Security Now Episode 881 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for security. Now, Steve Gibson is here with an update on the update. <Laugh> on last week's Microsoft patch Tuesday, maybe not as good as we thought including the weirdest printer solution <laugh> and problem you've ever heard of we'll then talk about the on and off again, VBA macro solution for Microsoft this time. Microsoft says, no, no, this is, this is definite. And finally he calls it the Demonn box, a GPS tracker. That is so woefully insecure that if you have it on your car and you may not even know, you must remove it immediately. It's all coming up next on security. Now, podcasts you love from people you trust. This is TWI.
Leo Laporte & Steve Gibson (00:00:52):
This is security. Now with Steve Gibson episode 881 recorded Tuesday, July 26th, 2022. The MV seven 20. This episode of security now is brought to you by Melissa. Make sure your customer contact data is up to date. Try Melissa's APIs in the developer portal. It's easy to log on, sign up and start playing in the API sandbox. 24 7 get started today with 1000 records, clean free, and melissa.com/twit And by BitWarden, get the password manager that offers a robust cost effective solution that can drastically increase your chances of staying safe. Online. Get started with a free trial of a teams or enterprise plan or get started for free across all devices as an individual user at bitwarden.com/twit. And by Barracuda. Barracuda has identified 13 types of email threats and how cyber criminals use them every day. Fishing conversation hacking ransomware, plus 10 more tricks. Cyber criminals use to steal money from your company or personal information from your employees and customers.
Leo Laporte & Steve Gibson (00:02:04):
Get your free ebook at barracuda.com/securitynow it's time for security. Now the show we protect you, your loved ones, your privacy online with this guy right here, Steve Gibson. And by the way, Steve, at least half a dozen people came up to me and said, cuz I had mentioned when I was going on the cruiser two weeks ago, oh, everybody's gonna say hi to Steve. They came up and said, tell Steve. We said, hi. <Laugh> so everybody you should accomplished mission accomplished. I said, we begged Steve to go on it. Maybe next time Steve will go. If you, why now we know why we didn't. You were smart <laugh> you were smart cuz yes, Lisa and I did contract COVID and a couple of, other of the twit group did that I know of, but most of them emerged on. Scathed had a great time.
Leo Laporte & Steve Gibson (00:02:54):
Thank you all for joining us. We really appreciate it. And I promise I am gonna strong arm, Mr. Gibson, maybe when C's over, we could do it. Okay. Or you pick the trip you want, you wanna go to Ireland, whatever you wanna do. Sounds good. All right. What's going on in the world, Steve? Well this is security now 8 81, our final episode for July. We're gonna start off by updating our, our actually updating our follow up to this month's patch Tuesday, which we did last week. Thank you, Jason, for, for filling in for Leo. Yes. Thank you, Jason. Things were turned out to be more interesting than they seemed at the time. Then we keep up with the evolving state of Microsoft offices, VBA macro foreign documents. Wait, there's more. Oh my God. And we got drama now also. So gonna add that, we also have a fabulous bit of news about some default security policy changes for windows 11 announced by Microsoft.
Leo Laporte & Steve Gibson (00:04:04):
And we also see that those are not easy for them to make. Then with August rapidly approaching, we've got a few calendar notes to mention. I have a welcome and long awaited bit of spin, right? News to share. We have a, a bit of miscellaneous and some brief bits of listener feedback to cover. Then we're gonna take a deep dive into, and this is why the podcast's title is the MV seven 20. It's a poor by design security of a very popular and frighteningly widely used aftermarket GPS tracking device. Yes, $26 from Amazon. Wow. you don't want one of these little puppies. Wow. Okay. Anywhere near you or your enterprise yet one and a half million of this particular model. Wow. Are out there and you're not gonna believe like this. Just the lack of care. And it's this, it's a another perfect example of the weird place we're in now where, where we're we're so such high end technology is available.
Leo Laporte & Steve Gibson (00:05:23):
So inexpensively that there's almost no budget for security or no apparent concern whatsoever. And people are buying these things because Hey, 26 bucks, I want one click and then, you know, if phones home to China and everybody else. So anyway oh, and Leo we've got, this is, this is one of the best pictures of the week in a long time. So I think another great podcast. I haven't peaked. I haven't peaked it. You should be on mic when you first see. Oh good. Because all right. It's no. So we, so the audience could capture your reaction. I will. I have not looked all right. I've been very good. Okay. I look forward to this. So I I like to save it for myself. It's one of those that takes some visual parsing, but when it hits you, it hits you hard.
Leo Laporte & Steve Gibson (00:06:14):
<Laugh> I love those. I love those. Cause you go, oh our show today, my friends brought to you by Melissa and you need Melissa. If you've got well, an address list, a customer list, maybe a supplier list, poor data, quality costs organizations on average, 15 million every year, 15 million every year. And of course it deteriorates the longer poor quality data stays in your system. The more you you're losing, the more it it's like it's rotting away to ensure your business is successful. Your customer information needs to be accurate. And that's why people turn to Melissa, a leading provider of global data quality and address management solutions. In fact, I'd say the leading provider there's another side to accurate data. Of course it's not merely that you're mailing something to the wrong address or emailing it to the wrong address or calling the wrong phone number.
Leo Laporte & Steve Gibson (00:07:15):
It's also a customer service issue. If you address somebody by the wrong name, when they call in or you know, you call 'em George and their name's Georgia, that's not such a good look. Especially when you're dealing with somebody who might already be a little upset calling your customer service line. You need Melissa's identity solutions. They have real time identity verification service. You could do it via an API via SAS. It will do identity ID and document verification, age authentication, global watch list screening. This is important all for security, right? You wanna establish the identity of a, of a custom customer. You may even have AML or KYC compliance requirements. This will satisfy them. You could easily tailor Melissa to your specific signup process and whatever your risk management requirements are. So you'll get fast onboarding fast eCommerce checkout, but you'll still protect your organization against fraud.
Leo Laporte & Steve Gibson (00:08:15):
And you know, live up to your compliance requirements. Your anti-money laundering requirements. You wanna, you wanna protect your data with Melissa because they have 2.1 billion, 2.1 billion clean, valid validated records. That's a lot, that's a lot. You'll be ensuring compliance in the anti-money laundering, politically exposed persons, the bank secrecy act, whatever country you're operating in, you could score and target customers with detailed demographic and firmographic data. Appends you can complete customer records too, because as notoriously the records, missing names or addresses or phone numbers and email addresses, you can go in there, add them, correct them, make sure they're right. And of course, Melissa treats your data like the gold that it is undergoing continuous independent security audits. There's SOC two HIPAA GDPR compliant. You can do it you know, use Melissa in any way that suits you. They have an on-prem solution.
Leo Laporte & Steve Gibson (00:09:16):
As I said, an API or SAS solution, you can even, they have an FTP, a secure FTP server. You can upload a customer list to and download the clean one. There's all sorts of ways to do it. And it works in 240 plus countries and territories batch address cleansing per produces a entire clean list, accurate, complete. You can do identity verification. They have geocoding enrichments, which means it'll take an address and give you longitude and latitude. You can remove up to 95% of bad email addresses from your database. They've got an app too, by the way, you wanna try that on iOS and Android, it's called lookups. You can, you can actually do it ones, Z two to search addresses names and more right there in the app. I think you're gonna like Melissa. I know you're gonna like Melissa. And I know the businesses who use Melissa universally say, it's a must.
Leo Laporte & Steve Gibson (00:10:08):
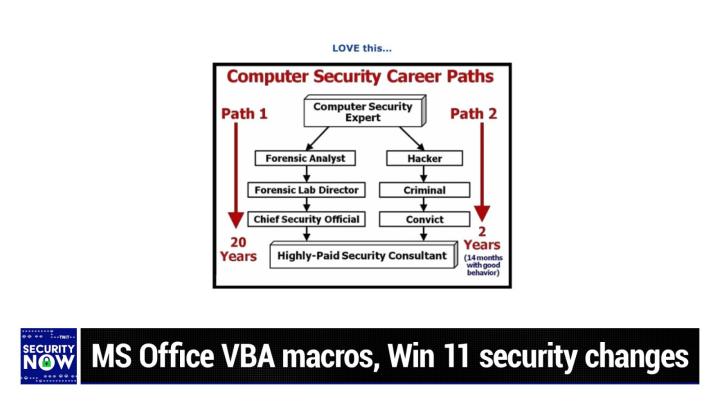
You need it. Make sure your customer data is up to date. Try Melissa's APIs in the developer portal. It's easy to log on, sign up and start playing in the sandbox. 24 7 you'll get started today with 1000 records. 1000 records clean, free, great way to try before you buy at melissa.com/twit melissa.com/twit. We thank of so much for their support of security. Okay. Let me push press the magic button here. I have not looked at the picture. I'm going to pull it up right now and we will look at it together. All of us, all right. It says, love this computer security career paths path one path two path. One is a long one 20 years, forensic analyst, forensic lab director, chief security official, or go the hacker criminal convict two years. And you can be a high paid security consultant in 14 months with good behavior.
Leo Laporte & Steve Gibson (00:11:08):
<Laugh> I love it. It's unfortunately kind of true. Isn't it? It's that's, that's part of what makes this thing work so well. So the, the, it starts off with a sec, a computer security expert, and you have a, you have a, you have two choices path. Yeah. A fork in the run run. Yes. You can become the forensic analysis and then get promoted to be a forensic lab director. Eventually get to be the chief security official and then become finally after 20 years, the highly paid security consultant. That's the traditional path. Or you can, you know, know your way around computer. Okay. Yeah. Yeah. You, you start, you, you do some hacking <laugh> you get caught, you get caught. Yeah. You're you get caught and you're a criminal. So you get convicted and it shows two years later, or 14 months with good behavior you're out. And now you're a highly paid, paid security consultant taking the shortcut route. Now it has been noted that you will end up with a felony on your record, which may, although on the other hand, you might just, you know, depending upon who's hiring you, they might just figure, Hey, that's just, you know, that's the way we we saved 18 years in hiring this kid.
Leo Laporte & Steve Gibson (00:12:30):
That's the price of entry. I love it. Okay. So last week, which was the week following July's patch Tuesday, I congratulated Microsoft for their having patched some 84 known flaws without simultaneously crippling windows. But since then it has come to light that I may have been somewhat premature in my praise published under issue details for July, 2022 is the topic. This is Microsoft's publication printing to USB connected printers might fail with the status of confirmed in their little table. They said, so it's the affected, or I should say afflicted platforms include both client versions of windows 10. This is windows 10, only 20 H 2 21 H one and 21 H two. And the server version 20 H two Microsoft explains Microsoft has received reports of issues affecting some printing devices. Following installation of windows updates released to June 28th and later symptoms observed may include windows, might show duplicate copies of printers installed on a device, commonly with a similar name and the suffix copy.
Leo Laporte & Steve Gibson (00:13:57):
One applications that refer to the printer by a specific name cannot print normal printer usage might be interrupted for either scenario resulting in a failure of printing op printing operations. Okay. So as we know, windows printing like windows, land manager, networking has pretty much always been a mess. As we know last year's windows, printer, spooling security debacle, dogged Microsoft for more than half a year. Some of windows architecture has not aged well through the decades. And it's understandably difficult to ever make that decision to scrap something that mostly works in favor of a major redesign, which while, you know, know fixing the problem, the underlying problems is certain also to break a large number of things that are currently working, you know, especially when there's so much hidden dependency upon the existing system, just being, you know, being left the way it is. So it really is the case that at this point, Microsoft can barely change anything without breaking everything.
Leo Laporte & Steve Gibson (00:15:20):
I think that the, that probably when a future history is written of this era of Microsoft at windows, it will show that they painted themselves into a corner from which there was no escape. And while it's easy for us to say, oh, look, they broke it again because of the way, you know, how creaky it's all become. It's like, yeah, but you know, when were they supposed to stop and like break it badly in order to fix it? You know, actually it's what I did with spin, right. I said, okay, no more. Anyway, we'll talk about that later. But it could not be any more clear that windows is at this point, not actually getting any better. Right? I mean like nobody wants any of what they're doing because it's not better. It's now clearly getting worse. Anyway, but that doesn't work with, or it isn't aligned with, I guess, guess we should say with Microsoft's need to appear to always be moving forward, even though no one wants them to.
Leo Laporte & Steve Gibson (00:16:23):
Anyway, if by some chance you are printing to USB stopped working earlier this month and you have not yet decided to tackle that, that problem hoping maybe like that, you know, August's patches will bring it back to life. Again. the trouble appears to surround the spontaneous creation of a duplicate printer instance where it, the duplicate somehow obtains the proper configuration while upsetting the configuration of the original instance in their, they have like this section of workarounds, Microsoft says open the settings app, navigate to Bluetooth and devices and select printers and scanners. They said, if there appears to be a duplicate installation of an existing printer, such as with suffix, copy one, confirm if printing works for this printer, they said, this printer should operate as expected. If there's a need to use the original printer installation and not the duplicate, you know, the one which now works, they said, right, click the duplicate printer, select printer properties, and select the ports tab.
Leo Laporte & Steve Gibson (00:17:53):
Observe the port in use. Now open printer properties on the original printer, select the ports tab from the list displayed, select the port option in use by the duplicate printer. <Laugh> <laugh> can you believe this Leo like preserve the port in use? Yeah, so, okay. So apparently reading between the lines of this workaround, it sounds as though whatever it was, Microsoft was attempting to do, <laugh> in intended to create a new instance of a USB printer, copy the original stances settings into the new instance. Then presumably remove the original instance and give the new instance the name of the original. Why? I, I know why be because windows <laugh>. So it, it sounds like for some users it's huge, <laugh> it? It's a, it's a disaster. This is what Microsoft is saying. If you really want to print, you know, like, whoa, you wanna print in windows?
Leo Laporte & Steve Gibson (00:19:12):
Well, here's how, oh, so my God, it sounds like, like the process got part of the way along and then died. And it did not back itself out and revert to the original configuration, which was working before all of this began. Mm. Like everything was fine. USB printers were going, and then <laugh> you got a, you got a copy one which works the, the not the, the original one stopped working. And they said, if, if your application addresses printers by name, you know, like, oh, okay, well the, the name it has broke, like we broke it. So <laugh> so copy the name to a new printer. Oh my God. This is why I do not answer printer questions on the radio show right there in a nutshell. Right. In fact, Lori, I think it was early last week. She said <laugh> nothing's printing. And I said, oh, cause I mean, and I had, I was right in the middle of like, this really cool work on spin.
Leo Laporte & Steve Gibson (00:20:24):
Right. And I just, or maybe it was after dinner and I was ready to go back to it. And I had my Eve, I had my evening planned. Yeah. Well there went, my evening here goes your you're a good husband. And, and you're a good husband. And, and she said, she said, honey, like when it was all working again, she said, how could anybody else do what you just did? Yeah. And I said, well, you, you open the printer dialogue, observe it working. And you observe, you observe the working printer. <Laugh> <laugh> oh, this is that's that's in a nutshell. That's exactly what Lisa says is what everybody I know says probably what everybody who knows the people who listen to this show say, which is, how does anybody use this crap?
Leo Laporte & Steve Gibson (00:21:10):
Unless you've got somebody, an expert, a local expert. There are, there are people who go buy a new one. Leo. Yeah. They just, most people, okay. Most people, the, the, yeah. It's like, well, you know, it, things began falling off. And finally, I just decided to go to best buy <laugh>, you know, <laugh> just, you know, they're not that expensive anymore. I just, I got one that's smaller and lighter and it's faster. Of course it's and it's exacerbated by terrible printer drivers. I mean multiple versions of windows. Oh that's yes. In fact, I was gonna talk about that. I went to HP's site just to remind myself how many hundreds. Yes. Of megabytes. Yes. It's it's a quarter gig of printers driver and you better get the right one because you can, oh God, it's a mess. Yeah. And the, the time before this last time, when Laura needed me to fix her printer, <laugh> I, I really, I mean, you've done this more than once.
Leo Laporte & Steve Gibson (00:22:12):
Oh yeah. Which we got about six months out at the last round. So that's, that's pretty good. So I realized you just need like ungodly patience. It's like something is spinning and just leave it alone. Don't touch it. I'm so te I'm so tempted to think, oh, it hung or it's not going anywhere. It's been 15 minutes. No, it needs hours. And I don't know why, but I just, I like finally, I just, just like said, I just gritted my teeth. I said, I'm just gonna wait. I'm gonna just wait. And then like, after a couple hours, something changed, I was like, oh, look. And then when, when I just like, let it really take, and this is we're running on a state of the art Knuck, you know, with like N VM E memory. It's this stuff is fast. Hers is the fastest machine in the house.
Leo Laporte & Steve Gibson (00:23:07):
Cuz of course, you know, I work on stuff you have to whine. So Lisa has the fastest machine in the house too. That's again. Yeah. We're good. Husbands. We're good husbands. Yes. That's all I can say. Oh Lord. Anyway, this is, yeah, this is windows though. And yeah, it is life and it's life is a TECA this morning, before I came to work, I spent an hour and a half trying to get the Sono stuff to talk with <laugh> and literally the last thing I did before I came into work was order a vis sound parts. I screw it. No more Sonos. All right. Yeah.
Leo Laporte & Steve Gibson (00:23:46):
And, and I've told a story about my wonderful realtor, Fred, Judy, who went from what she called her modem, which was actually a ti silent 700 Uhhuh. She, she was a realtor. And so she would dial the phone and then take the, that, that, that MLS that olive of green handset and stick it into the acoustic coupler cups. <Laugh> on top of the thermal printer. And then she would like the listings. Yeah, yeah. Get her, her, her scrolly that stinky thermal paper curls up roll. Yeah, yeah, yeah. The curls up. Yeah. And, and, and she would take that off into, you know, to a client anyway. So we moved her. I was there when we moved her to windows and oh, <laugh>, it was just, it was she, she called, she didn't realize that the internet was not Google. So she, she, you know, she thought that it was the same.
Leo Laporte & Steve Gibson (00:24:41):
And she used to say to me how, like when I would right click, I would say, oh no, Judy, you gotta right. Click what? I said, you see how your mouse has a, has two little ears up there, a left and a right ear. You push the right one in order to get that little menu. So what those called ears? Well, I had to help her along. So, so cuz if I said button, she'd say no, there's no button. There's no button. Oh. And that used to happen too. Oh. With her husband Jan, I'd say, oh, Y cuz I'd be like, I'd give up talking to Judy. I'd say Judy, put Y on the phone. <Laugh> and I'd say, okay now do you see that button? And he would go what? And finally I realized I, we were both looking at the same thing.
Leo Laporte & Steve Gibson (00:25:25):
Yeah. But different. He saw a rectangle with a shadow. Yeah, that's right. And I was calling it a button, a button. And he said, I said, no. Okay, John, it's that rectangle where see how it's shadowed to kind of look like it's it kinda looks like a button 3d. Oh and what should I do? Oh, we have everyone. Who's listening is immediately identifying with this where you start to describe stuff. <Laugh> there. It's just hysterical. There's a pick, there's a old video of John Mayer. The, the folk singer talking to his dad outside a concert. And he's on the street talking to his dad and he's going, no, dad, the start, the start. But it's in the lower <laugh> and when you see that you go, yep. It's universal. Well, and, and I remember saying to someone, I don't remember now who, but, but when I was trying to describe something by voice over, over the phone, I finally said, okay, here's the problem.
Leo Laporte & Steve Gibson (00:26:23):
We don't, we do not share a vocabulary. Like I, I, I cannot describe to you what has to happen. You. Oh, it's not just a vocabulary. It's use you use terms. No, no. Yeah. It's an entire different vision of the world and how it works. It's we're in different planets. I think it might even be a gene. There's something it's just, and that's not, not making a ju value judgment. It's not good or bad. No, but there it's different. Maybe it's different dimensions of, you know, well, and Judy finally asked me, she said, how, how, like, how is a very big question? People ever get this? And I said, no, Judy, you will die. <Laugh> I mean, it's like the dinosaurs they're gone, you will die. That your inability to navigate with a mouse will go with you. And, and everybody will be full of people who do hate.
Leo Laporte & Steve Gibson (00:27:22):
They've always had mice who knew that and who knew the mouse is now going away. It's all touch, baby. Yeah. That's probably why. Yeah. Nobody can figure this. Yeah. I've actually made the mistake after using a, a machine with touch for a while. You start touching the screen of things happens. Yep. And it's like, you get, you get a weird little ripple that kind of moves away from where you touch because of you disturbed the liquid crystal underneath. But it's like, okay, we have a Evan essence photo has provided us with new album art. Steve, I think you'll enjoy it. Disaster disaster. Now ladies and gentlemen, that's the name of the show disaster. That's a new album art.
Leo Laporte & Steve Gibson (00:28:04):
All right. I'll stop interrupting. Go ahead. Okay. So the continuing saga of windows, VBA macros as yet another example of one of Microsoft, very poor, early design decisions, not aging well and their refusal for many years, not to simply do the right thing. We have the continuing saga and drama of windows, VBA macros last Wednesday night. Okay. Now wait a Mike. Now when I left <laugh> this was all resolved. No, no. Okay. No. All right. Last Wednesday night they confirmed Microsoft confirmed that it was resuming the rollout of their plan, which they first announced earlier this year, back in February, which is when we ha through the party. But then, you know, that announcement back then was greeted with great relief by everyone who understood what it would mean for the security of Microsoft's much abused office documents. After years of head in the sand policy, Microsoft would finally be blocking the execution of remotely received VVA macros by default, across most office apps, predictably.
Leo Laporte & Steve Gibson (00:29:22):
This would break some things, which of course explains Microsoft's reticence to do the right thing sooner. We've never really talked about the pushback against this change, but I came across some interesting bits, which addressed that even though Microsoft declined to provide information about why the, the effort had been paused. Several experts said, customers complained about this new, well, this change. It's not really a new feature. It's a change. Michael TA the technical director for VO, which is a company specializing in malicious content filtering in the cloud. He told the record that he works closely with partners in the banking and financial sectors and explained that macros play an integral part of our clients' business workflows. He said that the initial block caused a massive hindrance on business productivity. Basically the recession was that we're heading into was caused by Microsoft's decision. No. Okay. What happened was that something changed just as Microsoft warned everyone.
Leo Laporte & Steve Gibson (00:30:45):
It was going to back in February when they said to get prepared, they, they told everybody in February, we're gonna do this. So everybody should like do what you need to because macros are gonna start running are gonna stop running by default the way they have been. Well, guess what it turns out, Microsoft wasn't kidding. Michael T explained, he said, macros are a powerful tool in the financial sector. As they're used to create robust financial modeling, calculate loan interest, automate repetitive labor, intensive tasks. There re there recorded sets of actions which could be run to save time and labor. It's also used to simplify budget forecasting and makes a difference in a day-to-day workload of any entity who's using it. As it speeds up the process to generate a task after finalizing the creation of the macro and setting the variables. Yeah. Right. And you're gonna have to now push a button to make that happen rather than not.
Leo Laporte & Steve Gibson (00:31:58):
<Laugh> anyway, he added that while he understood Microsoft's desire to combat malware like emote trick bot Q bot and dry deck, you know, they should have come up with a more creative approach. So he is complaining right about increased security, a more creative approach to deal with legitimate business use cases for macros and allow for continuity without compromising security. Okay. So, you know, it's not as if macros have been been stripped out of office tools. No. And are gone. No, no, no. They simply property now. Yes. They simply no longer run without provocation. You just need to click a button to explicitly permit their use. And you know, as we've seen, you showed two weeks ago, Leo, that flow chart, I have it in the show notes here again, we've seen that crazy flow chart that enterprise wide group policy settings can be made to cause it to like no behavior change decision box four a in the flow chart is cloud policy to block.
Leo Laporte & Steve Gibson (00:33:26):
Yeah. You said it to no. Then decision box four B gets control, which is titled a DMX or group policy to block that could be used to enable macros at that point. So behavior doesn't change. It's just really a question whether you want to fail secure or fail insecure. Right, right. What the default is. Exactly. And, and so basically everybody, all everybody's having a connection because they want the insecurity of allowing unsolicited unsigned documents of unknown Providence to be received by email or clicked on through, on a web page and just have everything work at the same time. They want Microsoft to somehow magically not allow malware to do the same thing. Well, folks, sorry about that. But you know, I mean, if all they, all the enterprises would have to do, if they wanted, that was to sign. Yeah. The document. Yeah. Sign signing them is another way sources immediately.
Leo Laporte & Steve Gibson (00:34:49):
Yeah. Yes. This is a, this is a decision tree where most of the outputs of the tree are macros enabled. There's only one red box that had the blocked by policy and Microsoft added one at the end. If you get through step after step after step after step after step, there are five steps and you still have reached a decision. It used to just be okay, fine. Let's go now. It's okay. Wait a minute. Yeah. Let's let, let's make sure this is what you want. Are you absolutely sure. And that was too much to ask of. So often of security takes a backseat to the stupidest user, right? Yes. And unfortunately the most common denominator, that's the guy in the corner office. And because he signs the checks, he's the guy who gets to say to the it guys. Well, I don't like this behavior Simmons and <laugh>, you know, so how can any moron think that it's a good idea to allow macros to run unbidden in a document received through email.
Leo Laporte & Steve Gibson (00:36:01):
Well, you have to press's the allow button, come on. It's not, <laugh> completely unbidden you have to inv, you have to say it's name three times. Oh, Leo. I, again, it's just, I mean, so, so, you know, I get it. Yeah. That, that Microsoft doesn't want to offend or upset or ruffle any feathers. These people should just be ignored. I mean, Microsoft warned the industry, the world in February, this was coming. It finally happened. And, and so, oh my God, you know, it's the end of life as we've known it because our macros don't run themselves. So what's the alarm and the current status, cuz it's been back and forth and back and forth. The current status is quote, this is what they said. We're resuming the rollout of this change in current channel, based on our review of customer feedback, we've made updates to both our end user and our it admin documentation to make clearer what options you have for different scenario.
Leo Laporte & Steve Gibson (00:37:19):
So get off your butt, set the group policy if you want it to be different, if you were it to be, if you default secure. Yes, exactly. If you, if you insist on allowing all the malware, you know, fo used office macros in may to infect a whole bunch of people. And if you want to be, you know, admissive of all of this malware by all means, we just, you know, set your document policies, set group policy. But the rest of us have decided it's an inconvenience we're gonna have to actually act a little more securely. Fine. Good. Actually I think signing, signing the macros is yes. Great idea. That's a win. Yeah. Just, just you, you, you, somebody is building these documents that has all this financial, you know, tricky financial stuff in it. Just have, give him a certificate. Yeah. Have him sign it.
Leo Laporte & Steve Gibson (00:38:24):
Yeah. And then it'll, it'll just, it's like moves like grease through goose. Not a problem. Speaking of which let's take a break. I have some grease for your <laugh>. I've been waiting. I've been waiting for you to ask for it. Yes. Let's take a little break more with Steve and security now and goose greasing coming up. I'm gonna tell you about a password manager. Surely if you watch the show, you listen to the show, you know, you need to be using a password manager, especially in your business. Passwords are broken. They don't work, but we gotta use them. They're you know, squirrel has not taken the world by storm yet. Pass keys is still a fantasy. You need password manager, right? Am I wrong? I think you do. Can I recommend the one I use? We've talked about there's lots of good ones.
Leo Laporte & Steve Gibson (00:39:17):
Look, I'm not saying there aren't but there's only one that's open source to me. That's important. Cross platform works everywhere. Mac windows, Linux, iOS, Android, everywhere. It could be used at home. It could be used at work. It can be used on the go. It's trusted by millions. There's one name you need to know. It's bit warden, bit warden with bit warden. You can securely store credentials, not only in your personal vault, but in your business fault. And that's really important for enterprises. When you have a business, we have a business, your employees have passwords to your most important resources, your, your QuickBooks online, your customer resources, your, your, your file, vaults, everything. It's like, they have the numbers on the safe. You wanna make sure that they're gonna store those securely, that when they share them and they will, that they are gonna share them securely.
Leo Laporte & Steve Gibson (00:40:08):
You need bit warden. Every bit warden account starts with the personal vault. And I love this cause bit warden's open source. That vault is free. I asked him, I said, now you're not gonna do what other guys have done and have this free account. Then you're gonna take it away. And no, their business model does not require that they're an open source product set up the personal vault. And then as a business, you can have an organizational vault and that's a really great way to do it. So I, as a user unlock one vault, I get my personal passwords, completely segregated, separate my business, passwords, segregated and separate. I learn good password hygiene. I do all the right things. And by the way, they're always upgrading this product with new features. They, after launching their username generator, we talked about that last month, which is really cool.
Leo Laporte & Steve Gibson (00:40:55):
They are now integrating with three popular email forwarding surfaces that are also open source, simple login, a non-ad and Firefox relay. So this is super cool. So when you're generating, now, you can generate a password, just like any password manager, good, long, strong, completely random passwords, but you can also do the same thing with your username, which gives you more security, right? It's not just, you know, Leo twit.tv. It's, it's a, it's a username. And now you can do that. In addition to generating that unique username through an email forwarding service to add complete anonymity, whenever you generate a username with bit warden, you get the option to create an email alias. You can choose the preferred service that I just mentioned. You can enter the API key for your individual account with a chosen service so that you always use that service is automatic.
Leo Laporte & Steve Gibson (00:41:49):
Select your options, set it all up once generated the new alias is instantly registered to your account. This is just brilliant. So you're now gonna be using not only a unique, strong password. You're gonna use unique usernames, email addresses every account. That's a powerful way for increasing internet security and privacy. It adds protection to logins in the face of data breaches and leaks. This feature is available or will be available on the web vault, the desktop app and the browser extensions. It's gonna come to mobile with a future release coming soon. I just love bit warden. They've got bit warden send. That was another feature they added last year, a fully encrypted method of transmit sensitive information. So if you're a tax attorney or a doctor or whatever, you can, you can send text or files, PDFs, whatever unique and secure passwords for every site, enterprise grade security, GDPR, CCPA, HIPAA, SOC to compliant with an end to end encrypted vault.
Leo Laporte & Steve Gibson (00:42:50):
You also mitigate phishing attacks because if you're always using that auto fill the bit word auto fill, it's not gonna fill on a spurious site. It's only gonna fill on the legit site. Now start with your personal vault free forever. If you wanna do a teams' vault, the teams' organization, option $3 a month per user, which lets you share private data, securely coworkers. They're gonna do that. So you wanna make sure that they do it securely across departments across the entire company enterprises use bit warden's enterprise organization plan. That's $5 a month per user. You start again with the basic free account. That's free forever for an unlimited number of passwords. Upgrade to the premium account for less than a dollar a month. That's what I did not so much cuz I needed the features cuz I wanted to support bit warden. I think they're really great.
Leo Laporte & Steve Gibson (00:43:38):
There's also a family plan up to six users with all the premium features and that's just 3 33 a month for the whole family. Look, you gotta use a password manager. Steve says that I say it bit warden is the only open source cross platform password manager that can be used at home on the go at work. It's trusted by millions of individuals, teams and organizations worldwide. It's the one get started with a free trial of teams or enterprise plan or of course as always get started for free across all devices as an individual user. If you're not using it, do it right now. Go to bit warden.com/twi bit warden.com/twi. There is small company that have a lot of money to spend on advertising. We're we're really honored that they chose this show. I think they knew this is the right place to do it.
Leo Laporte & Steve Gibson (00:44:24):
I just want to give 'em a little extra plug cuz I really believe in them bit warden.com/twi. Okay. Back to Steve. And so goose, greasing. Yes. In <laugh> and in a another bit of happy news. Yes. I mean, I don't wanna like draw any great conclusions here and suggest that maybe Microsoft is actually finally getting a clue. But windows 11 now blocks RDP, brute force attacks by default. Wow. Which is astonishing. Last Thursday Microsoft's VP for enterprise and OS security. Dave Weston. He tweeted from, at windows insider. He said, windows 11 builds now have a default. And he, I mean he understands it's all caps in his tweet, default account lockout policy to mitigate RDP and other brute force password vectors. This technique he says is very commonly used in human operated ransomware and other attacks. He says this control will make brute forcing much harder, which is awesome.
Leo Laporte & Steve Gibson (00:45:39):
Now, everyone listening to this podcast is acutely aware of the importance of default settings. There may as well, not even be any settings since the default is almost universally, what is left to apply? The other thing everyone listening to this podcast knows is that the inherent insecurity created by Microsoft's remote desktop protocol being placed out onto the public internet without any sort of brute force credential stuffing protection in place for years has been insane. It's been responsible for untold numbers of remote network, intrusion pain and loss to Microsoft's users. In fact, the FBI said RDP is responsible for roughly 70 to 80% of all network breaches. What? 70 to 80% my God come through remote desktop protocol. That's incredible because there's no, there there's, there's no protection monitored. Yeah. Right. Yeah. so David's news was incredibly welcome, but my jubilation was somewhat tempered when I saw the local group policy editor settings that he was announcing and celebrating.
Leo Laporte & Steve Gibson (00:47:09):
It is true. Windows 11 now has its failed login attempts account lockout triggering after 10 invalid log on attempts. But the lockout duration is only 10 minutes and oh, come on failed. I know. And the failed attempts counter also resets every 10 minutes, I guess that's not for the random route force guy, but not for targeted attacks. Right. Could someone explain to me how any legitimate user of remote desktop protocol whose RDP client has probably memorized and stored their log on authentication for them anyway making it, you know, which makes it automatic for the user, they don't even have to do anything. How, how any legitimate user is going to be inconvenienced by a lockout, which doesn't engage until they have somehow failed to properly authenticate themselves 10 times since, as we've seen Microsoft clearly goes to great lengths to never inconvenience any user in the name of security.
Leo Laporte & Steve Gibson (00:48:38):
They must believe as I do that, no one, but an attacker would ever trip the 10 strikes before your out rule. So why then give an attacker a clean slate 10 minutes after those 10 failed attempts. So, you know, okay. I, I get it, I guess baby steps, right? So let's just hope and pray that the error message returned by the R D P endpoint is the same for a failed log on attempt as for a block by policy. Just, you know, please Microsoft, just, just say your authentication failed. Don't tell them that a policy has been switched on, which is why authentication has been blocked because of course that would allow them to probe the end point to figure out what the timeout is and what the number of failed attempts counter is and so forth. Just, you know, tell them nothing. Let, let, let the bad guy believe that every single one of their attempts is still hitting a wall.
Leo Laporte & Steve Gibson (00:49:56):
And so that, you know, so that they're not able then to throttle themselves and slow down anyway you know, at least now we have the concept in place of mitigation against brute forcing unmonitored, authentication endpoints, you know, that's some progress and, and really that's the problem, right? Is that almost nobody knows that there security is being pounded on by a credential stuffing attack, 24 7 you know, everyone just sort of goes, oh, that's just, you know, internet noise. Right. Well, in fact, I coined the term internet background, radiation, just these packets flying around as like doing stuff. It's like, ah, yeah, we just ignore that. It's like, well accepted. It's, you know, pounding at you trying to get into your network. And as the FBI said, 70 to 80% of ways in is that, so we're taking note as I mentioned at the top of the podcast, this is our final podcast for July as we're gonna be heading into August, August traditionally contains a few interesting security events.
Leo Laporte & Steve Gibson (00:51:14):
We have the two traditional major hacking conferences, black hat and Def con this year running at, from the sixth through the 11th is the 25th black hat USA. It'll be holding as a consequence of what, you know, the changes that COVID has wrought a hybrid conference, allowing the cyber security community to choose how they wish to participate. The conferences. First four days will be virtual trainings conducted in real time online with all instructors accessible throughout each class. So virtual online, real time and interactive. Then the final two day main conference will occur both virtually online and live in person in Las Vegas at the Mandalay bay hotel and casino. Then as always immediately following black hat is Def con August 11th through the 14th. And I had to smile and it's just sort of shaked my head as I, as I was checking in on Def con's description of itself and its planned proceedings, since I think everyone will get a kick out of what they wrote, I'll share what they had to say.
Leo Laporte & Steve Gibson (00:52:41):
They said started in 1992 by the dark tangent, Def con is the world's longest running and largest underground hacking conference hackers, corporate it professionals, and three letter government agencies all converge on Las Vegas every summer to absorb cutting edge hacking research from the most brilliant minds in the world and test their skills in contests of hacking might Def con comes right after black hat, a conference and trade show for cybersecurity professionals while black hat feels more like a traditional Vegas trade show, Def con is anything, but how's it different from other conventions? Well, first Def con is run by volunteers and it has no corporate sponsorship. Secondly, there is no online registration. So even the organizers really don't know who is attending. When you arrive, everything is paid for with cash, they don't take credit cards. Most of these people attending really don't wanna a record of them being there, everyone from your average, everyday hacker to criminals and agents from government agencies like the FBI, CIA and NSA will attend.
Leo Laporte & Steve Gibson (00:54:12):
When you enter, you pay $280 cash and they hand you a generic badge, no ID is required for admittance. So those two conferences begin. Then you may be subject to spot the fed <laugh> that's part of the game. Isn't it? Exactly. So grow that, grow that crew cut out. <Laugh> and we are also celebrating security nows. 17 to birthday Leo today. No. Oh, on August 19th. Oh good. I have time to bake a, a cake. Good. We have, we have some time you have time to fully recover. <Laugh> August 19th, the anniversary of the first episode of this podcast. Wow. This coming August 19th will be finishing out our 17th year and we begin into year 18. Wow. So Leo, you're an adult almost at adulthood. You can drink, you almost reached maturity. You can't drink, but you can join the army and shoot a gun. I do like my Cabernet.
Leo Laporte & Steve Gibson (00:55:20):
Yes. I think you have to wait until 21. Most least in most states. Yes <laugh> yes. I remember mom after her divorce was dating someone and when she was going out, she'd set us up with a, a you know, a frozen pizza, which she'd quickly bake. Of course. Yes. And, and glasses of red wine that were, were two to one water down. Oh, I got my start. I got my star. I got my starter. That'll keep him, that'll get him to sleep. <Laugh>. And the point is I remember the know the, the, the guy that she was seeing, coming over and look and looking at the kitchen counter. And here were two, you know, eight and six year olds with wine class, you know, with, with red wine. Yeah. We're liking this dinner a lot. Hell, have a nice time mom. <Laugh> that's right.
Leo Laporte & Steve Gibson (00:56:07):
My mom didn't do that, but she did give us TV dinners. And I still have a taste for the weird cardboard flavored corn. <Laugh> I do yes. With the weird, the little they were sectioned off. Yeah. They were off, but the flavors combined somehow silver. Yes. <laugh> so everything tasted the, the same. Yeah, yeah, yeah. The, the, the, the, the, the peas sort of had a what was that whole apple pie mixed in with them? Yeah, that's right. And then there was the fried steak, Salisbury steak, the Salisbury, all the gravy would spill over. Yeah. The gravy of the Salisbury steak. That's right. Oh God. And we used the term steak very lightly. They don't in this context, sell TV. Does Swanson still sell TV dinners? Why would they have stopped? <Laugh> good. Guess? I don't know. I don't know. Microsoft still has pretty problems.
Leo Laporte & Steve Gibson (00:56:59):
So I think Swanson still selling TVs last Friday afternoon, I posted to the GRC dot spin, right.dev news group under the subject it's alive. As we know, I essentially had to take spin, right. Completely offline and down to perform the degree of surgery that was needed. Not only to completely strip out all of spin right's traditional dependence upon the bios, but to also, as I've explained during this journey to completely rearchitect spin right around a data recovery centric device, independent mass storage device abstraction, so that not only can sat and IDE drives connected with a HCI and PCI bus mastering adapters now be communicated with at their lowest possible hardware level, but also so that the next step in spin rights evolution, which will add similar direct access for USB and N V E devices, and whatever else might show up in the future will be able to support plugin drivers essentially without needing any, again, any similar reworking I've done all of that work upfront.
Leo Laporte & Steve Gibson (00:58:23):
I mentioning this because I could finally report that spin, right. Is beginning to come back to life. Humpty Dumpty is getting its pieces reassembled. It is starting to run again. Yeah. it is by no means ready yet. I don't want to give anyone that misimpression I still have lots of work left to do because the surgery that spin right needed broke virtually every assumption that it was originally built upon, you know, assumptions, which were made back in 1987 when we had 14, I'm sorry, 4.77 megahertz Intel, 80, 88 processors with a maximum of 640 K bytes of Ram and a 20 megabyte hard drive was a luxury. I actually, Leo in the show notes, I sniped out the top, the first three lines of the Sr dot ASM file. I, I wasn't sure whether it was 86 or 87 anyway that the fi the header of the file says file colon Sr dot M by wow.
Leo Laporte & Steve Gibson (00:59:35):
Steven M. Gibson. Wow. Created zero three slash 30 slash 87, which that's street right there. That's great. That's the, that's the creation of the first spin right. Data SIM file. Wow. Did you have a macro to do the plus dash dash dash plus? Or did you type that by hand? No, no, no. I figured in fact that was one that was brief I don't of course then, yeah, back that actually, that was before I hired Steve rank was my first non-security or non my first techie employee. I hired, I hired Sue and Sue's been with me for, I think like 36 years or something. Steve was employed number two, and his, the, one of the first things I had him do just to sort of get his feet wet, was to write this massive macro package for brief. And I mean, it did everything I could ever ask it to do.
Leo Laporte & Steve Gibson (01:00:37):
And so I was able to like snap text boxes with a beautiful line drawing characters around. And, and so this is actually an ized version of that. And I, cuz I later wrote a conversion of the, of the beautiful line drawing characters back into AKI. When I, when I as actually it was only, it was recently, it was a couple years ago because I needed to be working. I had to give up brief and you know, cuz it was 16 bit code and it, I would've had to run in a VM and it was just not worth the hassle. So now I'm you used brief for almost as long as I knew you though. I mean, I remember you were the brief. Yes. By the way, I looked more through that listing that assembly language listing from 1987 and Barry deep within it, I found I found this, which I thought was kind of surprising.
Leo Laporte & Steve Gibson (01:01:28):
There is a Salisbury steak, Salisbury steak. Now I don't know if you got these free safety colored rain. It's like a P show. It looks like a, it looks like a brownie in the middle there's it's gingerbread or some. And then remember that's those mashed potatoes that were stiff. Oh. And they were crusty and oh yeah, yeah. <Laugh> we were, we, we were Leo, we were hungry. <Laugh> we were, we need anything that glass of wine didn't hurt though, you know, with the appetite. Yeah. That helps to wash it down. That's for sure. It's so great. Anyway, so you posted that source coat or no. Is that private? That source code? The originally assemble language? I will ultimately release it to the world. Oh nice. Because it ought to the world ought to have it. And I will do that at a point when I, when I am no longer maintaining spare.
Leo Laporte & Steve Gibson (01:02:18):
So you could for somebody can fork it then, which would be cool. Yeah. Or yeah, exactly. At some point I'm just gonna say, okay, I'm it's yours. Hopefully it'll be at a point around where we said goodbye to Jerry porn. <Laugh> somewhere at that level. Yes. You know, I can't wait to have Steve Gibson come on this show <laugh> and talk about the good old days. How, how those things used to spin. They actually space spun. They can, why would you spin something like that? Thank you. Steven Tiber Gibson for joining us <laugh> showed 20,000 anyway. So anyway, everything since then has changed. None of those assumptions are any, they, they no longer hold, but they had been allowed to remain in place even through spin. Right. Six though, like with all things, Microsoft, they were becoming quite old and creaky. So as everyone knows, six one is not a patch to spin, right.
Leo Laporte & Steve Gibson (01:03:18):
Six, even though it's a minor version bump and therefore a free upgrade for everyone who owns six. I am making this multi-year investment in spin right's future today because I've seen the future. And to my utter amazement <laugh> well, yes, spin right. Is still in it right on, you know, so mostly, mostly I'm looking forward to writing the code beyond six one, but I've got, we have to have six one first to create the platform for that. So the point is it's alive. I'm sort of astonished. I mean like I actually have it running and I'm now I'm going through and like finding weird little bits cuz cuz among other things, you know, that it used to be 60 bit code, which means that I'm having to write within segments, which are 64 K and spin right. Used to fit all in one segment that is all of its data and all of its code was in 64 K but with maybe spin right.
Leo Laporte & Steve Gibson (01:04:21):
Five I think is where it would no longer fit. I needed to add things and there was nowhere for it to go. So I created a second segment, but it's a pain to cross segment boundaries. So for lots of reasons. Anyway, so one, one of the things that I've been doing is I've been moving chunks of spin right over into this secondary segment just to make some elbow room for the future. So anyway, it's coming back to life I'm finding the reason I mentioned that is that there were like weird little side effects of code running in a different segment that thinks it's data is in the same, same segment as, as it is because that's always been true, but it's no longer true. And so there's side effects of that. So I'm, I've, you know, it's, I have a ways to go, but it's we're getting there and I'm asking questions in the news group.
Leo Laporte & Steve Gibson (01:05:14):
Like should the log files still use the line drawing characters or should when we log, should I translate everything into AKI and everyone agrees, it should all be moved over to AKI because no one's viewing the log files in Daws anymore. They're they're viewing 'em in their own operating systems. So maybe UT F a will will see, but anyway, progress on that front. Woo. Also PF sense and tail scale, everyone knows that PF sense is my preferred internet firewall router solution it's open source has a fully capable, free community supported release it's rock solid runs on most hardware including little fan analyst, consumer routers, like my little favorite that net gate SG 1100 and it has a very comfortable web-based UI for, for configuring it. And it'll do anything you could want. As I mentioned, I use it to glue my various locations together over permanent links to, to, to keep, you know, essentially run a, a single what we would now call an overlay network.
Leo Laporte & Steve Gibson (01:06:27):
But I did it like the old fashioned way before we had easy to use overlay networks, which brings me to tail scale among PF sense. As many features is a modular package management system, which makes managing the router. You know what I would call man page free pleasure. You don't need to, you know, you just point and click and things go. So the news ING should have a package manager. That's just the best. Yes. Yeah. Yes. It's just, it makes life possible. Yeah. So the news I wanted to share is that PF sense will soon with its forthcoming version 22.05, which is now the dev release it. When it goes into the main channel, it will be receiving built in drop menu, selectable support for the tail scale VPN mesh overlay network. Nice. That's the way to do this. You missed somebody last week.
Leo Laporte & Steve Gibson (01:07:24):
Leo commenting that we, we were talking, remember the week before we were talking about using a VPN mm-hmm <affirmative> in, in a cafe mm-hmm <affirmative> or, or somewhere mm-hmm <affirmative> someone mentioned just, just bring a little box that has a raspberry pie on it, running tail scale. And essentially you can simply plug into that and be on your home network, wherever you are. Thanks to, you know, an overlay network, which works very much the way how hamachi did back in the day hamachi was the first overlay network to, to become really popular. So anyway, that's kind of cool. So like hamachi, you'd be appearing to yourself to be on your home network. Yes. Would, would all the other home network features be available as well? Yes, you, would it be like you were plugged into your router at home? That's that's very cool.
Leo Laporte & Steve Gibson (01:08:18):
I like that while, while tail scale is built on wire guard. So it uses that state of the art minimal next generation VPN, which is the improvement over open VPN, which very much like open SSL has just gotten too long in the tooth. Yeah, it's just, it's got so much crap in it now and you just no longer need it. So wire guard is a clean rewrite tail scale runs on top of it. It's all free. It does. It does automatic key rotation, natal single sign on with two-factor authentication. These guys have it nailed and shortly you'll just be able to do a draw, you know, a point and click in order to install it on under PF sense. So I wanted to give everyone a heads up about that. And lastly, two little bits of closing the loop.
Leo Laporte & Steve Gibson (01:09:10):
Someone whose Twitter handle or his Twitter name is dangerously close to hijinks. Apparently you can use long names in Twitter. Mm. He said, thanks for all you do. Would you share the software solution you use for grc.sc? Do you recommend it? And then he, before I could reply, he sent me another follow up. He said, thanks to you. And Elaine, I found the reference for URL shortner URLs in, in, in episode 8 58. So yes, URLs, Y O U R L S is.org is short for your own URL link. Shortner Hmm, Y O U R L s.org. And I love it. It's what I use. It is a tiny little PHP library. So you, you could bring it up on any system that has an an Q L server. You know, he, he likes my SQL L five or later PHP, seven point 0.4 or above you need mod rewrite enabled.
Leo Laporte & Steve Gibson (01:10:27):
If you wanna mess around with the API, it runs on pretty much in and know certainly Apache engine X Cherokee. I run it on I on IIS. It does need HTTPS support. Anyway, it's just a, it's a very, it it's, all it is, is what it does. Is it there, there's an admin panel you're able to, to, to drop in a long URL, tell it what you want it, the short one to be, it saves it to the, to, to the sequel database. And then when, when someone comes in with that short URL, it just issues a 3 0 2 redirect to the long one. And, you know, for a while I was using Bitly, but I was using episode numbers to, to, to, as a convenience to people. And of course, naturally somebody began, somebody stole it, oh, grabbing the episode numbers in, in advance of my use of them.
Leo Laporte & Steve Gibson (01:11:23):
There's always one. This is why we can't have nice things. <Laugh> this is why. Yeah. We can't have them. So is it gonna be you can do your custom domain too, right? So it'll be grc.com/actually, since I had SC for shortcut. Yeah. It's grc.sc. Oh, that's nice. Slash whatever. And you can slash whatever. That's great. And no one else can do it. Cause yeah. Good. Cause it's just, mine's yours. Yeah. Yeah. I used Bitly the the other day to create our shared photo library for the cruise. And I was thinking, yeah, why are, why am I not running my own URL shortener? So now you've pointed me in the right direction and TWI twi.sc if it's not already gone. Yeah. Yeah. in fact, Matt, well, we have TWI dot said that. No, no, we own twit. So perfect. Yeah. That's a good one. Yeah. Nice. Nice. Yeah, cuz it wants to be short too. And I just love this little bit of humor from, at B I S w B Matt, he said in regards to episode eight 80, he said, I P V six is the technology of the future. And it always will be <laugh>.
Leo Laporte & Steve Gibson (01:12:40):
That is a great line. Isn't that great. I love that. Wow. <Laugh> that's good. He wins on that one. Something came up. We were talking about that, like the, oh, I know what it was. It was Leo, the price of IP of Ann I P V four IP address. It, oh, I've forgotten now what it was it doubled in a year. I think that's what it was. It's now 25 to 25 to $30 per IP. Because again, they, no one wants IPV. Six they'll pay whatever the going price is for IPV for even if it's seeing crazy, it was like exponential price increase over the past few years. So again, IPV six is a technology of the future now and forever. <Laugh> all right. Before we get to the big story of the of the week, which I'm looking forward to we would like very much to talk about our sponsor and about protecting your E email because maybe RDP is a source of 80% of hacks out there.
Leo Laporte & Steve Gibson (01:13:54):
But I could tell you a hundred percent of fishing attacks come through your email, spear fishing attacks come through, you know, to you from your boss or what looks like your boss or your manager, something you're gonna act on right away. And it's a huge security issue. I think it's gotta be the number one way ransomware that gets into people's networks security. Now today brought to you by Barracuda in a recent email trends survey, 43% of respondents told Barracuda they've been victims of a spearing attack. 43%, only 23% said they have dedicated spear fishing protection. That seems low number. How are you keeping your email secure? Do you have spear fishing protection? I can tell you, we do here. Barracuda is the way to go. They've identified 13 types of email, not just spear fishing and they've, and they've, you know, kind of revealed how cyber criminals use 'em every day.
Leo Laporte & Steve Gibson (01:14:57):
Of course fishing's one, but there's conversation hacking ransomware 10 more tricks, cyber criminals use to steal money from your company or personal information from your employees and customers. Are you protected against all the main 13 types of email threats? That's the question you ought to be asking yourself. Email cyber crime is becoming so much more sophisticated. Attacks are much more difficult to prevent. They use social engineering, praying on your employees using urgency and fear cuz you know, you get those emotions stirred up. People act without thinking social engineering attacks, including spearing and business, email compromise cost businesses, an average of $130,000 an incident. That's just the average could be a lot more as demand for COVID. 19 tests has increased for instance at this happened at the start of the year, Barracuda researchers are an increase in COVID 19 test related fishing attacks.
Leo Laporte & Steve Gibson (01:15:55):
See they're always gonna be on the latest topic. Those went up 521% between October of last year and January of this 521%, these bad guys they're paying attention, they're reading the headlines and they're going, Hmm. How can we take advantage of your employees right now using today's headlines cryptocurrency, right? Lot of traffic going on about that right now, the opportunity for attacks is ripe the price of Bitcoin. When it goes up, when it goes down, that increases the impersonation attacks between October 20, 20 and twenty twenty one, a hundred ninety 2% increase as BI. That was when Bitcoin was climbing, right? In 2020, the internet crime complaint center received 19,369 business email compromised and email account compromised complaints with adjusted losses of over 1.8 billion. Oh my God, it's still important to secure your email at the gateway. I'm not saying you don't, but it's not enough. It's not enough.
Leo Laporte & Steve Gibson (01:17:04):
You, you wanna protect against traditional attacks like viruses and zero day ransomware and other threats. But your gateway is, is useless against targeted attacks like spear fishing protection at the inbox level, including AI and machine learning cuz so they can recognize attacks before it's even widely known you is necessary to detect and stop these most sophisticated threats. And those are the ones you need to be worried about. So protect the perimeter, but also at the inbox. Anyway, this is all stuff you'll learn. When you get a free copy of the Barracuda report, 13 email threat types to know about, get it right now. You'll see how cyber criminals are getting more and more sophisticated every day. How you can build the best protection for your business, your data and your people with Barracuda. Find out about those 13 email threat types you need to know about and how Barracuda can provide complete email protection for your teams, your customers, and your reputation.
Leo Laporte & Steve Gibson (01:17:58):
Get your free ebook, barracuda.com/securitynow that's barracuda.com/securitynow Barracuda your journey secured. Okay, I'm ready for the, I should have titled this podcast, the Demonn cube. Oh so the MV seven 20 is a tiny cube measuring about an inch by an inch by an inch. I've got a picture of it in the show notes at the top of this topic. And if someone were to were to tuck it under your car's hood, without your knowledge plugging into your car's wiring harness, you would be hard pressed to know that anything was outta place. In fact, if your cars authorized service, people were working under the hood. They too would likely pass it off as just some supposed to be there relay she's a little plastic box. It sits in between the connector and the, and the plug. Yep. You know, and this, this like innocuous would be by design since the manufacturer of this sneaky little cellular radio equipped GPS, satellite monitoring, and vehicle control overriding Demonn boasts at the top of its webpage below the title, easy to hide.
Leo Laporte & Steve Gibson (01:19:24):
It says that MV seven 20 looks like a relay, but is actually a locator. So the question is who put it there and why, since this thing only costs now in my notes, I wrote 20 bucks, but later I looked on Amazon and I found it for $26. So it could be anyone who put it there, who has reason legal or otherwise to wanna ma monitor and track a vehicle's location and speed while having the option, get this to remotely, shut down the, the motors flow of oil and gas causing the vehicle to gradually slow down to a point where the engine can be shut off and disabled. <Laugh> wow. All remotely. What? And now wait till you hear how insecure this is. I mean, it's one thing for your light switches and plugs to like have crappy security. This thing probably takes the cake.
Leo Laporte & Steve Gibson (01:20:33):
So it's really, it's not, it's not a tracker. It's a, it's a cutoff valve. It's a, yes. It's a kick. It's a kill switch and a tracker. Yes. Yes. <Laugh> and it's only $26 and yes, a single click on Amazon. Holy cow. So again, the question is who put it there and why these things exist and while I'd be happy, you know, I mean there's a legitimate use. Like sometimes now when you buy a car if you don't make your payments, they've got a kill switch in the car. So they don't have to send the dog after you to, you know, Audi hundred to get you. Yeah. Right. They just kill the car. And then they have the GPS to know where it is. So I imagine that's the market. They thought they were going after anyway. Right. You know, well, unfortunately they, they're getting more than they bargain for.
Leo Laporte & Steve Gibson (01:21:26):
You know, these things exist while I'd be happy to talking about them, if only for the sake of noting their existence as you and I just have been Leo, they wouldn't normally rise to the level of being a headline topic for this podcast. So our long term listeners can probably see where this is headed. What do we know about this thing's manufacturer? Okay. My CODIS, M I C O D U S is a sheen, China based manufacturer and supplier of automotive, electronics and accessories. The company's main products are asset person, personal and vehicle trackers. My CODIS devices are available for purchase via Amazon Ali express, eBay, Alibaba, and other major online retailers. And as I said, I found one on Amazon for $26. If you just put in MV seven 20 into Amazon up, it comes there's. Some other reseller is, is is the one that Amazon lists, but it's the same device it's obvi you know, you can just tell by looking at it and all the features are identical.
Leo Laporte & Steve Gibson (01:22:38):
So in addition to GPS devices, the company provides a cloud based platform via web iOS and Android apps for remote management fleet and asset tracking. As you were suggesting in fleet mode and vehicle specific applications, my Coda states, it provides quote, a secure, open and scalable platform that plays an essential role in the optimization of resource utilization by enabling visibility and simplifying management. And of course, everyone assumes, they said it's secure. Oh, okay. Then we don't have anything to worry about. The security vulnerability research firm bit site took a look at this little devices, security bit site chose the, the myco MV seven 20, because it's the company's least expensive model with fuel cutoff capability. As we'll see in a minute, it's a cellular enabled GPS tracker, which uses a SIM card to transmit status and location updates to supporting servers and to receive SMS commands from its user.
Leo Laporte & Steve Gibson (01:24:01):
And unfortunately also from pretty much anyone else <laugh> as I'm sure no one is gonna be surprised learning by what they found. They found six vulnerabilities of a severity up to two of them, CVSs of 9.8. I, if there were only a couple of these little one inch cubes wandering around the planet somewhere, hopefully mainly in China, that would not represent a clear and present danger, but one and a half million of just these particular models, these little demons are currently present in vehicles located throughout 169 countries later down on the show notes. I have a heat map showing where they are they're present in the vehicles used by several fortune 50 firms in the us also by European governments and by state government agencies in the us. There's a south American military agency that is employing them as well as a nuclear plant operator, given the tracking power.
Leo Laporte & Steve Gibson (01:25:18):
Oh, <laugh> I could possibly go wrong there. <Laugh> and the ability to remotely cut off a vehicle's fuel supply, multiple security vulnerabilities become worrisome. Okay. Now, cause a lot of them in China, that's really where they mostly are, right? Yes they are. They are largely for fortunately yeah. In China. So good. Unfortunately not all of them. Yeah. We know that mistakes happen, right. And that anyone can make a mistake. That's my mantra on the podcast. It's like, it's okay. You know, it's how you deal with the mistakes, how you own up to them and fix them that matters. And this is where things go from worrisome to worse on September 9th of last year, 2021 bit site initiated contact via the only email available on the Myko website, sales myko.com. Myko replied asking for additional information to pass on to the, my Codi sales department bid site requested a security or engineering contact.
Leo Laporte & Steve Gibson (01:26:33):
My CODIS never responded to that request. So they waited until October 1st again, contacted Mike codas using the only email address they had. And again, requesting to speak with a security or engineering contact, this request was refused. Then Mike codas contacted bit site. So you know, I'm sorry. China was made it's it's Russia. It's Russia. It's Russia. That's thank you for the correction. You're right. Yeah. You're right. Mojo said it's that's Russia, baby. It's actually green in China. Yeah. Russians love him. Yeah. He's great. <Laugh> we love them. We put his everywhere cubes he's we put him everywhere. He's great.
Leo Laporte & Steve Gibson (01:27:21):
Kg. We love him in cube. Q <laugh>. So after nine days, bit site did get a call a, a email from Mike CODIS. This was on October 10th and I love this claiming to be working on the issues despite the fact that bit site had not yet shared any technical information with Mike CODIS about what the problems were. So don't worry. Don't know. They don't know we got it. Nobody know we're working on it. Yeah. It's a missing, we're gonna like fix. We're gonna fix the security. Yeah. That you apparently are trying to tell us about. Even though we haven't yet, I knew that we haven't let you do so yet. I knew that I knew that <laugh> what makes you think? I didn't know that I knew that so a month goes by, that was October 10th. Now on October 23rd bedside made another attempt to contact the vendor.
Leo Laporte & Steve Gibson (01:28:21):
My codes did not respond. So now that was November and toward the end of November, let December go by. And most of January mid-January on the 14th bid site shared its research. And you'll see why in a minute, cuz I mean this did is worrisome shared its research and findings with CSA to further its efforts thinking, okay, maybe the us government security agency can get a response from these clowns bit site requested S a engage with the vendor and share the information. No luck on may. First of this year, SISs a again, attempted to contact the vendor to share information S a established, a connection with the vendor and shared the original research and findings. However, SISs a, has not heard from the vendor since it shared the research. So that was on may day. <Laugh> nothing may goes by. June, goes by first half of July goes by nothing on July 19th after reasonably exhausting, all options to reach my cos and given the lack of engagement from the vendor bit site and CS, a collectively determine that these vulnerabilities warrant public disclosure.
Leo Laporte & Steve Gibson (01:29:48):
So SISs a and bit site decided to publish the research. That's what happened on the 19th exposing all one and a half million of these little Demonn boxes, the Demonn cubes to immediate compromise because none of these problems have been fixed. Okay. So what do we, and now the entire rest of the world know about these one and a half million insecure Chinese vehicle tracking devices operating throughout 169 different countries, mostly in Russia. Gee, I wonder if somebody could take advantage of that? Hello Ukraine. Anyway oh bitch. Maybe there's a bright, bright side to all this <laugh> interesting bit site discovered six severe vulnerabilities in the myco, MV seven 20 GPS tracker. This is them writing a popular automotive tracking device designed for, for vehicle fleet management and theft protection for consumers and organizations. The MV seven 20 is a hardwired GPS tracker allowing for external physical control of the device, the device, meaning vehicle.
Leo Laporte & Steve Gibson (01:31:18):
In addition to GPS tracking the MV seven 20 offers, anti theft, fuel cutoff, remote control and geofencing capabilities. <Laugh> you drive too far, your car stops the exploitation of these vulnerability. I wonder if you have to like then push it back within, you know, in inside the geo fence, just a few feet, and then you can, you can then use reverse in order to, to get back inside the wow, the, the working area, the exploitation of these vulnerabilities, they, they wrote could have disastrous and even life threatening implications. For example, an attacker could exploit some of the vulnerabilities to cut fuel to an entire fleet, God of commercial or emergency vehicles. Oh my God. Or the attacker could leverage GPS information to monitor an abruptly stop vehicles on highways. Attackers could choose to surreptitiously track individuals or demand ransom payments to return disabled vehicles to working condition.
Leo Laporte & Steve Gibson (01:32:28):
Yeah, there are many possible scenarios which could result in loss of life, property, damage, privacy, intrusions, and threaten national security. And wait till you hear Leo where a a there's a, a non password protected command that allows the believe it or not allows you to tell the Demonn cube that it's command and control server's IP has changed to something else. So now it won't ever try to actually, even I know that's devious. You could per you could, you could permanently tell it that now you are in control of it. Yes. Oh my gosh. <Laugh> totally totally moly. They wrote bit sites. Research was conducted with a sole purpose just to like put everyone's mind at rest. Unfortunately, now it's all public, right? Because they had no choice. The sole purpose of assessing the security of the MV seven 20 GPS tracker and to determine whether an attacker could access a user's GPS position.
Leo Laporte & Steve Gibson (01:33:33):
Oh boy, can they, although the results surpassed the proposed initial goal, this report does not represent a full security audit. I mean, like they just thought, okay, we've done enough of the myco ecosystem. However they wrote, we believe other models may be vulnerable due to security flaws in the myco architecture myco states, there are a 1.5 million of their GPS tracking devices in use today by individual consumers and organizations, organizations, and individuals using MV seven 20 devices in their vehicles are at risk leveraging. Our proprietary datasets bit site discovered my cos devices used in 169 countries by organizations, including government agencies, military law enforcement, as well as businesses spanning a variety of sectors and industries, including aerospace, energy engineering, manufacturing, shipping, and more given the impact and severity of the vulnerabilities found it is highly recommended that users immediately stop using or disable any myco MV seven 20 GPS trackers until a fix is made available.
Leo Laporte & Steve Gibson (01:34:55):
And once again, children, $26 on Amazon, you can have one of your own. So Eric Tuckman in our chat room has analyzed the wiring diagram. He says that it is a relay. So you have to put it in between your, your power supply and your oil pump or your gas pump. You have to put it somewhere where it would have that cutoff capability. Right. Right, right. So that's what to look for kids. If you just wanted to check, you might, you might want, see if you have a Demonn cube see in your, in your car. Okay. So they said through packet and traffic analysis observed between the website, the Android application, GPS trackers and servers bit site determined that the, my codas architecture is organized as follows all services appear to be hosted by a single server, www.my codas.net, which is at IP address 47,000 2 54, 77, 28.
Leo Laporte & Steve Gibson (01:36:00):
It provides a website via HT DPS, the therefore port 4 43, thus. And so, so that that's the website portal. Also an UN encrypted API server to support the mobile apps via HTTP port 80. That's at app.my codis.net, same IP and a GPS tracker custom protocol server running on port 7,700 that's d.my codis.net. Same IP. Although the website that's used to access my codes, GPS trackers via a browser uses HTTPS the mobile app. As I mentioned, uses unencrypted and plain HTTP GPS trackers communicate with the backend server via a custom protocol on TCP port 7,700. The protocol does not appear to be encrypted. Users can directly control and access the GPS tracker via standard SMS text messages. So you can just text these little Demonn cubes directly. The full command list for model MV seven 20 is, and I have a link of the show notes and Leo, I couldn't put it.
Leo Laporte & Steve Gibson (01:37:33):
I couldn't embed it in the, in the show notes because it needs a full screen in order to see it. But it's a little bracing, what you can do with the commands without any log on or authentication, you can send the tracker, the simple SMS command where, and it will reply with a Google maps link centered on the vehicle's present location. So <laugh>, you know, you just send it a, to an SMS where, and up, and you get back a Google maps link that allows you to view where the vehicle is located. Or also with no password sending a 5 55 turns off the vehicle's fuel and sending a 6 66 resumes. The fuel actually it's too bad. Those weren't reversed. Oh, it be, be, be better if, if 6, 6, 6, wow. Where they would be the shut off bit site, it managed a couple of classic attacks, which are enabled by the vulnerabilities.
Leo Laporte & Steve Gibson (01:38:40):
They discovered there's the man on the middle attack. An attacker performs a man on the middle attack, intercepting and changing requests between the mobile application and supporting servers, taking advantage of the unencrypted HTTPS communications between them. This would give the, the threat actor complete control of the GPS tracker access to location, information routes, geo fences, and tracking and real time, as well as the ability to cut off fuel disarm the vehicle alarms and more, and note that by being a man in the middle, you can change what the GPS tracker reports. So after a, a after obtaining that status, you wait for the vehicle to go somewhere. You report its location somewhere else, and it cannot, it can no longer be found by, by GPS because the man in the middle is in real time changing the GPS tracker's reports back to the mothership.
Leo Laporte & Steve Gibson (01:39:55):
Second attack authentication bypass. And I'll, I'll detail this in a second, but a flawed authentication mechanism in the mobile application could allow an, an attacker to access any device via, via a hard coded key using the key. And by that they mean a password. An attacker could send messages to the GPS tracker as if they were coming via the SMS channel. So you don't even need to use SMS, which should only accept commands from the GPS owners mobile number. Again, this would give an attacker complete control of the device, access to the location information routes, G geo fences and tracking and real time. And the ability to cut off fuel disarm alarms and more, and finally the persistent invisible monitoring attack. It is possible to remotely reprogram the GPS tracker. Oh, here, they're talking about what I, what I, I, what I already mentioned to use a custom IP address as its API server.
Leo Laporte & Steve Gibson (01:41:00):
This would give an attacker the ability to monitor and control all communications to and from the GPS tracker. The attacker could completely control the GPS tracker with all the implications listed above, including the reporting of incorrect locations to the GPS server, the ability to remotely reprogram these devices, to use a persistent custom internet IP as its API server strikes me as one of those. Wouldn't that be cool? Or we can do this. So we should sorts of things that engineers toss in just because they can, without there ever being any possible need or justification for the feature and at a significant and serious cost insecurity. So, you know, it's just so dumb for that feature to be in there. And so prone to exploit. Okay. So what are these six vulnerabilities that bit site found? And that CS a agreed were worthy of a, of CVS designation and in two cases, a CVSs of 9.8.
Leo Laporte & Steve Gibson (01:42:20):
Okay. The first 9.81, get this, the API server uses a single <laugh>. I can hardly even say this Leo, a single master global password <laugh> for all devices. Is it 1, 2, 3, 4, 5, 6. <Laugh> no, it is seven D U two D JF, D R oh 8 3 21. Well, no, one's gonna guess that. Yeah. They're not gonna guess it, but now everyone knows it and it's global. Oh, that's all. And you can't disable it or anything. It's just that's it cannot be disabled. They can't ever change it because there's no provision in there or changing it. They don't do firmware updates. What are you crazy, Uhuh? That would be insecure on the Demonn cube. No, no. We just let the Demonn go off on its own. Yes. this is the password used by the user's mobile apps to query and perform actions and execute all remote commands.
Leo Laporte & Steve Gibson (01:43:25):
This allows an attacker to log into the API web server and notice everyone now knows the IP. Everyone now knows the password, and in a minute, everyone is gonna know the protocol. And then all one and a half million of these things are vulnerable because their device IDs are also knowable. This is just unbelievably badly. Okay. This allows an attacker to log into the API web server, impersonate, any user and directly send SMS commands to their GPS tracker as if they were coming from the GPS owner's mobile number, using the master API password, a remote unauthenticated attacker can gain complete control of any GPS, tracker access, location, information routes, geo fences tracking, tracking locations in real time, cut off fuel to vehicles and or disarm alarms and other features. So it's, it's impossible. I would argue to label this as a mistake or oversight the developers, the people who coded thus this must be well aware that this is not per account API authentication.
Leo Laporte & Steve Gibson (01:44:48):
All authentication is shared globally, and what's worse. It's not even necessary to reverse engineer one of their API endpoint apps or rig up some fancy sort of DNS spoofing and TLS intercepting man in the middle proxy with a fraudulent cert or certificate authority since the app's API endpoint is HTTP unencrypted to port 80, any passive web sniffer <laugh> can be used to capture the applications, interaction with the myco API endpoint server. Wow. So it's not surprising that SISs a gave this a CVSs of 9.8. And as I said, the master password, which is stored in all apps and which works universally. When you, when using the protocol, you could sniff with the, with the, a sniffer on the API. I mean, okay. It occurs to me. This hadn't occurred to me before Leo for $26. Our, every one of our listeners can buy one of these.
Leo Laporte & Steve Gibson (01:46:04):
You will, you can then download the app. You can sniff your internet connection while this thing, phones home, look at the protocol. Oh man. And play. Sure. This is like, this is a perfect tool toolkit for, for anyone who wants to play around with what is hacking like, because you, there, there's never been a more ready, made opportunity to do this. It's just amazing. Yeah. The, the password once again, which all apps use, which works universally for logging into the API endpoint at the IP that, that I gave earlier and port 80 over HTTP, meaning standard, you know in the text query and reply is seven D U two D J F D R a 3 2 1, which is stop saying that out loud. <Laugh> holy moly, vulnerability. Number two, the second major problem. Also a CVSs of 9.8 is broken authentication. These guys write the API.
Leo Laporte & Steve Gibson (01:47:21):
The API server provides a way to directly send SMS commands to the GPS tracking device. As if those commands were coming from the administrator's mobile device. 1, 2, 3, 4, 5, 6 is the default GPS tracker password, which should be changed. However, some commands work even without a password, notably 5 55 to kill the vehicle's fuel. You don't need a password for that. Go figure the web interface and mobile app also require a password when directly contacting the tracker via SMS. However, it shares the same default password issues as the GPS tracker. Even if the user changes the password, the device is not secure. Some SMS like command messages sent directly from the API server, do not need the device password to function. Leaving the device, exposed to hackers. One potential attack can be perpetrated by abusing the admin IP command. This is the feature that I noted earlier that would never, that should never have been included in the API in the first place, which defines the API endpoint of the GPS tracker, meaning where the GPS tracker though, they'll tracking, Demonn connects to, you know, the IP of the server.
Leo Laporte & Steve Gibson (01:48:52):
You can change it. This enables an attacker to achieve a persistent man in the middle position, controlling all traffic between the GPS tracker and the original server and gaining total control over the GPS tracker in their full disclosure, they provide a working proof of concept. I did, I did. I didn't put it in the show notes again. There there's a link in the show notes to their full disclosure. You had brought it up earlier in the video, Leo, where they show screenshots of all of this being done redirecting the API through their own server, to the original server so that they are able to install their own man in the middle vulnerability three. Okay. this one came, this was an an 8.1 only because probably they just got tired of issuing nine point eights. They said, <laugh> we always have the popular default password.
Leo Laporte & Steve Gibson (01:50:02):
1, 2, 3, 4, 5, 6. They said as noted above all devices, ship preconfigured with the Dalt password, 1, 2, 3, what? 4, 5, 6 <laugh>. Yep. As does the mobile interface. Well I I'll just jump to a different place in the show notes because I happen to have, have remembered. They did a test of 1000. They randomly chose 1000 devices. And again, how do you do that? The device IDs are not hard to guess. Can you go to Showan? Is it no. Cause it's board air traffic, so you, right. Yeah. Yeah. They, they, they actually, they, because the API is unencrypted and all you need is the password, which we now know. And and the, the password we, we now know, you can then guess the device ID, they guessed a thousand device IDs. Oh, found them 945 of the thousand had not changed the password. Of course, of course, from 1, 2, 3, 4, 5, 6 course, of course not, by the way, there's a simple command to change the password, but no, of course not ye Uhhuh.
Leo Laporte & Steve Gibson (01:51:26):
So the device ID follows the pattern seven 20, which of course is the model number, right? MV seven 20 is the title, the podcast 7 20 11 followed by six digits. And they said with the value represented by the Xs occurring in sequential order <laugh> so you start at zero, this is sympathetic. It is unbelievable. Everything they could do wrong. They did. Yes. That is that sums it up. <Laugh> I, that, that should be the title of the podcast. Everything they could do wrong, they did. So, you know, a, a big problem is that the need for security, the things that security is securing are more often than not a complete mystery to a device's new user. If someone explained to them what the con con the consequences would be of not changing the password, you know, they would almost certainly happily change it, but 945 out of a thousand users didn't bother.
Leo Laporte & Steve Gibson (01:52:41):
So, anyway, this is just a, the, I, I think, think one of the problems Leo is that we have devices that sell for $26. And so, you know, they're just not expensive enough to take them seriously, right. Yet when you plug them in and they drive off, they're now enumerable by every hacker in the world can now know where the vehicle is that is carrying this Demonn cube. And if you happen to wire it into the fuel supply, it could, it could stop it wherever it, they could stop it wherever they want to. It's just unbelievable.
Leo Laporte & Steve Gibson (01:53:25):
Lot of government agencies are using these. Yep. That's scary chimney. Okay. The takeaway lesson for us here is that, you know, to take this as a valuable case study, we need to recognize that when we're using anything such as this, which connects to a remote internet service of unknown repute, we truly are placing a huge amount of trust into entities whose trust has not been earned and may not be deserved. It's bad enough to have one's light switches and plugs connected back to potentially hostile foreign soil, but giving remote. And in this case, clearly irresponsible entities, real time, knowledge of vehicle, location, and movement. And even over the vehicle's real time, fuel flow seems reckless at best.
Leo Laporte & Steve Gibson (01:54:33):
Yeah. And yet it's inexpensive. So it's done. <Laugh> unbelievable. This does this qualify as an IOT device? I would say it is. Yeah. It's an I it's your car, not your house, but it's yeah, it's out there and it's on the internet. Does it use standard cell networks? How does it yeah, it, it won't do G it won't do the latest 5g or 5g. I think it's actually limited to two G as I recall, cuz I read the specs on it. Well, the good news is there's not a lot of two G networks left. That's probably why it's so big in Russia and Mexico. Yeah. So it's like 900 and 1800. And I, I remember seeing the, the, the various old school cellular frequencies. So the new version, I think they're gonna update it, the new password to be 1, 2, 3, 4, 5, 6, 7.
Leo Laporte & Steve Gibson (01:55:28):
Ah, so just a little tip. Whoa, Leo <laugh>. Nobody will get in. We're gonna address that security flaw right there. It'll just, it'll just go silent. <Laugh> wow. Yeah. So this must be an older device. If it's two G, unless it's for fleets that might have their own two G cell communications or something like that, the us two G's been turned off pretty much everywhere. That's interesting. So yeah. It, there is an, a red X on one of their web pages in their specs, which says not for use in U in the United States. Yeah. So that it may just be that it just doesn't work there. The two, two G network in the us goes down at the end of the year, but most of 'em already been turned off. So, but boy Ukraine. Hello Ukraine. Yeah. It's yeah. You see where it is?
Leo Laporte & Steve Gibson (01:56:15):
Developing nations. Well, you know who use it? Ukraine also use it, but you could really go after Russia with this. Oh, it's a, it's a hot Tama on that map. Wow. Wow. unbelievable. What a story. If you want all the details, there are lots of links in the show notes. And if you're looking to hack one of these everything you need to know is right there. <Laugh> I would, I don't, it's not illegal if you own it. Right. It's your own device hack it. I mean, it would, it's a perfect introduction to hacking. Yeah. Yeah. And you could, it's a re it's a certain kind of relay though. You need the right pin out. Cause I'm thinking maybe you could use it for an irrigation sensor or something. Yeah. Ping, ping your ping, your, your Rainbird or something. I don't know.
Leo Laporte & Steve Gibson (01:57:00):
It just seems like there could be some uses or stick it on your segue. Stick it on yours. Yeah. That's well, that's the good news. None of my electric vehicles have either a gas pump or an oil pump. So I think that's good. I don't know what they'd attach it to. I think we're all. No. Oh, they attach it to the battery. Just that just don't con gone. It's an NC relay. So you have to have an NC device that just means normally closed. Oh. Oh, thank you. Chatroom. Of course always. On top of this, there is a good news. If you go to ally express, there is now an updated 4g compatible ah, device. It's a little more expensive, but it's the same fine company Mike Cotis. Ah, nice. It's the 4g ML 500 G and this one's waterproof. So <laugh> so you can, yeah. You, you can know where your submersible sub went. Yes. yeah. So there you go. And I bet you it's just as insecure, but it'd be worth well, Leo it's all based on the same infrastructure it has to be, has to be just is insecure. Yeah. Cause it's the server that's insecure. Not that device. Yeah. It, it is the protocol and the server. Yeah. Which is not encrypted.
Leo Laporte & Steve Gibson (01:58:15):
This one has a device temperature and voice monitor as well. Just that's great. Think of what you could do. Oh my God. It's a spy box. It supports the latest 4g LTE cat one network on multiple bands for operation globally, a map with a little happy smiling face everywhere, all over the globe, all over the globe. And of course still support for two G in case you wanna, oh, look, this one can be ally attached under the chassis. <Laugh> oh, <laugh>. Oh, so this is in the cutoff. I think this is just just a cheap tracker. My stomach hurts from laughing. Yeah. Oh Lord. Remotely voice monitor. Look. Here's a good here's a good use. They've got a an eight year old girl with her backpack, voice monitoring her. And who's this creep listening in <laugh> geez, Louise. This is not good.
Leo Laporte & Steve Gibson (01:59:09):
There are, this is not good. Oh. Oh, okay. Thank you, Steve. As always this is the show that gives you the screaming Mimi at night, but if you don't listen, just imagine how scary the things you don't know about are right. Every Tuesday we gather together one 30 Pacific, four 30 Eastern, 20, 30 UTC to learn the latest from this guy right here. Steven M. Gibson. I now know Steven M. Gibson. If you wanna get the co the show from him, you can, it's at grc.com. That's his website, the Gibson research corporation. You can leave feedback for Steve there too. Grc.Com/Feedback. Steve has 16 kilobit versions. He's got 64 kilobit full bandwidth audio. He's also got transcriptions, grc.com while you're there. Check out spin, right? The world's best hard drive or mass storage, really any kind of mass storage, even SSDs maintenance and recovery utility.
Leo Laporte & Steve Gibson (02:00:12):
Currently 6.0 soon to be 6.1, we are inching close. And if you get 6.0, now you'll get the free upgrade. So this is a good time to get your copy of spin, right? Everybody, if you've got mass storage, you need spin, right? Lots of other stuff. There, free stuff that Steve does pro bono. We have copies of the show at our website ad supported at twit.tv/sn. Youtube has a channel dedicated to security. Now you can join the club, get the ads out. There's a couple of ways to get the ads out. You can either go to twit.tv/clubtwit, join the club for seven bucks a month and then get all the shows ad free. Plus the discord plus the special twit plus feed, or just get security. Now buy itself for $2 and 99 cents a month. If you're at cheap skate, spend the seven bucks, get it all.
Leo Laporte & Steve Gibson (02:01:04):
Plus the discord, which is a great place to hang. But again, we always have free versions available at the website. If you wanna chat with us while you're watching the show, irc.twi.tv, as well as the discord channel for club members and best way to get it, honestly, subscribe, subscribe to the audio or the video feed each, you know, format has its own feed and you'll get it automatically on a Tuesday evening, right after we chop it up and mince it and put it into fine delicious squares. I guess that's what the editors do. I don't really, I don't understand how that stuff works. Get your favorite podcast client and subscribe to security. Now you're watching any good sci-fi Steve. Actually we just started the dropout. Love that show. Yeah. And if you want more dystopian startup stuff, we crashed on apple TV is all about we work and is fantastic as well.
Leo Laporte & Steve Gibson (02:02:01):
Those two shows together. Oh, good, good, good. You like the dropout? You'll love. We crashed. Fun. Yeah. And we all, we also finished the final season of the expanse, ah, O Ozark. Ozark. Yeah. It's over. Yeah, I know it was. That was, that was great. When I go home tonight, last episode of better call Saul. If you have not watch, did you watch breaking bad? Oh, of course we watched all of better call Saul. Do what was the, you haven't seen at all? He had a heart attack, literally and Bob OER and they stopped and there are four final episodes which have been coming out. I, I thought it was as good. If not better. I agree. I mean, it was, it was at the top of its game, dude. Cool. It had a cliff hanger. Didn't you notice? There was a big cliff hanger, man. I don't wanna say anything. Go back and check your listings. Okay. <Laugh> cool. Oh, it's so good. And I, and everybody's probably already seen the final episode cause it came out, but I haven't yet. So I'm excited. It just came out today, I think. Nice. Nice. Thank you, Steve Arno. We'll see you next week, Mike, right here for that's right for the beginning of August. Yes. Take care. Bye
... (02:03:21):
Security. Now.