, and I know you do, and squirrel allow a way for somebody to change their proof, right? Oh sure, Yeah, yeah, yeah. You can still have a username and password and you are able to change your squirrel identity there. Actually, the way you do it is you give them both your old and your new. Ah, perfect. So it validates you with authentic, it validates you with the old and then switches over to the new. But there is that issue, and I don't know what's gonna happen with Paske if I lost my phone.
(01:55:23):
There are issues mean there are times you have to change this stuff, right? Yep. Even with Pasky and Squirrel. Yep. And what was so nice about Squirrel was if you lost your phone or didn't matter, right? Cause you, your entire identity was a single QR code, right? Right. Yeah. And you just put that in a drawer somewhere. Steve Gibson. See that's, I think that's the obvious and smart way to do it. But okay, fine. Steve is the best. grc.com is the place to go. You can get a copy of the show there as well as our site grc.com. The GRC version, actually there's two unique versions. There's a 16 Kilobit audio version which is, what is that? One seventh, one sixth the size one sixth the size, I guess. And the advantage of that is you can download it in a limited bandwidth situation. Doesn't sound great, but it's there.
(01:56:17):
That's the version that Elaine Ferris uses cuz I don't know what, she's got a satellite internet, I guess she's in the middle of horse country. She does the transcriptions, downloads it and types it all out. And that makes it easy to read. It's great for search, it's great to read along as you listen. Of course, Steve has the full quality audio, the 64 Kilobit audio as well. grc.com while you're there, pick up spin, right? The world's best mass storage, maintenance and recovery utility. I was using it the other day and I saw, oh my god, the copyright 2004 <laugh>. But if you write it right, you don't need to fix it all the time. However I'm hoping it'll be a 2022 copyright, if not a 2023 copyright for 6.1 that's due imminently, probably maybe early 2023. Let's not rush shit. Yeah, it's gonna be in full.
(01:57:07):
It'll be running within a week or two and then in Alpha test, right? We gotta make sure it's perfect before we release it. But if you buy now, you'll get a copy of that when that comes out any day. Now we have a copy of the show. We have actually two copies. We have the audio that Steve has, but we also have a video for some reason you wanna watch and we do, There's some visual aids, there's stuffs to see, There's pictures <laugh>, a twi do TV slash sn. There's also of course a YouTube channel dedicated to it. That's only video. But a great way to share it with somebody else is because YouTube will let you share a little clip, which is nice. And then probably the best way to get it, if you wanna listen every week, and I'm sure you do, is subscribe to it in your favorite podcast player and that way you'll get it automatically the minute we put it out.
(01:58:00):
We do security secure now on Tuesdays at about, it was a little late today, sometime between one 30 and 2:00 PM Pacific, four 30 and 5:00 PM Eastern 2030 utc. You can watch us do it live. That's why I mentioned the Times because we actually do stream it as we do it and that's why the time varies cuz shows before Go long or whatever. But you can watch the stream@live.twit.tv. You can also chat with us@irc.twi.tv of course. Let me put in a plug for Club Twit because that really supports a lot of our efforts here. Advertising has gotten us this far, but it may not get us much farther. We really need the support of our listeners. And the best way to show that seven bucks a month, you get ad free versions of all the shows cuz you're paying for it. We don't need to advertise to you, you don't even hear this.
(01:58:54):
You'd also get access to the Tip plus feed, which has shows we don't put out in public, like shows we're working on for the future. Like Hands on Mac with Micah, Sergeant Windows, hands on windows with Paul Thoro, the Untitled Linux show. Now that Steve is becoming a Linux head with Jonathan Bennett, the GFIs with D Bartolo Stacy's book club's coming up on the 27th. That's exciting. Can't wait for that. All of that is part of the club and that great discord too where you can chat along with us. And most importantly, that seven bucks a month gives us a consistent income stream that we can use to plan for the future. And right now, the future is cloudy, shall we say. So please, if you've thought about it, please follow through and go to twit.tv/club. We do wanna welcome, we got a new corporate membership.
(01:59:47):
We're always happy to welcome our corporate memberships. I think 50 new users through that, that that's also there at the website, twit.tv/club. Let me see if they, I don't know, I guess I don't know if I can say their name. That's okay. Just know. We know. Thank you. And we appreciate the corporate membership twi.tv/club. You can also, if you just wanted security now, and I know some of you only listen to security now, we offer that at the same place for 2 99 a month. Just, but that's the only benefit is the ad Free security now. Thanks Steve, I appreciate your being here. We'll see you next time on Security now. Righto.
Speaker 2 (02:00:33):
Bye.
Mikah Sargent (02:00:37):
Is that an iPhone in your hand? Wait a second. Is that an Apple watch on your wrist and do I see an iPad sitting there on the table? Oh my goodness. You are the perfect person to be watching iOS today. The show where Rosemary Orchard and I mic a Sergeant talk all things iOS, tv, OS, Watch OS, Homepod OS. It's all the OS's that Apple has on offer and we show you how to make the most of those gadgets. Just head to twit TV slash iOS to check it out.