Security Now 986 transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show
0:00:00 - Leo Laporte
It's time for security now. This episode with Steve Gibson blows the lid off of a number of my deeply held convictions. For instance, third-party cookies Does Firefox block them? No, no, even though they say they do. Does certificate revocation work? No, it turns out it never has. Steve explains, shows you how to test your browser. And then finally, yes, steve has another brand new freebie program. He wrote it over the weekend that you're going to find very useful. There's a lot of great stuff coming up. Next on Security Now Podcasts you love.
From people you trust. This is TWIT. This is Security Now with Steve Gibson, episode 986, recorded Tuesday, august 6th 2024. How, revoking it's time for Security Now, the show we cover, the latest security news, the show you wait all week long for. Here he is the man of the hour, steve Gibson, our host. Hi, steve, hey.
0:01:12 - Steve Gibson
Leo, it's great to be with you once again for well, the last episode we're recording in the Twit Eastside Studios the twit east side studios.
0:01:27 - Leo Laporte
I think a lot of people probably especially on this show listen and they won't notice any difference at all. There there will be no effect.
0:01:34 - Steve Gibson
No, yeah, even if you watch, I mean just as good, as it's always been pretty much the same, it's really it's it's mostly me that that's suffering from this.
0:01:45 - Leo Laporte
You're gonna have exactly the same experience. The listeners probably have 99 of the same experience. I'm the one who's gonna be all alone.
0:01:51 - Steve Gibson
Who's gonna bring me lunch I know, leo, it's just tough.
0:01:55 - Leo Laporte
I don't know I told lisa, you're gonna bring me a sandwich every day at one right? She said what are you crazy?
0:02:01 - Steve Gibson
we're gonna. We're gonna have to watch cats crawling around on you and there will be cats on the video there will be cats.
0:02:08 - Leo Laporte
So what's up in the uh in the news? Okay?
0:02:10 - Steve Gibson
so, uh, lots of good stuff. We've got a bunch of things that have been learned over the past week about what we the big topic from last week, which was this pk file exploit, the platform key misuse issue, and we're going to answer the question what is boot secure? That's the name of it. Is boot secure, and why? Does that sound suspiciously like a new piece of GRC freeware? Uh-oh? Then there's plenty of news on the third-party cookie front. What's going on with Firefox, and what position has the World Wide Web Consortium, the W3C standard setting body, finally taken on the third-party cookie issue After, as we know, chrome basically capitulated to? Okay, fine, I guess we're not going to be able to get rid of those. Basically capitulated to okay, fine, I guess we're not going to be able to get rid of those.
Also, now that we're a few weeks downstream of the CrowdStrike disaster, the attorneys have come out to play. What are we learning about the legal side of this massive outage? Things like limitations of liability and so forth. Also, I'm going to talk briefly about what's been going on, or what is going on with GRC's SecurityNow email system, and then we're going to finish thus the title how Revoking? By looking at DigiCert's recent mass certificate revocation event, why it happened, what happened did it matter was, was it necessary, and how does it compare to entrust's past behavior? So I think uh, lots of interesting, uh information and news for our listeners this week can't wait and of course, we have an apropos picture of the week.
0:03:59 - Leo Laporte
Yes, I did peak this time. I'm'm sorry. It's very funny. Our show today, brought to you by a brand new sponsor. Want to welcome ThreatLocker to the Security Now family. It should be a name, you know.
If zero-day exploits and supply chain attacks are keeping you up at night, that means, well, two things. One, you listen to Security Now every week, and the other, you're running a system that you know is vulnerable. Well, worry no more. You can harden your security with ThreatLocker, and you know. I was talking with the folks at ThreatLocker the other day and they mentioned that a client, one of their clients is a major airline that did not get shut down by CrowdStrike. They said, yeah, jetblue uses ThreatLocker to secure their data and keep their business operations flying high. Maybe some other airlines might have considered that.
This is what I love about ThreatLocker it's a deny-by-default approach to cybersecurity. It's proactive instead of reactive. Right, you block every action process and user everyone unless it's authorized by your team. It's the ultimate zero trust. Threatlocker helps you do this and provides a full audit of every action. So you've got risk management and compliance. Their 24-7 US-based support team fully supports you through the onboarding process and, of course, beyond. So it's very easy to implement, and this is what you need zero trust with a full audit trail.
Stop the exploitation of trusted applications within your organization. Keep your business secure, protected from ransomware Organizations across any industry. It's not just the airlines can benefit from ThreatLocker's ring fencing that's what they call it by isolating critical and trusted applications from unintended uses or weaponization, by limiting attackers' lateral movement within the network. In fact, if you think about it, this is what you need. Threatlocker's ring fencing was able to foil a number of attacks that were not stopped by traditional EDR. In fact, you know, you heard us talk about SolarWinds, the Orion attack, like all year in 2020. Didn't work on people running ring fencing from Threat Locker? Let me say that again, the SolarWinds Orion attack was foiled by ring fencing. That should, by itself, tell you why you need this.
Get unprecedented visibility and control of your cybersecurity Quickly, easily, cost-effectively. Threatlocker's Zero Trust Endpoint Protection Platform offers a unified approach to protecting users, devices and networks against the exploitation of zero-day vulnerabilities. It's the best way to prevent zero days Just block everything unless it's approved. Get a free 30-day trial. Learn more how ThreatLocker can help mitigate unknown threats and ensure compliance. Visit ThreatLockercom ThreatLockercom. This is defense done, right. Threatlockercom Threatlockercom. This is defense done right, threatlockercom. We thank them so much for their support of security. Now welcome you to the family Threat Locker. Some really good people doing great work. Now time for the picture of the week, steve.
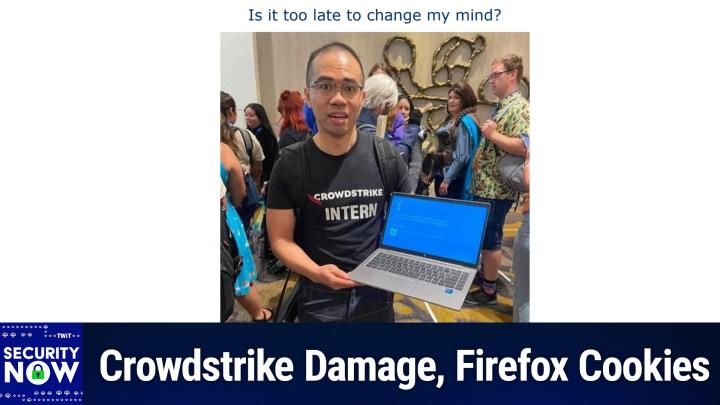
0:07:21 - Steve Gibson
So this was just a great picture one of our listeners sent me. I gave her the caption. Is it too late to change my mind? This shows a very unhappy person wearing a CrowdStrike intern t-shirt Obviously labeling him as a CrowdStrike intern. He's holding up a little laptop PC with the screen open and the frowny face your machine has just crashed blue screen and we can't really identify where he is. We don't. There's no obvious airportness about the background, except that there's a bunch of people who are kind of got carry on ish things and he is standing on industrial strength in destructo carpet that you, that you see in the airport where you know.
0:08:15 - Leo Laporte
So it it suggests that this you know that I've slept on that carpet a few times.
0:08:20 - Steve Gibson
I know that carpet, yeah, so it does it does look like this may be a have been an opportunistic shot. That was taken when his flight was canceled as long as well as everybody else's, and you know he turned his computer on. It's like oops, me too, yeah.
0:08:35 - Leo Laporte
Yeah.
0:08:36 - Steve Gibson
Yeah, so wow, I don't know that. I would recommend he changes.
0:08:40 - Leo Laporte
But where are that T-shirt with pride?
0:08:44 - Steve Gibson
That's a good point. You might want to turn it inside out for a while, Actually.
0:08:48 - Leo Laporte
I would love that T-shirt. Wouldn't you like to wear that T-shirt once in a while? That would be fun.
0:08:54 - Steve Gibson
Wow, it could be. I survived yeah.
0:08:57 - Leo Laporte
Yeah.
0:08:59 - Steve Gibson
Okay. So last week's discussion of Binerly's discovery that, by their estimate, the manufacturers of around one out of every 10 PCs, even those sold recently, have never bothered to replace the sample and inherently insecure platform key which AMI clearly marked as do not use and do not trust, has continued to bear fruit Over the weekend. One of the people in the news grew in GRC's news group discovered that one of his recently purchased Dell PCs I think it was last month he got this did indeed contain one of the insecure do not use platform keys. Now, since last week's podcast, I received a great deal of email from listeners and we'll be talking about a great deal of email and what that means a little bit later who were unable to get the command line that Binerly had supplied and which I quoted in the show notes and mentioned last week, to work. And I'm not surprised.
When I tried it myself, it was the definition of a mess UEFI commands. To work, which is one of the commands you must use. An extra, not normally present UEFI module must first be installed, so you have to do that, and then, since it needs this, the module apparently needs to run a script. The normally protective PowerShell script blocker must be disabled by disabling some of PowerShell's security. And then it turns out that if secure boot is not enabled, the command doesn't work at all. So if the machine is booted from BIOS rather than UEFI, you know it's not even working.
And then, to make matters worse, the binary command line silently checks the output text from the command, which you know I like, pipes it into a string finder. Well, the output might well be complaints about any of the above being a problem and needless, but even so, then a match is searched for the do not use, do not ship strings which will not be present in an error output. So, as a result, this will tend to return massively false, negative results, since any output which is not the platform key's actual certificate will not contain those strings. And so, even though the bogus AMI sample platform key's actual certificate will not contain those strings and you know so even though the bogus AMI sample platform key might be sitting right there on the motherboard, you would never know it. So long-time listeners of this podcast probably know where this is going. By Friday morning around 9 am, I had collected all of this feedback and tried using the command line myself. So I thought okay, this needs another one of GRC's little Windows apps.
0:12:15 - Leo Laporte
To let anyone this is why we love you, steve. This is amazing, unbelievable. I just got to write. I'll write it myself.
0:12:25 - Steve Gibson
That's right To let anyone quickly and easily get to the truth of what's going on. So I was all set up to continue working on Spinrite 6.1's documentation, which is my current focus. Since I need to get that behind me, I opened a new code project and began writing code to extract and analyze the motherboard's platform key and everybody could try it today, while I was doing that and publishing incrementally more capable pre-releases for the gang in the news groups to test, over the weekend we were also playing the name game, as we call it, that collective name. Brainstorming had previously resulted. Actually, it was from someone you know, leo Paul Holder. It had previously resulted. It was his idea to give the fake USB drive testing app, validrive, which I love yeah and, and oh my god, years ago somebody else came up.
I was working on that, that decom piece of freeware, and the guy said well, you have to call it the decomobulator.
0:13:37 - Leo Laporte
Yes, I do anyway, I thought you made up all these names yourself I think maybe all the other ones.
0:13:43 - Steve Gibson
Those are the only two. I think that I got from from the from trouble what was it trouble in paradise?
0:13:49 - Leo Laporte
oh yeah, that was mine.
0:13:50 - Steve Gibson
Yeah, that was the first one we talked about well, you and I and kate, on the, the old screen saver show yeah, in south san francisco yep tip, click of death, tip, you know, trouble in paradise. Yeah, move, I think you know, and opt out and all the other things those are my yeah.
But in this case I was coming up dry. So there was a lot of conversation with chat, gpt, among those in the news groups, lots of brainstorming. Finally, out of pretty much exhausted at the end of a long weekend of like endless names, we just settled on is boot secure, which you know it's kind of a good name I'm liking it yeah.
So if you go to grccom right now, there is an interim, working, fully working version of this. You can find it under the main menu, freeware Security, is Boot Secure or just grccom slash isbootsecure. It's currently a very small, dare I say, 21k, and actually about half of that is the signature that I had to give it. So you know, because it's got to be digitally signed, it's a little 21k windows executable that can simply be run on any windows machine, and I'm not sure about wine. Yet again, this is. This just happened. The paint is still wet on this and it will tell you exactly what's going on. And, leo, I see it there. Uh, you just ran it, apparently, or are you looking at the show notes?
0:15:20 - Leo Laporte
that might be that's in the show notes. Oh okay yeah, because I, I put I don't actually actually have a Windows UEFI machine. I could run it on.
0:15:29 - Steve Gibson
Anyway, it detects which firmware boot mode the system is in, bios or UEFI. If UEFI, it determines whether the UEFI firmware is in secure boot mode or not, which is not obvious, you know, unless you reboot. So it shows you that. And if secure boot mode is enabled and it's on some machines, even if it's not enabled it's then it will then extract which is to say if it's available, the platform key from the motherboard and display the certificate's most useful information the serial number, its issuer name and subject name. That's where the do not trust or do not ship strings will be found, if they're present, and it displays the certificates not valid before and not valid after dates just because they're kind of interesting.
0:16:17 - Leo Laporte
Did you put in the not valid after date yourself or is that the actual not valid after on one of your certificates? Actual not valid after on one of your certificates? Yeah, the why I ask that's four days before the end of the unix epoch.
0:16:32 - Steve Gibson
That's interesting, that is interesting yeah, it's not the epoch, which is the 19th, it's four days early I did not put that in, but that, uh, if the and I haven't looked at the certificate format, but it might be unix time in the cert, in which case I think it is yeah, it would make a lot of sense, wouldn't it? Very cool.
Good, good catch, leo when I see 2038, I'm yeah, here's perk up, yeah and you know, let's see how old will we be and what podcast will be on that I don't want to think about.
0:17:01 - Leo Laporte
Oh my god, it was. For people who don't know, unix time started january 1 1970, but it's a 32-bit, uh integer right. So after 32 bits it will roll over and, just like the y2k problem, and that turns out to be 3 14 am utc on 19 january.
0:17:22 - Steve Gibson
Well, that's only 14 years from now, Leo. So, we'll not be that old, we're only 80. At this point we're only a little over halfway there.
0:17:35 - Leo Laporte
Jerry Parnell used to come on the show in his late 80s. I think we could do it.
0:17:39 - Steve Gibson
Yeah, and you just have to somehow get up the stairs to the attic.
0:17:43 - Leo Laporte
Yeah, I need one of those little elevators. It's seven steps and I'll be ready to go.
0:17:50 - Steve Gibson
Okay, anyway. So right now this is just a Windows text screen which pops up. Oh, also, as an extra bonus, it displays the standard Windows certificate dialogue box containing your platform key certificate so that any of the other details of the certificate can be examined. For a while over the weekend, it was also exporting the certificate into a file, but since it didn't make sense to have it always doing that, I've turned that off for the moment. That'll be coming back. So what's available? Have it always doing that? I've turned that off for the moment. That will be coming back. So what's available right now does all that, but, as I said, it does it as a simple text window, since what I have was mostly meant as a tech development proof of concept.
What I'm going to do now, after starting this evening, after today's podcast, is turn this into one of GRC's standard little Windows GUI apps. So you know, I'll interpret what's going on to very clearly display the important bits and show the conclusion of what's happening to its user. And then, if you wish to view the full certificate, there'll be a button for that, and if you want to save it to a file, there'll be a button for that. So anyway, since this platform key mess is going to be a persistent and enduring concern, since there's no telling how long it's going to take to address these bad keys, if they are ever addressed. I felt as though this was exactly the sort of freeware app that GRC should offer. It can be downloaded as I said, right now it's just in its pre-release text window incarnation, but it works, and I'm sure I'll be announcing the final app on next week's podcast in a week.
So okay, so so much for PK fail. We'll briefly touch on it again next week. Let's talk about Firefox's third-party cookie mess and GRC's cookie forensics test. Two things are going on with Firefox and with what GRC's cookie forensics page shows. Part of the problem is that Firefox is being a bit, dare I say, foxy and appears to not have updated its user interface after it integrated its so-called total cookie protection into Firefox. There are no UI controls for it in evidence anywhere. There's a note about it in the UI, in a link, but you don't turn it on or off or do anything. So, as many people have noted, currently the only way to make GRC's cookie forensics test happy meaning to say oh yep, no third-party cookies at all to use firefox's custom setting and really forcibly turn off third-party cookies. Like we said last week, all that's correct. Um, at the same time, just turning off third-party cookies on other browsers works, whereas it sort of doesn't seem to with Firefox. So that's what brought this conversation up, the whole dialogue last week.
There are a couple of interacting things going on awareness of the inter-site third-party cookie isolation that Mozilla has now built into Firefox under the banner of total cookie protection, as I commented when the idea first surfaced. I think this is a really terrific idea. It potentially changes the game by stove piping cookie collections and aggregating them into their individual sites where they're being set. As Mozilla described it, instead of browsers having one big cookie jar that's shared among all websites, which is the way it's already been and has always been and of course, that's the reason tracking works is that the advertiser's cookie is in this big common cookie jar, which it's able to access no matter where the user goes. Instead, firefox creates individual, isolated mini cookie jars, one for every first party domain that a browser is visiting. So an ad tech company is welcome to place their third party cookie at site A. That cookie will be tagged with a Site A context and it will only be returned again when visiting Site A. So when a user visits another site where the same ad tech company is also using cookies, that ad tech company will not receive the cookie it set over on Site A, will not receive the cookie it set over on site A, so it will not know that this visitor is the same one who was over there viewing ads. So this is a huge change and it's a big win.
But I registered the independent domain, grctechcom, on New Year's Day of 2002 because I needed to have an unaffiliated third-party domain of my own available not a subdomain of GRC, because cookies know about subdomains. I needed an unaffiliated domain which I could build around a cookie forensics system, and back then there was no notion of the cookie site isolation that we have today with Firefox. As a consequence, firefox may well be isolating cookies by domain, but my 22-year-old test doesn't know about that. It's just seeing that Firefox appears to be very reluctant to fully disable third-party cookies. It can be forced to, but it doesn't really want to, and the reason Firefox can do this is because it has the site isolation trick up its sleeve.
What we're going to need in order to verify that site isolation is working and real is an updated cookie forensics test that's aware of the possibility that, while third-party cookies themselves might be enabled, they might not be shared with other first-party sites, and I don't recall why this was on my mind 12 days ago back on July 25th, because that was before last week's podcast, but the question of the need to confirm the presence of inter-site cookie isolation must have occurred to me since Hover shows that I registered another independent domain, grctechdev, on that Thursday I needed a second unaffiliated domain to create a second first party site to see whether it would be able to see the cookies that had been set by GRC techcom when visitors were at GRCcom.
So at some point in the not too distant future, I'll make some time, I'll dust off the cookie forensics site, figure out how it works because I knew 22 years ago and I haven't looked at it for a long time and then create an updated facility for the specific characterization of browser cookie handling which incorporates an understanding of inter-site isolation, since this seems like a good thing and clearly it's based on what just happened with Chrome and the EU or the UK, third-party cookie handling is going to be as important today as it was back in 2002, when I first got a bug about this and decided to fix it.
Okay, but there's more. It turns out that simply blocking all cross-domain third-party cookies can break things. A more nuanced approach is going to be needed, apparently, to create a real-world solution that does not cause more harm than good. I want to share Mozilla's discussion of this, since it helps to demonstrate how complex the web has become and also how dependent upon the details of its operation other services have become. And, leo, your timing is perfect, because this would be a great time to take a break. And then I want to share what Mozilla is explaining about the complexity of third-party tracking absolutely.
0:27:29 - Leo Laporte
I was taking the old server out to the car.
0:27:31 - Steve Gibson
I realized that I'm running as one does.
0:27:35 - Leo Laporte
I was running the web server and three mine four, five minecraft instances here and the other, and I realized, oh, I guess I better take that home. I hope I have enough bandwidth for your Minecraft enjoyment, but Club Twit members get to play in our little Minecraft sandboxes. Our show today brought to you by Delete Me something we know about we've used. I'll tell you why you need it. Have you ever searched for your name online? Don't do this, because what you'll see I mean, maybe you wrote an article for a magazine or something. You might see that but mostly what people see is a lot of personal information, sites that say who you are, what your address is, whether you're married or not. All of this stuff is online and available, and there are sites that sell it. There are a lot of them. Maintaining privacy, though, is more than just a personal concern. If you are a manager in a company my wife is the CEO of Twit you absolutely in fact, that's who we have Delete Me for. You absolutely need this for your executives, for your managers.
Twice now bad guys have used information gleaned from online data brokers to attack our staff. Using Lisa's name, her phone number, their names, they knew who her direct reports were and their phone numbers, sending them a text message saying I'm in a meeting right now, but I need $500 worth of Amazon gift card. Stat Mail them to this address In Nigeria. I don't know how that happened. Well, fortunately, our staff is smart. It wasn't Nigeria. But they were smart. They didn't fall for it. But the thing that scared me was all this information the bad guys knew about our management structure, our organization, people's phone numbers. That's when we subscribed to Deleteme. You should probably get this for your family too. Now you have to be an adult to use Deleteme, but if there are people in your family adults who are maybe not as technically savvy as you, you can use Deleteme to protect them as well. Deleteme helps reduce risk from identity theft, from cybersecurity threats like I just described, from harassment and more.
Deleteme's experts will find and remove your information from hundreds of data brokers and, by the way, there's new ones every day and they keep that list up to date. So they will go to each and every one of them day and they keep that list up to date. So they will go to each and every one of them, find and remove your information, get rid of it. But that's not all, because once you do that, great, okay, now that stuff's down. But they repopulate it, you know, as they get more information from all their many sources and your internet service provider might be one, your carrier might be another. Websites you visit, stores you do business with, they all sell that information on your TV set, your car. They're all selling that information on the data brokers, and the data brokers just repopulate the dossier. That's why delete me's.
Experts continue to go back again and again to remove your information, including addresses, photos, emails, relatives, phone numbers, social media, property value and on and on, and on and on. If you get the family plan, you're going to sign a unique data sheet to each family member, tailored to them. So you could say, yeah, the Instagram thing is fine, but you know she doesn't have any websites. That kind of thing was. With easy to use controls, account owners can manage privacy studies for the whole family, or your business, or your business I think, every business. Trust me, you need this for your management. Protect yourself, reclaim your privacy. Go to joindeletemecom slash twit. Use the code twit. It worked for us. Joindeletemecom slash twit. The offer code TWIT will save you 20%. Joindeletemecom slash twit. Now back to Steve and security now, okay.
0:31:36 - Steve Gibson
Okay. So if anyone wants a good example of the definition of a kludge, unfortunately we're about to encounter one. As I said, it turns out that simply blocking all cross-domain third-party cookies, like Mozilla's total cookie protection does it, can break things. So you need more nuance. Unfortunately, there's no clean solution, so get a load of this. This is Mozilla's explanation, which is titled Third Party Trackers, and they're going to explain to us what they've had to do.
They wrote cookies are invisible pieces of data that a website can ask your browser to store on your device. The next time you visit the same website, it can ask the browser to read that cookie. That's how a website can remember things such as your preferences for that website and that you're logged on. Another use for cookies is to transfer information from one website to another. For example, a sales website can store information about your purchase in cookies and redirect you to a payment or a review website. From the website's point of view, the cookies created by the sales website are called third party cookies. So the point is they're demonstrating there's a non-tracking use case for third-party cookies. Their websites, these libraries, can set cookies on your device too. If cookies are set by a library, that's on a different domain from the website's domain. They're also third-party cookies Again another use case, they said popular libraries are used by numerous websites. When you visit a website that uses a particular library, that library can set a cookie on your device. If you later visit another website that uses the same library, that library can set a cookie on your device. If you later visit another website that uses the same library, that library can read the cookie that was set when you visited the previous website. These third-party cookies set and read by libraries from multiple websites are called cross-site cookies. So they say there are two main reasons websites and libraries use cross-site cookies. So they say there are two main reasons websites and libraries use cross-site cookies.
Cross-site tracking is by far the most common use of cross-site cookies. Trackers use cross-site cookies to collect information about the websites you visit and send them to other companies, often for advertising purposes. When you feel like an advertisement is following you while you browse, this is the result of cross-site tracking. If the same tracker is present on multiple sites, it can build a more complete profile about you over time. The other type of cross-site cookie is a functional cookie. Some websites rely on these cookies in order to function properly. For example, some websites may need access to cross-site cookies to let you use their service to sign in to another website like Facebook login does this or to process a payment for that website. Amazon Pay does that.
Firefox's enhanced tracking protection they write blocks cookies from cross-site trackers and isolates cookies from all other third parties. This helps prevent your browsing activity on one website from being visible to other websites. Total cookie protection is now enabled by default. It's an advancement built into enhanced tracking protection that works by maintaining a separate cookie jar for each website you visit. They said. While cross-site cookies from trackers are blocked in Firefox by default, a site may signal to the browser that it needs to use them for important functionality. What, okay? In this case, firefox will allow a third party.
0:35:59 - Leo Laporte
Can I have those cookies? I know there's no functionality that third-party cookies could possibly implement it that I want yeah, I know, this starts to get really messy.
0:36:10 - Steve Gibson
So they said in this case, if a website says, oh, but sir, may I please have one? Uh, firefox will allow a third-party website to use cross-site cookies. Get this five times what? Oh, I know, leo.
0:36:28 - Leo Laporte
You got to use uBlock Origin, just block it all this is so bad.
0:36:34 - Steve Gibson
So they said, in this case, if a site asks, firefox will allow a third-party website to use cross-site cookies five times or I'm not making this up or up to one percent of the number of unique sites you visit in a session. Whichever of the two is larger where'd they get that?
from. I know it gets worse without prompting you. After that, firefox will prompt you to block these cookies. What? Without your consent, Firefox blocks these cookies from that point because a site requesting access that many times may be a tracker. Okay, Now just to interrupt this horror for a moment. The first time I read that I had to go back to make sure I'd read it correctly. I thought what? This is my browser, my browser.
0:37:34 - Leo Laporte
You can't do this to my browser. You know where some of this comes from. I think is at least in the EU and the UK. Advertisers and sites are complaining. This is why Google says we had to stop. You know, we know. Implement this change, yeah, and I think that Firefox is concerned about getting attacked in the EU by the government yeah because advertisers are complaining and, uh, it's very disappointing.
0:38:03 - Steve Gibson
It is Okay so, leo, it's going to still get worse. Okay so, but first let me just make clear. This means that Firefox now blocks cross-site cookies by default. They're also providing websites with a mechanism by which to ask to please have cross-site cookies turned back on, but only just a little I'm only a little pregnant, tiny, tiny bit.
It's just a flesh wound, presumably only enough to accomplish some specific task that needs to communicate with cookies across sites, so apparently they understand that if this was just a blanket request, then websites would eventually all claim to need it all the time. All the time they just add you know, it's like the do not track who is asking for it, though. Is it the third party? Yes, it's the time all the time they just add you know, it's like the do not track it'd be oh, who is asking for it, though?
0:39:05 - Leo Laporte
is it the third party? Yes, it's a third party. Yes, so it's so if you're going on a site, you go to a starbucks site, and they have a facebook thumbs up like button, facebook, which owns that button, could say oh, please leave these tracking cookies on, because oh, leo, it gets even worse because firefox makes exceptions based on the domain that's asking.
0:39:28 - Steve Gibson
Oh, I know, it's so bad.
0:39:31 - Leo Laporte
It's so bad, okay, really they're doing this so that they can still have that checkbox that says block third-party cookies, because they know people look at that and they won't have read this white paper, so they won't be. They'll think they're blocking third-party cookies when they're not, and that bothers me even more, right?
0:39:46 - Steve Gibson
It's deceptive, right? Well, that's. What we discovered last week was that GRC's forensics was saying what I got? A bunch of red bubbles here saying that it's not being blocked, even though it says it is not being blocked, even even though it says it is so. So presumably they they mozilla have done some testing of this and they've decided that no website has a legitimate need for more than one or two. So they added some margin and set it at five before they surface a dialogue to the user.
Now, what is the user going to do about this? Like, wait, what Do I say? Yes or no? And then they also look at the number of unique sites visited during a session of a browser use. Then take the larger of either five or 1% of the unique sites count during that session. So that means that the breakeven point would be after visiting 500 different sites, right. Then, once you visited another 100, then 1% of 600 sites. Total would be six requests that are allowed Can't allow that. So I suppose this means that if anyone is using their browser like crazy, the site they're visiting might need a bit more leeway, but a bit more is all they're going to get. Might need a bit more leeway, you know, but a bit more is all they're going to get.
Now, if all of this sounds like a horrendous mess to you, our listeners, that I would say you've been paying attention, because this is a horrendous mess. This sort of heuristic is not the way the Internet and the Web were designed. The Internet is as robust as it is because it doesn't have any sort of this nonsense. You know, it was designed with clear, clean and simple rules, which is, I would argue, why it's done as well as it has, you know. But this allows sites to request an exception, but not too many times. You know, it's the very definition of a kludge. I'm surprised they're not just tossing a coin Heads. You can use a cross-site cookie Tails. Ah, sorry, better luck next time. Anyway, they continue by writing this is Mozilla.
Third parties will only be able to prompt you if you interact with the website. You are on, okay. For example, if you visit dogscom and select the payment field, amazon Pay, cross-site cookies may be allowed to facilitate that transaction. After that, firefox will ask if you want to keep allowing them Again. And they say you can view the permissions panel to see if a website has been allowed or denied permission to use cookies by clicking the permissions icon in the address bar. So now there's going to be a new permissions icon in the address bar. Now there's going to be a new permissions icon in the address bar. If you deny the request, the third party will not be able to use cross-site cookies during that session. But if you refresh or reload the page, the third party may prompt you again. From the permissions panel for a site. You can click the X or revoke previously allowed access to cookies. Wow.
So website visitors, who have no idea what's going on behind the scenes, are being expected to make on-the-fly allow-deny decisions about whether or not the third party appearing at any given site should be allowed to use cross-site cookies. This is going to be interesting, they said. Firefox automatically allows third-party websites to use cross-site cookies on the first five or so websites you visit. So websites you visit, for example, amazon Pay would be able to use cookies on Old Navy, blick, dogcom and a handful of other sites without asking you for permission. But oh, I guess that means if you encounter Amazon Pay a sixth time during something a session, then, whoa, wait a minute. Do you want to allow this because you've been using it a lot? Wow, if a third party continues, they're saying they write.
If a third party continues to use cross-site cookies across multiple sites, this becomes a signal to Firefox that the third party might be a tracker.
At that point the third party would have to prompt you to ask for permission to use cross-site cookies, they said, and they actually used the word heuristics. There are other rules, they said parens in quotes heuristics that will make Firefox temporarily grant access to cross-site cookies to certain websites. These rules are designed to enable special use cases, such as single sign-on services, and usually require some special interactions, such as a top-level redirect or a user interaction, making it difficult for trackers to exploit them. Okay, so, boy, it is a tangled mess. Presumably, these heuristics that Mozilla is talking about for Firefox are things like Firefox knowing in advance the domain names of large single sign-on providers, so they automatically get special permission and can use cross-domain cookies without limit because that's their legitimate business purpose. So now that puts Mozilla in the position of deciding whose business model will and will not receive more permissive treatment under Firefox. I mean, we're losing the browser that we have always loved.
0:46:16 - Leo Laporte
What's happening is…. Thank God for Gorehill. I don't know what we will do. He better not die, or anything.
0:46:21 - Steve Gibson
Well, he did post recently that he's about to be in trouble with uBlock Origin, but not over on Chrome.
0:46:31 - Leo Laporte
Yeah, it won't work with Manifest V3. That's correct.
0:46:34 - Steve Gibson
So you know at least we do still have Gore Hill here on Firefox, and I'll be talking about that next week. So what's happening is that the industry is now tying itself in knots because cross-site information sharing we want and cross-site information sharing we don't want are using the same mechanisms. Mozilla's third-party tracker explanation begs the question. In light of this, how could Chrome's privacy sandbox designers have possibly imagined the elimination of all cross-site third-party cookies? Mozilla has just finished telling us all the reasons that you can't eliminate them, because they're having to poke a whole bunch of holes in this in order to keep things working. So, annoying though it may be to purists, mozilla highlights some compelling use cases which have arisen for needing cross-site information sharing in some form, sometimes okay. So the w3c finally weighs in. Amid all this, the world wide web consortium, the w3c, has finally weighed in on third-party cookies. So just to remind everyone and update everyone on the W3C, wikipedia's first sentence or two says the World Wide Web Consortium, w3c is the main international standards organization for the World Wide Web, founded in 1994 and led by Tim Berners-Lee and this is after he left CERN. The consortium is made up of member organizations that maintain full-time staff working together on the development of standards for the World Wide Web. As of March 5th 2023, the W3C had 462 members. The W3C also engages in education and outreach, develops software and services as an open forum for discussion about the web. So you know, these are the guys that are defining the APIs that our browsers support and the standards that makes the World Wide Web go About.
A week and a half ago, on July 26th, the W3C's official statement was titled Third-Party Cookies Must Be Removed. Okay, that's never been said before. Third-party cookies must be removed. The article's abstract says Third-party, aka cross-a, cross-site cookies are harmful to the web and must be removed from the web platform. This finding explains why they must be removed and examines the challenges in removing them. So a finding is what they're calling this thing that they published on July 26th. It examines the challenges in removing them. So a finding is what they're calling this thing that they published on July 26th. It examines the challenges in removing them. We highlight some use cases that depend on third-party cookies and offer some examples for designed for-purpose technologies that can replace them. In other words, instead of overloading in in an object oriented sense, like using cookies for the purpose they were never intended, the web is going to come up with designed for purpose technologies, replacement technologies that don't track, don't allow tracking, cannot be abused and will allow third-party cookies to be terminated. So they write specification authors are expected to ensure they do not undermine the benefits of removing third-party cookies when proposing new web platform technologies, and their introduction.
Here is interesting because they call out Chrome. They write we consider privacy to be a core design principle and differentiator for the web platform. Many browsers have restricted third party cookies. They said parens, see WebKit and Mozilla. They said, unfortunately, not C, webkit and Mozilla. And they said unfortunately, not all browsers have followed suit. And at that point they had a link to the article that the Privacy Sandbox Group had published four days before this, which acknowledged that third-party cookies would not be removed from Chrome. Okay, so TAG is their abbreviation for their technical architecture group, tag. So the piece continues TAG calls for all browsers to drop support for third-party cookies, as this provides an opportunity to further improve the privacy-preserving features of the web platform.
Removing third-party cookies from the web platform is not without complications. There are use cases for third-party cookies that need to be preserved and pitfalls we need to be careful to avoid in doing so. This document sets out some aspects that specification editors and implementers should be aware of in order to make sure we ultimately leave the web better than we found it after third-party cookies are removed. Okay, so this all sounds wonderful. This might be significant. If nothing else, it likely provides some cover for any browsers that wish to move in this direction. There's now an official position from the Internet's major web standards body unequivocally calling for the end of third party cookies. They're they're from the web platform, and we embrace the opportunity to improve the privacy features of the web. When we review new technologies to replace third-party cookies, we need to ensure that the replacements do not recreate the same pitfalls to privacy. Do not recreate the same pitfalls to privacy.
The TAG considers each new technology proposal both individually and as they fit together with the web platform as a whole. The web must be cross-platform, so multi-implementer, multi-browser support and developer support for privacy-related specifications is essential if they're going to achieve the goal of increasing privacy on the web. When we consider whether something makes the web platform better, we should be explicit about what that baseline for comparison is. Is a proposal better for privacy when compared to usage of third-party cookies or when compared with a web free from third-party cookies altogether? What about when some user agents restrict third-party cookies but others do not? We want to emphasize that, as any replacement proposals, progress implementations should have a strong commitment toward, and reasonable timeframe for, removing third-party cookies. We are also wary of new mechanisms being introduced that could be abused together with cookies, fingerprinting, surface or other tools for greater privacy invasion.
Given this context, we see an urgency to have a strict timeline for the removal of third-party cookies. We are strongly in favor of innovations to build sustainable business models on the web platform, but an in-depth discussion of the various possibilities are outside the scope of this document. From an architectural standpoint, web standards should avoid encoding particular business models which unfortunately, mozilla has just done that are available to authors, publishers and web content creators. In conclusion, when accommodating changes caused by the removal of third-party cookies, we should avoid introducing new technologies that, when deployed either individually or in combination, effectively preserve the status quo of harmful tracking and surveillance on the web. Okay, so I could certainly be reading too much into this. I'm not nearly enough of an insider to be able to venture a guess about what this might actually mean for changes in the future, but boy does it sound good.
You know they're using all the right words, and I think what this is saying is that those organizations, those entities like Amazon Pay, that are aware they are used, they're dependent upon third-party cookies, need to get serious about working with the emerging standards, and the W3C did mention a handful of them. Among them was Chrome's Privacy Sandbox, but it turns out there are others. There is other work in progress, not from a single company, but from multiple standards bodies that will provide a solution, so forth would switch to using a non-third-party cookie standard, thus protecting themselves from the end of third-party cookies, which the W3C is now calling for. So this lays out a template for the shape of the future approaches that would have a chance to succeed. You know they said we are strongly in favor of innovations to build sustainable business models on the web platform, and of course, we know what that means, right? That means that you know sustainable business models well. On one hand, amazon Pay and using the web and third-party authentication for logon probably also means that, like Google, they understand that advertising powers much of the Internet and that targeting ads makes those ads enough more effective that it can, as we've seen, double a site's revenue from advertising.
At the same time, I lost count of the number of times they used the word privacy. So it's clearly not their intent for anything like the status quo to remain. But will anything change? And it's definitely worth repeating what I noted last week, which is that there are significant enterprises employing many people whose entire purpose is to deliberately and surreptitiously violate the privacy of everyone who ventures out onto the Internet with their computer. You know, that's exactly what it is, right, you know. And these days, who doesn't venture out on the Internet with their computer? And equally unfortunate is the fact that these enterprises have paying customers who have some use for the aggregated private data of individuals, which is to say all of us. So this W3C action of very clearly working toward putting an end to third party cookies can be expected to see more opposition. You know, much as it appears, happened with Google in Europe.
0:58:28 - Leo Laporte
What is the they said in there? There are uses of third-party cookies that are legit. I'm racking my brain.
0:58:35 - Steve Gibson
So apparently and I didn't dig into it, but apparently Amazon Pay is using third-party cookies in order to link itself so this is the case and you do this too.
0:58:49 - Leo Laporte
It's not unusual for a site to have images from another server, to have data from multiple servers, so those servers would look like third parties when you're on a first party page they're by definition, they are third party, are literally yeah yes, so that makes sense.
So that's probably some sort of related thing where, well, I need to set a cookie from the image server so that I, you know, don't send you that image again, or whatever. But it's not going to come from this page because I'm a first party right, so so there might be, I could say that yeah right, there are.
0:59:22 - Steve Gibson
There are non-tracking, you know, currently legitimate applications now and so, and so their point is we that cookies have have been used legitimately because they're there. Right, I mean again, third-party cookies are being used to to create these, these interain connections, just because they're convenient. They're there, but it would be possible for a site like Amazon Pay to use a designed-for-purpose, a non-third-party cookie solution. Yeah, that makes sense. That's what the W3C is calling for is an alternative technology that everybody who currently is using third-party cookies for good will be able to switch to. So then third-party cookies can be turned off, and the problem is lots of companies are using them for for privacy invading purposes, and they're going to fight back right and and they use listening because they say well, these are advertising.
1:00:37 - Leo Laporte
These are, these are uh journalists.
1:00:40 - Steve Gibson
they say they're the businesses. Yeah, For advertising. Yeah, they have. You know, little babies they have to feed. I was like okay.
1:00:47 - Leo Laporte
So really it's a conundrum, it really is, but I can see now. Yeah, there are lots of servers, many servers you go to now, who have multiple endpoints, and those are all third-party endpoints, except for that one main server. So that makes sense. Those are all third-party endpoints, except for that one main server. So that makes sense.
1:01:04 - Steve Gibson
I could see that that's those JavaScript things. Everybody loads things like that. Yeah, time to take a break. And then we're going to update on what has happened to CrowdStrike as a consequence of that little problem a couple weeks ago.
1:01:18 - Leo Laporte
I'm curious you think anybody's upset.
1:01:20 - Steve Gibson
Leo, you think anybody called their attorneys.
1:01:25 - Leo Laporte
We should preface that, as you did a couple of weeks ago when we talked about this, with the fact that, up till then, CrowdStrike was a very well-known, very well-respected security firm. They did a lot of important research on the internet.
1:01:39 - Steve Gibson
Actually, Leo believe it or not, one group of I don't know what it is going on. They're actually suing because their reputation was so good. They're saying you misled us. Yes, you made all that money for us because you were just pulling the wool over our eyes.
1:02:01 - Leo Laporte
Yeah, you were so good until you weren't Wow, that does happen. Of course, none of our sponsors are like that. We only have the best hand-selected sponsors, like these folks at Big ID, who I had a great conversation with a couple of weeks ago. They are the leading DSPM solution Data Security Posture Management and they do it a little bit differently. Dspm centers around risk management, you know, keeping an eye on how organizations need to assess and understand and identify and remediate data security risks across their data.
Big ID is special because it works across your tech stack. It is designed for situations that many of you have where you're in a heterogeneous network, where your data is in multiple places. The US Army Training and Doctrine Command uses them and if you think about anybody whose data is in multiple places, it would be the US Army right. Multiple places, it would be the US Army right. Dspm Big ID seamlessly integrates with your existing tech stack, allows you to coordinate security and remediation workflows and, because data lurks all over the place, you can uncover dark data, you can identify and manage risk, you can remediate the way you want, the way that works for you, and you can scale your data security strategy, take action on data risks, annotate, delete, quarantine and more based on the data, all while maintaining an audit trail. More and more. That is critical to this right, and some of the best people, some of the biggest partners, use DSPM from BigID ServiceNow, palo Alto Networks, microsoft, google, aws and more. All use BigID and the US Army. With BigID's advanced AI models, you can reduce risk, you can accelerate time to insight, you can gain visibility and control over all your data.
So let's talk about this Army thing, because it's really interesting. They equipped the US Army Training and Doctrine Command to illuminate dark data. There was a lot of it, because, I mean, this is a perfect example of a data enterprise that's been around for decades, right? So as things evolve, new technologies emerge, old technologies, legacy technologies, live on. Your data gets fragmented. It's in a lot of different places. They were able to help the Army accelerate their cloud migration, minimize redundancy and automate data retention. This was a big job. That's why a big ID was there.
Here's the quote from the US Army Training and Doctrine Command, the quote, the first wow moment. That's right there. Some generals are going, wow, I had a wow moment. The first wow moment with Big ID came up with just being able to have that single interface that inventories a variety of data holdings, including structured and unstructured data, emails across all the emails, zip files, sharepoint databases and more. The Army goes on to say to see that mass and to be able to correlate across those is completely novel. I've never seen a capability that brings us together like Big ID does. Wow, that's an endorsement. That's fantastic.
Cnbc recognized Big ID as one of the top 25 startups for the enterprise. They were named to the Inc 5000 and Deloitte 500 for two years in a row. They are the leading modern data security vendor in the market today. You need to know these guys. The publisher of Cyber Defender Magazine says quote Big ID embodies three major features we judges look for to become winners Understanding tomorrow's threats today providing a cost-effective solution and innovating in unexpected ways that it can help mitigate cyber risk and get one step ahead of the next breach.
Start protecting your sensitive data wherever your data lives at bigidcom slash security now, in fact, go to the website and see the testimonials. They're kind of mind-boggling. The people who use BigID love BigID. You can even get a free demo there to see how BigID can help your organization reduce data risk and accelerate the adoption of generative AI. Yeah, they can help with AI too, because one of the big problems with AI Army faced this is you want to train on some things, but not everything. How do you control what the AI sees doesn't see? What are the rules? How do you know if the rules are being followed? That's what BigID can help with.
Bigid, bigidcom slash security now, they also have a lot of white papers there. If nothing else, they're a great information resource. There's a free report that provides valuable insights and key trends on AI adoption, the challenges and overall impact of generative AI across organizations, one of the many things that you can get there for free. Bigidcom slash security Now, big ID, it's a big idea. Get it. Yeah, thank you, big ID, for your support. We really appreciate it. All right, steve, let's talk about the sad tale of CrowdStrike.
1:07:24 - Steve Gibson
Well, predictably yeah, predictably the lawsuits and class actions have started up in the wake of CrowdStrike's little bitty problem. Little thing Did anybody notice that? I think that some details of them would be of interest to our listeners. Of them would be of interest to our listeners. The first is a shareholder lawsuit blaming CrowdStrike for the entirely predictable significant drop in the company's stock price. Apparently, the Plymouth County Retirement Association of Plymouth, massachusetts, now regrets having invested so heavily in CrowdStrike. The coverage of this, after removing the redundant stuff that we already know. It says.
Austin based cybersecurity firm CrowdStrike is facing a class action lawsuit from shareholders who claim the company defrauded them by concealing how its inadequate software testing could cause a global computer outage, resulting in a big hit to the share price and overall market value. According to the July 30th complaint filed in the United States District Court in the Western District of Texas, in the United States District Court in the Western District of Texas, crowdstrike's chief executive, george Kurtz, characterized CrowdStrike's Falcon software as validated, tested and certified during a conference call on March 5th. The plaintiffs say these statements were false and misleading because CrowdStrike allegedly failed to provide to properly test and update. Actually, they did update and that was the problem Allegedly failed to properly test and update its Falcon software before rolling it out to customers. The complaint alleges CrowdStrike, quote instituted deficient controls in its procedure for updating Falcon and was not properly testing updates to Falcon before rolling them out to customers. Ok, I think everybody would agree with that. Crowdstrike did not disclose that quote. This inadequate software testing created a substantial risk that an update to Falcon could cause major outages for a significant number of the company's customers. Unquote. The complaint alleges quote such outages could pose, and in fact ultimately created, substantial reputational harm and legal risk to CrowdStrike.
As a result of these materially false and misleading statements and omissions, crowdstrike stock traded at artificially high prices during the class period. Ok, so they're. They're upset over the terrific management, operation and reputation of CrowdStrike before the event that had presumably made them so much money. And now they're suing because what was once overly inflated is apparently no longer. The article notes that quote.
Following the outage, the legal complaint says CrowdStrike's share price fell 32 percent over the next 12 days, wiping out $25 billion of market value. As of July 31st, crowdstrike shares are worth $231.96. They closed at $343.05 on the day before the outage. The lawsuit led by the Plymouth County Retirement Association of Plymouth, massachusetts, seeks unspecified damages for holders of CrowdStrike Class A shares between November 29th of 2023 and July 29th 2024. 23 and July 29th 2024. The class action also alleges that Delta airlines hiring of an attorney to represent them in seeking damages from the country, along with Kurtz's being called to testify before the U S Congress over the incident, caused crowd strikes share price to fall. So they're also unhappy that other things that allegedly hurt CrowdStrike's reputation or also hurt the stock price. Ok, the article says CrowdStrike said in a statement provided to media outlets we believe this case lacks merit and will vigorously defend the company. Speaking at the time of the outage, crowdstrike chief executive George Kurtz said we identified this very quickly and remediated the issue period. He added that its systems were constantly being updated to ward off adversaries that are out there. Okay, so that's the first of the entirely predictable legal actions that are underway.
The second one surrounds the excessive degree of damage caused by, or caused to, rather, delta Airlines. As we know, whatever it was that happened to, delta kept many of their flights on the ground far longer than any of their other competitors who, you know, like most of the rest of the planet, removed the bad file, rebooted the machines and resumed operations, but not Delta. Something happened at Delta just yesterday, on on Monday, just yesterday on Monday, the publication CIO Dives headline read CrowdStrike rebukes Delta's negligence claims in a fiery letter. And the subhead of their piece was after the airline said it was considering legal action. Crowdstrike said Delta's contract capped the cybersecurity provider's liability to single digit millions. They didn't get, they weren't any more specific. But sorry folks, the five hundred million dollars you're claiming in damages we're not going to get there with our contract. Okay, so the article says CrowdStrike struck back forcibly against Delta Airlines claims of negligence and misconduct in a letter sent Sunday, just last Sunday, to the firm representing Delta Airlines, signed by attorney Michael Karlinsky. And I should mention, leo, that he addressed the letter to David Boise's, so you know some high-power legal talent there. So this is the latest in what has become a public dispute, that is, between Delta and CrowdStrike.
Following recovery from the global CrowdStrike outage, which was caused by a faulty software update, as we know, pushed to Windows servers on the 19th of July, delta was the hardest hit major airline carrier. Its disruption lasted longer and reached further than what United Airlines, american Airlines and others experienced as the airline grappled with the scale and length of the outage, it moved to shift some of the blame publicly against the cybersecurity provider. Delta's CEO, ed Bastian, told CNBC last week the airline was considering legal action seeking compensation for the $500 million in costs that the airline had endured. Yes, we're grounded and it's hurting. He said we're looking to make certain that we get compensated, however they decide to, for what they cost us. Bastion said Okay, so CrowdStrike pushed the recovery responsibility back on Delta. Interestingly, the airline declined CrowdStrike's help with systems recovery, according to the letter which was shared with CIO Dive.
Okay, now, no one disputes CrowdStrike's ultimate culpability here, even they don't. So what appears to be at issue is matters of degree. I tracked down the text of CrowdStrike's Sunday letter to Delta. So this is CrowdStrike saying Dear David, as in David Boise's you know superpower, well-known attorney said I'm writing on behalf of my client, crowdstrike Inc, in response to your letter dated July 29th 2024, in which Delta Airlines Inc raises issues and threatens CrowdStrike with legal claims relating to the July 19th 2024 content configuration update impacting the Falcon sensor and the Windows operating system Per ends, the channel, the channel file 291 incident. He writes CrowdStrike reiterates its apology to Delta, its employees and its customers and is emphatic to the circumstances I'm sorry is empathetic to the circumstances they faced. However, crowdstrike is highly disappointed by Delta's suggestion that CrowdStrike acted inappropriately and strongly rejects any allegation that it was grossly negligent or committed willful misconduct with respect to the Channel File 291 incident. Your suggestion that CrowdStrike failed to do testing and validation is contradicted by the very information on which you rely from CrowdStrike's preliminary post-incident review.
Crowdstrike worked tirelessly to help its customers restore impacted systems and resume services to their customers. Within hours of the incident, crowdstrike reached out to Delta to offer assistance and ensure Delta was aware of an available remediation. Delta was aware of an available remediation. Additionally, crowdstrike's CEO personally reached out to Delta's CEO to offer on-site assistance but received no response. Crowdstrike followed up with Delta on the offer for on-site support and was told that the on-site resources were not needed. To this day, crowdstrike continues to work closely and professionally with the Delta Information Security Team.
Delta's public threat of litigation distracts from this work and has contributed to a misleading narrative that CrowdStrike is responsible for Delta's IT decisions and response to the outage. Should Delta pursue this path, delta will have to explain to the public, its shareholders and, ultimately, a jury why CrowdStrike took responsibility for its actions swiftly, transparently and constructively, while Delta did not. Among other things, delta will need to explain why Delta's competitors facing similar challenges all restored operations much faster. Why Delta turned down free on-site help from CrowdStrike professionals who assisted many other customers to restore operations much more quickly than Delta. That any liability by CrowdStrike is contractually capped at an amount in the single-digit millions. No-transcript. Oh and yes, in light of Delta's July 29 letter, crowdstrike must also demand that Delta preserve all documents, records and communications of any kind, including emails, text messages and other communications in the possession, including emails, text messages and other communications in the possession, custody or control of Delta, its officers and directors and employees concerning, but not limited to, the items listed below. As I am sure you can appreciate, while litigation would be unfortunate, crowdstrike will respond aggressively if forced to do so in order to protect its shareholders, employees and other stakeholders. Crowdstrike's focus remains on its customers, including Delta. Crowdstrike hopes Delta reconsiders its approach and agrees to work cooperatively with CrowdStrike going forward, as the two sides historically have done. Strike going forward, as the two sides historically have done.
So, ok, you want to? You want to blame us? Let's, let's figure out Delta, why you stood alone as an outlier in the amount of damage that you are alleging that you took relative to all of your peer airlines alleging that you took relative to all of your peer airlines. Industry estimates are that the CrowdStrike outage to the various Fortune 500 airlines will be around a total of $860 million or so, and apparently that's on average about $143 million per airline. But it appears that there is in fact a contractual upper limit that does cap CrowdStrike's liability and that's not in dispute.
The article then offers some interesting background about this, quoting a guy named Scott Bickley, the advisory practice lead at Infotech Research. Scott explained he said, quote the standard limitation of liability, which is interestingly known as the LOL clause, limitation of liability for most SASS. You know, software as a service agreement caps liability at the actual funds spent on the subscription over a set period of time, usually the previous 12 months. That's what I had said before that often these things just say that you're entitled to getting your money back. Essentially is what they're saying. Many enterprises will negotiate a multiple of this amount. He says or a set capped amount or a set capped amount. Bickley said that CrowdStrike's liability is likely to match annual spend or a multiple of annual spend if the clause was negotiated. He said many large enterprises, surprisingly, do not negotiate these terms and default to using the language in the vendor's agreements, which of course in the vendor's agreements, which of course benefits the vendor. He said Delta is likely going to pursue damages outside of the LOL cap and may rely on other legal arguments to bring the claim to a third-party dispute, mediation or litigation. So you know this is exactly what's expected. So you know this is exactly what's expected.
One last note that is sadly happening. Individual travelers who were inconvenienced by this are also suing, even though you know travel delays and flight cancellations and rerouting is quite common. Yesterday Reuters reported crowd strikes. Legal troubles from last month's massive global computer outage deepened Monday, just yesterday, as the cybersecurity company was sued by air travelers themselves whose flights were delayed or canceled. In a proposed class action filed in the Austin Texas federal court, three flyers blamed CrowdStrike's negligence in testing and deploying its software for lodgings, meals and alternative travels, while others missed work or suffered health problems from having to sleep on the airport floor and yes, we did see the carpet on the airport floor and that's not where you'd want to sleep. They said CrowdStrike should pay compensatory and punitive damages to anyone whose flight was disrupted after technology related flight groundings for Southwest Airlines and other carriers back in 2023 made the outage entirely foreseeable. So they're saying, ok, these things happen, so we want to be compensated. And you know, we know what the effect will be.
Right after last year's troubles, after last year's troubles, I would be surprised to learn that the fine print in all passenger agreements doesn't already include a blanket liability waiver for any failure to fly caused by any foreseeable or unforeseeable events. And if it already doesn't, it certainly will in the future. You know this is just the way the world is now. Will in the future. You know, this is just the way the world is now. When you sign forms for a relatively minor procedure in a hospital, the fine print explains that you know quote we're really going to do the best we can to keep you alive, but you know stuff happens. So if something happens, we'll be really sorry. Sign here and good luck. You know it's always a bit unnerving, but what are you going to do?
So, anyway, just as I was finishing up this podcast, I received email from a listener, rob Woodruff, and actually since then a bunch more, informing me that, as a CrowdStrike customer, he had just received email from CrowdStrike's CEO and that their much-anticipated root cause analysis had finally been completed. I had no time to dig into it for today and I do not plan to spend much time on it next week, since we've already given this lots of time and coverage. But if we learn anything new, I will briefly share what we learned from it and, leo, let's share our break, our last break. Then I'm going to talk a little bit about GRC's email and how that's going, and we're going to take a look at how DigiCert handled a certificate revocation.
1:26:26 - Leo Laporte
I guess it's an emergency, but yeah, We've talked about this before and how hard it is to do.
1:26:33 - Steve Gibson
You know it's not Well, Entrust doesn't do it. Yeah, it's so hard that Entrust just says ah no, Nah, can't do it.
1:26:42 - Leo Laporte
We thought about it. We decided not to Our show today, brought to you by Vanta. Whether you're starting or scaling your company's security program, demonstrating top-notch security practices and establishing trust is more important than ever before, and that's where Vanta comes in. Vanta automates compliance for SOC 2, iso 27001, and more, saving you time and money and, of course, helping build customer trust. Plus, you can streamline security reviews by automating questionnaires and demonstrating your security posture with a consumer-facing trust center. All of this, of course, powered by Vanta and Vanta AI. Over 7,000 global companies, like Atlassian, flow, health and Quora, use Vanta to manage risk and improve security in real time. Get $1,000 off Vanta when you go to vantacom slash security now. That's V-A-N-T-A. Dot com slash security now. Vanta dot com slash security now and thatcom slash security now and that's a great deal. $1,000 off Vantacom slash security now. We thank Vanta so much for their support of security now.
Founded by a woman. It's a really neat company, actually Very interesting company, but I haven't run it by them, so uh probably shouldn't mention all of that stuff.
1:28:12 - Steve Gibson
Now back to mr steve tiberius gibson and uh, how revoking well, first I just wanted to mention um that um today's podcast filled up before I could share any of the terrific feedback that I've been receiving in great volume from our listeners. The incoming listener feedback system has been an utter success and I've been drowning in thoughts, notes, pointers to inbox, and we're currently at 1,512 pieces of email received. I guess it's been about four weeks now. I'm mentioning this because I'm torn by my inability to reply to this much incoming email. Initially I was trying to, but then I looked at how much time was going into creating replies and saying even you know, not much more than thanks, so much for sending that. So I need to explain that everyone should know that, even in the absence of any reply from me, if the email did not bounce back to you, I have it, I read it and I'm sure I appreciated it. Really, when I feel that I have to reply, I tend not to read them, since my seeing the feedback creates the feeling of an obligation to reply that I'm just not able to service. You know, that's the way I am. So I want to sincerely, really sincerely, thank everyone here collectively who has written and who will write. I really value this feedback and I am seeing what you have sent. You'll probably often sense it in the effect that you have on the podcast afterwards you know, bits of obscure news that I may have missed if you hadn't told me about it. So please, no one ever imagine that because you don't receive a reply, that means I never saw what you took the time to send. If you took the time to send it, I will have taken at least taken the time to read it, even if I was unable to say so explicitly. So really, thank you.
Last point is that I've received a number of complaints from listeners who were forced to write to Sue or Greg at our sales or support email because they were unable to find the special security now email address anywhere on the site. The reason for that is it's not meant to be public and it's for GRC's non. You know it's not meant for GRC non-podcast visitors, it's just for us. I want to keep it between us and the email address should not be too difficult to remember it's securitynowatgrccom. And to make it even easier, I've set the reply to address of every one of our weekly podcast mailings to that securitynowatgrccom email address. So anyone who receives the weekly email can simply reply to any email they receive, and many of our listeners just do that. So, anyway, again, I've been feeling like the mail's piling up. I just wanted to tell everybody how much I appreciate it. The system's working. I am seeing everything. I've been feeling guilty that I can't thank everybody, so here's a collective thank you. Okay, now revocation.
Just as last week's podcast was happening, my favorite certificate authority, digicert, to purchase interim certificates on behalf of their customers will still need to have their own customers. Entrust's customers prove their control over their pending certificate's domain name directly to SSLcom, and I noted at the time that there are various ways to get that done. The weakest of these is to use email received by and sent to the domain in question. Better ways involve adding DNS records to the domain, which the certificate authority can then remotely pull and verify. As we know, on the one hand, we have Entrust, who has for years effectively refused to revoke certificates which had been shown to be mistakenly issued out of compliance certificates mistakenly issued to their customers and, as we'll see today, on the other hand, we have DigiCert, who takes the CA browser forum requirements to heart and immediately jumped into action when a truly insignificant mistake was discovered. But, as this shows a rule is a rule. Many of our listeners understood this difference and sent notes to me with variations on the subject. This is the way it's supposed to be done. You know, congratulating DigiCert, essentially. You know. Consequently, we have you know how. Revoking for today's podcast title. We have you know how. Revoking for today's podcast title. The Hacker News explained the whole event, complete with updates as of Sunday, and there was one. Their headline was DigiCert to revoke 83,000 plus SSL certificates due to domain validation oversight. But just wait till you hear what it was. I've mixed their reporting with my own clarifications and some small additions. So here's what we have has warned that it will be revoking a subset of SSL TLS certificates within 24 hours due to an oversight in how it verified if taking the step of revoking certificates that do not have proper domain control validation, digicert said, quote Before issuing a certificate to a customer, digicert validates the customer's control or ownership over the domain name for which they are requesting a certificate, using one of several methods approved by the CA browser forum.
One of the ways this is done hinges on the customer setting up a DNS CNAME record containing a random value provided to them by DigiCert. Random value provided to them by DigiCert. Digicert, and this is a 32-character, right, it's a massive gibberish. Random number, random value. Digicert then performs a DNS lookup for the domain in question to make sure that the random values are the same. So they tell the customer put this in here here's some jibberish as a DNS CNAME record. Add this to your DNS. We'll query your DNS Once you say you have only you who control that domain could have done that. So we're good to go. So we're good to go.
The provided CNAME record is for a subdomain of the user's domain and the random value from DigiCert is prefixed with an underscore character. So it begins with underscore so as to prevent a possible collision with an actual, randomly named subdomain that might use the same random value. Note that domain names are not allowed to begin with an underscore. Thus the collision prevention. In other words, digicerts or the CA browser forum specs say browser forum specs say thou shalt begin a name with an underscore because it is an illegal domain name. But it's good for this purpose.
So what the what digi cert found was that it had failed to the underscore prefix before the random value used in some C name based validation cases. Ok, so whether or not that matters is really an edge case. There is an instance where it can matter, which I'll explain in a second, but you know it is a minor problem. But this demonstrates that in the certificate authority space, a rule is a rule and we certainly beat up on Entrust over their flagrant violation of the rules. This wasn't flagrant by any similar means, but OK. Ok, so the hacker news continues.
Digicert's mistake has its roots in a series of changes DigiCert enacted, starting in 2019, to revamp their underlying architecture, as part of which the code to add an underscore prefix was removed and subsequently quote added to some of the paths in the update system unquote, but not to one path that neither added it nor automatically checked if the random value had a pre-appended underscore. Apparently there was some instance where the user was expected to do that, but they didn't verify that the user had. So DigiCert said quote the omission of an automatic underscore prefix was not caught during the cross-functional team reviews that occurred before deployment of the updated system, while we had regression testing in place. Those tests failed to alert us or this sounds a little familiar to the change in functionality, because the regression tests were scoped to workflows and functionality instead of the content slash. Structure of the random value. Unfortunately, no reviews were done to compare the legacy random value implementations with the random value implementations in the new system in every scenario. Had we conducted those evaluations, we would have learned earlier that the system was not automatically adding the underscore prefix to the random value where needed. Okay, so the Hacker News said.
Subsequently, on June 11th of this year, digicert said it revamped the random value generation process, eliminating the manual addition of the underscore prefix within the confines of a user experience enhancement project, but acknowledged it again failed to compare this UX change you know, the user experience change against the underscore flow in the legacy system. The company said it didn't discover the non-compliance issue until several weeks ago when an unnamed customer reached out regarding the random values. In other words, somebody noticed, you know, one of their customers out in the field used in validation, prompting a deeper review. Y'all bet. Digicert noted that the incident impacts approximately 0.4% of the applicable domain validations which, according to an update on the related Bugzilla report, affects 83,267 certificates issued across 6,807 customers. Notified customers are recommended to replace their certificates as soon as possible by signing into their DigiCert accounts, generating a certificate signing request and reissuing them after passing domain control validation.
The development prompted CISA to publish an alert, interestingly, not over any danger that this incredibly minor and inconsequential mistake may have had, but stating that revocation of these certificates themselves may cause temporary disruptions to websites, services and applications relying on these certificates for secure communication. In a later update, digicert said DigiCert continues to actively engage with customers impacted by this incident and many of them have been able to replace their certificates. Some customers have applied for a delayed revocation due to exceptional circumstances and you know like they're on the International Space Station or something I don't know, and we're working with them on their individual situations. We're no longer accepting any applications for delayed revocation unquote. And so Hacker News finishes. These include customers who are operating critical infrastructure who, said quote, are not in a position to have all their certificates reissued and deployed in time without critical service disruptions unquote deployed in time without critical service disruptions unquote. And DigiCert further noted that all impacted certificates yes, all 83,267 of them, regardless of circumstances had been revoked as of August 3rd 2024 at 7.30 pm UTC. So here we have an example of a company that's doing it right, even in the face of a quite significant pain being caused to their own customers by the sudden and essentially emergency requirement to revoke and then replace well, hopefully replace before they revoked their certificates.
And what's more bracing is that there was nothing whatsoever wrong with those certificates, you know, they weren't formed incorrectly, they didn't have bad fields or anything. It was the fact that the domain validation missed something, which was meant to prevent a collision with real certificate names. So this lack of a leading underscore, it in no way allowed anyone to nefariously obtain a certificate fraudulently. Now I should say I wrote that and since I wrote it, one of our listeners who is on the emailing list got the show notes and read this, said Steve, actually there is an instance where there is a collision with a non-underscore name, with a non underscore name. So for there to be a collision, you would need to have a situation where somebody was creating a, a C name record under a domain they don't control. And it turns out that DynDNS works this way, right? Dynamic DNS allows people you normally have, like you're, able to choose from a number of top level domain names and then you choose your own subdomain under that domain name. Well, if that subdomain was what DigiCert had given them, lacking an underscore, that would then allow them to get a certificate for that DynDNS domain. Now, that's not good news, and in fact, it turns out that the DynDNS people are deliberately preventing the use of an underscore, whereas the certificate authorities are going to be deliberately requiring the use. In other words, this is all once again kind of a big mess.
Anyway, the point is, digicert jumped on this, fixed the problem, sent the painful email to all. What did I say? It was 68,000? I mean 6,807 customers immediately actually revoked the certificates, got it done in some cases within a day, where customers needed longer, within five, which is the requirement in the CA browser forums got it done, took responsibility, took the hit, informed their customers and did it immediately. So, yes, they did it immediately. So, yes, they did it right. I should note that since this issue with the DynDNS possibility occurring, history has been checked. This never happened, so there was never any abuse of it. And now the DynDNS people will be disallowing the use of a leading underscore, whereas all of the use of CNAME records will require one, and this will keep those two uses from colliding.
Finally, I'm third-party cookies, because the entire web browser revocation system is a total and utter joke. It is completely broken. It has always completely broken. It has always been broken and it has never worked, despite some half-hearted attempts from time to time to fix it. It is broken, you know. It never got fixed. Web browsers do not know when the certificates they're receiving from web servers have been revoked. Now, if we have some time next week, we're going to update ourselves on this space, that is, on this issue, because the truth is there may have been some use cases where certificates were being used where something actually would have known if they'd been revoked and that would have caused a problem, but mostly, no, not a single browser.
In the meantime, try aiming your browser, whatever browser you have, at revoked dot GRC dot com, at revokedgrccom. I brought that interesting and revealing test back to life last week in anticipation of this topic. So revokedgrccom, go there with your browser If it tells you, sorry, this site is untrusted. Well, that's amazing. That used to happen in some cases with Firefox if you forced it to do online certificate revocation checking and told it not to fail open and a bunch of other things that the revokedgrccom site provides the browser with a certificate. I revoked on purpose last week. No browser that I have tested works right. Even safari that used to no longer does so if you see that page, sorry folks you should.
1:49:21 - Leo Laporte
What should I be seeing like a big warning?
1:49:24 - Steve Gibson
I see that Is that what I should see. There you go, oops.
1:49:31 - Leo Laporte
I shouldn't be seeing that.
1:49:32 - Steve Gibson
No, that means that your browser is showing you a certificate that has been revoked.
1:49:39 - Leo Laporte
It's based on Chromium. Let me try Safari.
1:49:44 - Steve Gibson
Safari used to work on iOS. That was the one that I remember saying, wow, that's pretty good. I tried it last week after I brought the site back to life and issued a new. This certificate is only a week old, but I revoked it immediately after DigiCert made it for me.
1:50:03 - Leo Laporte
Oh, there you go, safari. Nice job, it says, if you can see this, and apparently, apparently, you can show this one too. Benito, that's Safari. Let me see Firefox. This is terrible.
1:50:18 - Steve Gibson
I know, leo, this is terrible Steve. It doesn't actually Certificate. Revocation does not work.
1:50:24 - Leo Laporte
Apparently crash Safari as well. Let's see here Not now Revoked R-E-V-O-K-E-DGRCcom. Oops, I said E-Revoked, that failed. Oh no, you got to show these Renita. Oh no, they're all the same. Yep, Everybody. That's amazing. Yep, Everybody.
1:50:53 - Steve Gibson
And if you go to SSLLabscom and have it check the server revokedgrccom yeah, because SSLLabs that's Ivan Ristick's really terrific site, because SSL Labs that's Ivan Ristick's really terrific site ssllabscom and then tell it to check, revokedgrccom.
1:51:23 - Leo Laporte
You will see what it thinks, because it actually checks to see what's going on.
1:51:28 - Steve Gibson
You're supposed to see an error, right?
1:51:31 - Leo Laporte
No, it's actually doing a deep test of like exactly what Testing all the different TLS systems.
1:51:34 - Steve Gibson
Yeah, different protocols. It checks the certificate chain, it checks which protocols you accept and I think if you scroll down you'll see some red there Insecure revoked.
1:51:46 - Leo Laporte
Do not trust.
1:51:47 - Steve Gibson
Do not use this in your code and every one of our browsers ignores that they're. They do not know that certificates have been revoked. It's broken it's always been broken. Okay, you remember when I went off on a binge about this years ago?
1:52:02 - Leo Laporte
yeah, because I also remember that that google said yeah, we're not even going to try to support this because it doesn't work.
1:52:09 - Steve Gibson
Actually, it embarrassed them, and so they added my certificate as a special case. Oh no, yes, that's not the way to do it. No, I just changed the certificate and it came back, and then they didn't bother doing it again because they knew that's hysterical.
1:52:25 - Leo Laporte
So they wrote an exception just for you yes, they did oh shame, shame, shame so what makes us revoked? Just that you. It's not that it is it's. It's not that it's invalid, it's just that you specifically said to digister.
1:52:40 - Steve Gibson
I revoke this well, it's so like, for example, if the certificate certificate got loose and malware was using it, then you would want to revoke it so that malware wasn't able to use it to impersonate your site Can't. Or DigiCert just revoked for what good it did? They just revoked 83,000, or what was it 8,300.
1:53:03 - Leo Laporte
Yeah 8,300. No, no, 6,800 customers, 83,267 certificates, and it didn't matter, they didn't have to invoke them Because the browser doesn't know, the browser doesn't care.
1:53:14 - Steve Gibson
It doesn't know.
1:53:16 - Leo Laporte
Unbelievable Yep.
1:53:18 - Steve Gibson
Doesn't work.
1:53:18 - Leo Laporte
Right now it's testing Bleichenbacher, so we're still testing. Bleichenbacher is what you tested for bleichenbacher? I don't know. This is sls. You're right, this ssl labs is pretty thorough yeah, it's really terrific yeah, yeah, I mean it's taken a long time to go through this.
1:53:38 - Steve Gibson
Wow, yeah, because it's going back and forth handshakes with with the server. Those are all.
1:53:45 - Leo Laporte
Those are all exploits against TLS that it's testing Very nice, but the main test is is this certificate revoked? Yes, it is.
1:53:57 - Steve Gibson
It is revoked and the browser doesn't know. Unbelievable.
1:54:03 - Leo Laporte
Wow, that is really so. How long has this page been on? I know this is a new cert, but you've had this page before, right? Oh yeah?
1:54:10 - Steve Gibson
yeah, we did multiple podcasts about it back in the day. I remember, yeah, and so that page will show that. I just edited it because I did in order to bring it back to life.
1:54:22 - Leo Laporte
If you're reading this, good luck.
1:54:26 - Steve Gibson
You may not be where you think you are.
1:54:28 - Leo Laporte
Good luck. What that means is you may not be where you think you are good luck.
1:54:29 - Steve Gibson
What that means is, you may not be where you think you are yeah, yeah, because the certificate's meaningless.
1:54:35 - Leo Laporte
Yep, wow, what a world see they? They've what. What people count on is that that you don't exist, that people don't listen to this show, that they don't know this stuff and they're just kind of blithely going along. Well, yeah, we have certificate revocation. Of course we do. It's. Uh, it's in the spec. We must have it. Wow, no, we don't. No, this is why you listen to the show. This is why steve is a national treasure. This is why you should join Club Twit to support Steve and his work. I don't know what else to say. You should buy ads on the show too. Grccom that's his website, the Gibson Research Corporation. If you want to be on the mailing list or send him email same page, grccom slash email He'll validate your address. Then you can or cannot subscribe to the mailing list, which you probably want to do, but you could also now email him because your address is good, verified. Yeah, we have a really neat one-click unsubscribe.
1:55:40 - Steve Gibson
What happens is I'm also getting subscribers just random GRC visitors and they go. Oh yeah, I want to get email from GRC, and so they subscribe to all three. Then on a Tuesday morning when they actually get the email, they look at it and go. I don't want this.
1:55:56 - Leo Laporte
And so there's and so.
1:55:58 - Steve Gibson
so there's a, you know, a single click, instant unsubscribe. And so, like I think, I got like six unsubscribes after doing the emailing, because these are people who had joined the list during the past week and thought, no, this is dumb, I just want to get, I want to find out. Well, actually, I'll do my first mailing as soon as the IsBootSecure app is ready.
1:56:21 - Leo Laporte
We should. By the way, there are a number of people saying, oh my God, this means the whole certificate thing is bogus. A number of people saying oh my God, this means the whole certificate thing is bogus. No, certificates still are valuable for encrypting your traffic between a site. To verify the site is who they say they are. It's just this revocation thing does not work. So you can't revoke a site that has leaked out or is somehow malicious. You can't take it back.
1:56:49 - Steve Gibson
But I guess it does mean you shouldn't necessarily trust the certificate certificate on any site. That's the whole point. That's why we have revocation where we're headed is and google has mentioned this before because they're the brokest of all they're they're. The chrome has never even I mean it was the pretense of of what the chrome was saying that upset me so much right back when we, when we were talking about this because they said oh, we have a crl set and it you know we, you know we're managing this ourself.
I said no, you aren't, and I created this to demonstrate it. So where they're headed is 90 day certs, like letrypt uses. So they just expired Exactly, you can't revoke them, but you don't have to wait very long for them to die a natural death.
1:57:35 - Leo Laporte
But that gives a cert as much as 90 days to be wrong.
1:57:39 - Steve Gibson
Bogus, yes, but it's better than nothing, which is what we have now, and unfortunately it does mean that all certificate management has to be automated. You know, right now it's it, they, they reduced it. Yeah, it used to be five years, then three years, then now we're at a little one year and one month, you know, 13 months and uh, so eventually we will uh, you know, probably get down to 90 days, and no one's going to want to do that by hand, they're just going to want to use the ACME protocol to do that.
1:58:11 - Leo Laporte
Right, if you want to share that last little bit about certs with other people, you can go to youtubecom slash security now and just clip it. That's a great way to do that. Steve has copies of the audio of the show 64-kilobit audio, 16 kilobit audio, which is, of course, much smaller. Uh, for the bandwidth impaired. He also has transcripts if you like to read along, and he has the full show notes, which is what I show from time to time on the screen. All that's at grccom. While you're there, pick up a copy of spin right, the world's finest mass storage, performance enhancer, uh, recovery utility and maintenance utilities. I get it all. That's good. Yeah, versus. 6.1 is the current version. You can get it right now at grccom. And it's his bread and butter, steve's bread and butter. So you know if you don't have a copy. Everybody who has storage of any kind should have it. Sieve's got a lot of free stuff there, like valid drive and decombobulator. I don't know anybody's really needs decombobulator anymore, but no, no, you don't get a lot of downloads for that anymore. Shields up though. Every time I got a new router I test it with shields up. That's a must. And on and on and on. He's really the king of freebies, including this new one. What do you call it again? And on and on. He's really the king of freebies, including this new one. What do you call it again? Is Boot Secure? Is Boot Secure? Is Boot Secure? He sounds like Boris Badenov version of utility. You can get that at GRCcom.
We have the show at our website, of course, twittv slash SN. I mentioned the YouTube channel and and, of course, you could subscribe in your favorite podcast client. That's probably the easiest way to get it. If you're a member of the club, you can get ad free versions of all the shows, including security now, plus access to a lot of other wonderful club benefits, uh, like access to the discord, which is full of smart, interesting people like you. You could. That's a really great community. You can also. We have regular events in there and with the new studio, the new Addict Studio, I expect to do a lot of ad hoc streaming based on the news of the day or just whatever. I feel like talking to somebody In your jammies.
In my jam jams. So if you want to join the club, you'll get notification automatically in the Discord whenever I go live. A lot of reasons and it's only $7 a month. The most important reason is you're supporting the work we do here. We're doing our part. We're shutting down the studio. We're going to save a lot of money by doing that. We haven't had to fire anybody. That's good news. We did cancel.
Ask the Tech guys. Micah's going to take that over, as hands-on tech do weekly half-hour shows and I'm going to use that time to do more live streaming, which I think will be a lot of fun now that I have a studio just up seven steps from the bedroom. It's a little too close. If you ask me, it's just right there. What else can I tell you? Join the club. Twittv slash club twit seven bucks a month Very important to us. It's kind of a way of saying a voting, of saying yeah, we like this, we need this, we want to keep this going. Here's $7. That's really what it is and your vote makes a big difference to us. So please, please, do join a club, steve. We'll, please do join our club. Steve will be back next week. I will be in the attic. This is it for the studio. Say goodbye, goodbye, studio. The attic is even more salubrious and cozy, kind of like your place.
2:01:37 - Steve Gibson
Kind of like the cottage used to be right yeah.
2:01:40 - Leo Laporte
It's actually a little bigger than the cottage. The cottage was a little cramped.
2:01:45 - Steve Gibson
Yeah, a little cottagey.
2:01:48 - Leo Laporte
We've been doing this a long time. Steve 999 is just 13 episodes away on our way.
2:01:53 - Steve Gibson
Yep, yep gonna make it.
2:01:55 - Leo Laporte
Yep, thank you so much, steve. We'll see you next time on security. Bye.