Security Now 924, Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for security Now. Steve Gibson is here coming up. What happened when HP attempted to update its office Pro 90 20 E printers? It wasn't good. I'll give you a hint. We'll also talk about a flaw and key pass that you probably don't need to worry about. A bug in spin, right? Six that's been there for years. We'll talk about why it's also probably not something to worry about. And then the rise of voice cloning as a service should you be worried. It's all coming up. Next on Security Now. Podcasts you love
Speaker 2 (00:00:34):
From people you trust.
Leo Laporte (00:00:36):
This is TWiT
(00:00:42):
This is security now with Steve Gibson. Episode 924 Recorded Tuesday, May 23rd. 2023 VCAAS – VOICE CLONING AS A SERVICE. This episode of Security Now is brought to you by Express vpn. Be smart. Stop paying full price for streaming services and only getting access to a fraction of their content. Get your money's worth@expressvpnn.com slash security now for three extra months free with a one year package and buy Ag one. Buy Athletic Greens. If you're looking for a simpler and cost effective supplement routine. Ag one is giving you a free one year supply of vitamin D and five free travel packs with your first purchase of a subscription. Go to athletic greens.com/security now and buy Lookout, whether on a device or in the cloud. Your business data is always on the move. Minimize risk, increase visibility, and ensure compliance with lookouts Unified platform. Visit lookout.com today. It's time for security. Now, the show we cover the latest since Security News with Mr. Steven Tiberius Gibson, who I think it now says that on your Wikipedia page, by the way, <laugh>. It does. <Laugh> from grc.com. Hello Steve. Good to see you.
Steve Gibson (00:02:04):
Hello my friend. So I was initially going to call this podcast. I, I wasn't very inspired cuz it was mostly just news, so I was gonna call it news Views and No Snooze, which, you know, it's cute, wasn't great, but, well, yeah, maybe we, we may have one in the future that's called that. But I, I ran across a story about the emergence of voice cloning as a service. You know, we've been talking about ransomware as a service, so like to, to make it much easier for the bad guys to deploy ransomware. Well, once you know, now of course we've got voice cloning as a service. So that, that took over the title and we're gonna wrap up by talking about that. But we're gonna lead off with a tracking device follow up, then answer some questions, including what happened when I updated own as router and what happened when HP attempted to update all of their office Jet Pro nine 20 E series printers in the field.
(00:03:10):
What did the Supreme Court have to say, if anything, about Section two 30? How concerned should key pass users B about this new master password disclosure vulnerability? What's Apple's position on chat? G P T? What's Google been quietly doing about its user profiling without tracking privacy sandbox technology? What disappointing news did the Senate Intel committee just reveal about the US fbi and why did the Python Foundation suddenly close all new registrations of users and packages? Then after I announce and explain the discovery and fix for a long standing bug that has always existed in spin, right? 6.0 what? Long thought? Long thought to be bug free?
Leo Laporte (00:04:04):
Long thought to be perfect.
Steve Gibson (00:04:06):
Ah, I know probably extending as far this bug extends as far back as spin, right? 3.1 as far as I know. Wow. Wow. In the early nineties I did confirm it in five. Oh hmm. We're gonna finish by examining the emergence of this new voice cloning as a service dark web facility, uhoh. And oh, we've got a, a terrific picture of the week. I I I am, I am being overloaded with fences and gates that go nowhere, <laugh>. It turns out
Leo Laporte (00:04:36):
Very common.
Steve Gibson (00:04:38):
Turns out the world is all of this, not I quit is going on here.
Leo Laporte (00:04:43):
But that's pretty cool. Today,
Steve Gibson (00:04:44):
We've, today we've got a really fun picture of the week that will be of interest. It's just so clever about a a mistake that people can make in coating.
Leo Laporte (00:04:56):
Ah, I'm gonna guess the mistake you made in spin, right? It was not a buffer overflow bug. I'm gonna guess
Steve Gibson (00:05:04):
It wasn't. And I will defend myself because it wasn't a bug back then either. Oh, but interesting. It's something that it became one. So see, it's, it's, that's, it's
Leo Laporte (00:05:13):
Interesting. Yeah, that's an interesting yeah, example. Yeah, well, we'll talk about that in a second. But first a word from our sponsor, express vpn, the only P N I use and trust, and I can explain to you why I trusted. But let me explain what you can do with it first. Net one of the things that Express VPN does is let you be anywhere in the world because they have servers all over the world and you can use any one of them as, you know, your exit door to the public internet. Why would you want that? Well, lemme give you an example. Netflix, they have different content available to users depending on where they're located. I asked Netflix about this. They said, yeah, is it, I said, is it wrong for me to do this? They said, no, you paid, you subscribe to Netflix.
(00:06:01):
We just don't think people are gonna end up doing it. Netflix has tens of thousands of shows worldwide. You only get to see you know, the fraction that's available in your country. So watching Netflix without express vpn, be kinda like paying for a gym membership and saying, you can only use the treadmill. Don't, don't look over there at the Bikes Express. Vpnn lets you change your online location so you can control where you want Netflix to think you're located. You're like anime, you go to Japan. You like British comedies, BBC comedies. You go to the uk, they have a more than almost a hundred different server locations all over the world. So you can get access to thousands of new shows. Works with many other streaming services besides Netflix, BBC's, eye player, YouTube, and more. So if you travel, and I know people actually I know quite a few people who have become, you know, gastro nomads like Mike Elgan who've, who, who, you know, live in Mexico or Portugal, other parts of the world, but still wanna see stuff that they got used to at home.
(00:07:09):
This is a great way, maybe the only way to do it. You can watch top Gear on the uk. Netflix can't get it here, but you could watch the top, the BBC top gear there. Jurassic World on the Hong Kong, Netflix, pulp Fiction is on the Canadian Netflix. Just, just for a couple of examples, open the app. Normally what you do is there's a big button, you press start and it picks the server that's closest to you. But right below it, there's a location chooser. And you could say, I want to be in the Docklands in London. Boom. And you are, you have a local IP address and BBC's eye player goes, oh yeah, he's Asian, Asian <laugh>, Asian, English <laugh>. They don't say it like that. I promise you. The, the other thing that Express VPN does is I think really good is, and this is why you want, you don't want a free vpn.
(00:07:59):
You want one that, you know, pays attention to its infrastructure invests they rotate their IP addresses. So there are a lot of services that say, well, we know that IP address belongs to, you know, a VPN service and they'll block you. They don't do that with Express VPN because they're always using fresh IP addresses. The other thing that's important, they invest in their bandwidth. So you can actually watch HD video from all over the world, even though you're on a vpn. N that's why so many people put express VPN on their router in their house. It protects the whole house. It's why people, why I, for instance, will turn on Express vpn. Forget, because, you know, it's not obvious I'm using a VPN N and keep it on all the time on my iPad. I I did that for I was demonstrating it, I think for a iPad today.
(00:08:47):
Back in the day. Left it on for a long time. I didn't even notice. Cause it's so fast and it works with everything. You've got iPhone, Android, phone, laptops, windows, Mac, Linux, media consoles. Yes, it works on smart TVs and more. Your data is encrypted. So you've got the, you know, you've got absolutely the benefit of privacy. It also secures you if you've got, you know, we've showed some of these devices the people use in open wifi access places like coffee shops like the wifi pineapple. You're protected with Express vpn. They can't, they can't. They can see you, but they can't see what you're doing and they can't see your system. And I know Express VPN is good because I have looked into how they operate and they make every effort. They, their policy is no logging. But they don't just stand on their policy.
(00:09:41):
They run a custom version of Debbie and for instance, on all their servers that every day wipes the drive and starts over. There's no log. And even if, even if that weren't there, they're running their special trusted server technology technology they developed, and by the way, has been independently audited by third parties to be absolutely, as it says it is. It was a sandboxed in memory. And when you open the server, you get your own copy and when you close the server, it's gone. There's no trace of your visit. I trust them. You should too. Be smart. Stop paying full price for streaming services and only getting access to a fraction of their content. Get your money's worth@expressvpn.com slash security. Now, if you go there right now, we're gonna get you three months free with a one year package. That's express vpn.com/security. Now make sure you use that so we get credit, right? So they know you saw it here. Express vpn.com/security now three months free with a one year package. And we thank him so much for support and security now and Steve's efforts here to educate, to inform and to make you laugh,
Steve Gibson (00:10:51):
Ed, to Ed Edutain
Leo Laporte (00:10:53):
Edutain with our picture of the week, <laugh>.
Steve Gibson (00:10:56):
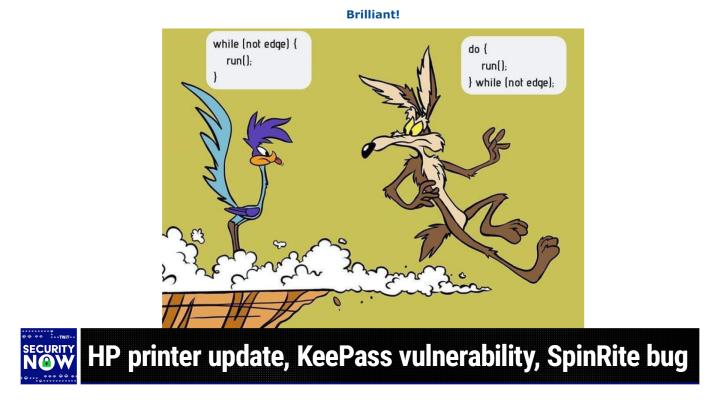
Oh, okay. So in, in programming in general there are often times where you want to do something multiple times. You, you wanna repeat something and we know it's called a loop. So you, you are looping in order to continue doing something. Well, there's a question then, like, how do you know when to stop looping the there, the two standard constructs are to test at the top of the loop before you do whatever it is you are gonna do or to test at the bottom of the loop so that after you've done something, you check to see if you should do it again. And the reason both exist is that they, although they're very similar, right? You are looping and you are testing to see if you should keep looping. The test at the top of the loop may result in, in never doing something if you don't like, if you don't want it to happen at all.
(00:11:59):
Testing at the bottom of the loop normally is used when you, when you always want to do something once, at least once, and then you, you, you test to see if you should do it again. So anyway, so we have a cartoon here with the roadrunner and the Wiley coyote and the, the loop that is controlling the roadrunner says while not edge run. So it's going to check that there, that the road runner is not at the edge and if not the road runner's gonna run and then check again and run the, however, unfortunately the Wiley coyote, his, his actions are controlled by the other sense of loop, which says do run while not edge. The problem being that running is running is happening before the check for the edge. So as often happens to this unfortunately Wiley Coyote, he ran right off the edge, right off the edge then after he was in the air, you know, and, and it's always odd how he's suspended there for an unusually long amount of time.
(00:13:14):
Like what, what has happened? You know, where's the gravity here anyway, so we all have a chance to see that the coyotes in trouble. Then we check to see, oops, he's not over the edge anymore. And then woo. And then we switched to the long distance, you know, little, little dust you know, explosion down at the bottom of the canyon. But the good news is now he seems always undaunted and he springs back the life for, you know, to harass the roadrunner further. Okay, as I mentioned last week, GRCs security Now news group was holding a great deal of discussion surrounding this. All of the air tag the air tag tracking issues in that vein, a person named Lee Ally posted that they had stumbled across a YouTube video which explained how to without much trouble remove the little beeping speaker from an air tag.
(00:14:12):
So he posted that and I asked him whether he had any impression from the video about why the person making this video thought that that would be useful. And Lee replied, the reason is to prevent alerting a thief to the presence of the air tag. And he said the YouTuber begs people not to misuse the hack. Well there's been some related discussion in the news group questioning how an air tag that's beeping can be used for stolen item recovery since the beeping will inherently disclose the hidden of the tag. You know, at which point the attacker might either, well Leo, as you did last week, smashed the crap out of it with a mallet in order to render the tag inert or perhaps be more sneaky and you know, tuck it down into the backseat of an Uber driver's car so that the tag will drive off with the car and you know, good luck finding it.
(00:15:14):
The salient point here being that we have two use cases which are inherently at odds with one another. Someone trying to locate something that is not in the hands of someone nefarious wants help locating the object. So in this context, beeping to call attention to the not stolen tagged object is desirable. Whereas someone trying to locate something that has been stolen doesn't want the nefarious thief to know that they have been tagged and are being tracked. So in that context, beeping which calls attention to the presence of a tracking tag is undesirable since the tag's paired owner might know which of the two contexts is proper. You know, did I leave my car key somewhere or has my scooter been stolen? I'm sure that at some point someone must have suggested that it would be possible technologically to give the tags paired owner remote control over the beeping since they would know which context applied and whether the tag should be set to beep or not.
(00:16:31):
But of course we can't do that either since that control assumes that the tag's paired owner is honest, honorable and ethical, which would not be the case when someone wishes to deploy the tracking tag. Not to keep track of their own stuff, but to surreptitiously track someone else or somebody else's stuff. So the point I'm hoping to highlight here is that a fundamental, and I think irresolvable, you know, irreconcilable tension inherently exists for which there is no single perfect answer. And that's the 10 that is this tension that apparently was reflected in this forthcoming i e TF tracking specification, which we went over in detail last week. The spec never explains the why of any of its requirements, right? We didn't see that it only lays out the what, so we're left to guess. But for example, the provision that tags must wait a random length of time from eight hours to 24 hours after being physically separated from their owner before they're allowed to start making any noise.
(00:17:51):
And then only when they are jostled feels like a compromise between the need for stealth in the event of a tagged items theft and the need for disclosure in the event that someone else's tag is being used for nefarious tracking. Now we learn that disabling a tags beeping speaker is easy to do and using, you know, somewhat more precision surgically than Leo you you did last week. Clearly someone who tags their own E-bike for example, would desire to keep their tag quiet. Since locating a tag attached to a large bicycle won't ever require a speaker and preventing a thief from discovering the tag could be extremely useful. In fact, if I were to tag something big like that today, you know, knowing what I know now, I would disable this tiny speaker too. Unfortunately, the obvious flip side to this is that, you know, low budget bad guys who wish to track others surreptitiously using air tags could also disconnect the devices tiny speaker in order to keep the tag from revealing itself.
(00:19:05):
There's no way to win on this one. These Bluetooth LE tags are a powerful consumer tracking technology that is inherently prone to abuse. But you know, presumably that is offset by the fact that they're also very useful and we know that a hundred million plus have been sold so far in just the last two years. Okay, so automatic i o t device updating an issue we've been talking about recently and two really interesting little tidbits. Well, one somewhat interesting and the other really interesting <laugh>. So we know that some of it is here already and the more is clearly coming. Much of the forthcoming legislation and pending regulation surrounding the behavior of connected I o T devices makes mention of the need for the provision for automatic autonomous firmware updates. I recently mentioned that when I was asked that when I asked the A R T A C 68 U wifi router at one of my locations to perform a self-check for newer firmware, it said there was an update available.
(00:20:23):
I mentioned this in the context a couple weeks ago of the problem of a lack of automatic autonomous firmware updating, wondering how many of us were incessantly checking for the availability of updated firmware for our various devices and presuming that most of us generally had more pressing things to do and thus the problem that routers may not be getting updated the next week we learned from a TP link using listener that those vulnerable TP link routers, at least some of them did have autonomous update capabilities, which was enabled by default. So that was great news. Then I received a Twitter DM from another of our listeners. Sean Merrigan tweeted Steve regarding auto update routers Aus added this feature into this now old router and he had old and per in quotes, R T A C 68 U the one I just mentioned, I the one that I use a couple of years ago he said, and they're still updating the firmware regularly.
(00:21:32):
Well that was interesting to me. I knew from having recently checked new firmware was available for that router though I hadn't taken any action on that yet. In defense of my apparent laxity, I'll remind everyone that this consumer router is not on the front line with its wham port facing a hostile internet. It sits safely behind the frontline router, which is running pf sense since I play lots of static port translation gymnastics to avoid Cox cables annoying consumer bandwidth port filtering. But Sean's tweet came at a perfect moment, so I logged into the A R T 68 or R T A C 68 U and asked it to please update itself and it did that. And low and behold, what missing feature do you think I found had been added to this router since its last update? Yep. Automatic firmware updating my router now has the ability to update itself autonomously at 2:00 AM whenever it detects that ASUS has some new firmware for it. So that's the good news. But this good news comes nicely paired with the most catastrophic possible outcome of auto autonomous auto updating.
(00:22:58):
I labeled this story HP 90 20 e error code eight three C 0 0 0 0 B. A post dated May 8th of this, so May 8th of of of obviously this month at 7:30 AM on HP's customer support forum. They a addressing HP office Jet Pro 90 22 E all in one printer. The post is, hi there, my printer is offline with a blue screen and didn't you know they had to choose blue as the background at error code 83 CUN 0 0 0 0 B. I have read through other posts and tried the Powerade reset but to no avail. Can someone send me instructions to perform a semi full reset please? Many thanks. That particular forum posting, which launched a thread generated 132 replies all on its own, such as I have the same problem and have just been going around in circles trying to find a solution or ditto. No coincidence that we're all having the same issue on the same printer on the same day.
(00:24:22):
Software issue. HP please help or same problem here too. Did anyone get a solution? My printer's only three months old and it is used for business, so I need it to work asap. Has anyone had any luck resolving this? I have the same issue. Hi there. Did you get any resolution as the same exact thing has happened to me this morning and, and final three? I had the same problem. Brand new printer. I've tried unplugging the power cable and waiting for a minute. The error is still there in a blue screen and a power button sign. HP please find a solution as our work is affected also. Hello, same problem on my 90 20 20 E four months old, I switched it off for a few hours, removed the power cable, but still blocked on 83 CUN 0 0 0 0 B error message. And lastly, I have an office Jet 90 90 22 Pro under warranty and with an HP cartridge subscription.
(00:25:22):
I have same error code since yesterday, 8 5 20 23 after three calls to HP after sales service, more than an hour and 30 minutes, no solution. The problem is being studied by hp. I am awaiting instruction. If no return info, I return it and it could end with a refund via distributor. And he says peren, Amazon, France. Thank you. Oh and and one last one. This is insane and not a word from hp. I came here to make a post about this and it seems it's basically a global issue. Can someone from HP provide an update? This is terrible. We cannot print anything stuck with this error. Okay, so now let's turn to our friends at bleeping computer for a succinct summary of what's going on. Bleeping computers headline reads, HP rushes to fix bricked computers after faulty firmware Update and note that this was posted just this past Saturday.
(00:26:28):
12 days after all of their affected printers were turned into expensive bricks. H bleeping computer writes, HP is working to address a bad firmware update that has been bricking HP office jet printers worldwide since it was released earlier this month, meaning the firmware update was released. While HP has yet to issue a public statement regarding these ongoing problems affecting a subset of its customer base, the company told Bleeping computer that's addressing the blue screen errors seen by a limited number of users HP told Bleeping computer. Our teams are working diligently to address the blue screen error affecting a limited number of HP office Jet Pro 90 20 E printers. We are recommending customers experiencing the error. Contact our customer support team for assistance@supporthp.com. Believe being computer wrote impact that printers include HP Office Jet 90 22 9 0 2 x models including HP Office Jet PRO 90 22 E, 90 25 E, and the 90 20 E and 90 25 E all in one printers.
(00:27:48):
In fact, that customers report that their devices display blue screens with 83 CUN 0 0 0 0 B errors on the built-in touch screen. Since the issues surfaced, multiple threads have been started by people from the us, the uk, Germany, the Netherlands, Australia, Poland, New Zealand, and France, who had their printers bricked some with more than a dozen pages of reports. One customer said, HP has no solution at this time. Hidden service menu is not showing and the printer is not booting anymore. Only a blue screen. Another added. I talked to HP customer service and they told me they don't have a solution to fix this firm or issue at the moment. Others have said that the only way to address the issue is to send the printer for servicing to hp and that the firmware doesn't even load partially, it instantly fails. HP remotely bricked our devices. Some user said that HP would be sending out a placement.
(00:28:54):
Since the buggy update, leaping computer finishes seems to install automatically onto internet connected printers. HP customers are advised to disable their device's internet connection and wait for a firmware update to fix the bricking issue. So as it happens, it's not often that we actually get a horrific real life answer to our often posed question <laugh>, what could possibly go wrong? But oh boy. Wow. Apparently the only reason some of these susceptible model printers were not blasted into oblivion was that they had not phoned home to check in for a firmware update. In this instance, they had a blessed lack of connectivity. We do need to expand upon our normally rhetorical what could possibly go wrong. Question to also ask how could this possibly happen? Right? I mean, this would lead anyone to ask, did HP not ever actually test the firmware that they set out to every available printer, which then proceeded to kill all of them?
(00:30:26):
It must be that HP had at some point working firmware in the lab. So we have to conclude that somewhere between the lab and all of those end users, that firmware image file became corrupted somehow. Perhaps it was a corrupted file transfer to the update server or somehow the file on the update server itself became corrupted. But without information that only HP has and which we will probably never have, it's impossible to know exactly how and why this blew up. All we can do is examine the debris field, but regardless of what happened upstream of these printers, which will almost certainly forever remain unknown, what we do know today is that HP's autonomous updating system is not well designed because this should have been not just unlikely to happen, but impossible to have happen. We're witnessing the obvious downside of poorly designed autonomous updating, which is that if you're not careful, you can potentially hose your entire installed base of devices, whatever and wherever they may be.
(00:32:01):
And I suspect that since HP has not yet been forthcoming with an explanation, though I'm sure by now they know just how deep in the do-do they are. We're never gonna know exactly what happened. Today's HP is a massive enterprise, which means that they have squadrons of well-paid attorneys who immediately clamp down on all communication in an attempt to minimize perceived culpability. Even though it's gonna be difficult to explain this one away. Today's HP is not The HP I grew up admiring HP as many of I'm sure old timers know, was founded by a pair of electrical engineers working in a small garage in Palo Alto, California back in 1939. Bill Hewlett and David Packard correctly divined that what the world really needed was a high quality analog signal generator. So they built and sold some and then they built and sold many more.
(00:33:11):
The reason for my annoyance is not just HP sloppy software, although their printer software, at least for Windows, is a true atrocity now. But what appears to be the case is that HP has just bricked all of these printers, rendering them unusable, at least for the time being. In order to update the printer's detection of non HP Printer Inc. Cartridges in a move to further thwart the use of significantly less expensive and just as effective third Party Inc. Ours Technica also covered this month's HP printer bricking debacle. And at the end of their coverage, they added some additional interesting insight ours wrote. It's unclear what exactly prompted the firmware update that broke HP's printers. HP's support pages for the 90 20 E and 90 25 E series only emphasizes the printer's use of HP's much maligned dynamic security. They have that in quotes. HP they write uses dynamic security to stop printers from working with non HP brand ink cartridges.
(00:34:38):
HP's notoriously sudden issuance of dynamic security to printers has abruptly rendered piles of ink useless Officially, HP says it uses dynamic security measures to protect the quality of our customer experience, maintain the integrity of our printing systems, and protect our intellectual property. But since debuting in 2016, it has resulted in class action lawsuits and irate customers stuck with otherwise functioning Inc. That HP decided should not work. HP's dynamic security page notes that dynamic security printers require periodic firmware updates to quote, maintain dynamic security effectiveness. I'll bet, I'll just bet they do. And that updates can improve, enhance, or extend the printer's functionality and features protect against security threats and serve other purposes. So ours finishes HP's poor handling of printer firmware updates can deter people from future updates that may be important. Meanwhile, HP has traumatized countless customers and mean and, and many will now think twice before, depending upon an HP printer again.
(00:36:07):
So if we wonder why HP printers which employ dynamic security might require periodic security updates, it may be because HP feels that their control over their printers allows them to avoid playing on a level playing field where they need to compete with other suppliers of ink cartridges. So they're engaged in a game of cat and mouse with the third party ink vendors who are continually working around HP's dynamic security measures in order to get their ink to flow. That then necessitates HP again updating their non HP Inc. Defenses with new firmware. It's a sad game, really. And this time it appears that the jokes on hp, but regardless of why this happened, it's gonna be quite interesting to learn whether this can be fixed in the field. The printers do all have a U S B port. So if the printer is able to boot from a properly formatted u sb thumb drive, even with its firmware in this apparently badly blasted state, HP might be able to avoid replacing all of the destroyed printers in the field by giving their users a recovery image to download onto their own thumb drive or express mail.
(00:37:37):
A ready to boot thumb drive to anyone who requests one. But we don't yet know whether that can be done since customers would probably not have shipping boxes. The shortest path might be to send a new printer in a box and ask the user to box up their dead printer and return it in the same box no matter what. It's a mess. The Aus router upgrade page says, in case the upgrade process fails, R T A C 68 U enters emergency mode automatically. The l e d signals at the front of the router will indicate such a situation. Please visit asus Download Center to download ASUS firmware Restoration Utility for a manual update check FAQ for more instructions. It doesn't appear as though HP has provided for such a contingency, but the observation I'd like to make is that today's flash memory is very inexpensive, so there is no excuse for not incorporating a factory backup image of printer firmware that the system can boot can fall back to.
(00:38:59):
Oh, that's a good idea. Yes. And, and boot into in an emergency simply by pulling the most significant address line of the flash memory high, thus switching to a secondary memory bank containing the backup image, then trigger a reboot and you're back. In. Business processors used in embedded environments typically incorporate what's known as a watchdog timer. It's a sort of a dead man switch. The idea is that running software will periodically reset the watchdog timer, always making sure to do so before the timer has the chance to expire. This is typically easy to do since the watchdog generally doesn't need to respond instantly to any problem. It's the response of absolute last resort. So whereas the code in the device's main execution loop might reset the watchdog timer every second or so, the timer might wait for se for 20 seconds without a reset occurring before it has the chance to expire and declare an emergency.
(00:40:16):
The first time an emergency occurs, the watchdog might just perform a reset to recover the device from a random glitch, you know, a power line hiccup or cosmic ray. But it would remember that that's what it had done. And if it got back if, if it got called back again into action soon or several more times, it would pull that address line high switch to the backup firmware and bring the printer back online. If HP had done this, a couple of third party ink cartridges might have slipped past due to not running the latest anti third party ink firmware, but a major economic and reputational disaster would've been averted. So the point I wanna leave everyone with is that yes, of course autonomous updating can be done wrong and we are apparently seeing a glaring example here, but it can also be done in a way that will always fail safe rather than fail dead. And on that happy note, Leo, let's take our second break <laugh>, and then we're gonna talk about section two
Leo Laporte (00:41:32):
30. Yes, indeed, we are I will remind everybody that we have a wonderful sponsor. Now you are, I know Steve, a big guy on supplements. And so you know how important it is. The diet alone, especially our modern diet, often misses critical vitamins minerals and pre and probiotics. Well, there's an easy way to get it all in one inexpensive dose. It's AG one by Athletic Greens. I've been using this and I I love it. It tastes great. It gives my body everything it needs. One daily nutritional drink. Athletic Greens AG one has been around since 2010. Part of millions of routines since. In fact, I was very surprised when we were talking about this and Aunt Peru said, oh yeah, I haven't taken that for years. AG one is the best all in one solution for daily nutrition. It saves you time, it saves you confusion, and it saves you money.
(00:42:27):
Each dose is about $3 a day. That's a lot less than I was paying for about 20 different supplements. Plus Ag One's Daily Habit gives you powerful long-term results. This is the kit I got, and you can see I drank mine, <laugh>. There's very little left, just a sip left of my ag one. The kit's great. It comes with a even a nice metallic measuring spoon so you don't have to worry about the packets. But for travel, I love these AG one Daily packets. This is what you take on your trip with you. You don't have to take a bunch of a pill miner and a bunch of bottles of pills or anything. AG one makes it easy to take high quality supplements, whether it's improving de digestion or supporting your sleep. Ag one, the best bang for your buck. The tastiest too. It's a seamless, easy daily habit.
(00:43:13):
Just one scoop of ag one in the morning covers your entire day's nutritional bases. Get all your supplements, support your long-term gut health. I love the probiotics in here with AG 1 75, 75 high quality minerals, vitamins, pre and pro-biotics. If you're looking for a simple and effective supplement routine that doesn't cost an arm and a leg ag one by Athletic Greens. In fact, you right now, if you order and subscribe, you'll get a free one year supply of Vitamin D, little droppers you could put in and five free travel packs, which I tell you what, you're gonna get hooked on these. They're great for travel with your first purchase of a subscription. How do you do it? Just go to athletic greens.com/security now. Athletic greens.com/security. Now it's delicious. Mm. And it is nutritious <laugh> atlantic greens.com/security. Now, I thank him so much for their support. Back to you, Mr. Steve.
Steve Gibson (00:44:15):
So Leo, I know you had some Section two 30 legal experts on the Sunday.
Leo Laporte (00:44:19):
We had a great show on TWI. Yeah, cuz that's all we talked about pretty much. Yeah. Yeah. I
Steve Gibson (00:44:24):
Was able to listen to the, just the beginning. I've not been able listen to the whole thing, but I, I plan to as we know, the bit of law that's become famous for its section number two 30 is what essentially allows Facebook, Twitter, YouTube, and anyone else who hosts content provided by others to avoid liability for any consequences which might arise from their hosting of that third party material. So perhaps the biggest news of last week, or at least a relief for a lot of the internet was that the Supreme Court, which first surprised many court watchers when they agreed to weigh in on the appeals made to the Ninth Circuit Court's earlier decisions produced their conclusion in May rather than waiting until the end of the current term, which is in June. And to the great relief of practically everyone, section two 30 held up under the Supreme Court's review and remains, at least for the time being in full force and effect, both tech and non-tech press covered the news.
(00:45:29):
I felt that the E F F was a bit snarky in their coverage, which they headlined the internet Dodges censorship by the Supreme Court. Yeah. Dodged it by nine to zero. So I would say that <laugh>, it's a unanimous dodge. Yes, that's right. Tech Dirts Mike Masnick dug deeply into the details. It's way more than we need here, but I linked to his coverage in the show notes for anyone who really wants a deep dive. Reuters, however, provided a very good overview of the issues. And since this is of crucial importance to the way the internet evolves, and since this may not be settled law forever, I think it's worth looking at the way Reuters summarized the court's involvement. So they wrote the US Supreme Court handed internet and social media companies a pair of victories on Thursday, leaving legal protections for them unscathed and refusing to clear a path for victims of attacks by militant groups to sue these businesses under an anti-terrorism law.
(00:46:35):
The justices in a case involving Google's video sharing platform, YouTube, part of Alphabet side stepped making a ruling on a bid to weaken a federal law called Section two 30 of the Communications Decency Act, the safeguards internet companies from lawsuits for content posted by their users. They also shielded, they also shielded Twitter Inc in a separate case from litigation seeking to apply a federal law called the Anti-Terrorism Act that enables Americans to recover damages related to an active international terrorism. In both cases, families of people killed by Islamist gunmen overseas had sued to try to hold internet companies liable because of the presence of militant groups on their platforms or for recommending that content. The justices in a nine to zero decision reversed a lower court's ruling that had revived a lawsuit against Twitter by the American relatives of Nawas aloof. A Jordanian man killed in a 2017 attack during New Year's celebration in an e Istanbul nightclub claimed by the Islamic State Militant Group.
(00:47:51):
In the case involving YouTube, the justices returned to a lower court a lawsuit by the family of Nohemi Gonzalez, a college student from California who was fatally shot in an Islamic state attack in Paris in 2015. The justices declined to address the scope of Section two 30, concluding they did not need to take that step because the family's claims likely appeared likely to fail. Given the Twitter case decision, section two 30 provides safeguards for interactive computer services by ensuring they cannot be treat, be treated for legal purposes as the publisher or speaker of information provided by users. Calls have come from across the ideological and political spectrum, including Democratic President Joe Biden and his Republican predecessor Donald Trump, for a rethink of Section two 30 to ensure that companies can be held accountable for content on their platforms. This case marked the first time the Supreme Court had examined Section two 30 s reach, Google's general counsel said countless companies, scholars, content creators, and civil society organizations who joined with us in this case will be reassured by this result.
(00:49:13):
We'll continue our work to safeguard free expression online combat harmful content and support businesses and creators who benefit from this content. Critics have said Section 2 32 often prevents platforms from being held accountable for real world harms. Many liberals have condemned misinformation and hate speech on social media. Many conservatives have said voices on the right are censored by social media companies under the guise of content moderation. The massacre at Istanbul's Rihanna nightclub killed Ossoff and 38 others. His relatives accused Twitter of aiding and abetting the Islamic State by failing to police the platform for the group's accounts or posts in violation of the Anti-Terrorism Act. Gonzalez's family argued that YouTube provided unlawful assistance to the Islamic State by recommending the group's content to users. In their brief ruling, the justices wrote that they quote, decline to address the application of Section two 30 to a complaint that appears to state little, if any plausible claim for relief.
(00:50:27):
Chris marches an attorney with net choice, a technology industry group that includes Twitter, meta, and Google as members said, even with the best moderation systems available, a service like Twitter alone cannot screen every single piece of user-generated content with 100% accuracy. Imposing liabilities on such services for harmful content, that intention unintentionally falls through a crack would have disincentivized them from hosting any user-generated content. The quitter, the the Twitter case hinged on whether the family's claims sufficiently alleged that the company knowingly provided substantial assistance to an act of international terrorism that would allow the relatives to maintain their suit and seek damages under the anti-terrorism law. After a judge dismissed the lawsuit, the San Francisco based ninth US Circuit Court of Appeals allowed it to proceed concluding that Twitter had refused to take meaningful steps to prevent Islamic state's use of the platform conservative Justice. Clarence Thomas, who authored the Supreme Court's ruling, said the allegations made by the plaintiffs were insufficient because they point to no act of encouraging, soliciting, or advising the commission of the attack.
(00:51:53):
Quote, these allegations are thus a far cry from the type of pervasive, systemic and culpable assistance to a series of terrorists, atta activities that could be ascribed as aiding and abetting each terrorist act. Thomas added in the Twitter case, the Ninth Circuit did not consider whether Section two 30 barred the family's lawsuit. Google and Facebook. Also, defendants did not formally join Twitter's appeal. Okay? So as with many of the decisions reached by the Supreme Court, the result was not terribly satisfying. The court presumably obtained the outcome they wanted, which was to leave Section two 30 in place as is in its entirety. But they did so not by directly addressing the issue, but by focusing on procedural distractions like, you know, complaining that someone had forgotten to tie their shoes. At the end of his long and interesting analysis, tech dirt's, Mike Masnick concluded, he said, finally speaking about money, time, and resources, the, as Mike put it, he said, a ton of all three were spent on beliefs from Amic amici for the Gonzalez case in which dozens were filed, including one from us.
(00:53:26):
And the end result was a three page per Curium basically saying quote, we are not going to deal with this one. He said, the end result is good, and maybe it wouldn't have been without all of these briefs. However, that was an incredible amount of effort that had to be spent for the Supreme Court to basically say, Hey, we'll deal with this some other time. The Supreme Court might not care about all that effort expended for effectively nothing. But it does seem like a wasteful experience for nearly everyone involved. Okay, so anyway, two 30 stands un weakened, but still likely as saleable in the future if the right challenge is brought. And Leo, I didn't, as I said, I didn't have a chance to listen to your experts on Sunday. Did they have a different take?
Leo Laporte (00:54:25):
Well, for Kathy Galles, who was the person who wrote that Mike Maks tech Dirt Amicus you know, there were two cases. There was Google and there was Tam. And the reason that they they put aside one is because they said our, our ruling in Tamma applies to both. So the ruling that the, and, and I think Mike's point in Tector was that the the you know, it was Clarence Thomas who wrote the opinion, the opinion in the Tamma case basically made the case for Section two 30 without actually mentioning Section two 30. They ended up deciding more on what aiding and abetting meant in the Terrorism Act and whether this was aiding and abetting, and they said it didn't. So it didn't, it, yeah, I mean, it's true. It doesn't really one way or the other.
(00:55:18):
It doesn't confirm two 30. But what Thomas wrote certainly can be used in future cases, right? To justify right. Two 30. You know, one of the issues in in the Google case was the idea of an algorithm. Does an al if an, if a, if a company, or I guess it was a Twitter case, if a company uses an algorithm, no, it was Google to recommend to recommend a a a video. Is that the same as them publishing the video? And that was the contention of the plaintiffs. But in fact the court said no algorithms are used everywhere all the time. That does not make it something that the the, the company published. This is important for you too, because you run forums on your website. Yeah. Section two 30 protects you. If, if it didn't exist, you would probably think twice about running forums as I would not just forums, but our Mastodon instance, our chat rooms.
(00:56:12):
We wouldn't do it because we would be liable. What section two 30 does is so important is it provides immediate injunctive relief. You say, no, no somebody sues you. You don't have to really defend yourself. You just say Section two 30, your honor, and this judge will throw it out immediately. So, and that's how it's supposed to work. The none of that was impacted by the Supreme Court's decision, but the opinion Masnick says, and I think he's right it makes a very strong case for why two 30 exists. You have to have it. So I think yeah, Dodges in the sense that they didn't really address two 30 is probably not inaccurate, but what they did do, did not in any way weaken it and perhaps even strengthens it. Good. There'll be another case, I'm sure. Yeah, this was the right thing. I mean, they were, if you listen to the arguments in the Google case, which is I listened to, they were, they were at the one point they were saying, well, Google made thumbnails of this video that makes 'em liable. And it's like, no, no, no. They just, they, it was poorly argued, frankly. So anyway, okay, so victory. So declare victory. Yes. And move on. Yes,
Steve Gibson (00:57:17):
Yes. Last week the entire tech press community lost its collective mind over the news generated by a hacker. That key pass was insecure and that it was possible to obtain the key pass master password and thus everything else that it was protecting infosecurity Magazine's headline was Key Pass Flaw exposes Master Passwords. Well, that didn't sound good. The Hacker News reported under the headline Key Pass Exploit allows attackers to recover master passwords from memory. SE Magazine said, key pass Bug let's attackers extract the master password from memory. And actually they had by far the coolest graphic, which I put in the show notes. Tech Target wrote Key Pass Vulnerability enables master password theft Amania passwords at risk, major key pass flaw unearthed <laugh> tech radar. This top password manager apparently has a major security flaw that could spill all your logins and finally, help net security Key pass flaw allows retrieval of master password. Proof of concept is public. Oh. Oh, okay. So here's the one and only thing that this podcast's well-informed listeners need to know. It's an entirely local attack. In other words, newsflash, if your machine has malware running amuck, it's not safe to use a password manager. <Laugh> no.
(00:59:01):
Any password manager. Correct. You know, not just Key Pass, right? But by the very nature of what any password manager is and needs to do, no password manager is safe from local attack and they don't try to be because it's a fool's errand. Recall how almost all commercial video DVDs, DVDs were encrypted to prevent the theft of their contents. But D V D players were fundamentally unable to keep their keys secret because they needed to use them in order to decrypt the DVDs. <Laugh> it was, it was so dumb. <Laugh>, it's an ana, it's an exactly analogous way, a in an exactly analogous way. A password manager that's going to fill in blank username and password feels must have access to that passwords ma, that password manager's decrypted password database. Even if you set it up in an annoying way to require you to provide the master password each and every time you use it, it would still briefly need to decrypt and read the master database to obtain the required password. The reason we were so upset with Last Pass was not over something like this, which as I said is an inherent design point for any client's side. Password manager, we got upset with LastPass because they lost everyone's encrypted data all at once. And then we learned that a lot of it had never been encrypted and that what what was encrypted might not have been very well encrypted. Key Pass is a popular free and open source password manager. I don't use it, but I know from Twitter that some of our listeners do. Most
Leo Laporte (01:00:57):
Of them I would hope use Key
Steve Gibson (01:00:58):
Pass xc,
Leo Laporte (01:01:00):
Which is not by the way, vulnerable to this. This
Steve Gibson (01:01:03):
Is it is, it is, it is a fork of of that is not vulnerable. So you have to imagine the key pass is lead developer Dominic Reichle, who has recently been attacked from every angle has gotta be asking himself about now <laugh>, why he's been working so long and hard sad on this currently thankless project.
Leo Laporte (01:01:24):
We do not treat our open source developers very well, do
Steve Gibson (01:01:27):
We? No. No. So here are some details to give everyone some sense for what's going on in this particular case. The issue affects the software's custom text box control, which is used for entering the master password and other passwords during editing for the, and it's called KeyPass two point x master password dumper proof of concept tool to work. You need some access to the system ram through a system RAM snapshot. So on a Windows machine, that would be the process dump the page file CIS swap file the the HI file CIS hibernation file or a RAM dump of the entire system. The researcher whose work has generated so much click bait said quote, the flaw exploited here is that for every character typed a leftover string is created in memory because of how dot networks, it is nearly impossible to get rid of it once it gets created.
(01:02:42):
So this sounds like a case where a developer using a very high level language framework.net is being betrayed by the low level way. Some of the language environment functions behind the scenes. In this case, the environment's automatic string management, it wasn't really meant for implementing super secure systems, at least not without giving it extra explicit thought. There's just too much automatic stuff happening in the background. You know how when entering a password in iOS, the most recent character typed can be seen for confirmation while all previous characters are blanked out with a round bullet character. It appears that this is what Key Pass does, but that the custom control that its author initially created is discarding each of the intermediate strings, which leaves them floating around in ram. The exploit's developer said quote for example, when the password password is typed, it will result in these leftover strings, a bullet and an A, which is the the second character, and then two bullets and an S three bullets and an S four bullets and a W five bullets and an O six bullets and an R seven bullets and a D.
(01:04:17):
He says the proof of concept application searches the RAM memory dump for these patterns and offers a likely password character for each position in the password except for the first character, which is not available. The vulnerability affects the key pass two point x branch for Windows and possibly for Linux and Mac Os. It has been fixed in the test versions of Key Pass version 2.54 whose official release is expected in two months in July. Presumably in this updated release, Dominic is no longer using intermediate strings or he's blanking the intermediate string before releasing its storage back to the environment. So that released strings will not contain any sensitive information. But stepping back from the details, the broader lesson here is to always keep a secure systems security model in mind. There are things that the model provides and things that it doesn't. The security model for a password manager is security and protection across the network.
(01:05:33):
No one acting remotely should be able to obtain any secret information in return for using a password manager. Impossible to remember or even enter passwords can be used to provide today's highest generally available level of security for remote network log on, but only from across the network. Password managers do not protect themselves against local attacks and they really cannot because users demand operating systems that are fundamentally insecure. A truly secure operating system is no fun to use because you really can't get any work done. <Laugh>, right? You spend all of your time manually authorizing the system to do anything you want. For a long time, users were running with root privileges because they'd grown tired of always needing to log off of their low privilege account and log back on as a root administrator to install a program. Then having, they'd have to switch back again.
(01:06:42):
Microsoft finally developed Windows split token U A C, right? The user account control system, which minimizes the grief of normally running as a user who only has safe permissions. It is a terrific compromise. So, yay. But anyway, anyone was, I mean, I was just astonished by the amount of of nonsense headlines that was generated by this and poor old Dominic. I mean, he was quoted all over the place saying this is not a problem. This is like, you know, everybody else does it. And as the reason he's not rushing out, like some emergency update, he's saying it's fine and I'll be releasing this in July. So everybody take a break. You know, you don't want malware on your computer if you've got it, don't use anything <laugh>, you know, get rid of the malware anyway. Apple Insider reported that Apple has joined the growing ranks of companies that are banning the use of AI conversational language model AI inside the company.
(01:07:49):
And we know what you know and we know that Apple runs a tight ship. Internal documents and anonymous sources have leaked details of Apple's internal ban on Chad G B T and similar technology, as well as some tasty bits regarding its inevitable plans for its own language. Large language model, as we know, despite their popularity chatting with large language models, can be unpredictable and do tend to leak the data that's being fed to them. Even if dialogue logging is disabled, this information is still leaving the local facility to travel out over the internet. It's not a friend you're sitting in front of or in the box you're holding in your hand. It's a massive remote cloud compute farm. A report from the Wall Street Journal details an an internal Apple document, which restricts Apple employees from using Chat G P T Barred or any similar large language models.
(01:08:50):
Anonymous sources also shared that Apple is working on its own version of the technology, though no details were provided and maybe we'll get some in Apple's big event next week. We previously noted that Samsung had publicly banned their employees from using chat G P T after three incidents where employees had uploaded very sensitive proprietary corporate information in order to get chat GT's opinion. So Apple has also joined the ranks of Amazon, Verizon, and likely many other lesser known organizations in telling their employees that there will be no chatting with the bots during work. As for Apple's own internal large language model work we've, I, I haven't heard anyone assembling a fully interactive speech interface for one of these textual chatter boxes, but boy, it sure does seem like the next obvious thing to do. Being able to have a verbal conversation with this sort of simulated intelligence would take a voice assistant to an entirely new level.
(01:10:02):
So someone's gonna do it sooner or later. We'll, we'll see who gets there first. Although we covered Google's next generation user interest profiling technology in full detail when its detailed mechanism of operation was first announced, we haven't focused upon it for some time yet. Google has been diligently and quietly at work getting the technology ready for release. Google will be rolling out this new Privacy Sandbox technology, their name for it in the third quarter of this year with the release of Chrome one 15. This rollout will take the form of a set of new built-in browser APIs that JavaScript code running in ads hosted on websites will be able to use to obtain categories of interest for the website's visitors. The idea is that online advertisers will be able to deliver ads without collecting any personal information about users and without tracking their movements across the web using third-party cookies.
(01:11:17):
Google has said that as the rollout proceeds, it will also be removing support for third-party cookies from Chrome next year. This will be done incrementally and through careful testing. Initially, in the first quarter of 2024, support for third party cookies will be removed from 1% of Chrome's user base, and by the third quarter of 2024 Chrome and its users will be 100% third party cookie free. The message of course, to advertisers is we're gonna be releasing the api. You'd better switch over to it because the number one browser on the internet that has the lion share is going to be preventing all of the tracking technologies that it's able to in favor of this new api, which, you know, will be in the chromium core, which I can imagine then other browsers may choose to support or not. We'll see, I really wanna believe <laugh> Leo <laugh> Yes.
(01:12:30):
That the agents of that, the agents of the F B I are good law abiding people. Yes, I really do. Yes. And for the most part, I'm sure they are. I wonder how many of our listeners know the name Efram Zimbalist Jr. Oh, I do. Yep. Because we're old. He was the, we're old. He was the lead in the F fbi, which was a television series. I grew up watching every Sunday night from 1965 when I was nine, and I think that makes you seven Leo. Yeah. Through 1974. Yep. In any event recently, CLA declassified documents have revealed that the real US fur Federal Bureau of investigation improperly searched the personal communications of Americans more than is everyone sitting down more than 300,000 times between 2020 and early 2021, according to, as I said, newly declassified documents, which were released by the Senate Intel Committee.
(01:13:39):
I don't know any details, but it seems disappointing and I'm quite sure that Efram Zimbalist Jr. Would've had no part in that. I am sure he didn't even know what a pen register was. I am sure. No. The inappropriate searches occurred under fsa, our Foreign Intelligence Surveillance Act, which may have been, you know, somewhat inappropriate Hmm. For US citizens, you know. Good point. Yeah. The foreign, that foreign part FS A is currently up for renewal by Congress. So, you know, it keeps getting renewed. I imagine it will. Again, the documents reveal that the F B I used the massive trove of communications data gathered using F I A powers to search for information on participants who attended the George Floyd protests Ouch. And the January 6th storming of the US Capitol. The FBI also searched the names of more than 19,000 donors to political campaigns for plausible connections to foreign governments. Hearing this causes me to think that even though my own communications are quite boring, it's my right as a US citizen for them to remain truly private unless and until a court orders otherwise. So utterly unbreakable end-to-end encryption. Yes, please.
(01:15:10):
Over in the increasingly fraught open source registry supply chain world, things have grown so bad that the Python Foundation was finally forced to suspend the creation of new accounts and new packages. The foundation has suspended all new user registrations as well as new package uploads to pii. The official Python package index, the organization's security team says PII saw another wave of malicious packages being uploaded on the platform over the past week. PII staff says the incident occurred while some of its members were on leave, and that the smaller group of personnel on duty were quickly overwhelmed by the large number of reports and malicious packages they were, they had to remove. So they threw the switch and said no more of anything for the time being existing users can still access and update their projects. It's just new accounts and new projects that are barred for the time being. What was that about? Why we can't have nice things. I'll have more to say about these disturbing trends at the, in this week's closing comment.
(01:16:28):
But first I have some interesting news about a long standing spin. Right. 6.0 bug to share. It turns out that my claim that spin right six oh has had no known bugs for the past 19 years has not been correct. Though I suppose it would depend upon how you define known. Certainly it hasn't had any appreciated bugs, but it definitely has had a bug. And thanks to the work of an independent coder named Paul Farer, F A R R E R G R C is now offering a pair of patch utilities, which fix this bug. That spin right has had perhaps since the mid nineties with spin Right three one, since it only occurs on drives larger than 549 gigabytes when Spin Wright's Dyna stats system kicks in to perform data recovery and repair. And since this behavior has been present since at least spin right three one, what is now seen as an overflow was very likely my deliberate design decision at the time since drives of that size were not even a dream back when 50 megabytes was a large drive.
(01:17:56):
So what likely happened was that as I evolved spin right through the decades, I never revisited the parameters surrounding this one division operation to notice that modern drives might now cause it to overflow. Through the years we've had reports of spin, right? Halting with a division overflow error. Somehow I got it into my head that the location reported by Spin Wright of this overflow was the segment where the error was occurring, not the offset. So B zero four E would not be in program space, it's in the region of memory that was once set aside for the monochrome display adapter, which is now completely unused. So I assumed that this error was occurring in a chunk of code that the system's bios had mapped into that unused region. And this belief was supported by the fact that GT's GRCs tech support guy, Greg, has developed a collection of workarounds for spin rights users who encounter this error.
(01:19:09):
Things like try running spin right with that drive on another machine, which he says often works. In fact, over the weekend, when I wrote to him to tell him that we had a patch for this longstanding problem, his reply was, since we are getting closer to six one, I'll probably use this as the last thing to try, as all the other fixes we have in place are much less technical. So my point is, this hasn't been a big deal or issue for us, but I do know for certain that it has been so for some users and that's not okay. So I also now understand why moving to a different machine may have helped since part of the issue surrounding the biosis mapping of cylinders heads and sectors to a drives linear sector number was what was going on. And that mapping is one of the many things that different bios might do differently.
(01:20:10):
In any event, Paul had just finished developing a different patch for all of those buggy AMI bios, which I talked about before, that we discovered were blasting main memory when anything attempted to access sectors past 1 37 in gigabytes on U S B connected drives out of an abundance of caution, which I feel is warranted. Spin right? Six one, the forthcoming spin right will refuse to go any further than the first hundred and 37 gigabytes on any USB drive. But Paul had access to our news group, which was full of people who had machines with those buggy. It turned out to be AMI only bios. So working with those users, he's created a tiny utility that can be run before spin, right? That is before spin, right? Six one if it finds an AMI bias that it recognizes, it patches it. And then with my blessing, we discussed how this should be done to be stable.
(01:21:20):
His utility will remain in RAM and cause spin, right? Six one to believe that U SB devices are scuzzy devices, thus lifting six point one's cautionary clamp on U SB drive size. So that little utility will be made available for users to use at their own risk if they choose spin, right? Seven will not use any bias. So all of this will be going away as soon as we move there. After doing that work, Paul became curious about that B zero four E error without my bias of assuming that this was the segment of the problem and therefore in the bios and not in spin. Right? He assumed that I had been reporting the offset as I was. So he looked into spin right's running in memory code and sure enough, he found a division instruction at that offsite off at that offset in spin, right?
(01:22:21):
He then proceeded to reverse engineer that region of spin rights code to figure out what was going on there and why at one point I provided him with the relevant chunk of spin rights source so that he could be sufficiently confident that he knew exactly what was going on. He had it exactly right. Drives had become much larger, and the math that I had not revised for decades, which decomposed a linear sector number into cylinders, heads and sectors for the bios, was no longer able to handle today's larger drives. So Paul has produced another patch utility, which fixes this problem for spin, right 6.0. He created both a DOS driver, which can be loaded through config SISs and a DOS tsr, you know, a terminate and stay resident that can be run before running the current version of Spin. Right? Six, after testing it thoroughly.
(01:23:22):
He provided me with his source code to review and it was immaculate. So thanks to his efforts, we have a patch for this bug that's always been in spin, right? Since its very early days. Out of curiosity, I checked spin right's source code for spin, right 5.0, which is dated February 11th, 1996, and it's the same code that Spin, right? 60 is still using. So I never changed it for spin, right? Six zero since, again, at the time it was not a bug, but it is today hitting this error, which can only occur on drives over 549 gigabytes and only when Ssta engages does not endanger or damage any of a user's data. But it does mean that Spin Wright cannot proceed with its recovery and repair. So my advice to all Spin Wright users listening to this podcast would be to grab Paul's patch and to add it to spin right's boot media.
(01:24:23):
The file is called MD F Y SR 60 as in modify spin, right six zip, and it has a menu entry under GRCs main man menu under spin right and knowledge base B zero four E. It's also in our freeware collection, and it's now referred to near the top of the spin right faq. My hope is that anybody who hits the problem will be able to patch spin, right? And then move on. And of course, I've told Greg about it as I was writing this up for today's podcast. I suddenly became curious about what the code for this looks like now, since, you know, a lot of spin writers is still the same, but we already know that six one doesn't contain this bug. We've all been running lots of dynas stat recoveries on lots of multi terabyte drives without any trouble for the last six months. So I was pleased to see when I went to look that I had completely replaced that old code with a new routine, which is capable of handling a full 64 bits worth of sectors. That's 18,446,744 terabytes, <laugh>. Oh, you'll be okay for a while. <Laugh>. Yeah. Eight more than 18 million terabytes <laugh>. So what is that 18 yacht aytes, or who knows? <Laugh>. so even though releases of spin right, tend to live for long time, we should be good for for
Leo Laporte (01:26:05):
A while. Yeah,
Steve Gibson (01:26:06):
I think we'll be okay.
Leo Laporte (01:26:07):
And you'll know where it'll look if, if suddenly 18 yaa bite drives come out, you'll know that's right. You'll know to what To work on <laugh>
Steve Gibson (01:26:14):
Since this bug is already long gone from spin, right? One since spin, since 6.1 it's so vastly superior to six oh is nearly finished, will be free to all six oh owners. And since this is, this is never destructive to any spin right. Users data, I plan to get six one finished rather than delay it in an attempt to announce this patch to all of six zero's current owners. After I put all this online Sunday night, I updated Greg so that he'll be pointing anyone who encounters this problem to the patch. And when I do announce six one, I'll also inform six OH'S users of this patch so that they'll have it for six oh, just for the record, even though it will largely become obsolete as will 6.0. So a big public thanks to Paul Farr for his terrific work on this.
Leo Laporte (01:27:05):
Wow, that's
Steve Gibson (01:27:05):
Nice. One final, just a
Leo Laporte (01:27:06):
Fan, right? Yeah. Not just a user. Yeah.
Steve Gibson (01:27:09):
Yep. J just a very, a talented coder. One final point, something else I'd forgotten from 19 years ago, which recently came to light, was that for a couple weeks after Spin Wright's initial public availability LA is first time that it went online, I was still finding and fixing some final bits of debris. No showstoppers apparently, or I would've made a big deal about it. I mean, I was po posting publicly in the news groups about this. Everyone knew but I was updating spin right's downloadable code on the, on the fly. I didn't have the mature version stamping system that all of my recent work carries, and which spin right? Six one will have. So all of those early additions, just say 6.0 without any indication of any subversion or build number, nothing has changed since in 19 years. But if you believe that you may have downloaded six Spin, right? Six within weeks of its first release in 2004 and never again since then, you might wanna update your copy until six one is ready. I'm just saying. And Leo, let's take our last break and we're gonna look at the emergence of voice cloning as a service for, you know, the nado, Wells
Leo Laporte (01:28:38):
<Laugh>, something we've needed for so long. So glad I did the voice cloning. And Apple's gonna offer this as well, but it was for a good reason. If you have ALS or some other debilitating disease and you can't talk anymore, it's good to record your voice now like Stephen Hawking had, so that if, if you
Steve Gibson (01:28:56):
Wish, apples gonna, Apple's gonna announce this,
Leo Laporte (01:28:58):
They did announce it, it'll be in the next version of iOS, and there's a company called a acapella. I just did this with acapella. You record in the case of acapella, about 200 phrases, like, could somebody open the window and please be patient. I'm typing this. It does it in your voice, the idea if you have to use a voice. Synthesizers Hawking did he was intentionally chose a robotic voice, but you could use your own voice in the theory being one that would make it be a little more appealing. It's not good enough. At least I don't, I haven't heard the Apple one. Acapella is not good enough to fool anybody but the Apple one, you know, it's Apple. It might be well, wouldn't be surprised. Well, we know where
Steve Gibson (01:29:39):
This is going, Leo. Oh, sure. It's be good enough. Sure. It's better
Leo Laporte (01:29:41):
Be good enough to cool anybody. Oh, sure. Hey, let's talk about our sponsor for the show this week. Oh, I have the wrong ad copy in front of me. I wanna talk about Lookout. Let me get, look out, look out. I want to get the right. I
Steve Gibson (01:29:57):
I assumed that Hawking was using that because he'd had it for so long. No, he chose
Leo Laporte (01:30:01):
Then he chose, yeah. That's interesting. And I can't remember the rationale. It was because, because it's creepy. Yeah, he, I think he didn't want it to sound like him. He, he wanted people to understand it's a synthesized voice. I'll look it up. I remember this conversation. Well,
Steve Gibson (01:30:19):
You're, you're good with your facts, so I'm
Leo Laporte (01:30:21):
Sure you're right. We also talked about it on Sunday because one of our guests had tried the Apple product and was talking about that. [inaudible] Brought to you by Lookout. As I mentioned, business is changing. It's changed dramatically, and it's probably changed forever because we work e everywhere, right? The boundaries to where you work or even how we work have disappeared. You can thank the pandemic, but now that employees have tasted freedom, you can count on it. They're gonna be moving around. That means your data is gonna be moving around with them, whether it's on a device in the cloud, across networks, or at the local coffee shop. While that's great for workers it's a challenge for IT security, of course, that's why you need lookout. Lookout helps you control your data and free your workforce. With Lookout, you'll gain complete visibility into all your data so you can minimize risk from external and internal threats.
(01:31:21):
Plus ensure compliance. That's really important these days. By seamlessly securing hybrid work, you don't have to sacrifice productivity for security. Look how it makes it security a lot easier. You're working with multiple point solutions and legacy tools in today's environment. That's just, that's a recipe for disaster as you say. Steve, what could possibly go wrong? <Laugh>, look out, has a single unified platform with everything you need to reduce it complexity to give you more time to focus on whatever else is coming your way. Good data protection doesn't have to be a cage can be a springboard letting you and your organization bound toward a future of your making. Visit lookout.com today to learn how to safeguard data secure hybrid work and reduce it complexity. That's pretty, pretty good. Goals. Lookout, L O O K O u t lookout.com. We thank Lookout so much for support and security. Now, you know, people understand when you buy an ad on this show, you are getting the best. You're, you're not just the best show. You're getting the best audience people who really pay attention to this stuff. So thank you Steven. Thank you. Lookout on, I know from
Steve Gibson (01:32:35):
Our com, I know from our communication with our audience. I mean, it's, it's a great high end group.
Leo Laporte (01:32:42):
Oh, they're sophisticated. Absolutely. Yeah, yeah, yeah. Very smart.
Steve Gibson (01:32:47):
Okay, so I suppose it was inevitable if we follow the, anything that can be done will be done rule. My original title, as I mentioned for today's podcast, was News Views and No Snooze. And I think that's been delivered <laugh>, which I felt was, you know, not particularly inspired, but accurate. That was right up until I hit upon the news that the barrier to entry for malicious voice cloning had just dropped with the inevitable in retrospect, appearance of voice cloning as a service. So, although today's coverage of this will not be a deep dive, I thought it merited some special attention. Thus, we gave it the title of the podcast last Thursday. The security firm recorded Future published a 16 page Cyber Threat analysis report, which was titled, I Have No Mouth and I Must Do Crime. A link to this full PDF is in the <laugh>.
(01:33:47):
It's great title, yes, I have no mouth that I must do crime. I've got a link to the pdf in the show notes for anyone who wants to read the whole thing. But the, it's a lot got lots of detail. I'll just share the executive summary which, which, which, which it leads with. They wrote Deep Fake Voice. Cloning technology is an emerging risk to organizations, which represents an evolution in the convergence of artificial intelligence threats when leveraged in conjunction with other AI technologies such as deep fake video technology, text-based large language models such as G P T, generative Art and others, the potential for impact increases. Voice cloning technology is currently being abused by threat actors in the wild. It has been shown to be capable of defeating voice-based multifactor authentication, enabling the spread of misinformation and disinformation, and increasing the effectiveness of social engineering.
(01:34:47):
We are continuously monitoring the emergence of deep fake technologies and their use in cyber crime. As detailed in our April 29th, 2021 report, the business of Fraud, deep Fakes, fraud's Next Frontier, as outlined in our January 26th, 2023 report, I chatbot, open source or freemium AI platforms lower the barrier to entry for low skilled and inexperienced threat actors seeking to break into cyber crime. These platforms, ease of use and out of the box functionality, enable threat actors to streamline and automate cyber criminal tasks that they may not be equipped to act upon otherwise. Many of the voice cloning platforms referenced in this report are free to use with a registered account, thus lowering any financial barrier to entry for threat actors. For those that are not free, premium prices are available. Rarely more expensive than $5 per month Voice cloning samples that surface on social media messaging platforms. Dark web pla sources often leverage the voices of public figures such as celebrities, politicians, and internet personalities, you know, influencers and are intended to create either comedic or malicious content.
(01:36:08):
This content, which is often racist, discre, discriminatory, or violent in nature, enables the spread of disinformation as users on social media are sometimes deceived by the high quality of the voice cloning sample. This proof of concept work shared by threat actors has inspired a trend on dark web and social access sources with threat actors speculating about the emergence of voice cloning as an attack vector. Conversations among threat actors often reference executive impersonation, callback scams, voice phishing, now known as phishing and other attacks that rely on human voice. One of the most popular voice cloning platforms on the market is 11 Labs, prime Voice ai. Mm-Hmm. <affirmative>, a voice-based text tope software that allows users to upload custom voice samples for a premium fee. While there are a number of voice cloning platforms referenced in this report, such as Meta Voice, Speechify, and so on, 11 Labs is one of the most accessible, popular and well documented, and thus serves as the case study for this research.
(01:37:25):
Then they wrap up their summary with five bulleted key findings. First voice cloning technologies such as 11 labs lower the barrier to entry for inexperienced English speaking, cyber criminals seeking to engage in low risk impersonation schemes and provide opportunities for more sophisticated actors to undertake high impact fraudulent schemes. Second, currently the most effective use of voice cloning technologies is in generating one-time samples that can be used in extortion scams, disinformation, or executive impersonation limitations to the use of lo voice cloning technologies, especially for enabling real-time extended conversations and generating prompts and languages other than English mean that extensive planning is required for fraudulent operations with a higher impact. Third, threat threat actors have begun to monetize voice cloning services, including developing their own cloning tools that are available for purchase on Telegram and the merchants of of voice cloning as a service. Fourth, public interest in ai, including voice cloning technology, has prompted an interest on dark web and special access sources in AI platforms potential for abuse.
(01:38:49):
Threat actors are also interested in leveraging multiple AI platforms in concert, thus enabling the convergence of AI threats. However, not all threat actors are confident in their ability to leverage such platforms in their current state. Threat actors that do not have an expert grasp of the English language may have the greatest hesitation about using these new technologies. And finally, in order to mitigate current and future threats, organizations must address the risks associated with voice cloning. While such technologies are in their infancy, as these technologies will only get better over time, an industry-wide approach is required immediately in order to prevent further threats from future advances in voice cloning technology. And sadly, to that, I say, well, good luck with that. I went over and took a look@elevenlabs.io, which is their u r l e l e v e n l a b s.io. They call their web-based service Prime Voice ai quote, the most realistic and versatile AI speech software ever.
(01:40:04):
11 brings the most compelling rich and life-like voices to creators and publishers seeking the ultimate tools for storytelling. So we need to be clear that there are and will be all manner of public benefiting wonderful applications for this emerging technology. But that once again, as always, along with the good with the, with the good comes the bad. They mention applications, the Day 11 labs for storytelling, audiobooks, and news articles. They boast having indistinguishable speech quality. They claim our AI model is built to grasp the logic and emotions behind words. And rather than generate one by one, it's always mindful of how each utterance ties to preceding and succeeding text. This zoomed out perspective allows it to ate longer fragments convincingly and with purpose. And finally, you can do this without w you can do this with any voice you want. So I played a bit with their online tool, and I have to agree that it was producing far better, more believably human less robotic sounding speech than we normally hear from text to speech.
(01:41:33):
But I wouldn't say that it's at the point where it's gonna fool anyone who might be at all suspicious. As for cloning well-known voices under their voice lab, they say, voice lab is your creative AI toolkit. Clone voices from samples or clone your own voice. Our design entire, our design or sorry, or design entirely new synthetic voices from scratch. Our cloning model learns any speech profile based on just a minute of audio without additional training. And our generative model allows you to create completely new voices that never spoke before. And then at the bottom of the page, they do have a statement under the topic, ethical ai, where they write at 11, we believe that we should strive to make the most of new technologies, but not at all cost. As we develop them, we make every effort to implement appropriate safeguards which minimize the risk of harmful abuse.
(01:42:38):
With this in mind, we're fully committed both to respecting intellectual property rights and to actioning misuse. So I wanna end with this observation. A macro trend that we appear to be seeing with increasing frequency is that bad guys are now jumping onto and exploiting new technologies every bit as quickly as the good guys. Over the lifetime of this podcast, we have watched doing bad on the internet evolve from being a curiosity, perhaps a basement hobby into truly full blown industries under our watch. The Dark Web went from being a fanciable idea, you know, just a theory to a widely inhabited active and quite busy underground. So it's gonna be interesting to see what comes next.
Leo Laporte (01:43:48):
I mean, I don't know how you, you can't shut it down. It's not gonna stop. No. I there's
Steve Gibson (01:43:54):
No way. It's out of, it's like the genie that's out of the box. You,
Leo Laporte (01:43:57):
It's like deep fakes. It's like Photoshop. I agree. It's here. So what you've gotta do is just train people that you can't trust yes. Voices. Yes. Raise
Steve Gibson (01:44:08):
You a level of awareness that, that trust no longer means identity. I mean, the, the, the, the voice no longer means identity.
Leo Laporte (01:44:16):
I mean, Charles Schwab uses voice ID to log in. The companies that are doing that need to stop <laugh>. Yep. I would suggest I maybe, I don't know, I, but I think, you know, look, it's here. We use, we've used 11 labs to generate my voice. I I have a AI Leo that has my voice. Spotify just announced through the ringer that they're gonna have use AI voices to have host red ads that weren't read by the host <laugh>, but sound like they were,
Steve Gibson (01:44:47):
It'll be nice to have audiobooks being better.
Leo Laporte (01:44:49):
Oh yeah, they already are. Apple has AI generated audiobooks using very, I think, very high quality voices. They sound very good. And you could buy as you, if you look at the apple bookstore, the audio bookstore it'll say some of them, I can't remember exactly the wording, but it's, it's generated by a computer and they're very good. And, and that means there's a lot of books that would not have a, an audio version will now, which is great, right? As always, Steve, if you cover the, you know, what's the stuff, the changing world around us, this is the place to go to find out what's happening. Actually, when I say this, I, I mean a couple of places. One grc.com, which is Steve's website. He has, of course, the podcast there. He has even two unique versions of it. A 16 Kilobit audio version for the bandwidth impaired. Of course, the regular 64 Kilobit audio version and human written transcripts. Lane Ferris does these every week. And that, that's really nice to read along or to search. You'll all find, and the show notes are also there. You'll find that@grc.com. While you're there, pick up a copy of Spin, right? 6.0. Now with a new bug, do, do, do you, do you bug fist current downloads? Are they fixed?
Steve Gibson (01:46:02):
No, I, I it would patch take so much time to, to update the current build. We, we'll, we'll
Leo Laporte (01:46:08):
Just, and for a small number of users, I mean, it's not very common, I'm sure. Right?
(01:46:13):
grc.com spin, right World's best Mass Storage, maintenance and Recovery utility, 6.061 s coming, that will be fixed and that will be out soon. Steve's working hard on that. We also have copies of the show at our website, twit Do TV slash SN for security. Now, you can also find a YouTube channel dedicated to it. That's a great way to share little clips. If you wanna, you know, tell your friends about this voice, you know, speech synthesis and the dangers of it. Share a little clip from YouTube. Everybody has access to that. It's an easy way for them to, to, to watch or listen. We put the video up there and of course you can subscribe in your favorite podcast player. Just search for security now and you'll get it automatically as soon as Steve's done. On a Tuesday afternoon. We recorded Tuesdays around one 30 right after Mac Break Weekly.
(01:47:02):
So between one 30 and 2:00 PM Pacific. That's four 30 Eastern. That's 2030 ut utc. You can watch or listen live at Live TWI tv if you're watching Live Chat, live in our irc. And of course we really encourage you, if you're not already a member to join Club Twit, then you get your very own Discord dedicated to nerds everywhere. There's a Security Now channel, but there's channels for everything coding and everything else. Anything nerds or geeks are interested in. You also get ad free versions of all the shows. You wouldn't even be hearing this Plug for the Club. You get shows we don't put out in other places. For instance, we ever get Steve back in front of the microphones talking about vitamin D. We'll do that as a club special cuz I think that's something everybody would like to hear, that kind of thing. And more importantly, those seven bucks a month really help us, you know, fill in the gaps. But we're, we're ad supported, but the ads don't necessarily cover all the costs. So your contributions make a huge difference. If you'd like to help us out, go to twit tv slash club. Thanks in advance. We will be back next week for episode 9 25. Thank you, Steve.
(01:48:19):
Have a great week. <Laugh>. Actually, we're both waiting for each other. Yeah. See you next week. See ya. Hey there. Scott Wilkinson here. In Case you hadn't heard, home Theater Geeks is Back. Each week I bring you the latest audio, video news, tips and tricks to get the most out of your AV system product reviews and more you can enjoy Home Theater Geeks only if you're a member of Club Trip, which costs seven bucks a month. Or you can subscribe to Home Theater Geeks by itself for only 2 99 a month. I hope you'll join me for a weekly dose of home Theater Geek Two