Security Now Episode 871 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for security. Now, Steve Gibson is here. Big show playing for you. <Laugh> why the government is saying don't install the Microsoft patches from last Tuesday. <Laugh> a patch Tuesday that didn't go as well as planned. We'll talk about the ransomware gang that wants the citizens of Costa Rica to rebel and a new proposed regulation in the EU. That could mean disaster for privacy. It's all coming up next on security. Now, podcasts you love from people you trust. This is TWiT. This is security. Now with Steve Gibson episode 871 recorded May 17th, 2022. The new EU surveillance state security now is brought to you by Thinks Canary. Detect attackers on your network while avoiding irritating, false alarms. Get the alerts that matter for 10% off and a 60 day money back guarantee. Go to canary.tools/twit and enter the code TWiT in the, how did you hear about this box?
Leo Laporte / Steve Gibson (00:01:11):
And by ExpressVPN. Going online without ExpressVPN is like using your smartphone without a protective case. Most of the time you'll probably be fine, but all it takes is one accident will drop outta the concrete to make you wish it protected yourself. Use our link expressvpn.com/securitynow today, and you'll get an extra three months free on a one year package. And by JumpCloud, your complete platform for identity access and device management works smarter, not harder by securing SSO MDM, MFA and more from one pain of glass fully evaluate jump cloud for free today at cloud.jumpcloud.com/securitynow, and help your organization move to a modern secure hybrid work model. It's time for security. Now to show we cover your security privacy safety online with this guy right here, Steve Gibson of grc.com. Hi Steve. Yo Leo. Great to be careful. The drone is right in front of you.
Leo Laporte / Steve Gibson (00:02:16):
It could wake up at any time and well it's it's tethered right now, so that's good. It can't, it can't escape. Cause it's got a, it's got a tail on it for those who don't know, Leo's been playing with a little inexpensive sort of a selfie cam drone that doesn't really get cut the mustard, but, but as you point out, I mean, given this thing is about, you know, four square inches. It it's pretty impressive what it can do. Yeah. It's basically flying propellers that suspend a camera. Yeah, it has sensors not only a camera, but it has sensors and things. It doesn't, it's gotta have, it's gotta have position sensors. Yeah. Inertial sensors in order to be stabilized and all that. Yeah. Pretty impressible. But anyway <laugh> so we we're at episode 8 71 for mid-May and I titled this one, the new EU surveillance state that was about the fourth title the podcast got.
Leo Laporte / Steve Gibson (00:03:25):
And I kept changing the title as I read more deeply into the details of some proposed legislation in the EU, which first leaked last Tuesday and then was, and it was funny too, cuz the leaked copy actually had the word sensitive on the front page. Yeah. Yes, yes it is. <Laugh> and that was removed from the actual formal official legislation that came out the next day on the 11th. Anyway, we gotta talk about that because it it it's been compared to the, the CSAM apple stuff. No, this is way beyond what apple was proposing. It's just, well, it's, it's it's breathtaking anyway. We'll we'll get there first. We're gonna take a look back at what no one wanted, which was an eventful patch Tuesday, you know, you don't want your patch Tuesdays to be eventful. No. Want them to be uneventful?
Leo Laporte / Steve Gibson (00:04:32):
Yes. We didn't get that. Apple has pushed a set of updates to close an actively exploited zero day across a bunch of their products. We'll we'll touch on that. Google has announced the creation of their open source maintenance crew. That's the, that's the formal name of it? The what is O S M C the open source maintenance crew? A ransomware gang has the tamity to call for the overthrow of a government Google's play store is facing an endlessly daunting task, which will mention, talk about and, and, and look into the predicted disaster for F five S big IP systems, which we expected last week that arrived right on schedule. We've got a piece of a Erata I've got a bunch of closing the loop feedback from our terrific listeners there. We're gonna look at just how far a field that European union has now wandered with their forthcoming breathtaking surveillance legislation.
Leo Laporte / Steve Gibson (00:05:37):
And last week I mentioned cuz it was in the context that we were talking about that I had already queued up this week's picture of the week which talks about supply chain security, which actually we'll be talking about also in the middle of the podcast. So I think another great podcast for our listeners. Yeah. boy, this picture of the week is not funny at all. Not a, not a comic this time. Security now is brought to you by thanks, Canary. Let me talk a little bit, since we are talking about security, about one of the biggest threats to your business, to any business. And of course that's the attacker who is already inside the network, the advanced persistent threat. What do you do? You know, security we've talked about of course many times is it's a layered approach, right?
Leo Laporte / Steve Gibson (00:06:26):
And you certainly I'm sure protecting on the perimeter, you're training your employees to be careful about spearing and, and all of that. But nevertheless, they get in and if they get in and you don't know they're in, you got a problem. That's why I talk a lot about this. The thinks Canary, this little black box, it's not much bigger than a, a USB hard drive is a honey pot and a honey pot. That's easy to configure, easy to use, but will let you know the minute a bad guy starts snooping around on your network. Unfortunately, companies find out too late, they've been compromised. What do hackers do these days? Well, they don't just get in there, trigger ransomware and leave. They get in there. They Snoop around, they download assets that they might use to blackmail you later. That seems to be more and more the Mo they also look for places that you might back up data store data and make sure that they make sure those are also mind.
Leo Laporte / Steve Gibson (00:07:28):
And then sometime later, maybe they'll sit off the ransomware. Maybe they're not, maybe they won't. Maybe they're gonna continue to wander around on average companies. Don't find out they've been breached for 191 days, more than six months, unless you've got a Canary, this thing is awesome. It doesn't look like a security device. It, it doesn't look vulnerable. It just looks valuable. It looks like, well, anything you want it to do a skated device to a server to in this case, mine's an a, a Sonology NAS. And because you know, it's a brand named NAS. It actually has a Mac address. It looks like a legit Sonology NAS. They can't tell it's not the login screen is DSM. It looks exactly like the real thing. Of course, when they log in, they don't get in. They just assume, well, maybe I didn't get that password or they keep trying, but I get an alert that lets me know, somebody thinks that's a NAS cuz you know, it's not it's your Canary Canary will notify you in any way you want and you won't be inundated with false alarms.
Leo Laporte / Steve Gibson (00:08:31):
Just the alerts that matter email text message you'll get a console with all your canaries. You can do it through slack. It supports web hooks, CIS log. Even it has an API. So you can easily, you know, track what's going on with your Canary. You could put it on active directory. So as hackers are browsing around and they look at the directory for file servers or file shares, there it is. Oh, what's on their documents. They'll try to fault passwords against network devices against web services. They'll scan for open services in the network. They will find your Canary. The other thing you could do with Canary is set trip wires throughout your network, with something they call Canary tokens. You can use the Canary to make documents, PDFs, stock, word files, whatever spreadsheets, name 'em provocatively, spread around your network. Same thing. When somebody tries to open that document, it pings the Canary, which then gives you an alert.
Leo Laporte / Steve Gibson (00:09:25):
It is a brilliant conception and I'm not surprised it was created by people who have trained companies, militaries, even governments on how to break into networks. So that expertise help them build the Canary. You'll find them deployed all over the world. Really one of the best tools against data breaches, you need it. You really need it. Visit canary.tools/twit. I'll give you an example of pricing, but it's gonna vary depending on how many canaries you get. Some small businesses, a handful, a big bank, a big, you know, casino back in might get hundreds for 7,500 bucks a year. You'll get five of them. And of course the more you get, the less it costs. You get your own hosted console. As I mentioned, you get all year long, free upgrades, support maintenance. You sit on your Canary. They'll immediately send you to new one. No questions asked.
Leo Laporte / Steve Gibson (00:10:13):
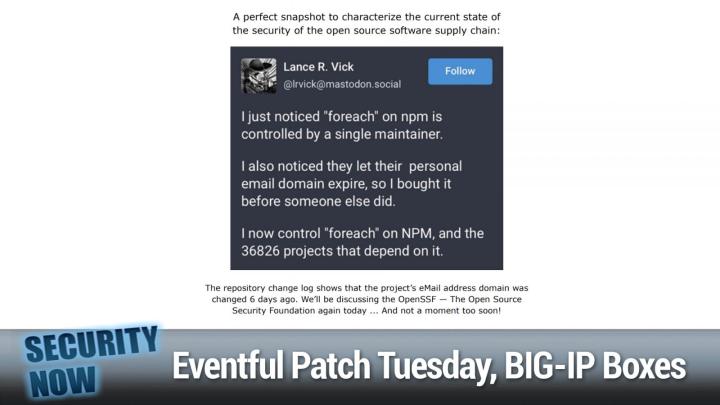
And if you use the offer code twit, T I T, and the, how did you hear about us box 10% off for life, 10% off for life. And by the way, this is a no risk purchase. Cuz if you're not happy, you can always return your canaries with a two month money back guarantee, 60 days for a full refund. I I'm honestly, this is a brilliant way to put honey pots in your network so that if somebody gets in, you will know it. They won't wander around UN impeded, canary.tools/twitt. The offer code of twit. Put that in. How did you hear about his box for 10% off for life canary.tools/twitt. And we thank of so much for supporting Steve and security now. And the work, the good work Steve is doing here picture of the week time. So yeah, this is a perfect snapshot to characterize the current state of the security of the open source software supply chain.
Leo Laporte / Steve Gibson (00:11:11):
This was a legitimate, I actually dug into it and went to the NPM listing for this someone named Lance R Vic. He he, he, he put up a note on mastodon.social. He wrote, I just noticed for each on NPM is controlled by a single maintainer. I also noticed they let their personal email domain expire. So I bought it before someone else did, oh my God. He said, I now control for each on NPM. Oh my God, the God 36,826 projects that depend on it. And when I went over there, sure enough, more than 6 million downloads of this little for each module per week. Wow. So this thing is like deeply dependent. All it does is iterates across an array. Like I, I mean, it's like the dumbest thing. It's like, why would you just not, why would you go get that? But that's the people do Python has it, a lot of languages have it, I guess, for some reason JavaScript doesn't so now you can't.
Leo Laporte / Steve Gibson (00:12:25):
Yeah. So it adds that to it. And because, oh, you wouldn't have to wanna write an iterator you're on your own. Oh goodness, no offend, let let's instead depend on somebody else's who apparently has wandered off and allowed his personal domain to expire. But, but here's the point. So, you know, this is the system that has, that has evolved. And we're gonna be talking about this today, talking about the open source soft security foundation, open source software security foundation, because there's news there. And I'm really glad there's news there because open source software, it's just sort of, you know, started off as being kind of a Curio and it's cert everybody would agree. Now it's become a real force. The problem is it's much less fun to maintain and secure things than it is to just write them. And so, you know, a lot of stuff is written and then like, here you go, I'm gonna go back to my regularly scheduled job.
Leo Laporte / Steve Gibson (00:13:28):
And, and you know, things kind of just get left. So we have to fix this over time. We'll get there in a minute. First of all I've observed in the past that what one looks for in a patch Tuesday is a seamless and uneventful experience. Either you check for updates and then decide to install them. If they're ready for you or you receive a notice that updates have arrived and have already been installed and are just waiting for you to step away from your computer again, uneventful, what you don't want to see is a headline such as bleeping computer ran yesterday, which reads CS a warns not to install may windows updates on domain controllers. Oh boy. In fact, <laugh> CS a so much doesn't want MA's updates installed that they went so far as to temporarily remove the listing of one of their must patch, mandates security flaws from their own catalog of known exploited vulnerabilities because they really can't have it listed there while they're also warning all users of active directory, not to install those updates, to fix the problem, which is in their catalog because it's known to be exploited.
Leo Laporte / Steve Gibson (00:14:59):
It's a mess. The headline on C's published notice reads CS, a temporarily removes CVE 20 22 26, 9 25 from known exploited vulnerabilities catalog <laugh> and they wrote CS a is temporarily removing CV 20 22, 20 6,000 9 25 from its known vulnerability known exploited vulnerability catalog due to a risk of authentication failures. When the May 10th, 2022 Microsoft roll up update is applied to domain controllers. After installing May 10th, 2022, roll up update on domain controllers. Organizations might experience authentication failures on the server or client for services such as network, policy server routing and remote access service radius, extensible authentication protocol, and protected, extensive extensible authentication protocol. Microsoft notified CIS a of this issue, which is related to how the mapping of credentials to machine accounts is being handled by the domain controller. So as we know, once upon a time, it was possible to individually install security patches so that a troublesome patch could be manually avoided no longer.
Leo Laporte / Steve Gibson (00:16:35):
Now everything is rolled up into a take them all or none solution. And I don't blame Microsoft for that. Frankly, my mind was always boggled that Microsoft was even able to somehow consider offering ALA cart patching of such an incredibly complicated code base as windows has become the complexity of, of offering that option to me was just astonishing. And I don't know how they even did it. And as we know it often didn't quite work as hoped. So now it's all or nothing. And in this case of windows, domain controllers for the time being nothing is what you want as enterprise admins last week began installing the may updates problems quickly started surfacing with admins, sharing reports online of some active directory policies, failing with the error message authentication failed due to a user credentials mismatch either. And this, it continues either the username provided, does not map to an existing account or the password was incorrect.
Leo Laporte / Steve Gibson (00:17:52):
So Microsoft explained that the issue is only triggered after installing the updates on servers used as domain controllers. Okay, well that doesn't help those domain controllers, but the updates they made a point of saying will not negatively impact when deployed on client windows, devices and non domain controller windows servers. Now, this is an example of an instance where it's gonna be really interesting to eventually watch and learn whether Microsoft's announced and forthcoming auto patch system turns out to be a good thing or more trouble than it's worth. Presumably auto patch is somehow going to handle unforeseen problems like this, right? I mean, that's the whole point. And at the moment it's unclear where this omniscience is gonna come from since it's apparently not coming from Microsoft. So <laugh>, we're gonna be writing that eventually the problem, all of this is trying to fix.
Leo Laporte / Steve Gibson (00:19:05):
And in this case, you know, of this domain controller patch, it's a flaw that's being actively exploited. As I mentioned before, thus, the reason it was on CI's, you know, Fous shall patch now list actively exploited in the wild. It's a windows LSA. That's the local security authority spoofing zero day, which has been confirmed as a new petite Potta windows, NT land manager, relay attack vector. The petite Potta problem was discovered and named last July by the French security researcher J Lionel. He talked about it at the time, or I'm sorry, we talked about it at the time last July, which is probably why petite Potta sounds familiar. It's just fun to say. And an NTLM relay attack, which is what this specific petite Potta exploit allows. It allows bad guys to force devices in this case, domain controllers to authenticate against malicious servers under their control, essentially joining the malicious server to the domain.
Leo Laporte / Steve Gibson (00:20:24):
Once a device authenticates the malicious server is able to impersonate the device and gain all of its privileges. This in turn gives attackers complete control over the domain. In other words, not good. <Laugh> not what you want. Okay. Now, as for the actual patch itself, we're back to that disheartening story where Microsoft patches to stop the proof of concept from functioning while leaving the underlying problem. Unresolved Jill is, has confirmed to the tech press that may security update the one that you're not supposed to install even leaves the underlying problem unresolved. It, it did finally fix that particular specific problem. A and even that was Microsoft's second attempt. They first tried to fix it last August. He worked around that because they didn't really fix it. And now he's saying it still isn't fixed. They, they closed one specific attack vector in the encrypted file system, which is where this whole thing surrounds this.
Leo Laporte / Steve Gibson (00:21:40):
But he said, attack vector still exist, which will allow a slightly modified attack to continue to work. He said, all functions of petite Potta as other vectors still work, except the EFS open file raw, which was the one thing they fixed. So to me, this feels like there's a bigger problem that is that they've posted workarounds for this and ways of locking things down so that this isn't a problem, you know? So it, it feels like it's kind of big the way the, the, the all of these printer server problems were that we faced at the beginning of last year, where it just took them basically all year to fix this problem, because it was fundamental to some early assumptions that windows had made back when security wasn't such a focus, and they're kind of stuck with the protocol feels to me like they're kind of stuck with, with not, not breaking things, which is what would happen if they really locked this down as it needs to be. So they're just kind of trying not to. So all of this is current as of yesterday, assuming that Microsoft is eventually able to fix and reissue May's security bundle in a way that doesn't break active directory servers, and hopefully they'll test it. <Laugh> first this time to be sure, then they will either announce an out ofAnd update, or maybe they'll just wait till next month till June.
Leo Laporte / Steve Gibson (00:23:18):
Okay. But this is all this all happened last Tuesday, right on patch Tuesday. What else happened? We received fixes for three new zero day vulnerabilities. One of which was that one and patches for a total of 75 flaws in Microsoft, you know, across Microsoft's hall and entire software suite eight of those 75 flaws were rated critical 26, which would've been more than one third of the 75 were remote code execution vulnerabilities. Now closed 21 were elevation or privilege vulnerabilities. 17 were information disclosure, six were denial of service. Four were security feature bypass. And I still love that it's so generic. We have one spoofing vulnerability, nothing was fixed in Chrome this month by Microsoft. And remember that Microsoft classifies a flaw as a zero day different than the rest of the world. If it's been disclosed publicly, even if it's not known to be actively exploited.
Leo Laporte / Steve Gibson (00:24:33):
So somebody talked about two other problems aside from this active, this petite Potm problem. But as far as they know, it hasn't been exploited at the time that they closed it. So, okay, fine. So as we know, given that exploit Wednesday now follows patch Tuesday, the urgency to install updates in a timely matter has increased because we, we just see one example after the other month after month, that the bad guys are jumping on patches, reverse engineering and them, and working to exploit them as quickly as they can. And speaking of zero days yesterday, apple updated watch OS to version 8.6 TV OS to 15.5 and the Mac OS big sir, to 11.6. So that would cover the apple watch series three or later, apple TV 4k first and second gen the apple TV HD and max which are running big, sir, in each of those cases, the updates fixed and out of band's right, which could be made to occur in the apple, a V D module that's akernel extension for handling as AVD sounds, audio and video decoding.
Leo Laporte / Steve Gibson (00:26:00):
It will come as no surprise to our longtime listeners who have all learned to expect trouble to arise in complex media decoders, which are inherently complex interpreters of encoded bit streams. In this case, remote attackers could have, and were known to be executing their arbitrary code with kernel privileges, which is never good. Apple was as closed mouthed as usual about this only saying that they had added improved bounds checking, which yes, you would want to add to an unbounded, right. In one of these modules. So they didn't, you know, they never share very much, they just update and say this is important, everybody, please fix this. Okay. Google's open source maintenance crew. Recall that two weeks ago, we first talked about the open S SF, the tongue twister open source security foundation. At that time, I enumerated the gratifyingly large number of participating in supporting companies, pretty much a who's who, and even some you wouldn't expect.
Leo Laporte / Steve Gibson (00:27:25):
And the occasion two weeks ago was their announcement of that package analysis project, which in just one month, they said, had identified more than 200 malicious packages, which were present in the Python and JavaScript, repositories. And recall that I was a bit wary at, at this point of getting too excited about this particular effort. Although I applaud the whole concept of an open source security foundation as we'll see. But in this case, it appeared that they were mostly just scanning, doing static code scanning for references to previously known malicious domains and IPS. Okay. Which would all be trivial to change once it became clear to the bad guys that this was the way to avoid being picked up by this particular detector. So that's not gonna take long to fix. And like, you know, that that malware we'll be back under a different name using an unknown domain and apparently not go detected anyway, we'll see.
Leo Laporte / Steve Gibson (00:28:35):
But as for the open SSF effort overall I'm very bullish about the prospect of this it's what has been needed for now quite some time. Those of us who are old enough to, to have our hair thinning will remember once upon a time when open source software was sort of a counterculture phenomenon, you know, back in the days when source code was not commonly shared for any purpose. And the idea of doing that was kind of bizarre. You know, I mean, even shareware was still closed source. It was just, you know, please pay me if you find this useful, but it's still mine. And back then the idea of software being free, represented a clear threat to the interests of commercial proprietary software vendors. In fact, in February of 2001, Microsoft's Jim Chen publicly stated that quote open source is an intellectual property destroyer.
Leo Laporte / Steve Gibson (00:29:44):
He said, I can't imagine something that could be worse than this for the software business and the intellectual property business. Well, yeah, I guess that's sort of obviously true. And, and then early the following year in January of 2002, one of Microsoft's chief strategist, Craig Mundy addressing New York university's school of business said that releasing source code into the public domain is unhealthy <laugh> causes security risks. Yeah. You wouldn't want anybody else to look at your code and find all those bugs. And as he said, quote, as history has shown while this type of model may have a place, it isn't successful in building a mass market and making powerful, easy to use software broadly accessible to consumers. Okay, well, now that was then, and no one is holding Microsoft responsible for anything that was said 20 plus years ago. The world today is an entirely different place, but it does remind us just how much things have changed in 20 years.
Leo Laporte / Steve Gibson (00:31:00):
And we know that change is slow. We also know that the open source model has produced tremendous wealth, both intellectual and economic. I saw somewhere, and this was, it was an old stat. So I didn't put, put, add it to the show notes. But years ago it was estimated that 60 billion of wealth had been created and just sort of dumped into the public community by open source software. And as we know, it's become a crucial component of today's software technology landscape, which even Microsoft has now begun to embrace today. It is entirely possible to operate a major enterprise using nothing but open source software, which says a lot, but its problems are also many. The trouble is as I mentioned, but at the top of the show that volunteer effort is much more interested in creating new stuff than in maintaining and securing. It. It's not that maintenance and security focuses are absent, but as we've seen so much maintenance and security focus is needed beyond just getting something to work, that it's a big ask and truly securing software understanding the many ways in which code, which works can still be made, not to work requires an entirely different mindset and a very different type of, of specific education and training.
Leo Laporte / Steve Gibson (00:32:43):
So many major organizations are now benefiting from the work that has been done for them, that having them join a foundation so that they have an organized platform for giving something back, especially when it's about improving the crucial security of the software, they are now all using within their own enterprises and on their network borders. It's the right thing to do. And the open SSF looks like it's, you know, the foundation that's gonna succeed. We're talking about this today because last Thursday, Google made a major announcement about specific new support for this effort. Google wrote today, we joined the open source security foundation, open SSF Linux foundation and industry leaders for a meeting to continue progressing the open source security initiatives discussed during January's white house summit on open source security. During this meeting, Google announced the creation of its new open source maintenance crew.
Leo Laporte / Steve Gibson (00:34:00):
A that is the meeting on Thursday of last week opens. They Google announced the open source maintenance crew. They wrote a dedicated staff of Google engineers who will work closely with upstream maintainers on improving the security of critical open source projects. In addition to this initiative, we contributed ideas and participated in discussions on improving the security and trustworthiness of open source software, which is why our picture of the week was. So apropo amid all this momentum and progress. They wrote. It is important to take stock on how far we've come as a community over the past year and a half. In this post, we will provide an update on some major milestones and projects that have launched and looked towards the future and the work that still needs to be done. And I'm not gonna share all of it, but a little, just a little it's sort of the preamble of that.
Leo Laporte / Steve Gibson (00:35:02):
They wrote a little over a year ago, we published no prevent fix, which laid out a framework for how the software industry could address vulnerabilities in open source software. At the time, there was a growing interest in the topic and the hope was to generate momentum in the cause of advancing and improving software supply chain security and amen to that. So they said the landscape has changed greatly since then a year and a half. They have, they had, they highlighted three points. They said prominent attacks and vulnerabilities in critical open source libraries, such as log for J and co and code Cove made headline news, bringing a new level of awareness to the issue in unifying the industry to address the problem. Second, the us government formalized the push for higher security standards in may of last year, 2021 with the executive order on cyber security, the release of the secure software development framework, a set of guidelines for national security standards on software development sparked an industrywide discussion about how to implement them.
Leo Laporte / Steve Gibson (00:36:24):
And finally, last August technology leaders, including Google, apple, IBM, Microsoft and Amazon invested in improving cyber security and Google alone pledged 10 billion over the next five years to strike them cyber security, including 100 million to support third party foundations like open SSF that manage open source security priorities and help fix vulnerabilities. So I I'm finishing their quote saying in light of these changes, the no prevent fix framework proved prescient beyond just the increased discussion about open source security. We're witnessing real progress in the industry to act on those discussions. In particular, the open SSF has become a community town hall for driving security engineering efforts, discussions and industrywide collaboration. And again, I will say what I said two weeks ago. I will encourage any of our listeners who are so inclined to go over over to open ssf.org and P poke around consider perhaps getting yourself involved.
Leo Laporte / Steve Gibson (00:37:49):
Google's post goes into greater details about their plans for participation, but I wanted to just follow up on our introduction of the open SSF two weeks ago, to note that this is looking like the organization that's going to succeed. Previous efforts were well meaning, but premature and as history shows, visionaries are often too far ahead of the pack. You know, as the saying goes, they they're the ones who get the arrows in their backs. And then, you know, just because they're out in front and they're like, they, they get the problem, but there's just not enough yet. You know, mass behind them. To me, it feels like the open source movement is finally being recognized and is earning the respect it deserves. And it may have taken something like the scare of the log for Jay vulnerability at the beginning of this year to give major organizations a bit of a wake up call to realize just how dependent they had slowly grown on open source solutions through the years, but either way, it appears that it's finally happening now and, you know, Bravo we, we really need some, someone to take a look at the things that have sort of just been created with no oversight and no real focus on security in mind and, and get them strengthened.
Leo Laporte / Steve Gibson (00:39:18):
And Leo, I need to strengthen myself <laugh> with a sip of water, indeed, glad to help this show is brought to you this week by ExpressVPN going online without ExpressVPN. And I always look forward to this because they've, they always come up with interesting analogies. It's like using let's say, using your smartphone without a protective case, do you wear a, do you have a case on your phone, Steve? I do. I do. I do. Most of the time. You're probably gonna be fine, but all it takes is one boom on the concrete and you'll wish you had protected yourself. Why do you need a BPM? Well, every time you connect to an unencrypted network that could be at a cafe, a airport, a hotel, your online data, not secure any hacker in the same network can gain access to all sorts of stuff, not just stuff passing through on the clear, but we've talked about this before.
Leo Laporte / Steve Gibson (00:40:09):
They can even see your computer and using tools widely available for very low cost on the internet. Like though wifi pineapple figure out what wifi access points you access on a regular basis like your home one they can impersonate it, get you to log into them. Now you're talking to your hacker <laugh> instead of the internet and well, you know, I don't think it, I need to go much further. It doesn't take a lot of technical knowledge, just some inexpensive hardware, frankly. A smart 12 year old could do it. Your data is valuable. Your laptop is valuable. Hackers can make a lot of money selling personal information about you on the dark web, and they can also just mess with you. You know? So what do you do with ExpressVPN? Well, first of all, all your traffic is in an encrypted tunnel.
Leo Laporte / Steve Gibson (00:40:58):
And the beauty part is the hacker can't even see your laptop on the network. It completely defeats the wifi pineapple and all those devices. So they can't see anything going in the clear, they can't see your laptop it's as if you don't exist, it would take a hacker with a super computer, or maybe, you know, you get one of these quantum computers someday any day, right? No it would take 'em a long time without a quantum computer, like a billion years to get past the strong encryption express. VPN uses you fire up the app. You press the button, you're protected. They've got apps for iPhone, Android, phone, laptops, tablets, even smart TVs, even routers. So you could be secured not only on the go, but at home as well and ExpressVPN invests in their network. They do it right so that you you're so fast.
Leo Laporte / Steve Gibson (00:41:48):
You can watch HD video. You won't even know you're on a VPN, so there's no disincentive to use it. There's just every reason too. It's the only VPN I use and recommend secure your online data today. Visit expressvpn.com/securitynow E P R E SS, vpn.com/security. Now you'll get an extra three months free with a one year plan brings the cost a less than seven bucks a month. You wanna pay for a VPN. You really do. Otherwise. You are the, the product <laugh> expressvpn.com/securitynow we think of so much for their support of Steve and his efforts to serve and protect. And now back to the show <laugh> so as I've promised, I won't spend lots of our listeners valuable time discussing boring details of endless ransomware attacks. Mm. But when a ransomware gang gets so big for their britches, that they suggest that perhaps a government, which is refusing to pay their ransom should be overthrown by its citizenry.
Leo Laporte / Steve Gibson (00:42:57):
This was so ridiculous. I know <laugh>, I think that rises to a new level of interest. Yes. I referred to this drama for the first time, mostly in passing last week, Russia's Canti, ransomware gang is behind the attacks on several Costa Rican government ministries. Over the weekend. They doubled their ransom demand from 10 million to $20 million. The Costa Rican operations, which have been affected are the finance ministry, the ministry of science, innovation technology, and telecommunications, the labor and social security ministry, the social development and family allowances fund the national meteorological in Institute, the Costa Rican social security fund, and the inter university headquarters in two messages posted to CTI's leak site on Saturday, the gang, which has already leaked 97% of the 670 gigabytes stolen during their attacks claimed the us government was sacrificing Costa Rica. And that the government's the country's government should pay for the decryption keys to unlock their systems and our systems.
Leo Laporte / Steve Gibson (00:44:20):
As I mentioned last week, Costa Rica's new government had just taken office and immediately declared a state of emergency after refusing to pay the initial 10 million ransom demand issued by CTI Costa Rica has received assistance from officials in the us Israel and other countries. And the context for me mentioning all this last week was the state department, us state department's announcement of a 10 million bounty for information about anyone connected to KTI with an additional 5 million payable for information leading to an arrest and conviction. So KTI posted quote, why not just buy a key <laugh> yeah. Why not? Yeah. Why? Yeah. Million dollars. Yeah. Nobody come on, come on. And the, and the persons wrote in the first person saying, I do not know if there have been cases of entering an emergency situation in the country due to a cyber attack. I think they're like, again, getting a little too ahead, like ahead of themselves, is this, is this a ransomware for higher kind of ransomware KTI or like where, you know, it's a service.
Leo Laporte / Steve Gibson (00:45:38):
So this could be just some guy question who's being a jerk or is this the KTI group themselves? I think this is the KTI group themselves. And, and we'll, and, and we'll actually, they, they sort of mentioned henchman. Honestly, they, they mentioned this. So they said in a week we will delete the DEC description keys for Costa Rica and then followed up with a posting. I appeal to every resident of Costa Rica. That's so evil. I know, go to your government, wherever that is and organize rallies so that they would pay us as soon as possible. But apparently you only have a week because the Crip, the cryption keys are gonna deleted, then it's too late. They said, if your current government cannot stabilize the situation, maybe it's worth changing. It. <laugh> like I said, too big for their Brits. Oh my God. In another message. The group called president Joe Biden, a terrorist probably as a result of the state department's new bounty declaration and said it was raising the ransom to 20 million.
Leo Laporte / Steve Gibson (00:46:48):
The group also implied that it would begin calling government officials to demand the ransom. Yeah. Like they they've got a spare 20 million in their pockets. And then finally, the <laugh> the last message I'm quoting. They said just pay before it's too late. Your country was destroyed by two people. We are determined to overthrow the government by means of a cyber attack. We have already shown you all the strength and power. You have introduced an emergency. Wow. <laugh> so depressing this such. Yeah. So it's true. It, yeah, it's true. That Costa Rica is limping along at the moment, the attack crippled the country's customs and taxes platforms alongside several other government agencies, even bringing down one Costa Rican town's energy supplier, the country's treasury department has been unable to operate any of its digital services since the attack, making it nearly impossible for paperwork, signatures, and stamps all required by law to be processed more than three weeks after the attack began, the country is still facing significant struggles, particularly because of the damage done to the finance ministry. Last week, the country told its residents that taxes need to be calculated by hand and paid in person at local banks, as opposed to the digital system the country had previously used. So back to the stone age or pre-internet at least wow. And yes, Leo, as you said you know, they're not gonna get any money from this. The Costa Rica will, you know, get outside assistance and limp themselves back into existence. And yeah, nothing will come of it.
Leo Laporte / Steve Gibson (00:48:56):
Okay. Policing the Google play store. There's a probably intractable problem with the model we currently have. And I can't think of a better one. So I'm not criticizing the model. I'm just elucidating. For freely downloadable mobile device apps created by individuals lacking a reputation after all, everyone starts off with no reputation. Android handsets are available for a fraction of the price of Apple's devices. And Android users typically cite the expansive freedom provided by the Android platform as their primary reason for preferring that much more open mobile environment. But those listening to this podcast realize that with that freedom comes significantly increased danger.
Leo Laporte / Steve Gibson (00:49:58):
I think it's clear that Google is doing the best they can to minimize this danger, but a continuous daily incoming torrential flood of apps is arriving at the Google play store. And there's just no way for Google to deeply research the behavior in each and every one of these apps and to provide the useful and powerful freedom that Android users demand apps must be given powerful enough access to the underlying hosting platform that a malicious app could be quite abusive. So Google is always stuck playing catch up. And in addition to their efforts, thank goodness. They're able to rely upon the motivations and scrutiny that is also being offered by third party security companies yesterday, trend micro posted their piece titled fake mobile apps, steel, Facebook, credentials, and cryptocurrency related keys in their article trend micro explained that malware that's expressly designed and intended to steal the Facebook log on credentials of Android phone users continues to pop up on the play store.
Leo Laporte / Steve Gibson (00:51:25):
Such malware has become so commonplace. In fact that it's now being called face Steeler malware, but it doesn't stay. It doesn't say that on the cover. Of course it's hidden in apps that otherwise look harmless compelling and are of course completely free trend micro recently identified more than 200 face Steeler variance in the Google play store notified Google and Google took them down. But how long will it be before they're replaced by another 200, some of the apps that were just taken down had been installed more than 100,000 times. The apps take the form of tools for editing, manipulating or sharing photos, but they can take many other forms. An example was daily fitness, O L which appears to be a fitness app complete with exercises and video demonstrations. I, I looked at the, at the screenshot of this thing, it's gone now, but it looked like completely convincing, but it was entirely designed to steal the Facebook credentials of anyone who used it.
Leo Laporte / Steve Gibson (00:52:48):
The so-called face Steeler apps were first identified in July of last year and have been to Russian servers by researchers with the mobile security company, predo attackers typically use the compromised Facebook accounts they acquire for various malicious purposes, such as phishing scams, fake posts and ad bots. In the case of daily fitness, ol users are prompted to log in to Facebook through an embedded browser. Okay. What could possibly go wrong with that? Right? Then not surprisingly, a piece of JavaScript is injected into the loaded webpage, which of course steals the log on credentials entered by the user easy peasy trend micro identified, many other face dealer apps with names like enjoy photo editor, Panorama camera, photo gaming, puzzle, swarm photo, and business. Metamanager. In addition to these 200 plus face dealer apps, trend micro noted, they had also found 40 fake cryptocurrency mining apps that are designed to steal their user's cryptocurrency.
Leo Laporte / Steve Gibson (00:54:10):
Not only what it mines, but what was there before last month, Google reported that last year, they had removed more than 1 million malicious apps from the play store. Think about that 1 million malicious apps in 2021 alone, an intractable problem, indeed. And the trouble is there is next to zero general awareness of this problem among the Android using population. There are presently more than 3 billion with a B active Android devices being used worldwide. There's no question that the majority of Google play store apps are legitimate and well meaning, but when a malicious app is only removed after having been downloaded and installed more than 100,000 times, it's also clear that downloading Android apps carries a non-zero risk. And it's not clear that there's anything that can be done again. It's a, it's a, it's a nice open model, but it is under constant relentless attack.
Leo Laporte / Steve Gibson (00:55:26):
<Laugh> speaking of relentless attack, the situation has indeed grown more dire for F five systems, big IP boxes. The day after we talked about this last week, SISs a added that recently disclosed F five big IP flaw to its known V known exploited vulnerabilities catalog. Following reports of its active abuse in the wild. The problem is CVE 20 22, 13 88, bearing a well deserved CVSs of 9.8 due to a critical bug in big IPS eye control, rest endpoint, which provides an unauthenticated attacker with a method to execute arbitrary system commands <laugh>. And I actually saw one that was posted in some of the writeups <laugh> they posted one of the commands that was being issued, excuse me, that was being issued was RM space, hyphen RF, that hyphen R as in recur slash asterisk, which of course will remove all the files on the system, in the file system, starting from the device's route.
Leo Laporte / Steve Gibson (00:56:49):
Wow. Anyway the firm horizon three AI wrote quote, an attacker can use this vulnerability to do just about anything they want to the vulnerable server. This includes making configuration changes, stealing sensitive information and moving laterally within the target network. Although patches and mitigations for the flaw were introduced by F five on May 4th, the Wednesday before last, we know how that tends to go. And in fact, the F five boxes have been subjected to in the wild exploitation ever since F five's announcement was followed by reverse engineering, the fix, and then going to town. Some attackers attempted to install webs, web shells that would grant backdoor access to the targeted systems. And others simply destroyed the device's usability by executing that recursive RM the remove files command across the entire file system from the root outward rapid seven wrote due to the ease of exploiting this vulnerability, the public exploit code, and the fact that it provides root access, exploitation attempts are likely to increase <laugh>, but their security researcher, Ron Bowes added that widespread exploitation is somewhat mitigated by the relatively small number of internet facing F five big IP devices.
Leo Laporte / Steve Gibson (00:58:27):
And yeah, like those that are still surviving on the internet because once wiped they're, they're no longer a big IP device. They're just a machine with no mission. The sand's internet storm center at ISC wrote on Twitter that quote, given that the web server runs as route, this should take care of any vulnerable server out there and destroy any vulnerable, big IP appliance. And indeed that's what's happening pursuant to S's addition of this vulnerability to their catalog. All federal civilian executive branch agencies have been mandated to patch all systems against this issue by May 31st, but that's two weeks from today. And of course by that time there will be left, nothing left standing to patch. I did see Gossi the dog also tweeted that he had used I'm I'm blanking on the service, the, that scanning service. Oh, Showdan he had used Showdan to find the machines they were discoverable using Showdan so, you know, it's just a matter of they're out there. Like yeah, no time before they're they'll all be gone.
Leo Laporte / Steve Gibson (00:59:48):
Okay. I have a piece of a era not often, but important. We do this since it's an interesting and important topic. That's perfect for this podcast. I want to take a moment to talk about classical computing, quantum computing, and symmetric versus asymmetric cryptography back in 1994, an American mathematician by the name of Peter shore, conceived of an algorithm for quantum computers, which would be able to determine the prime factors of in integer that algorithm worked and it bears the name shores algorithm. Wikipedia explains that quote, the efficiency of Shore's algorithm is due to the efficiency of the quantum foyer transform and modular expon by repeated swearings if a they're right, if a quantum computer with a sufficient number of qubits, you know, quantum bits could operate without succumbing to quantum noise and other quantum de coherence phenomena, then Shore's algorithm could be used to break public key cryptography schemes, such as the RSA scheme, the finite field Diffy Hellman key exchange and the elliptic curve Diffy Hellman key exchange.
Leo Laporte / Steve Gibson (01:01:27):
In other words, I was incorrect to state last week that the use of elliptic curve crypto was post quantum safe. It's generically, any asymmetric public key crypto that we're currently using that is not safe. And I know better. So I wanted to correct the record it's symmetric crypto, interestingly enough, that remains safe in a post quantum crypto world. What uses symmetric? Well, everything does we start with asymmetric in order to share the key, then that key, because asymmetric encryption is so slow. We don't actually do the bulk encryption and decryption asymmetrically. We only use the asymmetric encryption for the key then. So that decrypts the key. Then we use symmetric encryption, like rein do AEs to perform the actual bulk, the bulk dection or encryption cause with symmetric, the real issue is the transfer of that key, correct? Yeah. Correct. So you use, you use public key to kind of get the symmetric key across precisely, and then you can continue with the symmetric key precisely.
Leo Laporte / Steve Gibson (01:02:53):
So wi Wiki PD explains RSA based. RSA is based on the assumption that factoring large intes is computationally intractable as far as is known. This assumption is valid for classical non quantum computers. No classical algorithm is known that can factor integers in polynomial time. However, Shore's algorithm shows that factoring integers is efficient on an ideal quantum computer. So it may be feasible to defeat RSA by constructing a large quantum computer. It was also a powerful motivator, right? Wikipedia for the design and construction of quantum computers. Yeah. Let's crack crypto. That would be good. And for the study of new quantum computer algorithms, it has also facilitated research on new crypto systems that are secure from quantum computers, collectively called post quantum cryptography. Okay. Now, Leo, the good news is you're gonna get a kick out of this from a practical standpoint. It still looks like we're well away from the quantum crypto apocalypse, since Wikipedia also reports on the recent progress being made in quantum prime factorization, they write in 2001 Shore's algorithm was demonstrated by a group at IBM. Well, you hear this who <laugh> who?
Leo Laporte / Steve Gibson (01:04:41):
Go ahead, go ahead. What did they factor, Steve? What did they factor? Who factored? Who factored 15, 15, the number 15. Yeah. Into three times five. Wow. That used nuclear magnetic residence implementation of a quantum computer with seven cubits now progress right after IBM's implementation two independent groups implemented shores algorithm using photonic qubits. Ooh. Yeah. EMPH. That's some fancy photonics there. They can get a big number there. Huh? Emphasize. Well, emphasizing that multi cubit entanglement was observed when running the shores algorithm circus, is that good or bad? Who knows? Seems like entanglement would be bad, but okay. This is all. This is all okay. Deep voodoo. I know. Okay. Now, so 11 years later in 2020, in 2012, the factorization of 15 was performed with solid state qubits, so, okay. Oh yeah. Also in 2012, wait for it. The factorization of 21 was achieved. Oh my God.
Leo Laporte / Steve Gibson (01:06:04):
Setting the record. Leo was it seven and three? That's good. Those are both prime. I did that in my head. That's you know, you are faster than a quantum cubit. <Laugh> that set the record for the largest integer factored with Shore's algorithm. What is the largest integer ever factored? Well, now here's the problem. Yeah. Three years ago. Yeah. Now we're up to three years ago, just in 2019. Yeah. Yep. You know, an attempt was made to factor the number 35 35. Wow. Yeah. Sounds like they couldn't do it. Yeah. Unfortunately it was using shores algorithm on an IBM Q system one. I hated Q I told you. Yeah. But the algorithm failed. We were to fact, a minute sures algorithm, 35 doesn't work. And Leo, it's not fair if you give IBM Q system one, a hint on, on the, the prime factorization of 35, 2 prime numbers, that would be cheating.
Leo Laporte / Steve Gibson (01:07:13):
<Laugh> don't don't don't don't don't give it a hint. The algorithm failed because of accumulating errors before we got to the answer. So it's not the algorithm's fault. It's those damn quantum bits you know, their they're little fuzzy on the edges. And so they're not, you know, you want a zero and or you want a one you don't want like something in between there. No. Yeah. So these algorithms are similar to classical brute force checking for factors. So unlike Shore's algorithm, they are not expected to ever perform better than classical factoring algorithms. Okay. So shores, the whole point of shores is down the road using many, many qubits. We're gonna find out how many in a moment, and you will love the number. This is gonna be better than, than just brute force. Well, better than prime factorization, the old school, the old way.
Leo Laporte / Steve Gibson (01:08:08):
Right? So, so quantum computer Newton's method or whatever it is have successfully factored the, for bit value of 15. Now they've done it several times. And Leo, you did it right here in front of us, which was astonishing. I thought that was impressive. Wasn't it? Yeah. Wow. And broke the record by factoring the five bit value of 21 using Shore's algorithm. Well, nice. However, it, they were, you know, they thought, Hey, we're on a roll here. We did four bits. Now. Then we got five bits in an effort three years ago in 2019, couldn't quite make it to six bits. Mm-Hmm <affirmative> to factor 35, which is binary 1 0, 0, 0 1. Is that supposed to help me? Cause I think it's seven and five, but I might, I could be wrong. You, you spoiled it. We had to wait. We had to wait for the answer. Okay. To come, you know?
Leo Laporte / Steve Gibson (01:09:13):
Okay, fine. Now one of our listeners is a crypto aware physicist who wrote after last week's podcast. Good. And he raised a couple of very good points, which I wanna share. We'll get to him in a minute, but I wanna finish up on the asymmetric versus symmetric crypto question elsewhere, Wikipedia in notes that quote in contrast to the threat quantum computing poses to current public key algorithms. And again we're not, we should not be worried. We don't need to change our passwords. Everybody's okay. Most current symmetric CR symmetric cryptographic algorithms and hash functions are considered to be relatively secure against attacks by quantum computers while Grovers algorithm. He, I think he was that green creature. Wasn't he on Sesame street while Grover's algorithm does speed up attacks against symmetric ciphers doubling the key size can effectively block these attacks. Thus Wikipedia concludes post quantum symmetric.
Leo Laporte / Steve Gibson (01:10:26):
Cryptography does not need to differ significantly from current symmetric cryptography. And as we know, we already periodically doubled the links of our symmetric crypto keys and hashes as the speed of traditional computation begins to narrow their practical security margins. So anyway, we can all collectively Leo breathe a sigh of relief. I, I absolutely want to correct the record. It's not that ECC is better. It's it's just as vulnerable. It is. Yes. Basically any asymmetric scheme is just as vulnerable. Is that what you're saying? Well, well there is, for example, LA lattice based crypto, there, there are asymmetric post crypto. Yeah. Cause we, so it's not, we kind of need ASIC. Yes, yes. Yeah. We, we, we, we need it and we're gonna have it. And all the mathematicians are loving the fact that they're, that we're now it, well, not quite the six bits, but that, that lets them dangle the threat in front of the budget committee. Right. in order to get, you know, more funding, cuz maybe we'll get to six and, and maybe to seven bits, the process right now is just expanding the number of bits in the key, right to, to 5 12, 10, 24, 24, 8, and Leo and, and Leo, at some point we will get to a bit number that you will not be able to factor in your head <laugh> and that will be a day to celebrate. I think we've gotten past that point, but okay.
Leo Laporte / Steve Gibson (01:12:08):
What is your physicist friends say? Cause I I'm, I'm very curious. He he's a crypto expert as well as a physicist. So he would have yes, a good handle on all of this. His name is a and his he's he's at Dutch physicist on Twitter. Oh, okay. He said, hi, Steve hope all is well with you. As my weekly routine, I listened to your last podcast episode where you discussed Biden's memorandum on quantum computer threats on classical cryptography, being a physicist by education. He is, he's a PhD. And having practiced PKI related it work, you know, pub public key infrastructure. Yeah. For the past five to six years, I wanted to make a few remarks on your comments and I'll just preface this by say, they're good ones. It is not only, he wrote RSA based on difficulty, a factorization problem, but also ECC based on the discrete log rhythm problem, which is V is vulnerable to Shore's algorithm, but a powerful enough quantum computer, he said recently, Bruce Schneider also referred to an academic article where the authors discussed how much cubit capacity is required to achieve a reasonable attack on the Bitcoin blockchain.
Leo Laporte / Steve Gibson (01:13:33):
Oh, there you go. That's an interesting point. Ah, Leo. Yeah. Yeah. You know, is that seven bits? Is that eight? You need 10. How many is, is that also is blockchain based on prime factorization? It's the same idea? I don't know. That's a good point. Yeah. He says, indeed, the required number of physical qubits is tremendous on the order of 10 to the power of six <laugh>.
Leo Laporte / Steve Gibson (01:14:02):
Okay. So the blockchain also is safe cuz we don't yet have six. Yeah. Let alone 10 to the power of six that's six that's a lot. Okay. Yeah. That would be a million bit qubits. Yeah. And they can't be fuzzy little bits. They gotta be, you know, stable. Sure of them. Well, stability. A big problem with these. I mean, you gotta be sure of your bitterness. On the other hand, we know how fast it went. He says with the traditional Silicon technology, remember Moore's law. Oh, I'm not sure that applies here. Yeah. Feels too. It does. I don't think it does, but, but, but the point here is now he, he really raises some good ones. He says, I find Biden's statement, correct. From some aspects first there is an attack called store. Now decrypt later, of course we've talked about that years ago, but that's why you want perfect forward secrecy.
Leo Laporte / Steve Gibson (01:14:52):
Right. Because he's yes. No, actually that doesn't solve work for that. Oh, okay. Yeah. Okay. He says any stored information today can be broken right by a powerful quantum computer in the future. Therefore, any confidential information that should stay confidential for a long period of time should be protected against quantum computers like sh should today be protected against quantum computers of tomorrow. And again, I mean, that's a good point also, and this is really good. All everyone will get this. He, he wrote achieving crypto agility is very difficult. Most cryptographic algorithms are embedded deep in the protocols and products. There are even cases that Des algorithm is still used in SIM cards and payment cards today. Right. Right. And that's been broken for years. Yeah. Yeah. This makes the lifetime of such algorithms very long. Mm-Hmm <affirmative> he says I E 40 years or more mm-hmm <affirmative> therefore he writes Biden's warning on the federal agencies.
Leo Laporte / Steve Gibson (01:16:05):
And thus the industry is an early call for a very hectic and difficult transition. He said though, I also see some issues with Biden's statement. He wrote two NS competition on post quantum algorithms has not announced the winners yet. And standard finalization is still a few years down the road. From this perspective, he said any organization to attempt to implement a post quantum solution is a premature action. Things may still change. Meaning let's not be too quick to like, like forced N to choose a winner here. Right. And he finally said, I sincerely hope that Biden's administration will not implicitly try to pressure N to finalize the competition by this statement, just a few moments ago, a weakness was found and reported in one of the post quantum digital signature algorithms. He said, rainbow, there should be no political pressure on such standardization activities. And researchers should be left free in making their decision and given enough slash proper time.
Leo Laporte / Steve Gibson (01:17:18):
So we don't really have a quantum safe algorithm yet. No we, we haven't like N does not standardized on right. The way we have like rein do, which is now our, our chosen a our chosen AEs. And, and his point is you don't want pressure on N to, to propose something prematurely you're really, you wanna describe and, and get people using it. The pro the concern is that that, that something will be standardized and there will be a political mandate to start using it because as he noted, there was just a problem found in one of the post quantum digital signature algorithms. Okay. So like, yeah, we don't want that to be in use when the problem is found. And again, it's like, you know, 35, we still can't factor. So just, you know, it's but the he's also right about it taking it's being so difficult to change this stuff.
Leo Laporte / Steve Gibson (01:18:22):
Yeah. Yeah. So he's he finished saying needless to say, I definitely share your opinion that there are way are way more fundamental issues to be addressed urgently, which was the point I was making when I was kind of poking fun at this last week. He said, however, I believe the quantum computer threats on cryptography is very serious and should be given enough attention due, due to slow adaptation or adoption of new cryptographic algorithms in billions of computers. Right. Protocols, et cetera. And you can't rush it either. We agree. Exactly. Yeah. So we're just gonna keep looking for a post quantum technology, and then I'm not too worried about my SSH keys being cracked by a quantum computer, anytime in the next, in my lifetime. Probably it's got a ways to go. Yeah. Yeah. But important point, the fact that I switched to elliptical keys, isn't really germane.
Leo Laporte / Steve Gibson (01:19:22):
Yeah, yeah, yeah. Actually the El the elliptical keys are nice, mostly because they're so much shorter. They're, they're small much shorter. Yeah. It's much shorter. Yeah. I used to have to paste a paragraph in right now. It's one line, so that's right. I mean, that's a silly reason line and that 5 21 bits is, is better than the 20, 48 bits I had in RSA. I, I presume right. Or as good as. Okay. All right. Yeah. also I've I got just for the record, I got a bunch of tweets from people saying Steve, better look at ECC again and see if you still think it's yeah. Quantum safe. But the thing I was worried about is somebody's, somebody's saying, oh, you're so wrong. Quantum computing is just around the corner. Yeah. I don't see that yet, but, you know, I, but, and, and again, I think we, I think we've, we've, we've framed it exactly, right?
Leo Laporte / Steve Gibson (01:20:12):
Yes. We need to be thinking about it. Yes, it is advancing. Yes, it is advancing slowly, but yes, it does take a long time to take existing crypto out of circulation. Yeah. And, you know, so, so I would say as soon as we absolutely know that we have a Bulletproof qu post quantum crypto, that is not where, where problems are not gonna be found in it and see, and that's the other problem is we, we were, when, when we went through the Rhind do competition or, or, or the AEs competition, which ended up choosing Rhind doll, there was a whole bunch of ciphers and they were li and they were able to say, well, we used a F network here, and we ran that through a triple scrambler and the blah, blah, blah. I mean, like the, the, our understanding of how to do symmetric crypto, which is what AEs and, and Rhind all are, it's so mature that we are, that we were like taking building blocks and mixing and matching them and understanding in detail how they worked. We're in a whole new environment now with post crypto, crypto post quantum crypto. And we're, we're at risk of making a mistake. And we, that that's almost worse than, than prematurely obsoleting something that isn't broken today. Right. So, yeah. Yeah.
Leo Laporte / Steve Gibson (01:21:46):
I got a nice note from someone whose name I thought to, I thought I ought to redact, even though he didn't say I should. He said insecurity. Now you've reported on a number of cybersecurity initiatives that the federal government has introduced this past year, including CI's known exploitive vulnerabilities, catalog, Congress' strengthening American cybersecurity act and the white house's executive order on cybersecurity. What I haven't heard you mention are the TSAs two as two security directive pipeline memorandums. These are two successive directives issued in response to the colonial pipeline compromise. Mm. That impose, yeah. That impose explicit cybersecurity requirements upon the main, the midstream oil and gas pipeline industry. And he said, one of the lesser known regulatory mandates of the TSA, he says, yes, that TSA is the safety of interstate pipelines. He says, I work in the midstream pipeline industry. And these TSA directives have been the ban of my existence for the better part of a year I'll reserve specific criticism, but will offer a recent political article, which summarizes the situation nicely.
Leo Laporte / Steve Gibson (01:23:13):
Unfortunately, I'm not able to go into many particulars because the government in its infinite wisdom has marked the entire second directive, SD zero two as sensitive security information, which prevents me from publicly divulging details suffice to say that, yes, the government has instituted a cybersecurity standard that a segment of critical infrastructure must adhere to, but that can't be discussed except behind closed doors. See, that seems like a bad idea. I could not agree more. I, yep. I understand the notion of security through OBS security, but honestly, anything that you're doing for security should be test needs oversight. Yes. Other experts have to look over. I think he said one tidbit that I'm compelled to share is the role that ceases known exploited vulnerabilities catalog plays SD zero two requires that pipeline operators, patch, vulnerabilities published in the catalog within certain timeframes. Since you've mentioned the catalog in several security.
Leo Laporte / Steve Gibson (01:24:27):
Now, episodes, I wanted to call out the fact that this applies not just to government entities, but also to private pipeline companies. And yes, we are forced to review the list daily for new additions. And he finished, thank you for all you do. And especially for a wonderful, informative weekly podcast. And I will say back to him, thank you. You've just contributed to making it more informative. Nice. So Liam Lynch tweeted from at L two actual, which I thought was a cool handle. He's at high Steve. I only listened to episode 8 69 the other day, and heard you and Leo again, refer to the GDPR as being the cause of cookie notices. I kept meaning to contact you about this as the only thing the GDPR did for cookie notices was to strengthen the consent requirement. On the other hand, I would or argue that is what created the notices.
Leo Laporte / Steve Gibson (01:25:29):
He said, cookie notices have been around for a lot longer than the GDPR has been enforced as they came from the EPRI directive. Yeah. And, but we ignored it until DPR <laugh>. Exactly. And then he cited a thread. So I, I, I wanted to, you know, for the record, put that out there, but again, it was the GDPR that gave it teeth and then forced it to be such an annoyance. Yeah. For all of us. Yeah. It's it is the, kind of the canonical example of over regulation or, or privacy regulation gone wrong. I think boy. Yeah. Yeah. And I wanted to officially note that the work on spin rights backend has officially finished spin rights. <Laugh> new spin rights, new hardware drivers are working without any exception. Wow. That the group's extensive testing has revealed in the case of two very old systems.
Leo Laporte / Steve Gibson (01:26:30):
They were like back when, you know, you could like set the, the DMA speed in the bios. You remember like you could set it to 0 1, 2 or three or something. They, they were also the first via implementation chip set in two varied systems. It was necessary to turn off the ultra DMA setting in the bios to obtain reliable transfers, spin right. The tech that they weren't reliable and, and refused to operate otherwise. But when that was done, everything worked perfectly throughout this work, spin rights knew and much improved benchmarking was used to exercise that backend those backend drivers through the IO abstraction that I've talked about before. What so what that does is effectively isolate any backend devices from the front end code when spin right. Seven adds native hardware, USB drivers, and then N Vme drivers, nothing else about spin right's front end needs to change because the IO abstraction provides a uniform interface to the front end code.
Leo Laporte / Steve Gibson (01:27:44):
The benchmark was the first client of that IO abstraction, the actual spin right machine with its multiple switch switchable screens, the grid display the Dynas stat data recovery, the detail technical log, and all the rest will be the second and final client. So that's where I now turn my focus. What we've just slogged and fought through has been by far the longest and toughest part since it was where all of the hardware and machine dependency was now, that's all behind us. Since the bios was historically spin rights, IO abstraction, which has now gone. I now have a lot of rewriting to do, to support spin right's new abstraction, but it's not the sort of thing that will need constant interaction and iteration and tireless testing at the way the previous work on the back end did, I'm sure that the spin right testing gang will end up finding things I've missed and will have ideas for improvements.
Leo Laporte / Steve Gibson (01:28:52):
When, when they begin to see something that is actually operating, which is what will happen next, but at this stage they're mostly gonna be waiting for me rather than me waiting to learn from them how the latest test release turned out. So we are getting close, getting very close. Very exciting. Yay. Can't wait. All right. We're gonna talk about the new EU surveillance state boy. I, you know, for a long time, I thought you know, on balance, GDPR is good. You know, at least it's some protection and et cetera, et cetera, but I'm increasingly dissatisfied with what the EU is doing. And I don't think it's the way forward, but we'll find out, wait until you hear this new one. Oh, oh yeah. Our show today brought to you by a company you need to know about if cybersecurity is an issue for your smaller medium business jump cloud, many companies are spending a large portion of their it budget each year to buy more complicated cybersecurity tools, to hire expensive, hard to find staff that can integrate and run these tools, but it doesn't have to be that way.
Leo Laporte / Steve Gibson (01:30:06):
Good security doesn't have to be more complicated security, finding the right solution to solve your specific needs without overburdening your overworked. It and security staff can really make a difference and jump cloud is here to help. That's why jump cloud is recognized by G2 as a leader in five different categories, including a top five security vendor read the thousand plus positive reviews on G2 for more than 150,000 organizations use jump cloud today, it's really a smart choice for a few reasons. One, you wanna build a strong cybersecurity foundation by doing the basic things, right? I mean, you can't, you know, build on a house of cards, reduce 98% of the issues that lead to cyber incidents by just a few simple things. And, and these are foundational, including using multifactor authentication. You hear us talk about it all the time, applying least privilege access kind of like zero trust patching your systems.
Leo Laporte / Steve Gibson (01:31:09):
How often does Steve talk about that? Except for that most recent Microsoft patch, don't do that. <Laugh>. That's why it's hard. Patching's hard. I understand protecting your data using Annie malware. That's just a handful of things that can really take care of almost all the situations and jump cloud. Lets you do all of that from a single platform with a single pane of glass, which means you're reducing it sprawl cuz all that complexity, all those other tools that you might be blaring on really just adds to your cyber risk. It can lead to brittle systems security. Misconfigurations there's always alert, fatigue on the part of your staff. Challenges having to do with piecemealing together, a number of solutions from different vendors. Jump cloud reduces that administrative overhead reduces complexity. You can do more with the resources you have and, and you really have a clearer view of what's going on.
Leo Laporte / Steve Gibson (01:32:07):
All of that because jump cloud does so much. Of course, zero trust is really important these days because you've got remote workers, you've got a hybrid workforce. People can be working anywhere. You need to give them access to their most important resources, but you also have to make sure that you're not giving bad guys the same access granting secure access without jump cloud could be a painful multiyear process, cobbling together, a number of identity and SSO and, and other providers and capabilities to implement jump cloud. Does it all in one place, it makes it seamless for you to provision and grant access. Just to that, those resources that individual employee needs all from a single integrated platform. Zero trust makes a big difference. And now everybody, you know, is working here, working at home, going back and forth. People are coming back to the offices, but we're also seeing a lot of hybrid work jump cloud really is designed for that environment.
Leo Laporte / Steve Gibson (01:33:07):
Makes it very easy for administrators to securely manage users, devices, and access, and they don't have to be on-prem. They could be wherever it is that they're working. I want you to fully evaluate JumpCloud absolutely free right now, cloud.jumpcloud.com/securitynow help your organization move to a more modern, secure hybrid work model with a single, a single tool that does it all. Cloud.Jumpcloud.Com/Securitynow you owe it to yourself to check it out. Find out why so many businesses, 150,000 businesses are using JumpCloud today. Cloud.Jumpcloud.Com/Securitynow we thank them so much for their support of security. Now you support us when you go to that dress. I know it's a little complicated, get it right. Cloud dot jump cloud.com/security. Now you can also go to our sponsor page and, and click it there. And we'll put a link on the show notes too. All right, Steve, I'm very curious.
Leo Laporte / Steve Gibson (01:34:06):
We've been a first reporting on this story for the last week. We talked about a Sunday on twit on twig on Wednesday, but I'd like to get your take on the new EU rules here. So the title of today's podcast, the new EU surveillance state might seem hyperbolic, but just wait till you hear what the EU is proposing. The European unions propose new legislation will not only require scanning encrypted communications for child sexual abuse, material content, but believe it or not actually reading all text messages with a goal of detecting any textual content that might be regarded as grooming a minor. Ugh, that's such those two. Haven't a nebulous term. Oh, Leo it's impossibly nebulous. Yeah. Okay. So those who haven't read far into the legislation quickly and correctly recognize that accomplishing any of this is inherently necessarily and unavoidably violating it, it requires some agency or entity to scrutinize all communications capable of conveying any graphical or textual material.
Leo Laporte / Steve Gibson (01:35:25):
In other words, all of the social messaging platform used by European union citizens and such scrutiny necessarily contravenes the well-established goals, intense and capabilities of end to end encryption. So yeah, this would be the end of true meaningful privacy enabled and facilitated by end to end encryption. But <affirmative> but reading some of the proposed legislation as I did one discovers that it also requires that this surveillance goes beyond the matching of previously known content hashes to also include content that has not been previously seen. So this would require either humans to view everything that everyone sends to anyone or to train up machine vision and learning models, to automate the identification of previously unknown child sexual abuse material. Okay. Listen, listen to what John Hopkins cryptographer Matthew Green tweeted upon hearing of this last week, Matthew tweeted this document is the most terrifying thing I've ever seen.
Leo Laporte / Steve Gibson (01:36:49):
It is proposing a new mass. I mean this Delio, as I'm saying this, it sounds like fiction. It sounds like I'm making this up. This is the actual legislation. He says, it's proposing a new mass surveillance system that will read private text messages, not to detect CSAM, but to detect grooming. That's the ridiculous part. CSAM. You could pretty much know that CSAM, but if I ask you Steve, what's your age, sex and location, am I grooming you? Right? Or what are your pronouns? Yeah, it's very contextually dependent. And I think it's a judgment call. So it actually says, it actually says in the, by the way that eliminates E Dowe encryption entirely, cuz they say don't encryptions. No excuse. No. In fact they say we still want the best encryption possible. Okay. But we also want this. So, so, so here's what Matthew highlighted from the legislation.
Leo Laporte / Steve Gibson (01:37:54):
This is, this is the legislation as mentioned, detecting grooming would have a positive impact on the fundamental rights of potential victims, especially by contributing to the prevention of abuse. If swish swift action is taken, it may even prevent a child from suffering harm. At the same time, the detection process is generally speaking. The most intrusive one for users Perens compared to the detection of the dissemination of known and new child, sexual abuse material closed pers since it requires automatically scanning through texts in interpersonal communications, it is be so the point is the legislators know this. They and they continue. It is important to bear in mind. This re it is important to bear in mind in this regard that such scanning is often the only possible way to detect it. And that the technology used does not understand the content of the communications, but rather looks for known pre-identified patterns that indicate potential grooming detection technologies have also already acquired a high degree of accuracy and they cite something.
Leo Laporte / Steve Gibson (01:39:34):
Although it's footnote 32, although human oversight and review remain necessary and indicators of grooming are becoming ever more reliable with time. As the algorithms learn, give me a frigging break. It's pretty horrible. Oh, Leo, Matthew then issued a series of tweets in a thread which I'll read. He said, let me be clear. What this means to detect grooming is not simply searching for known CSAM. It isn't using AI to detect new CSAM, which is also on the table. It's running algorithms, reading your actual text messages to figure out what you are saying at scale. It is potentially do going to do this on encrypted messages. That should be private. It won't be good and it won't be smart and it will make mistakes. But what's terrifying is that once you open up machines, reading your text messages for any purpose, there are no limits. Here is the document.
Leo Laporte / Steve Gibson (01:40:55):
It is long but worth reading because it describes the most sophisticated mass surveillance machinery ever deployed outside of China and the USSR, not an exaggeration. The link Matthew shared last week was from a leak of the official legislation, which then appeared the next day. The, they are the same. I looked at them both 135 page document. The title is proposal for a regulation of the U of the European parliament and of the council laying down rules to prevent and combat child sexual abuse. As I said, the legislation is 135 pages, but it's first two paragraphs set the stage and they're worth sharing. So here's the first two paragraphs, the United nations convention on the rights of the child, UN CRC, an article 42, paragraph two of the ch of the charter of fundamental rights of the European union enshrine as rights, the protection and care of children's best interests and wellbeing in 2021, the United nations committee on the rights of the child underlined that these rights must be equally protected in the digital environment. The protection of children, both offline and online is a union priority.
Leo Laporte / Steve Gibson (01:42:36):
At least one in five children falls victim to sexual violence. During childhood a 2021 global study found that more than one in three respondents had been asked to do something sexually explicit online during their childhood and over half had experienced a form of child sexual abuse, online children with disabilities face an even higher risk of experiencing sexual violence up to 68% of girls. And 30% of boys with intellectual or developmental disabilities will be sexually abused before their 18th birthday child sexual abuse material is a product of the ch of the physical abuse, the physical sexual abuse of children, its detection and reporting is necessary to prevent its production and dissemination and a vital means to identify and assist its victims. The pandemic has exposed children to a significantly higher degree of unwanted approaches online, including solicitation into child sexual abuse. Despite the fact that the sexual abuse and sexual exploitation of children and child sexual abuse materials are criminalized across the EU by this child, sexual abuse directive six adopted in 2011. It is clear that the EU is currently still failing to protect children from falling victim to child sexual abuse and that the online dimension represents a particular challenge.
Leo Laporte / Steve Gibson (01:44:27):
Well, okay. One of the, one of the most difficult lessons, an ethical person learns and must come to terms with, as they grow is that not all problems have workable solutions and it doesn't matter at all, how big the problem is nor how much we want there to be a good solution. The entire problem here can be broken down into two separate issues. First, in order to some, in order for some overviewing agency to obtain the raw data, to be scrutinized, there can be no true and meaningful privacy between digitally communicating endpoints or individuals that must end period. Everything needs to be visible and visited. And it's not sufficient to only surveil the devices used by miners because the original intent of detecting child sexual abuse material was to discover and apprehend those non miners who were actively trading in such illegal content. Thus curtailing the demand for the creation of more material.
Leo Laporte / Steve Gibson (01:45:44):
This means that all of everyone's social media messaging content must pass through surveillance filters, which brings us to the second issue. What to do with that content. Once it's obtained, Matthew put it bluntly in one of his tweets, he said, quote, it is going to do this on encrypted messages. That should be private. It won't be good. It won't be smart. And it will make mistakes. Even if we agreed to voluntarily relinquish all of our privacy rights, it's not at all clear that the world has the technology to do what the EU governing legislators want. It's easy for them to write a law stating what they want, but wanting doesn't will it into existence, no matter how fervently and sincerely they want it. So the technology is gonna miss things that it should catch and flag things that it should not. Humans will be required to examine the previously private photos that some image classifier believes to be salacious and previously private text messages shared by consenting adults will be open to others scrutiny.
Leo Laporte / Steve Gibson (01:47:05):
And then there's the devil's advocate side, which is also absolutely true and well established cryptography has already escaped the algorithms, which are able to BR unbreakably and cipher plain text are already public. So if the use of truly unbreakable end to end encryption is outlawed, then only the Outlaws will be using it. And yes, that too could be prevented. The next step in this escalation to doom would be for the communications carriers to refuse to transit any encrypted communications. They cannot themselves decrypt that's possible. In which case we might as well just turn back the clock to the 1970s and give up because the internet would no longer be useful for commerce. Matthew also noted the other elephant in the room by tweeting, but what's terrifying is that once you open up machines, reading your text messages for any purpose, there are no limits that distasteful issue of child sexual abuse is certainly real, but it has also been observed that it serves as a convenient stalking horse for governments, much broader interests in monitoring and controlling speech of many other kinds, much of such speech could be criminal, but much that might be of interest to sensors would not be the EU governors are wrong to want this legislation, which can only be characterized as dangerous, wholly impractical, and impossible to implement as they hope.
Leo Laporte / Steve Gibson (01:48:59):
So, all we can do is pray that it dies. And that's a possibility it's not it's not law now, correct. It's just a proposal. Correct. And you know, the good news is it's now being aired. Everybody is talking about it. You know, the EF F just <laugh>. I mean, they just melted down as you can imagine over this. And boy, I mean, you know, as, as we've said, when we were crossing into this next decade encryption, is this massive challenge. It, I mean, it just is the governments do not like the idea that they have no means for seeing what their citizenry is saying. And I mean, at both sides have valid, you know, valid positions. It's a tough one, learn how to write your own encryption kids <laugh> and you might wanna invest in your own telecommunications network while you're at it.
Leo Laporte / Steve Gibson (01:50:10):
Well, and, and would, you know, would somebody who wanted to abide by the law feel okay about doing it? I, I couldn't do that. Yeah. I mean, first of all, I'm just texting Lori would, I'm gonna be home for dinner. Right. So it's not like I'm, I'm caring about that that much. Yeah. Yeah. There's nothing I'm doing, but, but you know, we've been given this and now it's looking like the EU wants to take it away. I mean, lit Leo, literally you have to, in order to do this grooming detection, everything, someone types on their keyboard of their computer and their mobile device, it has to go through some sensors, screening filter. Yeah. Or the system isn't providing yeah. What the law requires.
Leo Laporte / Steve Gibson (01:51:01):
And we and we know that users don't want them on their own phones. Apple tried that and everyone went, you know, pinched their nose and said, Ew, I don't want, you know, any form of, of kitty porn on my phone, you know, in order to, you know, in order to keep apple from being involved. So that says you have to have a third party somewhere in a cloud that all this runs through. Yeah. So you have to have a man in the middle, a sanctioned, a man in the middle, able to decrypt this in order. Unbelievable for, you know, what a horrible there's no idea.
Leo Laporte / Steve Gibson (01:51:36):
All right. My friend, we we've we've wound people up enough. I think it's time to stop. <Laugh> that is Steve Gibson right there, man. That's the guy, if you like this show, go to his website, grc.com. Pick up a copy of spin, right? The world's best mass storage. I almost said surveillance, master storage. Oh, maintenance. It's not now no surveillance and recovery utility available@grc.com pick up 6.0, you'll get 6.1 free if you buy it today. And you get to participate in the development. We're just as obviously just around the corner. While you're there, you can also get this show. He has two unique versions of the show at his website, a 16 kilobit audio file for the bandwidth impaired and really nicely done transcripts, which you can read along as you listen or use to search for parts of any of the 871 shows.
Leo Laporte / Steve Gibson (01:52:35):
That's all@grc.com. You can leave him feedback at grc.com/feedback or slide into his DMS on Twitter. He's at SG, G R C. We also have copies of the show at our website, 64 kilobit audio. We have video trick.tv/sn. This is a YouTube channel, also devoted to security. Now, if you wanna share clips with friends, that's probably the easiest way to do it. You can also subscribe with your favorite podcast client, get it automatically. The minute it's available, we do the show Tuesdays one 30 Pacific, four 30 Eastern, 20, 30 UTC. You can watch us do it live. We stream live you know, behind the scenes right now, right now what's happening, right? We're doing it as we speak unless you're watching later. And then this case it's not live. You can watch that@livedottwi.tv. In those hours, if you're watching live chat, live@ircdot.tv club, TWiT members get their own special discord server.
Leo Laporte / Steve Gibson (01:53:32):
They also get access to the show without any ads. And they get a special feed, which will include some of the upcoming events in our club, twit discord. We've got some good stuff just around the corner this week, a rare chance to see behind the scenes with our VP operations. Jerry Wagley is gonna be on the microphone with the mic Sergeant Thursday for an inside TWiT the book club with Stacy's coming up, Neil Stevenson's termination shock. That's in a couple of weeks, Alex Lindsay in July is gonna do and ask me anything. There's lots of special events going on in that discord. Just one of many benefits you get by being a member of club twit seven bucks a month. It's nothing go to twit TV slash club TWiT, and have a couple less lattes. And you're good. I'm not suggesting that to you, Steve though, I know you need your triple actually that'd be one less latte. Believe or not. That stuff is so expensive. Now I know it's outrageous. Thank you. Yes. One inflation has not yet hit club Twitter. That's the good news. We'll see you next week on security now byebye. Thanks buddy.
Rod Pyle (01:54:41):
Hey, I'm rod Pyle, editor of ad Astra magazine, and each week I'm joined by Tark. Mallek the editor-in-chief over@space.com in our new this week in space podcast, every Friday Tark. And I take a deep dive into the stories that define the new space age what's NASA up to when will Americans, once again set foot on the moon. And how about those samples from the perseverance Rover? When are those coming home? What the heck has Elon must done now, in addition to all the latest and greatest and space exploration will take an occasional look at bits of space flight history that you've probably never heard of and all with an eye towards having a good time along the way. Check us out on your favorite podcaster
... (01:55:18):
Security.
... (01:55:19):
Now.